Medusa Ransomware: A Growing Threat with a Bold Online Presence

Medusa is a prominent ransomware group that emerged in 2023. Unlike most ransomware operators, Medusa has established a presence on the surface web, alongside their traditional dark web activities.
In 2024, Medusa continues its campaign, launching cyberattacks at an expedient rate with posts added every few days on published leaks and active ransoms. The group often posts information using a victim name and shame blog, X, and Telegram. While Medusa’s approach to managing their online presence combined with their capabilities have garnered widespread attention, their operational practices leave room for greater scrutiny.
The Medusa Ransomware Malware Family
A search for cyber threats with the name Medusa will return results that include more than one malware family. It’s important to keep in mind that the Medusa ransomware differs from the ransomware known as MedusaLocker. The two groups have unique tactics, techniques, and procedures. Medusa (ransomware) is also distinct from the Medusa Android malware.
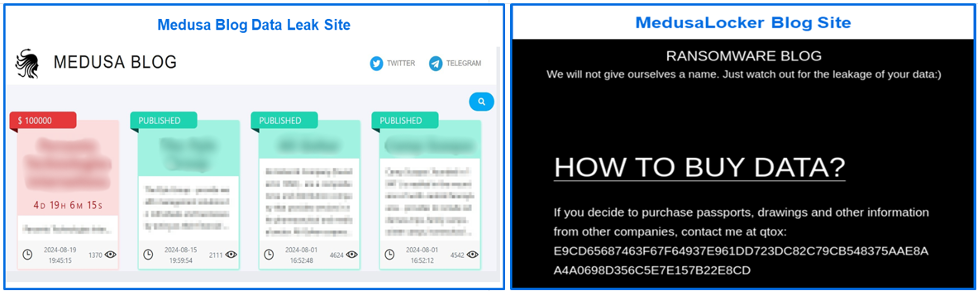
Figure 1: Different Sites - Medusa Blog and MedusaLocker (Ransomware Blog)
Medusa’s Attack Demographics
Medusa manages a ransomware-as-a-service (RaaS) operation that employs a profit-sharing model, where affiliates receive a substantial portion of the ransom payments, while the operator retains a smaller cut.
Medusa is known for attacking sectors that include healthcare, manufacturing, and education. They have also targeted the government and finance sectors. This is an opportunistic threat group that is not restricted to attacking victims from a specific geographic region or interest area. They have launched attacks against organizations based in varying countries, including the United States, Israel, England, Australia, the United Arab Emirates India, Iran, Portugal, and numerous others.
