Deep Dive into Supply Chain Compromise: Hospitality's Hidden Risks

In today's hospitality industry, vacation rental software has shifted from a luxury to a must-have for hotels, resorts, and smaller businesses, simplifying booking, guest interactions, and property management. While vacation rental software may seem focused on booking, it holds valuable data like credit card info, guest preferences, and communications. This data is a prime target for cybercriminals seeking financial gain or unauthorized access.
Especially attractive is credit card information, which draws the attention of financially motivated hackers, accounting for 41% of hospitality breaches (source: Verizon Data Breach Investigations Report). The combination of the hospitality industry's substantial transaction volume and the integration of payment gateways make it a lucrative target.
Another key characteristic of financially driven attacks targeting payment and financial systems is the attackers' intimate familiarity with the internal workings of the software. Often, these threat actors possess a deep understanding of how systems function and connect, and they are motivated to allocate effort and resources into developing specialized tools. Unsurprisingly, cybercriminals find the idea of generating a steady, repeating income by exploiting payment systems quite interesting.
While significant resources are at the disposal of large hotel networks and travel search engines, enabling them to enforce robust security measures (though recent breaches underscore that this isn't infallible), smaller hotels and resorts face an even more formidable challenge. Custom software is costly and time-consuming, so they opt for third-party solutions from trusted providers. But this reliance introduces a new issue: supply chain vulnerability.
This deep-dive article examines a recent breach targeting a small resort in the United States. The business in question had adopted the IRM Next Generation (“IRM-NG”) online booking engine, a product by Resort Data Processing, Inc. During the investigation by Bitdefender Labs, we discovered a collection of vulnerabilities in this software. In addition, the attack was supported by a suite of tailor-made malware, designed by the threat actor to seamlessly integrate with the software’s architecture. This underscores the threat actor’s intricate understanding of the software’s internal workings and highlights their capacity to exploit its functionalities for extracting sensitive information.
Responsible Disclosure
First and foremost, let’s address the elephant in the room. We have tried reporting the vulnerabilities to Resort Data Processing since May 2023 right after the first vulnerability in IRM-NG software was discovered, but we were unsuccessful. Our initial attempt took the form of emails, but regrettably, our endeavors remained unanswered. Over the ensuing months, we pursued communication with the software vendor through various channels, which included the official bug bounty program, Twitter, or contacts on LinkedIn associated with the company.
Despite our repeated and varied attempts to establish contact, we received no response. Given that the threat actor responsible for the attack demonstrated a deep understanding of the software in use and the discovery of additional compromised victims, we have taken the initiative to allocate CVEs to the identified vulnerabilities. It’s important to clarify that we haven’t attempted a comprehensive evaluation of the security of the IRM-NG engine; rather, we just documented the vulnerabilities encountered during our analysis. This approach leaves room for the possibility that additional vulnerabilities may exist within the software.
Below is a list of CVEs assigned to identified vulnerabilities:
- CVE-2023-39420 - Use of Hard-coded Credentials in dll (CWE-798)
- CVE-2023-39421 - Use of Hard-coded Credentials in dll (CWE-798)
- CVE-2023-39422 - Use of Hard-coded Credentials in /irmdata/api/ endpoints (CWE-798)
- CVE-2023-39423 - Improper Neutralization of Special Elements used in an SQL Command in dll (CWE-89)
- CVE-2023-39424 - Improper Neutralization of Special Elements in Output Used by a Downstream Component ('Injection') in dll (CWE-74)
Anatomy of an attack
Based on our analysis, this attack began during the summer of 2022. One of the tools' PE headers further supports this timeline, indicating a compilation time of 2022-07-11 12:49:31. As a defense evasion tactic, the threat actor employed timestomping to seamlessly blend with other legitimate files within the same folder. Timestomping is a technique that involves altering the timestamps of files on a computer system to manipulate their creation, modification, or access times. This is done to deceive investigators, obscure malicious activities, and create confusion regarding the timeline of events. As an example of this technique, the malicious file wow64log.dll matches the timestamps of the legitimate file wow64win.dll (both in the C:\Windows\System32 folder).
