Healthcare Cybersecurity (Part II) - Pernicious Threats and Their Ripple Effects

Cooperation between health professionals and IT staff has never been more important. The data shows it and real-life crises healthcare organizations go through prove it.
What makes healthcare such a high-value target for cybercriminals?
You’ll find the reasons are a lot more nuanced - and even surprising - than you may think.
Industry profile
Healthcare has gone through many changes over the last decade and the main one is driven by technology. As medtech has evolved, hospitals and medical practices invested in upgrading their equipment to improve diagnostics, speed, and results in patient care.
However, security spending was bumped further down the list, even as vulnerabilities piled on with new tech becoming part of the ecosystem. That’s because security wasn’t directly tied to outcomes in patient care until a few years ago.
What’s more, because of the urgency of health professionals’ work, there was never enough time to dedicate to cybersecurity education. More often than not, there still isn’t.
52%
of surveyed organizations agreed that lack of employee awareness and training affects their ability to achieve a strong security posture (2018 Impact of Cyber Insecurity on Healthcare Organizations).
Cybersecurity healthcare jobs are also difficult to fill. The ISACA State of Cyber Security 2019 report reveals that:
|
27% of healthcare organizations are unable to find suitable candidates |
14% of healthcare organizations are unsure they’ll be able to fill vacant positions |
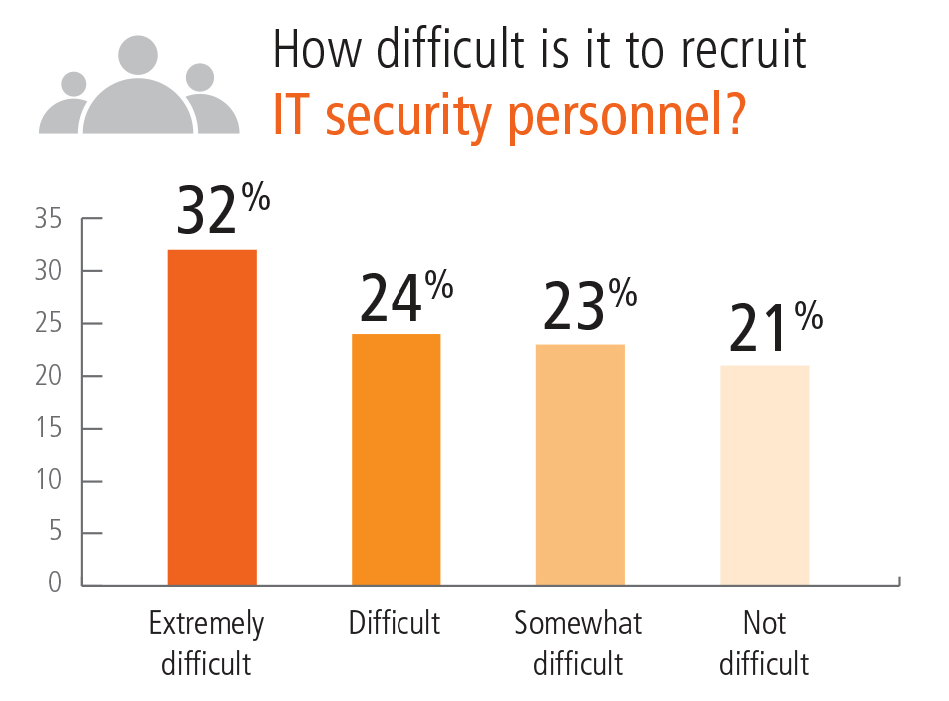
2018 Impact of Cyber Insecurity on Healthcare Organizations
The consequences of this chronic lack of investment in cybersecurity are today’s widespread issues. We’re now at a point where the risk can no longer be ignored.
Environment complexity
The increasing complexity of IT environments places healthcare security decision-makers in a difficult position. They must find a way to secure their infrastructures against multiplying attack vectors while using roughly the same resources.
The range of connected medical devices, systems & applications in healthcare
Devices
- Desktops
- Servers
- Smartphones
- Tablets
- BYOD
- Self-service kiosks
- mHealth systems
- Specialized medical equipment
- Bedside computer terminals
- Bedside medication verification
- Medical imaging devices
- Implantable medical devices (IMD), etc.