In 2023, Medusa targeted a total of 145 victims. Since then, attacks have persisted. Bitdefender estimates that Medusa will claim over two hundred victims by the end of the 2024 calendar year.
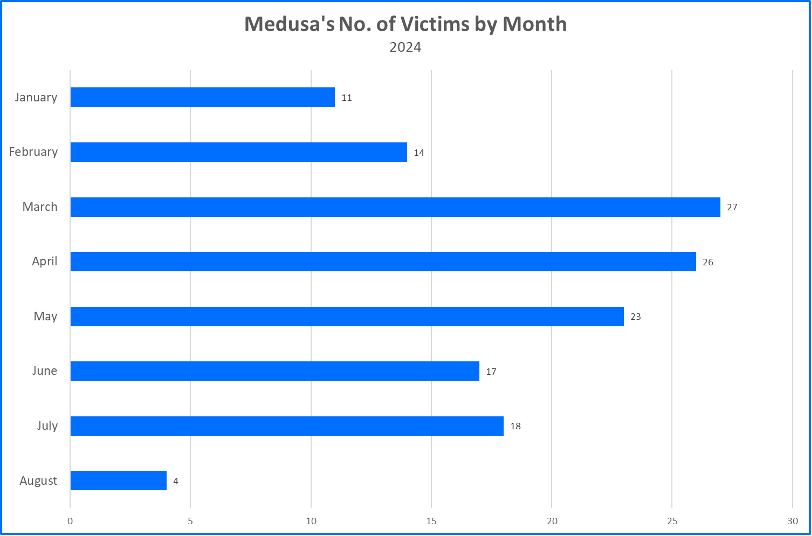
Figure 2: Medusa's No. of Victims by Month: 2024
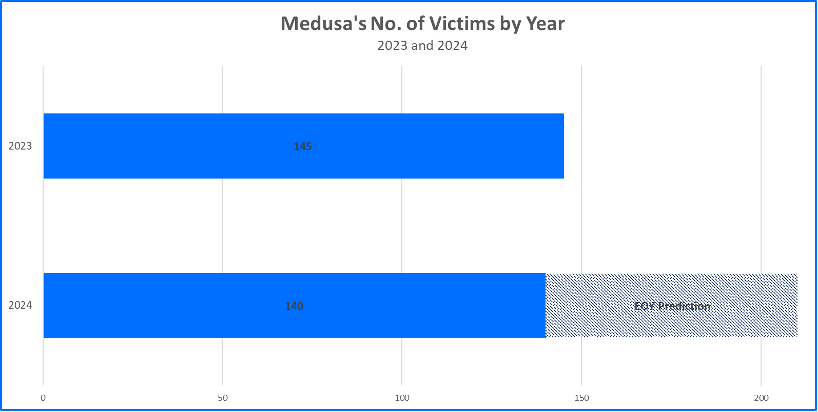
Figure 3: Medusa's No. of Victims by Year: 2023 & 2024
Medusa’s Blog
Medusa has a name and shame blog that is accessible using Tor. Once a user navigates to the site, they complete a captcha to validate entry. The user must re-verify, completing a new CAPTCHA when refreshing the page or if idle. The blog features posts about organizations impacted by their attacks and a summary of the data stolen and/or leaked. Multiple posts from July of 2024 onward have more than 4,000 views.
A countdown timer shows how much time the victim organization has left to contact the group and make a payment. Bitcoin is the required payment method, and the victim can choose from several options: paying to download the stolen data, paying to delete the stolen data, or paying to extend the deadline for ransom.
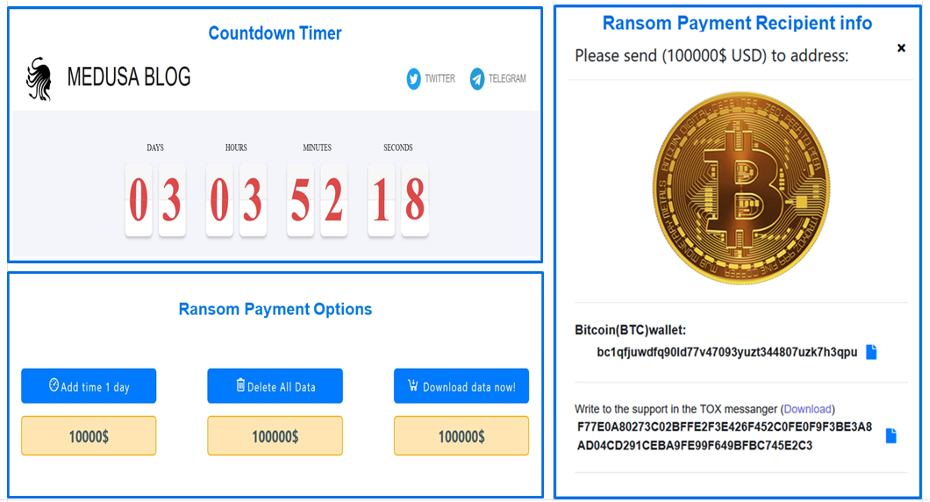
Figure 4: Ransomware countdown timer, payment options, and pay recipient info.
A Blend of Dark Web and Clear Web Activities
Medusa’s online presence is an unusual mix of both dark web and clear web activities. While operating on the dark web is typical for\ ransomware groups, Medusa’s clear web presence, particularly under the ‘OSINT without borders’ identity, is highly unusual.