While we cannot definitively pinpoint the specific threat actor group behind the attack, we can confirm that the attack's primary objective revolves around financial gain and the illicit acquisition of personal information. The IRM-NG engine was implicated in a security breach in 2021; due to the limited availability of publicly available information about this incident, we are unable to ascertain any direct link to the attacks that we analyzed. During our investigation, we identified similar webshell infections among several other victims who were also utilizing the same booking engine. However, the confirmation or negation of the XModule component's usage in these attacks remains inconclusive.
Initial compromise
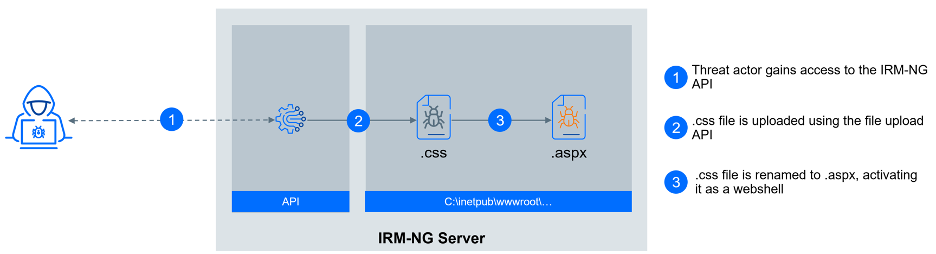
Although we were unable to confirm the precise initial attack vector, we hold a strong conviction that it was connected to an undisclosed vulnerability within the booking engine. The threat actor first uploaded a file index.css (containing webshell code), exploiting that .css extension is allowed by the file-uploading API. As the next step, the threat actor used an undisclosed vulnerability to change the extension of this file to .aspx. This change in extension allowed the file to be executed within the ASP.NET framework, enabling its functionality as a webshell.
cmd.exe /c rename c:\\inetpub\\wwwroot\\rdprepository\\irm\\content\\<SERVER>\\<RESORT>\\index.css index.aspx
cmd.exe /c rename c:\\inetpub\\wwwroot\\rdprepository\\irm\\content\\<SERVER>\\<RESORT>\\index.css index2.aspx
This location further underscores the exploitation of a vulnerability within the booking engine, as this is the default upload path for management users logged onto a designated server.
An additional tool deployed by the threat actor on the compromised server was ConsoleApplication5.exe. This custom-made tool was specifically crafted to run PSQL queries on the database, utilizing Pervasive PSQL, which is the relational database system used by the booking engine. Notably, this database is not password protected.
This tool was initially used to remove traces of the initial login. Significantly, this specialized tool was put into action within a mere 18 minutes after the initial breach. This strongly suggests that the threat actor possessed previous knowledge of the system.
c:\\windows\\system32\\cmd.exe /c cd "C:\\Users\\<USERNAME>\\XRM\\Files\\" && dir && ConsoleApplication5.exe <SERVER> <DATABASE> "DELETE FROM Logins WHERE Browser='Firefox94'"
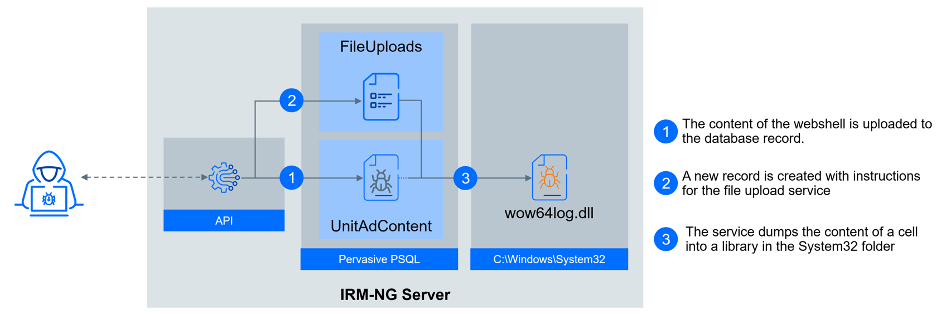
The same tool was used to deploy malware to a secure path C:\Windows\System32. To begin, the threat actor took advantage of an unknown vulnerability or content management interface to upload the malicious code to a separate table named UnitAdContent, storing it within a row marked by a PropertyName value of '333333333333333333333333333333'. With the code now stored in this record, the next step for the threat actors was to save this file in a protected path.
