Bitdefender a Top Performer in New Independent Tests

Bitdefender GravityZone continues to consistently stand out in new independent tests from AV-Comparatives and AV-Test, demonstrating exceptional threat prevention and response capabilities across a variety of platforms. Below is an overview of the tests and Bitdefender performed.
The AV-Comparatives Endpoint Prevention & Response Test
The AV-Comparatives Endpoint Prevention and Response Comparative Report for 2024, are a set of periodic evaluations that are published to measure security vendor’s products for their capacity to provide active and passive response to modern cyber threats. This year, products from twelve different vendors including Bitdefender, CrowdStrike, Check Point, ESET, Kaspersky, Palo Alto Networks, VIPRE, and five other unnamed vendors were tested.
Each product was put through 50 different attack scenarios in a hypothetical 5,000 endpoint environment. The attack scenarios were chosen for their ability to mimic real-word multi-staged attacks that target an organization’s network and systems. Beyond protecting against successful execution of the attacks, the solutions were expected to perform in-depth analysis of attack vectors, methodologies, and intent. By providing this level of visibility they can empower security teams to effectively contain threats, remediate compromised systems, and implement measures to prevent recurrence of security breaches.
AV-Comparatives Evaluation Criteria
The 50 attacks were evaluated in their capacity to reach three critical stages:
- Endpoint Compromise and Foothold: How successful threat detonation was in an effort to compromise the security of the system.
- Internal Propagation:Once the system was compromised, how successful was the threat’s capacity to spread to other systems.
- Asset Breach: The attack’s capacity to gain access to sensitive data or resources.
Within these critical stages, AV-Comparatives assessed each product for their active response, and passive response capabilities. AV-Comparatives defines active response as the solution’s ability to automatically block the threat, while passive response measures the solution’s capacity to provide “actionable intelligence that an administrator could use to intervene.”
With these criteria in place, the vendors were each evaluated over a hypothetical five-year period measuring them for breach prevention effectiveness, cost-effectiveness, operational accuracy, and workflow efficiency. These measurements are then translated into what AV-Comparatives call their “CyberRisk Quadrant,” that is then used to designate each vendor in one of the following categories: Strategic Leader, CyberRisk Visionary, Strong Challenger, and Not Certified.
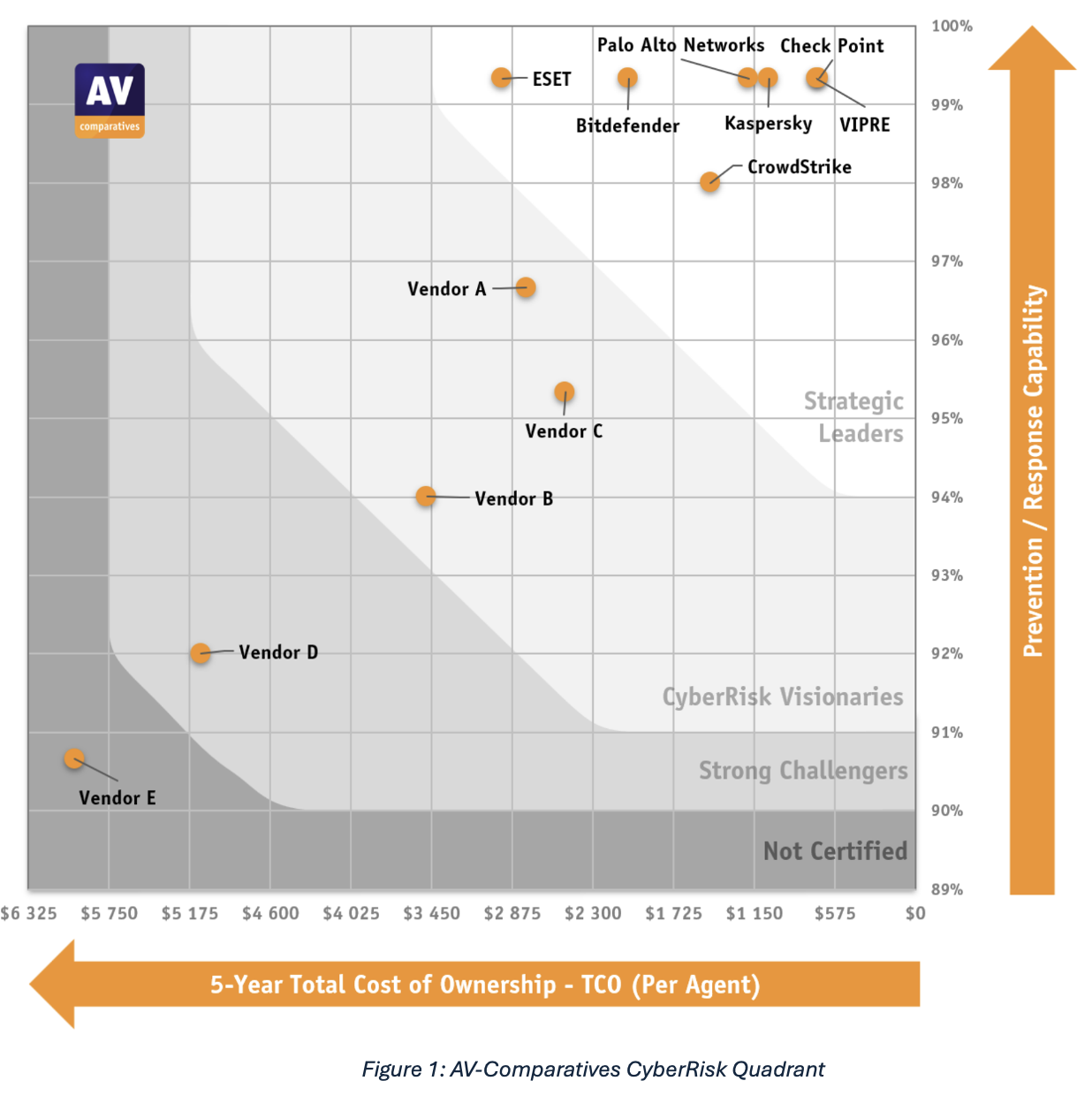
Bitdefender Classified as Strategic Leader