The 'OSINT Without Borders' identity, along with profiles linked to 'Robert' under various surnames, operates on a dedicated website (osintcorp.net) and social media platforms like X and Facebook. Although Medusa tries to present these entities as separate, numerous connections suggest otherwise. For example, Medusa’s official data leak site links to a Telegram channel that shares the same logo as 'OSINT without borders,' and the site’s owner frequently refers to Medusa in ways that imply a close affiliation.
Medusa’s Connection to OSINT Without Borders
Queries surrounding the ways Medusa communicates with the public continue to draw the attention of cybersecurity analysts and investigative teams. OSINT Without Borders (osintcorp.net) is a blog site that posts information on breaches, leaks, and hacker activities. Several cybersecurity firms have surmised that Medusa’s public relations team runs the site . Medusa could have different objectives for maintaining the OSINT Without Borders site, including pushing content about their leaks and similar attacks, promoting intelligence gathering efforts, and identifying potential targets.
Multiple posts on OSINT Without Borders provide information about downloading data leak content. These posts appear in the Author's Blog section and are accompanied by video reviews. At the end of each data leak review, a disclaimer is displayed stating the following: “I remind you that I am providing all data from the public segment of the Internet solely for the purpose of familiarizing myself with possible information security problems. I am not engaged in illegal activities and I do not advise you. If any data block is unavailable, please let me know in the comments.”
Links to data leak content direct the user to the information support Telegram channel, the same channel linked on the Medusa Blog.
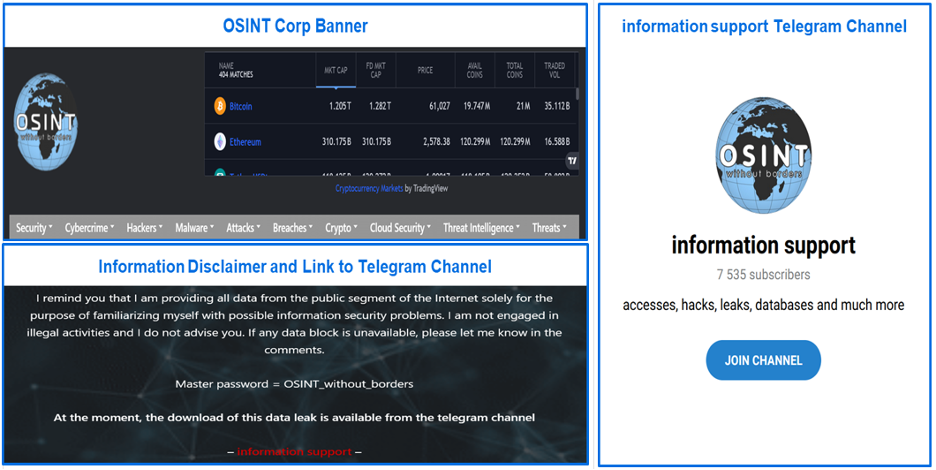
Figure 5: osintcopr.net Banner, Disclaimer, and Telegram Link
Continuing the Link Analysis
While the content on OSINT Without Borders aligns with posts found on other media, including content on Medusa’s data leak site, there are two other active social media accounts that act on behalf of this blog. These accounts include the X account, @osint_with_bord, that’s associated with display name Robert Vroofdown and the OSINTwithoutborder Facebook page associated with the user Robert Enaber.
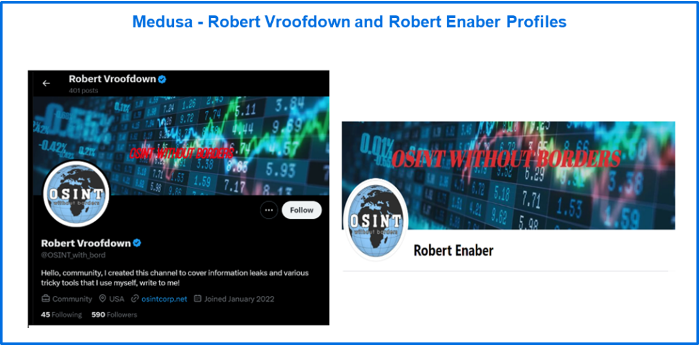
Figure 6: Robert Vroofdown and Robert Enabler profiles.