- IoMT (Internet of Medical Things)
“Medical technology (medtech) companies manufacture more than 500,000 different types of medical devices, including wearable external medical devices (skin patches, insulin pumps and blood glucose monitors), implanted medical devices (pacemakers and implantable cardioverter-defibrillator devices) and stationary medical devices (home monitoring devices, connected imaging devices and scanning machines).“
Medtech and the Internet of Medical Things, Deloitte Center for Health Solutions
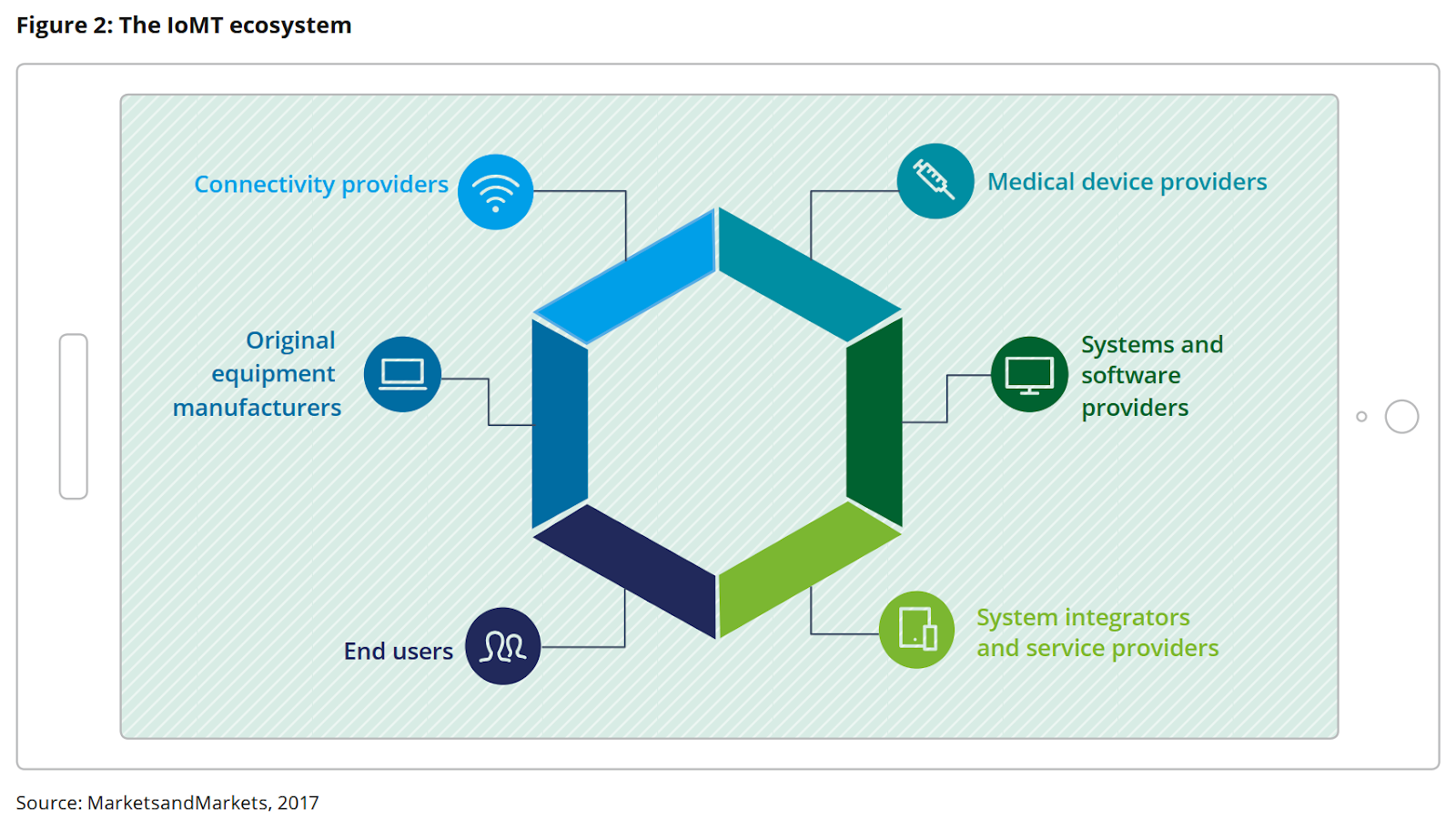
Medical software
- EHR/EMR systems
- Medical practice management software
- PACS (Picture Archiving & Communication Systems)
- Patient Data Management Systems
- Patient scheduling systems
- ePrescription applications
- Telemedicine platforms
- Patient portals
- Medical billing systems with/without online payment
- Third-party clinical systems integrations
- Real-time locating services for tracking systems for instruments, devices & clinical staff
IT infrastructure
- VDI (Virtual Desktop Infrastructure), public cloud or multi-cloud deployments
- On-premises data centers
- Hybrid infrastructures
- Legacy systems
- Internal networks connecting all devices, cloud deployments & medical equipment
What’s more, it’s not just internal systems that IT and security professionals must keep safe and compliant. Third-party service providers also introduce security risks in healthcare organizations.