The test results firmly place Bitdefender as a “Strategic Leader.” In the 50 simulated attacks, Bitdefender excelled at handling threats "before the threats could progress inside and infiltrate the organization's network." We achieved the highest active and passive response rate at 99.3%.
Phase 1
The first stage of the attacks measured three important tactics described by the MITRE ATT&CK framework:
- Initial Access: The method used by the threat to gain unauthorized entry into a target's network or system.
- Execution: The threat’s ability to run malicious code on a compromised system to achieve the attacker's objectives.
- Persistence: This describes the attacker's actions to maintain unauthorized access to a compromised system or network. This could include installing backdoors, modifying system settings, or exploiting vulnerabilities to gain and maintain control.
Bitdefender GravityZone was not only able to automatically detect and thwart each of these tactics, but the solution was able to provide helpful contextual data that allowed the evaluators to prioritize events.
Phase 2
The second phase of the attacks measured internal propagation. Once again, several different tactics were used to test the capacity of the solutions to prevent the threat from spreading:
- Privilege Escalation: once a system is compromised, an attacker gains higher-level access within a compromised system or network.
- Defense Evasion: This involves the threat’s actions to avoid detection by security systems or personnel.
- Credentials Access: The attack’s ability to steal credentials, such as usernames and passwords, from a compromised system or network.
- Discovery: This measures the attack’s capacity for identifying valuable assets, mapping network topology, or system configurations.
- Lateral Movement: Techniques used by threat actors to move from one compromised system or network to another within the target environment.
During Phase 2, Bitdefender GravityZone provided full active and passive response against the tactics measured in this stage of the attack. Furthermore, AV-Comparatives pointed out that “When attacks were detected at a later stage, Bitdefender was able to trace them back to their origin and provided detailed information.”
Phase 3
The final stage of the attack, asset breach, measured the ability of the threat actor to acquire sensitive data from the target. This is clearly the most damaging potential of any cyber attack, as it would allow a criminal access to sensitive personal data, critical infrastructure details, or intellectual property. There were four different categories that were evaluated in this phase of the attack by AV-Comparatives:
- Collection: The theft of data, which could include files, documents, databases, emails, images and more.