For this purpose, the threat actor used a vulnerability within an "RDPng File Upload" service operating at the SYSTEM level. This service employs a table named FileUploads to store instructions for file uploads. The threat actor inserted a new record into this table, specifying their intention to create a file named wow64log.dll. The content of this file was to be derived from the value stored in the UnitAdContent table. Upon adding this instruction to the database, the file upload service executed the directive, successfully generating the requested file. This file was an installer for a custom version of Micro Backdoor.
c:\\windows\\system32\\cmd.exe /c cd "C:\\Users\\<USERNAME>\\XRM\\Files\\" && dir && ConsoleApplication5.exe <SERVER> <DATABASE> "INSERT INTO FileUploads (FileName,File,Action,Location,DateEntered) VALUES ('wow64log.dll','41',0,'c:\\inetpub\\wwwroot\\rdprepository\\irm\\content\\<SERVER>\\<RESORT>\\..\\..\\..\\..\\..\\..\\..\\..\\windows\\system32\\',now());UPDATE FileUploads SET File=(SELECT CAST(Description as char(5120)) FROM UnitAdContent WHERE PropertyName='333333333333333333333333333333') Where FileName='wow64log.dll'"
To enter the database or authenticate with APIs, we discovered a collection of hardcoded credentials within different libraries. Some of these credentials relied on passwords that are reset daily, yet these passwords can be readily generated by analyzing one of the DLL libraries. Although we have chosen not to disclose sensitive details within our research, it's important to highlight that the threat actor was already aware of this.
The threat actor employed additional tools to escalate privileges. One of these was the widely recognized PrintSpoofer (though packed with Themida to make analysis and detection more challenging), and another was a proof-of-concept tool for CVE-2020-0787 to copy files to a protection location. This POC was a customized variant of the one available in this repository. Another tool that the threat actor used for defense evasion was a process ghosting tool named KingHamlet.
Establishing persistence
For persistence, the attackers used a scheduled task named ChkUpd that runs as SYSTEM. This task executes the following command line: C:\Windows\system32\rundll32.exe batchd.dll,ResChkUpd. The very small DLL file batchd.dll executes a batch file (C:\irmsetup\install.bat) that deploys malicious components:
copy "C:\Users\All Users\XRM\Data\api.dll" C:\windows\system32\logapi64.dll
copy "C:\Users\All Users\XRM\Data\wow.dll" C:\windows\system32\wow64log.dll
copy "C:\Users\All Users\XRM\Data\x.config" C:\inetpub\wwwroot\web.config
copy "C:\Users\All Users\XRM\Data\i.dat" C:\inetpub\wwwroot\rdprepository\irm\content\<SERVER>\<RESORT>\index.aspx
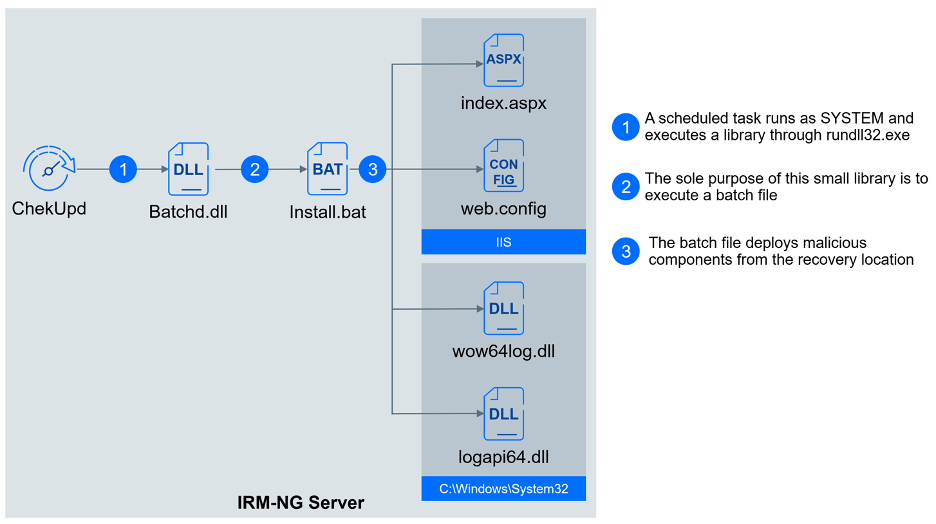
While the file index.aspx is just a regular webshell, the other three files constitute the heart of this operation.