In 2018, 42% of all exposed/stolen records resulted from business associate data breaches.
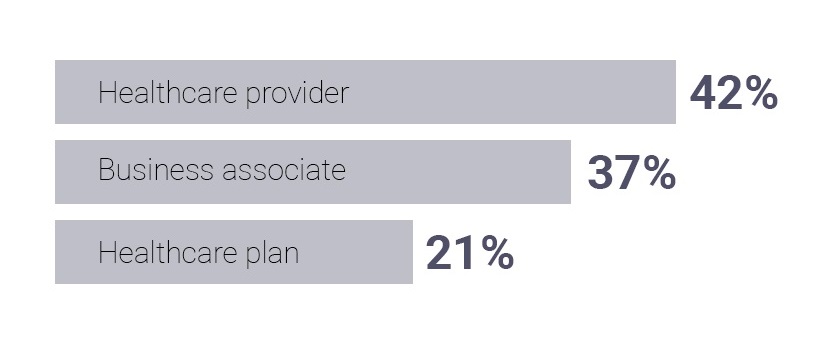
Although they cannot control business partners’ security, there’s a lot healthcare organizations can do to minimize their risk of being breached.
It’s blatantly obvious that the attack surface in healthcare organizations is expanding exponentially.
With such a huge volume of data traveling across devices, channels, and platforms, keeping tabs on everything can be overwhelming. From specialized connected medical devices to patient portals, the diversity of assets requires a security setup that can protect them all and maintain visibility across this complex, vital ecosystem.
Risk profile
Speaking of risk, in healthcare, cyber attacks have different consequences than other industries.
Cybercriminals exploit this by trying to cripple hospitals’ ability to function, forcing them to pay the ransom to resume normal activity. They can also do things like tamper with hospital elevators or encrypt radiology equipment essential for diagnosis.
On top of ransomware attacks, malicious hackers also target health data collection and data management practices. That’s because a single Electronic Health Record (EHR) includes:
|
|
1 Electronic Health Record = $250 on the black market
50x more than credit card details
EHRs are a goldmine because they include a lot of nonperishable and highly valuable information and, for a motivated attacker, they’re also relatively easy to get.
But that’s not all! Cybercriminals are also looking for other types of data:
- Lab results they can use for extortion or identity theft
- Medical licenses to impersonate doctors and forge medical documents
- Health insurance company login details to fraudulently claim health insurance compensation
- Connected medical devices to use for cryptocurrency mining or to hijack the device’s functions
- Administrative paperwork to issue fake health insurance cards, counterfeit prescriptions, and even forge drug labels.
The main attack vector they use to get this data are phishing emails and by exploiting vulnerabilities and misconfigurations in the network.
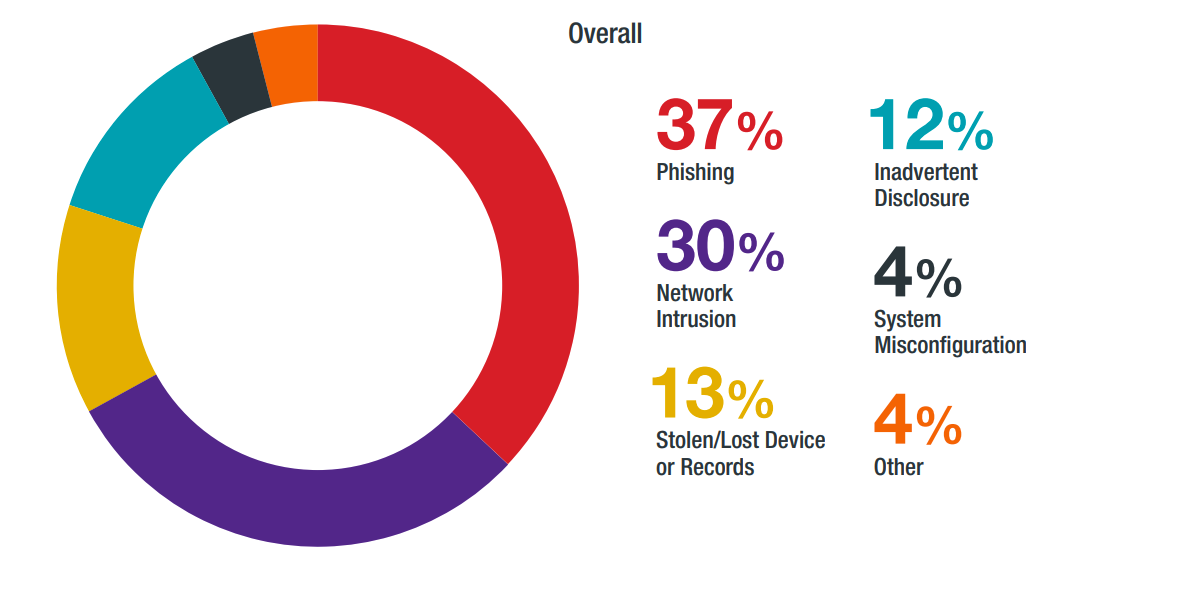
2019 BakerHostetler Data Security Incident Response Report
Once they’re in, most attackers focus on gaining persistent access by compromising email accounts and also moving laterally through the network to harvest valuable data.