No information to attribute users of the Robert accounts to a specific city, venue, or partner organization is available. Still, OSINT Without Borders, and by extension Medusa’s use of social media in this manner is unusual and clashes with common conventions on how ransomware groups must operate.
There are also accounts that are no longer active that represent links to Medusa. A user named t0mas from a former OSINT Without Borders site known as osintcopr.uk had an account on BreachedForums; following the site’s takedown by law enforcement, no other connections have been made. A YouTube OSINT Without Borders channel was once active, however, the channel was removed following a user report in 2022.
Medusa’s Use of X and Telegram
Medusa’s blog includes links to X and Telegram. However, the X link does not lead to a dedicated account but instead returns search results for the term 'medusa ransomware,' which also includes references to the group MedusaLocker.
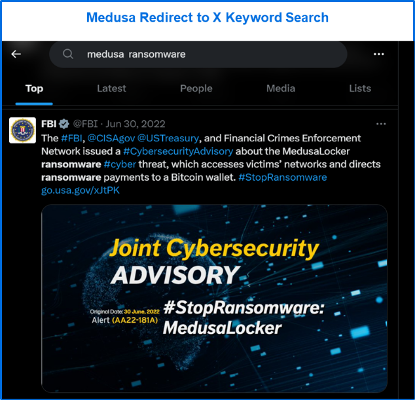
Figure 7: Medusa redirect to X search results.
A Telegram link featured on Medusa’s blog directs users to the information support channel.
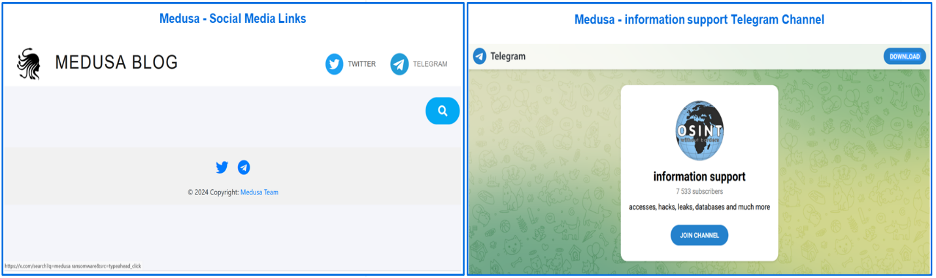
Figure 8: Medusa social media links and Telegram channel.
The information support channel has posts dating back to July 30, 2021, including a mention of a data leak. An announcement by Robert on November 17, 20022 references the release of the site osintcorp.net, a Twitter feed, Facebook page, and Telegram channel. The posts referencing Medusa follow in the weeks after the November 2022 announcement.
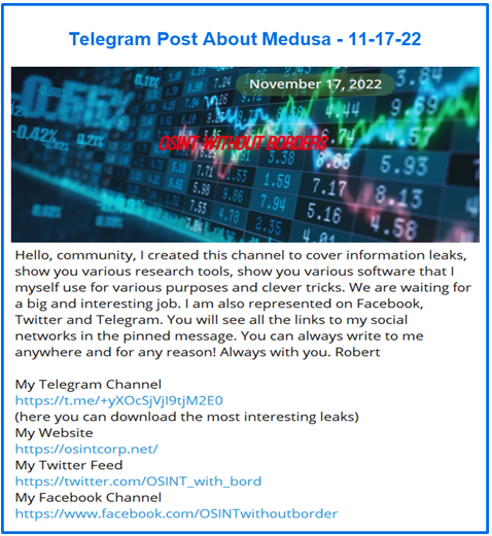
Figure 9: November 2022 information support channel announcement.
Aside from data leaks, Medusa onion links are shared throughout the information support channel. The Telegram channel’s organizer often presents Medusa in a favorable light, referring to the ransomware group as ‘my friend’ and ‘the best team’ in multiple instances. The group is also called a jellyfish, possibly due to the outline of Medusa’s image forming the shape of a creature with tentacles.