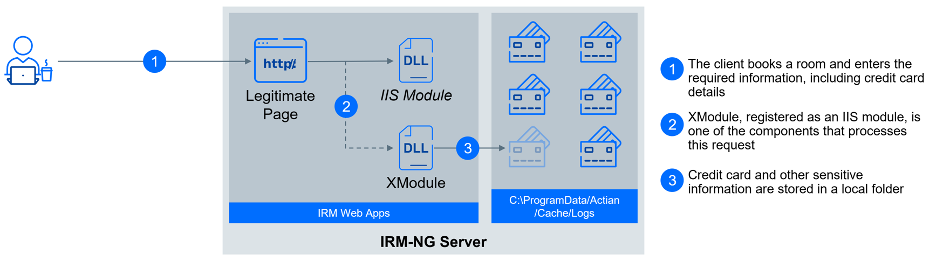
First, the file web.config provides integration with the IIS. This file plays a crucial role in configuring settings and behaviors of an IIS server, such as authentication, security, URL rewriting, and caching, impacting how IIS modules interact with the hosted application. Using this web.config file allowed the threat actor to inject a malicious IIS module called XModule.
While a detailed description of this module will be provided in the subsequent "Execution" section, we wanted to describe its connection to establishing persistence. The XModule is automatically loaded by IIS, initiating the loading of the wow64log.dll library. This installer, in turn, creates a service responsible for loading the Micro Backdoor library logapi64.dll. This service can be configured to utilize either network communication (C:\\windows\\system32\\svchost.exe -k netsvcr) or named pipes (C:\\windows\\system32\\svchost.exe -k netsvcp) as a communication channel between XModule and Micro Backdoor.
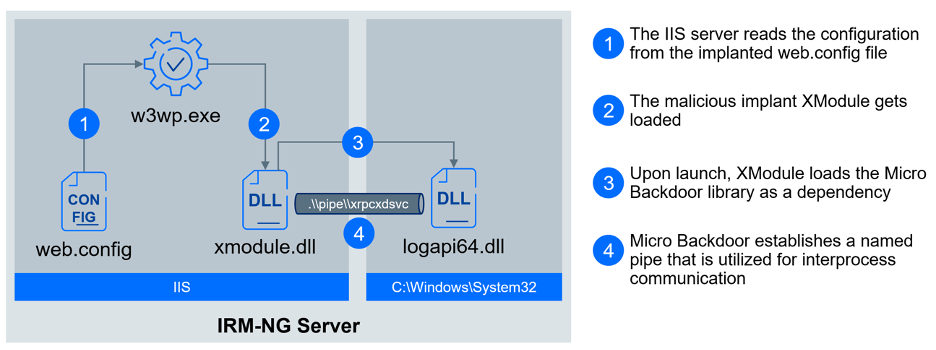
At this moment, all essential components are present and operational. XModule is loaded by IIS and can intercept requests directed at the booking engine, while Micro Backdoor is up and running, prepared to handle instructions from XModule.
Execution
The IIS module XModule is integrated into the flow of the booking engine, actively monitoring all incoming and outgoing traffic to intercept valuable information or receive commands from threat actor. This is achieved by implementing a handler for OnSendResponse event with medium priority.
When an IIS module implements a handler for the OnSendResponse event, it means that the module is designed to intercept the response generated by the web server before it is sent back to the client's browser. This allows the module to inject additional content, modify headers, or perform other actions on the response data.
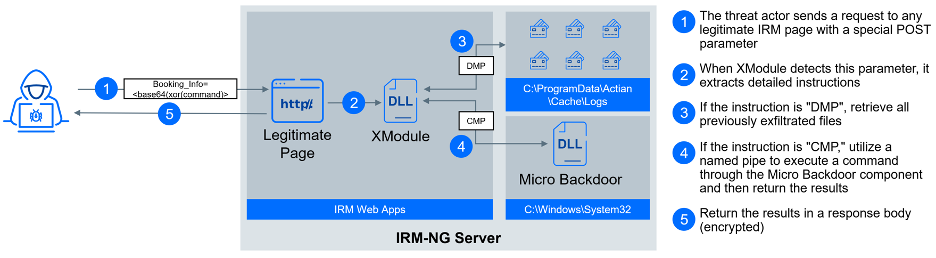
The second component is Micro Backdoor. Micro Backdoor is a minimalistic backdoor for Windows operating systems, designed to be easily customizable. This is exactly how the threat actor used this malware with a small footprint. The customized version does not directly communicate with the command & control (C2) server - instead, it uses a named pipe (\\\\.\\pipe\\xrpcxdsvc) to communicate with XModule. Named pipes are a type of interprocess communication (IPC) mechanism used for communication between processes or applications on a computer system. XModule effectively acts as a proxy between the C2 server telecomptd[.]org and Micro Backdoor, making it much harder to detect, since there is no network traffic.