- Command and Control: The ability of the attack to enable communication between the attacker’s system and the target’s network. A successful C&C connection can allow unfettered access to the entire organization by a threat actor.
- Impact: Measures direct harm on the target’s systems and network, which could include the encryption, manipulation, or destruction of data.
- Exfiltration: Describes the attack’s capacity to transmit data from the target through the network to the threat actor’s servers.
In the evaluations, Bitdefender did not allow a single attack to reach phase 3. These results reflect our commitment to protect organizations of all sizes against the most damaging aspects of a security breach.
Other Factors Measured
In this yearly evaluation there are other aspects of the AV-Comparative measures. They first start by comparing what they label as “EPR Cost Structure” which is intended to contrast the end-user cost for the vendor’s product over the hypothetical 5-year span covering 5,000 endpoints. Here, Bitdefender was identified as having the lowest EPR Cost among the evaluated vendors.
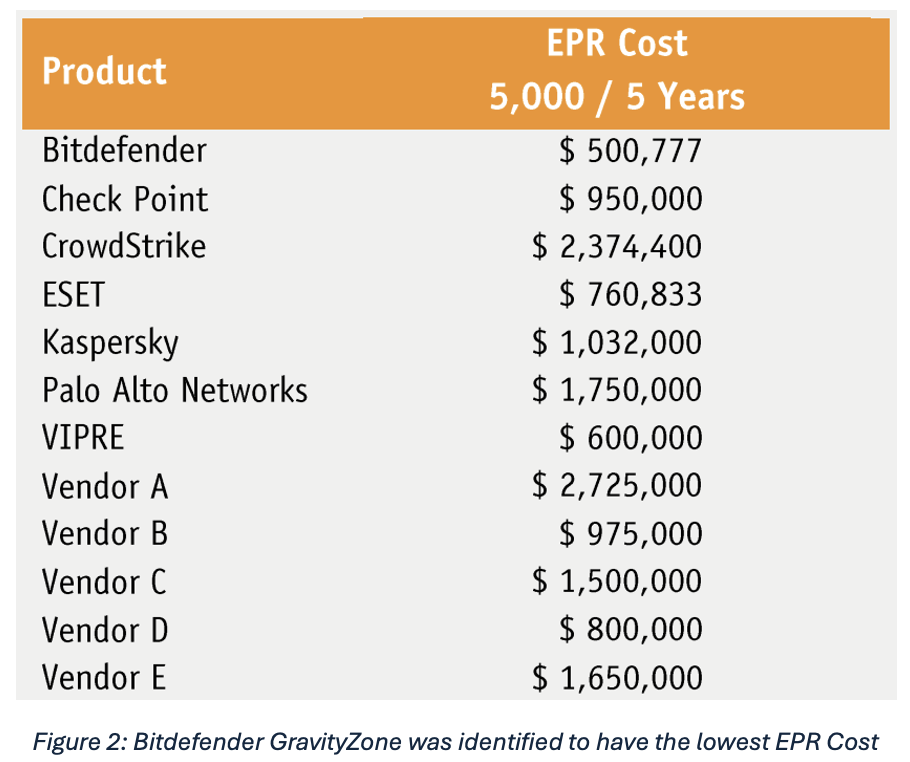
AV-Comparatives does caution that “pricing may vary based on factors like volume discounts, negotiated discounts, geolocation location, distribution channels, and partner margins.” With this as a baseline, AV-Comparatives then goes on to implement two additional criteria:
- Operational Accuracy: This measures the product’s propensity to block the execution of “administrator-friendly tools and scripts”, which could lead to false-positives.
- Workflow Delay Costs: This measures the product’s proclivity to stop the execution of files while it performs further analysis (such as in a sandbox environment).
With these factors in place, AV-Comparatives then performs additional calculations on Total Cost of Ownership of the product. Bitdefender’s results in this part of the evaluation were mostly positive, given we experienced no workflow delays, while operational accuracy was measured as “moderate.”
