Bitdefender Threat Debrief | September 2024

Ransomware threats continue to challenge security professionals, requiring constant vigilance. By closely tracking shifts in victim profiles, attack techniques, and industry targets, we uncover critical insights into how these cybercriminals operate. In our monthly Threat Debrief, we examine ransomware group activity from August 1 to August 31, 2024 where 414 victims were publicly claimed across various industries.
Now, let’s explore the most notable ransomware news and findings since our last Threat Debrief release:
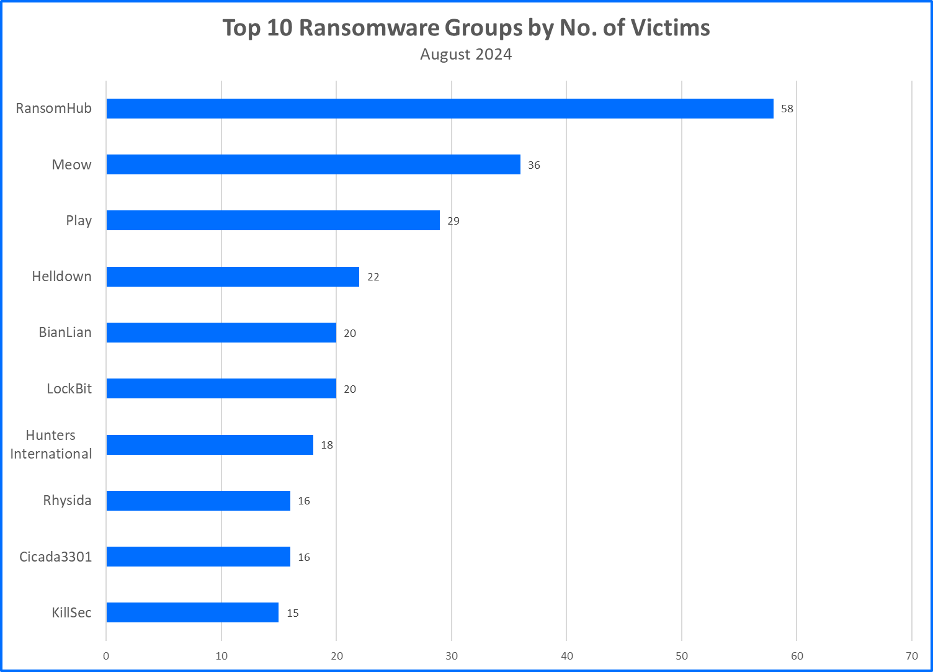
- RansomHub Leaves More Victims in Its Wake: RansomHub, a group that has historically maintained a position in Bitdefender’s Top 10 Ransomware Groups, has claimed more than 200 victims in their campaign against private and critical sectors. RansomHub’s operations were identified by multiple investigation agencies in February of 2024; CISA recently published a joint advisory documenting RansomHub’s TTPs and mitigation practices. RansomHub has incorporated EDRKillShifter into its EDR bypass techniques; the tool is leveraged based on the BYOVD concept. Several payloads are extracted to identify trusted drivers that are a match for vulnerable ones on a victim’s system, exploit vulnerabilities present to gain privileged access, and stop EDR processes.
- Cicada3301 Ransomware Emerges in BlackCat’s Shadow: The ransomware group known as Cicada3301 (also Cicada) claimed more than 15 victims in the past month. Various reports refer to Cicada as a variant from the BlackCat family since aspects of its code are similar. It’s also possible that Cicada is a rebranded group that operates under a new name in place of BlackCat. Cicada shares characteristics that align with BlackCat’s TTPs, including lateral movement, defense evasion, and the inhibition of system recovery measures.
- Meow Leaks Attacks Persist: Meow Leaks, a ransomware group with a global reach, claimed over 30 victims in August. As posts on their data leak site accumulate, Meow Leaks remains a significant threat. We anticipate that Meow Leaks will be featured in next month’s Top 10 Ransomware Groups among the top five families.