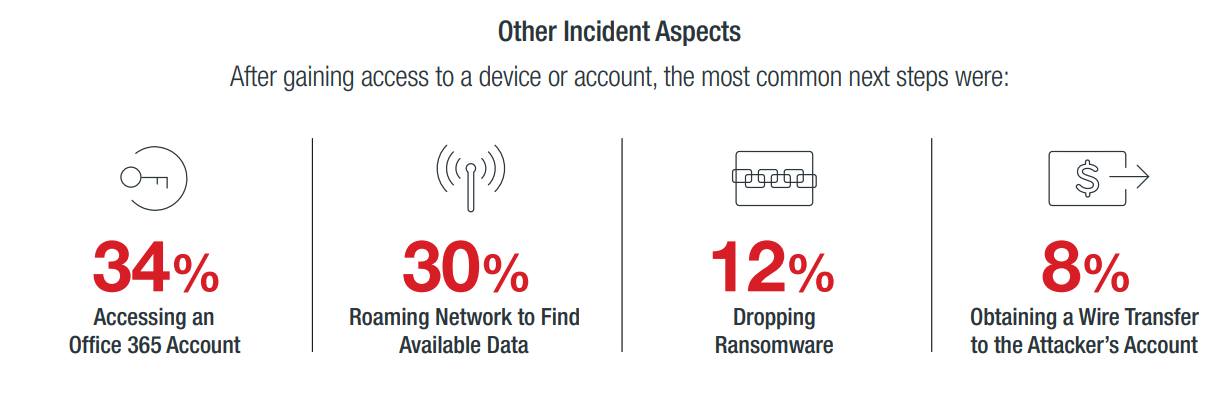
2019 BakerHostetler Data Security Incident Response Report
The technology, processes, and people involved in healthcare paint a very specific risk profile that requires a systemic approach.
Digital transformation
The industry’s digital transformation is also adding layers of complexity and changing workflows. Each change introduced into the organization, from devices to processes, adds new items on security leaders’ agenda.
Let’s take a look at the typical range of components that work together in a healthcare organization in the context of digital transformation.
Benefits vs security risks for healthcare IT infrastructure elements
|
Technology layer |
Healthcare benefits |
Security risks |
|
Specialized medical devices (medical imaging devices, IMDs, etc.) |
|
|
|
BYOD |
|
|
|
IoMT |
|
|
|
mHealth systems |
|
|
|
EHR/EMR systems |
|
|
|
Virtual Desktop Infrastructure |
|
|
|
Hybrid infrastructures |
|
|
While this overview may look burdensome, there’s a great reason to weather the challenges of constant adjustments and improvements. New digital health tools and technology bring fantastic benefits for patients.
Remotely monitored medical devices bridge the geographic divide and improve results with 24/7 availability.
Big data helps surface health trends and identify solutions that help vulnerable patient groups.
Treatments become more personalized, leveraging more of the patient’s current context and medical history.
Doctors and other medical professionals make better decisions based on more data, correlated by faster, smarter algorithms that continue to improve as they learn.
However, to harness the power of digital transformation, IT and security leaders must also secure necessary legacy systems and the transition towards a more integrated approach to healthcare.