When the threat actor wants to collect extracted data or send commands to the backdoor, they make a POST request with specific content to any legitimate page on the compromised web server. The XModule intercepts this request, decrypts and processes the embedded instructions, and reports results in the response body. This is an almost undetectable method of communication.
For data extraction, XModule stores intercepted data in the location C:\ProgramData\Actian\Cache\Logs, with a file prefix identifying the type of exfiltrated data.
If the request is GET and the URL contains /irmng/polyfills-es2015 string (this is a .js file used by IRM-NG booking engine), XModule will inject a malicious JavaScript that will set a cookie named __gglmap. This cookie stores the following information: firstname, lastname, address1, address2, city, state, country, postal code, email, card holder, card number, CVV, expiration month & year, billing zip and other data identified by elements with the following IDs (that we couldn't identify): "tc91", "tc90", "tc92", "tc93", "tc94", "tc95". If this cookie __gglmap later appears in the headers, the XModule will save its value (encrypted using a simple XOR) in a file named error_<year><month><day>_<crc32_of_cookie_value>.dmp.
If the request is POST, the action depends on the body of the request.
If the request body contains passwords (one of the strings "password", "pass", "pwd" is present), the body is written (encrypted) into a file named info_<year><month><day>_<crc32_of_body>.dmp.
If the request body contains credit card information (one of the strings "cvv", "cvc", "cardnumber", "cardholder", "ccnum", "cc_num", "i4g0", "tenerum" is present), the body is written (encrypted) in a file named dump_<year><month><day>_<crc32_of_body>.dmp.
Finally, if the request body contains paramers Module=BookData&Booking_ID= and &Booking_Info=, XModule will interpret the value of the Booking_Info as a command. The command is base64 encoded and encrypted with a simple XOR. The XModule (or Micro Backdoor) executes the command and returns the result in the response body (encrypted).
This command can be one of the following:
- PIN - responds with "PONG”
- INF - responds with <username>|<computer_name>|<user_is_admin>|<integrity_level>
- CMD - a command that is executed using exe /c (or %COMSPEC%)
- CMP - a command for the Micro Backdoor (using a named pipe)
- DMP - initiate data exfiltration, appends the content of all the files in C:\ProgramData\Actian\Cache\Logs folder to the response body
Conclusion and recommendations
The investigation has revealed a series of security breaches within a booking engine software that have been orchestrated by a sophisticated threat actor. This incident appears to be part of a larger, coordinated effort, as the attacker demonstrated an intimate knowledge of the software's architecture and inner workings. The threat actor went beyond conventional attack methods by developing custom malware designed to seamlessly integrate with legitimate network traffic, facilitating the covert exfiltration of sensitive data. Threat actors, like everyone else, aim to maximize their gains while minimizing effort. They're willing to invest time and resources in crafting custom attacks if it leads to a consistent income.
Larger companies have the capacity and responsibility to conduct routine security audits and penetration testing, a luxury that might not be feasible for smaller businesses – a demographic often served by third-party solutions. For these smaller enterprises, focusing on the security maturity of their supply chain becomes paramount. It's essential to recognize that opting for seemingly more affordable solutions can sometimes lead to unforeseen, substantial expenses due to security breaches or vulnerabilities.
The best protection that businesses can deploy against modern attacks remains the defense-in-depth architecture. This approach involves employing multiple layers of overlapping security measures that are designed to protect against a variety of threats.
The first step in adopting a multi-layered strategy is mastering prevention capabilities. Try to limit the exposed attack surface and minimize the number of entry points that threat actors can use. Identify and correct weaknesses by implementing patch and risk management solutions before threat actors can exploit them.