- International Ransomware Operation Disrupted: The ransomware operation organized by Dispossesor (Radar), also known as Brain, was disrupted following the seizure of 24 servers and 9 domains by international agencies. Multiple intelligence agencies were involved in the international investigation, including forces based in the United States, the United Kingdom, and Germany.
- UNC757 Campaigns are Identified as State-Sponsored Attacks: Ransomware attacks launched by the Iranian group UNC757 have claimed a range of victims, including organizations in the United States and Middle East. CISA reported that while UNC757, also known as Br0k3r and xplfinder, has operated since 2017, in recent years their attacks have been backed by the Government of Iran (GOI).
- Jenkins Vulnerability Reported: CVE-2024-23897 has been reported as an infection vector for ransomware groups such as RansomExx and IntelBroker. The Jenkins vulnerability is a path traversal issue. Attackers exploit it to read files from the affected Jenkins server and perform remote code execution.
- Proton Variant Advances Predecessor’s Capabilities: Zola, a ransomware that’s associated with the Proton family, has emerged with enhanced capabilities; Zola’s keyboard-based kill switch, ChaCha20 encryption scheme, and overwriting of the slack space are key characteristics that illustrate the strain’s evolution. Slack space or disk slack is an unused area of storage space that contains data segments; overwriting disk slack can thwart efforts to recover deleted items.
Top 10 Ransomware Families
Bitdefender's Threat Debrief analyzes data from ransomware leak sites, where attacker groups publicize their claimed number of compromised companies. This approach provides valuable insights into the overall activity of the RaaS market. However, there's a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and might be unreliable. Additionally, this method only captures the number of claimed victims, not the actual financial impact of these attacks.
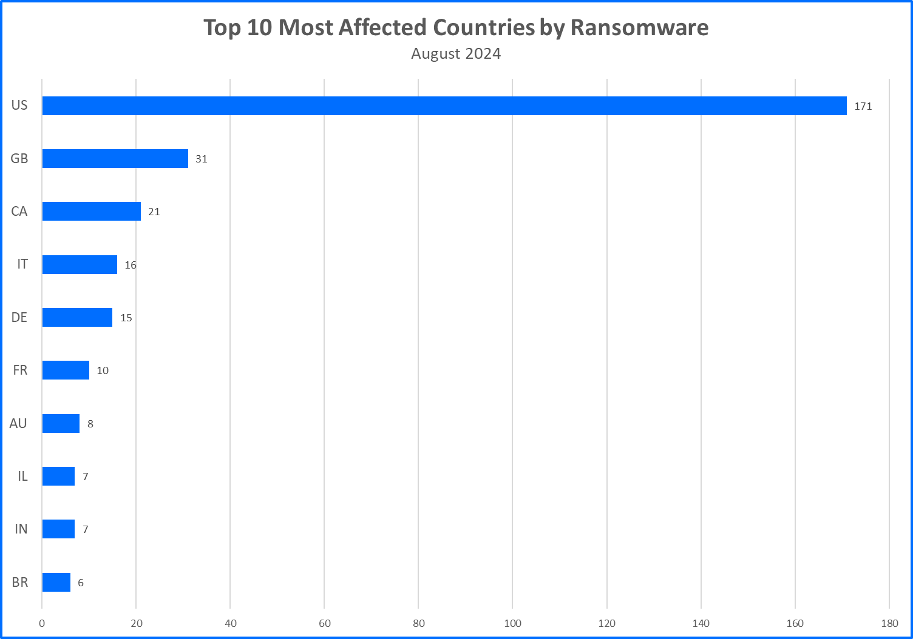
Top 10 Countries
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. This often means focusing on developed countries. Now, let’s see the top 10 countries that took the biggest hit from these attacks.
About Bitdefender Threat Debrief (H2)
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank the Bitdefenders Vlad Craciun, Mihai Leonte, Andrei Mogage, and Rares Radu (sorted alphabetically) for their help with putting this report together.
tags
Author

Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