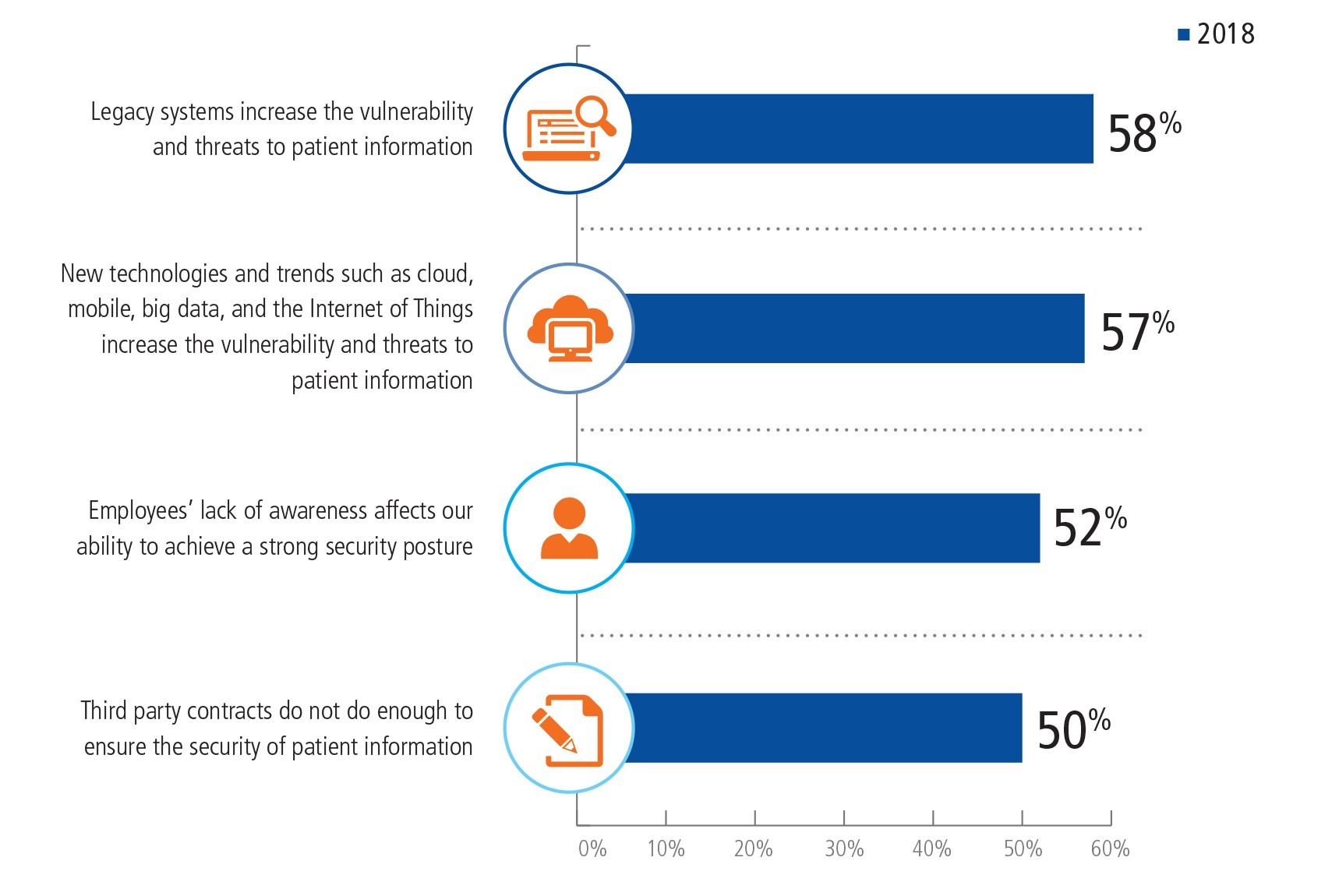 2018 Impact of Cyber Insecurity on Healthcare Organizations
2018 Impact of Cyber Insecurity on Healthcare Organizations
One of the particularities of healthcare security is that specialists responsible for this side of the business must look farther than ever before for the implications of their work. Increased complexity calls for a deeper understanding of the ecosystem, which is why part three of this series is dedicated to putting critical security needs in perspective for healthcare organizations and their role as critical infrastructure.
Suppress cyber attacks targeting medical data with Bitdefender’s industry-leading solutions. Learn more
tags
Author
Bitdefender is a cybersecurity leader delivering best-in-class threat prevention, detection, and response solutions worldwide. Guardian over millions of consumer, enterprise, and government environments, Bitdefender is one of the industry’s most trusted experts for eliminating threats, protecting privacy, digital identity and data, and enabling cyber resilience. With deep investments in research and development, Bitdefender Labs discovers hundreds of new threats each minute and validates billions of threat queries daily. The company has pioneered breakthrough innovations in antimalware, IoT security, behavioral analytics, and artificial intelligence and its technology is licensed by more than 180 of the world’s most recognized technology brands. Founded in 2001, Bitdefender has customers in 170+ countries with offices around the world.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks









