Bitdefender Again Leads the AV-Comparatives Advanced Threat Protection Tests

In November of 2022, AV-Comparatives concluded their 2022 Advanced Threat Protection Test for enterprise cybersecurity. The test simulates attack methods used by cybercriminals to gain control of an organization’s network. These advanced persistent threats (APTs) utilize fileless attacks that leverage popular scripting languages like JavaScript, PowerShell, Visual Basic, and more, to gain access to an organization’s internal computer systems. Fileless attacks are executed in memory by leveraging expected processes to avoid detection from traditional antivirus products. These types of tactics are common in data extortion attacks perpetrated by cybercriminal organizations and state-sponsored cyber-espionage operations. The tactics and techniques used in the test can be mapped to the MITRE ATT&CK framework.
Test targets are Windows 10 64-bit systems that make up most computer endpoints used in organizations at the time of this writing. The test consists of 15 different attacks concentrated on challenging the security solution’s protection capabilities. The participating vendors were measured on how well each solution prevented the attacks from succeeding in the attack’s initial phase. To not distract from the specific emphasis of the analysis, detection and response capabilities were not evaluated. Nine enterprise vendors had their products evaluated by AV-Comparatives: Bitdefender, Acronis, Avast, CrowdStrike, ESET, G Data, Kaspersky, Microsoft and VMware. A separate test of EPR products and their detection / response capabilities can be found on AV-Comparatives website.
About this evaluation
The 15 attack scenarios used by AV-Comparatives mimic real-world malware. These attacks follow the Lockheed Martin Cyber Kill Chain framework that involves several different conditions. The most prominent are the ability to exploit the vulnerability of software installed on a system and the capacity to establish a command-and-control channel for remote manipulation of the system. A “false alarm” test was also included in the evaluation to measure each cybersecurity solution’s ability to distinguish between an actual threat and a false-positive, and to prevent vendors from using aggressive settings to artificially improve their results.
A common trait of advanced persistent threats is the ability to use a standard user account on the system to avoid raising suspicion. With that in mind, each of the 15 attack scenarios used by AV-Comparatives targeted standard user accounts in the Windows operating system. Different communication channels were used for the command-and-control communications including HTTP, HTTPS, and TCP. Popular exploit frameworks such as Metasploit, PowerShell Empire, and commercial frameworks were employed. In their evaluations, AV-Comparatives describes a compromised system as one where a “stable Command-and-Control connection” is established.
The tests included fileless attacks that can effortlessly bypass traditional antivirus solutions by running exclusively in memory. These attacks are often delivered through commonly used Office macros, WMI calls, JavaScript, PowerShell, and more. In the evaluations, AV-Comparatives leveraged several different command-line stacks which loaded the malware directly from the network into memory, avoiding writing to the system hard drives which are usually heavily protected by security solutions. Once the attack was loaded into the memory of the system, the evaluators then attempted to successfully establish command-and-control utilities over standard HTTP, HTTPS, and TCP protocols. This allows attackers to bypass firewalls and other network protections an organization may employ. Once the C&C connection is established, the attacker may effectively gain control of the victim’s network and could exfiltrate data, plant ransomware and keyloggers, access the victim’s webcam, and more.
AV-Comparatives goes on to advise that “readers who are concerned about such attacks should consider the products participating in this test, whose vendors were confident of their ability to protect against these threats in the test”.
Analyzing the evaluation results
The AV-Comparatives tests are meant to spotlight the evaluated security solutions ability to protect systems from these potentially devastating advanced attacks. The 15 different scenarios are used to expose weaknesses in the security solution’s ability to identify and prevent malicious behavior from succeeding during an attempt to compromise a system. AV-Comparatives goes on to say, “We expect attacks to be blocked regardless of where/how they are hosted and where/how they are executed. If an attack is detected only under very specific circumstances, we would say the product does not provide effective protection.”
The false-positive detection included in the evaluation is also immensely important as a product that can’t distinguish between a legitimate threat and a false alarm can be incredibly disruptive to security teams. The failure to provide accurate detections creates alert fatigue which quickly overwhelms security teams by wasting their time with unnecessary incident investigations. The ultimate result can be increased dwell time of an advanced persistent threat while teams are distracted by a deluge of persistent false positives.
Bitdefender results
Bitdefender tied for the highest score across all 15 test scenarios. We successfully prevented the Command-and-Control connection in all but one scenario.