Automated protection controls are deployed to all potential entry points exposed to threat actors (including work-from-home laptops for roaming employees). This includes next-generation antivirus, but also seamlessly integrated IP/URL/Domain reputation, and protection against previously unknown threats. This gives you the capability to detect and block most security incidents before they can do any harm.
Despite your best efforts, it is still possible that modern threat actors will make it past your prevention and protection controls. This is where your detection and response capabilities come into play. Whether you get these capabilities as-a-product (EDR/XDR) or as-a-service (MDR), the purpose is to minimize the time when threat actors remain undetected. Bitdefender MDR team conducts a proactive search through an environment to hunt malicious, suspicious, or risky activities that have evaded detection by existing tools.
In conclusion, the investigation underscores the need for a multi-layered and adaptive security strategy. By combining technological enhancements with vigilant monitoring and proactive measures, organizations can better defend against sophisticated threat actors targeting critical software systems.
We would like to thank Adrian Schipor, Victor Vrabie, Cristina Vatamanu, Alexandru Maximciuc and Bogdan “Bob” Botezatu for help with putting this advisory report together.
The full research paper, published by Bitdefender Labs, contains additional details and technical insights.
Indicators of Compromise
An up-to-date and complete list of indicators of compromise is available to Bitdefender Advanced Threat Intelligence users. The currently known indicators of compromise can be found in the table below.
XModule
|
File Path |
MD5 |
|
%PROFILES%\\<PROFILE>\\desktop\\urlmodz.dll |
cb911c01d89b3a35bb3a7f525021b609 |
|
c:\\temp\\test_regmodule.dll |
504a54e53727d418003d7b71647f6230 |
|
c:\\temp\\test_regmodule.dll |
87397cdbf0e62dd422dfcd0c54b39710 |
|
c:\\temp\\test_regmodule.dll |
07c7dffc9237373eeca170cc332e5ee0 |
|
c:\\temp\\test_regmodule.dll |
5955f14160bb8aacc63f620065317c2c |
|
c:\\temp\\test_regmodule.dll |
3411c97b2017c5a60bacbae722afa9e3 |
|
c:\\temp\\test_regmodule.dll |
58e200a60c8329058bb7e63118e6ce3f |
|
c:\\temp\\test_regmodule.dll |
225fee186de514e1a24536a95bfa118d |
|
c:\\temp\\test_regmodule.dll |
1d6554842dc48fd87b83113318e9256d |
|
c:\\temp\\test_regmodule.dll |
f74271e58d20f42be4bf2a685c78217d |
|
c:\\temp\\test_regmodule.dll |
a1d80427445b6db77daa39dfb89d3c2f |
|
c:\\temp\\test_regmodule.dll |
d98ef3e72ed8cac642a51498ff67c3b0 |
|
c:\\temp\\test_regmodule.dll |
ce7fde78cb3d3fa08e053d8a6ccdb931 |
|
c:\\temp\\test_regmodule.upx.dll |
284e2bef6bec53942442a80daa3ab56d |
|
c:\\temp\\test_regmodule.dll |
91f0ba3999e7d368b294f8dd2b326865 |
|
c:\\temp\\test_regmodule.dll |
3ee42bc3f765c8ac7e0708641fab4e9e |
|
c:\\temp\\test_regmodule.dll |
063588bfda9642c835b5a2bcfedaf1da |
|
c:\\temp\\xmodule.dll |
ac7cdd4d1d08f74a7f9c56b760aa991b |
|
c:\\temp\\xmodule.dll |
b487e7bfd88aa57ccbf47568055f47da |
|
c:\\temp\\xmodule.dll |