AV-Test ATP Endurance Test
Periodically, AV-Test releases their six-month report for its Advanced Threat Protection Endurance Test. The results compare 31 different products from 14 different vendors. These endurance tests are designed to not only evaluate how well the solutions can detect advanced threats, but also how successful they are at preventing the threats from harming Windows 10 systems.
Two Bitdefender business products were evaluated in these tests, Bitdefender Business Security (previously known as Bitdefender Endpoint Security) and Bitdefender Business Security Enterprise (previously known as Bitdefender Endpoint Security Ultra). Both products performed admirably, achieving the top marks across each of the evaluation criteria.
AV-Test Evaluation Criteria
The AV-Test Advanced Threat Protection Endurance Tests were designed to reproduce complex attack techniques Windows 10 systems would be vulnerable to. Among the techniques reproduced were:
- Reflective Code Injection: A type of file-less attack, this technique consists of injecting malicious code into a system’s memory. By not writing the malicious code to disk, this can bypass traditional detection methods.
- Fileless Malware: This describes the type of malware that operates entirely in memory. Using tools like PowerShell, the attacker can use fileless malware to make changes to the registry or system files.
- Use of a Scripting Interpreter: The test used AutoHotkey, an open-source scripting language for Windows used to automate tasks to directly execute instructions on the Windows 10 subsystem for the purpose of loading ransomware or an infostealer.
- MSI: The Microsoft Software Installer program was used to conceal malicious files that can later be extracted during the attack.
- NSIS: The Nullsoft Scriptable Install System is an open-source scripting tool that, like MSI, can be used to package malicious files into an archive which can later be extracted.
- Malicious Code in a LNK Fle: Using the Windows Shortcut file format (LNK), attackers can hide malware disguised as other programs. Once the shortcut is clicked, the malicious code is executed.
Using these techniques, 31 products were tested from January to June 2024 across three different tests. Not every product participated in each of the tests. AV-Test did not specify exactly why this method was selected but regardless, each of the products was scored on how well it detected the attack, and how well the solution prevented malicious payload from infecting the system. The later criteria were reflected in the “Protection Score” and “Max Protection Score.” They way AV-Test describes it, products that committed minor errors were deducted points from the “Max Protection Score.” The details of these errors were not shared by AV-Test. Let’s review the results.
Bitdefender Scores Top Marks in AV-Test Endurance Test
Bitdefender Business Security Enterprise was the top performer among all evaluated solutions, achieving the highest score possible. Three separate tests were conducted featuring 30 attacks. According to AV-Test, “The only product in the endurance test achieving 105 out of 105 possible points was the solution Bitdefender Endpoint Security Ultra (Bitdefender Business Security Enterprise).” The core business product, Bitdefender Business Security, came in second in these test.
-png-Oct-03-2024-02-21-36-3219-PM.png)
Figure 3: Bitdefender achieved the best result on the business tests, achieving a Max protection score of 105.
Bitdefender’s strong performance inspired AV-Test to declare that our business product “stood out of the crowd” with its impressive results. These results add to Bitdefender’s remarkable record of being the only active vendor that has achieved perfect scores in Protection, Performance, and Usability over the last seven AV-Test Endpoint Security tests.
Conclusion
With the results of the two new independent tests from AV-Comparatives and AV-Test, Bitdefender has once again demonstrated the ability to provide exceptional protection and prevention capabilities suitable for organizations of all sizes. These findings underscore Bitdefender's commitment to delivering top-tier cybersecurity solutions that can effectively safeguard businesses against a wide range of threats. As cybercriminals continue to develop new ways to attack businesses, Bitdefender will be there to help your business prepare for whatever comes next.
tags
Author

My name is Richard De La Torre. I’m a Technical Marketing Manager with Bitdefender. I’ve worked in IT for over 30 years and Cybersecurity for almost a decade. As an avid fan of history I’m fascinated by the impact technology has had and will continue to have on the progress of the human race. I’m a former martial arts instructor and continue to be a huge fan of NBA basketball. I love to travel and have a passion for experiencing new places and cultures.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks