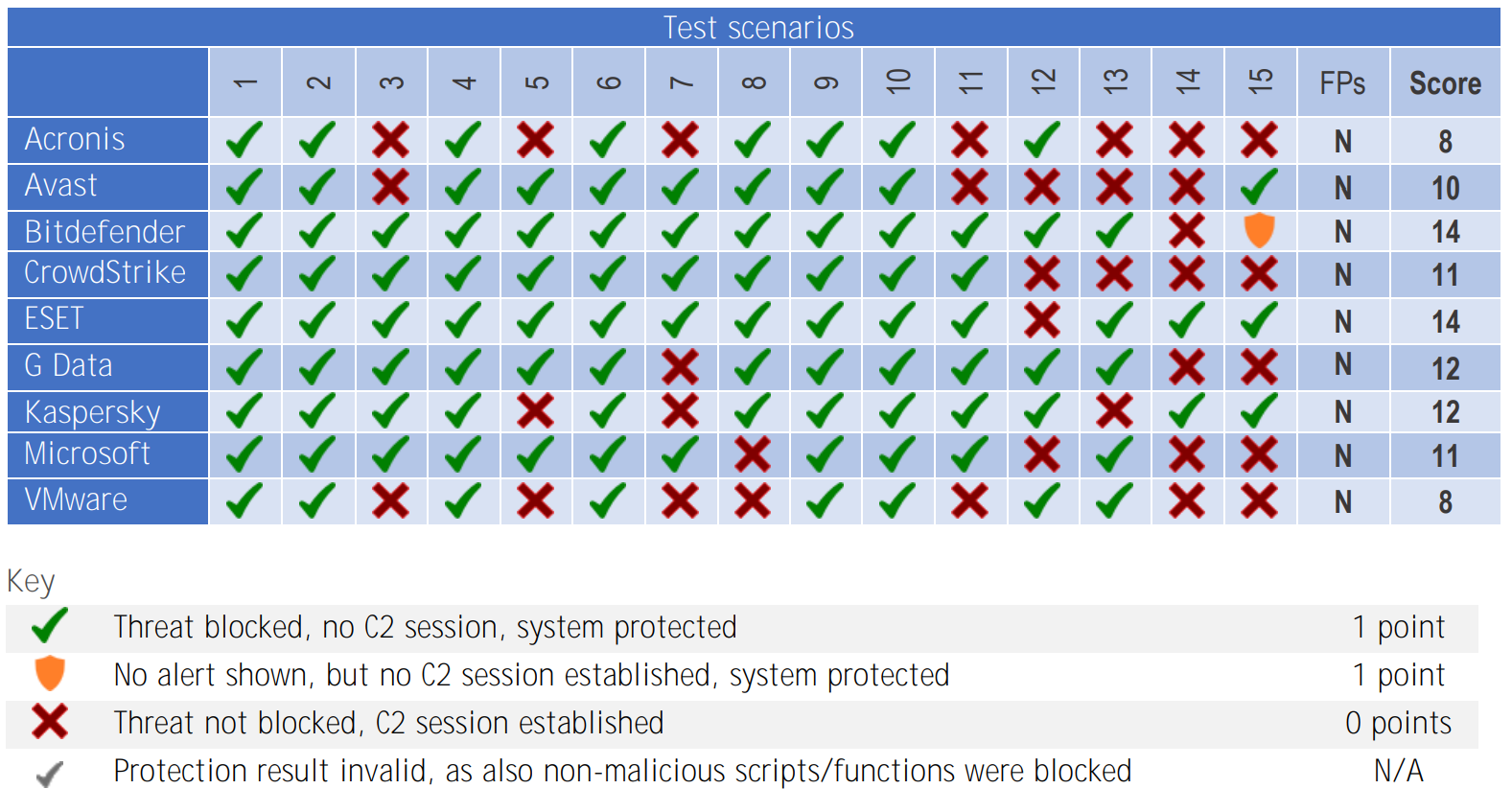
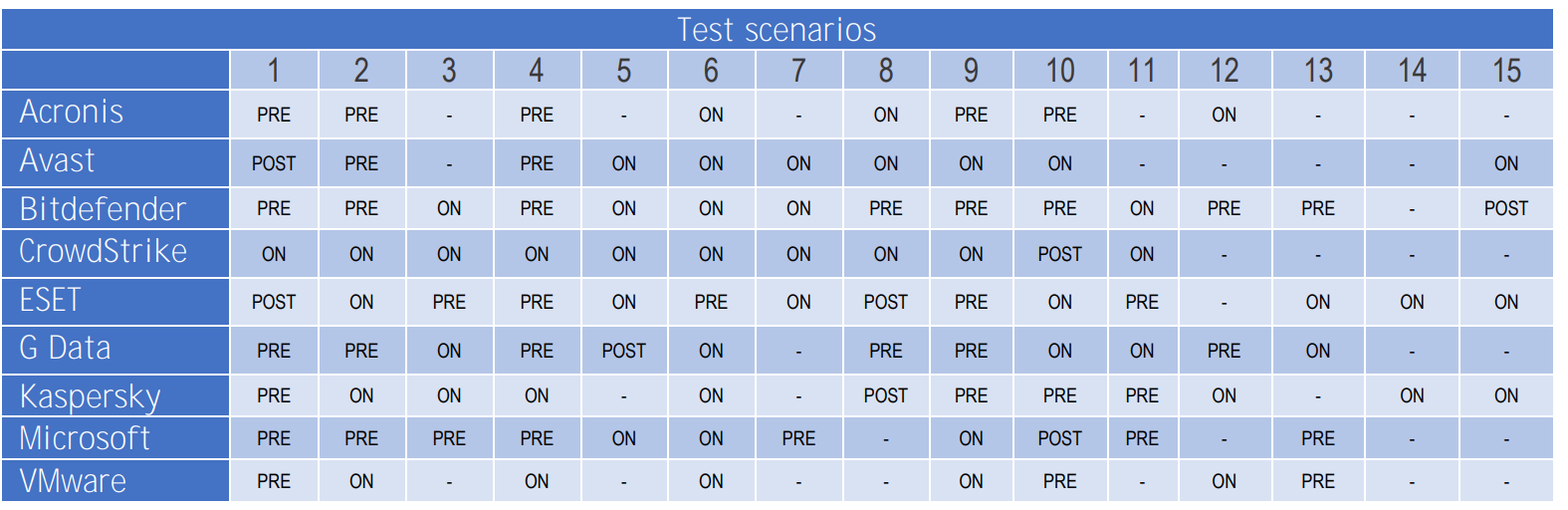
However, that is only part of the story. If we look at the chart provided by AV-Comparatives detailing when in the attack chain each detection occurred – during pre-execution, on execution, and post-execution – Bitdefender stopped the threat before execution in 53% of scenarios. For comparison, the average of the other vendors was 27%, with some participants not detecting any threats prior to execution. When reviewing the entire evaluations, Bitdefender was able to prevent attack in 93% of scenarios while other vendors averaged 72% -- this difference could result in exposing your organization to four times as many security breaches!
A security solution that can stop an attack at the pre-execution stage is not only more likely to keep systems secure, but it provides the attacker with a much more difficult time breaking through. If you think of each attack stage as a barrier an attacker must get through, Bitdefender provides the most effective barriers against cyberattacks.
As AV-Comparatives themselves so aptly put it in their analysis, “A good burglar alarm should go off when somebody breaks into your house, not wait until they start stealing things”.
Conclusion
Bitdefender proves once again that we are the top choice for organizations of all sizes which demand protection from the most advanced new, existing, and emerging cyber threats. Our ability to prevent attacks before they can do damage is unsurpassed! Bitdefender offers fileless attack protection that is designed to monitor a system’s memory for malicious code injections. It uses patented machine-learning technology to analyze command lines and PowerShell, scrutinize internet connections, monitor process behavior and protect memory space of running process. When it detects malicious intent, it terminates the process at the pre-execution stage, preventing any harm from being done.
It’s no surprise that AV-Comparatives named Bitdefender a “Strategic Leader” in their Endpoint Prevention and Response test for 2022. We pair this potent technology with impressive Endpoint and Human Risk Assessment tools included with our core offerings.
Along with world-class prevention, Bitdefender XDR also offers powerful extended detection and response tools that identify suspicious behavior across systems, networks, cloud workloads, identities, and productivity applications. Businesses of all sizes can pair this award-winning technology with extensive cybersecurity expertise through our Managed Detection and Response service.
Learn more about how to combat advanced persistent threats with Bitdefender Business Solutions.
tags
Author

My name is Richard De La Torre. I’m a Technical Marketing Manager with Bitdefender. I’ve worked in IT for over 30 years and Cybersecurity for almost a decade. As an avid fan of history I’m fascinated by the impact technology has had and will continue to have on the progress of the human race. I’m a former martial arts instructor and continue to be a huge fan of NBA basketball. I love to travel and have a passion for experiencing new places and cultures.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