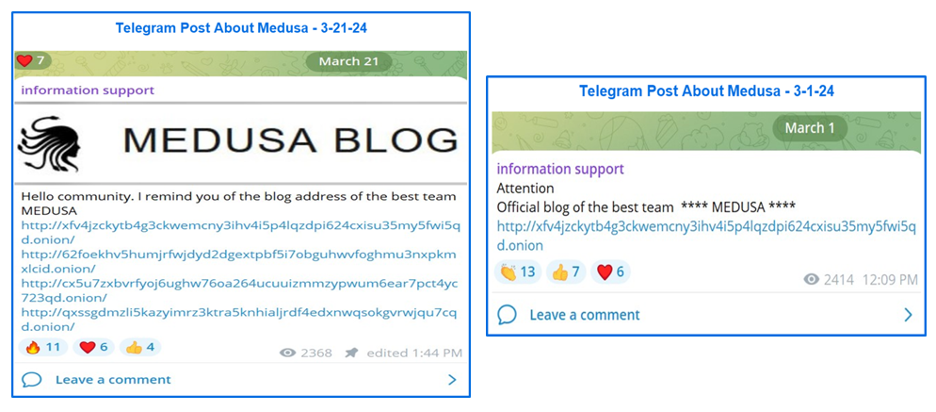
Figure 10: Mentions of 'the best team': Medusa
When examining the use of language by the information support channel organizer, there are unusual instances that indicate a shift in tone or, perhaps the organizer’s attitude towards Medusa. Several posts simply call Medusa ‘My friends from the hacker group’ while others begin with ‘Medusa decided not to be petty and hacked.’ Whether this ‘decided not to be petty’ phrasing is a result of a language proficiency issue or is indicative of a conflict between ransomware group members, frustrations over operations, or other dynamics is unknown.
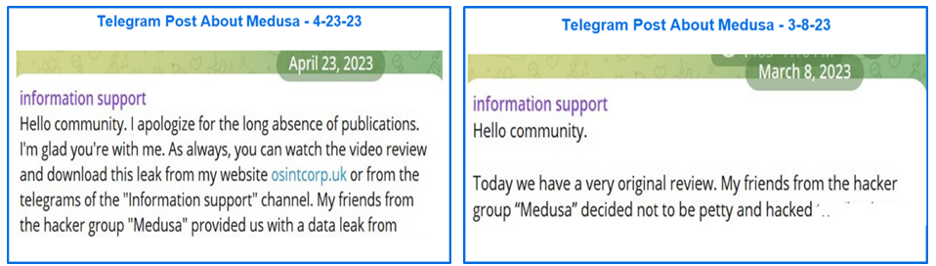
Figure 11: Posts with different language and tone referring to Medusa.
Medusa’s use of Telegram is notable due to its ease of access, overt connections that tie in with osintcorp identities, and ongoing presence. The channel remains active with over 700 shared files.
Risks to Medusa Operations
Communicating about leaked data and victims of ransomware attacks on the clear web is one type of action that may jeopardize the success of an operation. Events such as infiltration by cybersecurity groups can also spell disaster for an operation if there’s information exposure to identify the bad actors and technologies they use.
A recent event uncovered by Dark Atlas in summer of 2024 resulted in Medusa experiencing a major security operations failure. Medusa’s capabilities were reduced once the group’s cloud account became visible and accessible to an unintended group. Dark Atlas, the group who discovered the security gap obtained information from a configuration file on the mechanism needed to authenticate the Medusa account.
Equipped with a put.io token, Dark Atlas was able to set up a web proxy to observe the parameters needed in the authentication process. They input the put.io token from the configuration file as the value needed to complete account authentication. Once access was granted through this authentication process, Dark Atlas could see information about the compromised victims and leaked data; they began taking action to remove victim information.
While this event represents one instance where data and access to Medusa’s resources were compromised, it is a striking example that demonstrates the countermeasures available when a ransomware group’s effective tools fail because of information disclosure.
The Attack Chain
Medusa has received extensive coverage in the news and in cybersecurity forums due to their style of attack. The advanced capabilities mapped to execution and defense evasion highlight how groups like Medusa operate as formidable, evolving threats.