a92e0651bc8fef306ecbe992351d311f |
|
c:\\temp\\xmodule.dll |
adecf847a06fb12589e92c522f59473f |
|
c:\\temp\\xmodule.dll |
800294f84f61830b79577d241ef6c7df |
|
c:\\temp\\xmodule.dll |
8f39d5df4c38c2b90e5b9b091458eed7 |
|
c:\\temp\\xmodule.dll |
61cac5c66aaba9f896da026bb2a7c899 |
|
c:\\temp\\xmodule.dll |
c453f876e25c8a04d9cde58f9290c88f |
|
c:\\temp\\xmodule.dll |
b1703ed5441ac3fb5004a37722e14b22 |
|
c:\\temp\\xmodule.dll |
89c283604857ea44ef8d0bc109d53a73 |
|
c:\\temp\\xm32.dll |
3b15d7a3e9eea9c403ddc4e74fd329aa |
|
c:\\temp\\xmodule.dll |
450d4c982490350082ca3dc89a0e8ee2 |
|
c:\\temp\\xmodule.dll |
05b0418263ac7ab3431f2329d0d3e2b0 |
|
c:\\temp\\xmodule.dll |
bdbeb4dd064cc30a3c02cfb1ea0e5dc8 |
|
c:\\temp\\zxmod33.dll |
366f6e5b7db3c0ef0eaa8776ae7ade24 |
|
c:\\temp\\xmodule.dll |
953ccf89d1452a7142a1d3970219ed8a |
|
c:\\temp\\xmodule.dll |
c0ba71922ba520ad479f4b77d6e70688 |
|
c:\\temp\\xmodule32.dll |
871de9bf5a4fdfa5e448f47a14259335 |
|
c:\\temp\\xmodule.dll |
adcc2d68a2d7c5e830be550890efd42b |
|
c:\\windows\\system32\\inetsrv\\issrpch64.dll |
d5373e33861c09697af6c62987983321 |
|
c:\\windows\\system32\\inetsrv\\issrpch.dll |
24d7baab665b51719aca24718e3d0115 |
|
c:\\windows\\syswow64\\inetsrv\\urlmodz.dll |
cb911c01d89b3a35bb3a7f525021b609 |
Micro Backdoor
|
File Path |
MD5 |
|
c:\\windows\\syswow64\\logapi64.dll |
e919e2ca19daa40904000a3222963b21 |
|
c:\\windows\\system32\\logapi64.dll |
e919e2ca19daa40904000a3222963b21 |
Micro Backdoor Installer
|
File Path |
MD5 |
|
C:\\Windows\\System32\\wow64logf.dll |
6d85ea5b1d88aadd43fec8a53662c0ad |
|
C:\\Windows\\System32\\wow64log.dll |
6d85ea5b1d88aadd43fec8a53662c0ad |
Persistence
|
File Path |
MD5 |
|
c:\\windows\\system32\\batchd.dll |
12f2a5faa01efcee7a0829133173da2b |
|
c:\\irmsetup\\install.bat |
fc45969de0677b995bfbc829906871f5 |
Privilege escalation & defense evasion
|
File Path |
MD5 |
|
c:\\temp\\tmp\\uninstall_2.exe |
bfea2b4a02a8044cb5f7fccc36172460 |
|
c:\\temp\\tmp\\procghost.exe |
4912f690fc30bb2217d1b1f3029003fe |
|
c:\\temp\\tmp\\bitsarbitraryfilemoveexploit.exe |
582862be0c3bdda4f65376169c57af98 |
Webshells
|
File Path |
MD5 |
|
c:\\inetpub\\wwwroot\\rdprepository\\irm\\content\\<SERVER>\\<RESORT>\\eval_full_fud.aspx |
7efc7f94cbbc3e1d38873039996efe64 |
|
c:\\inetpub\\wwwroot\\rdprepository\\irm\\content\\<SERVER>\\<RESORT>\\eval_full_fud.aspx |
714f7493b7eb384f3ef7a49b73f8c66f |
|
c:\\inetpub\\wwwroot\\rdprepository\\irm\\content\\index.aspx |
9cf1bbd0d83d5701aebdba6e05f7bb93 |
|
c:\\inetpub\\wwwroot\\irmcms\\custom\\31pip2pi.m3i |
9cf1bbd0d83d5701aebdba6e05f7bb93 |
|
c:\\inetpub\\wwwroot\\irmcms\\custom\\pcnlgjs1.rcc |
9cf1bbd0d83d5701aebdba6e05f7bb93 |
|
c:\\inetpub\\wwwroot\\rdprepository\\irm\\content\\<SERVER>\\<RESORT>\\index.aspx |
45ff3ba7c1ebc1db28d4438691b13bea |
|
c:\\programdata\\xrm\\data\\i.dat |
45ff3ba7c1ebc1db28d4438691b13bea |
Custom PSQL Tool
|
File Path |
MD5 |
|
C:\\ProgramData\\xrm\\files\\consoleapplication5.exe |
5db5a373b1395d9f6aeb87f99e8a801c |
Domains
telecomptd[.]org
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