Targeting known vulnerabilities is key for ransomware actors like Medusa to chart their attack path. The diagram below illustrates this tactic, a common practice in ransomware group playbooks.
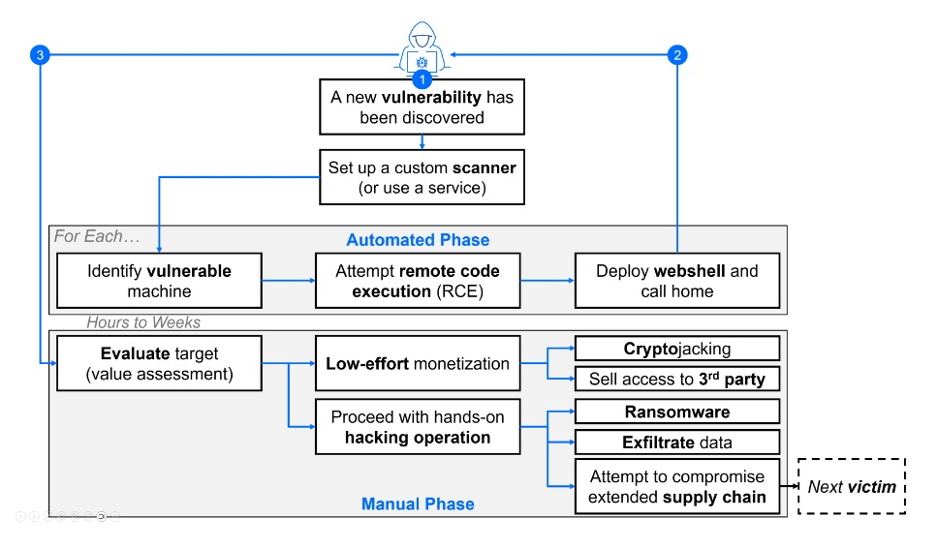
Figure 12: The ransomware attack - from vulnerability discovery to ransomware deployment.
Initial Access
Medusa gains access to a target system through a known weakness such as the Fortinet EMS SQL injection vulnerability. CVE-2023-48788 impacts environments that have FortiClient EMS, versions 7.2 to 7.2.2 and 7.0.1 to 7.0.10, installed to manage endpoints.
The vulnerability allows the attacker to send malicious web requests containing SQL statements. The malicious SQL input is designed to alter the FCTUID parameter that is found in the header section of requests and passed to Fortinet’s FCTDas service. FCTDas is a program that interprets incoming requests that are routed to the SQL server database.
After the FCTUID parameter falls victim to the SQL injection process, allowing the attacker to manipulate application queries, the attacker passes SQL input to issue the xp_cmdshell command. xp_cmdshell is a native component of Microsoft’s SQL Server. When the command is invoked, the attacker performs remote code execution, issuing commands that impact the affected server and connected resources and hosts. Medusa creates a webshell on the exploited server to exchange payloads and host data. This is accomplished using a service such as bitsadmin. The webshell is configured to encrypt and/or conceal traffic.
Persistence
Medusa establishes persistence through several methods. The group employs compromised RMM tools in their campaigns such as ConnectWise, PDQDeploy, and AnyDesk. Medusa uses RMMs that are likely to be whitelisted. The group also completes discovery processes to enumerate applications in the victim environment. The discovery results allow the attacker to validate the types of programs they can introduce to the host, masking their compromised iteration of the program as a legitimate version.
Medusa transfers the compromised program and other payloads to a victim's system via bitsadmin. Since the RMM typically has a trusted installer, once loaded on the victim's system, Medusa continues their attack chain and evades suspicion.
Persistence is also established once PowerShell commands are executed to modify the registry key values on victim hosts like run in HKLM and HKCU to ensure that execution occurs at startup.
Execution
Medusa leverages PowerShell scripts to run commands that affect host systems, exfiltrate data, and reference the executable and binary code needed to launch the ransomware attack and perform encryption. At the execution phase gaze.exe is executed, which kills a multitude of services by issuing the net command. It also loads files that reference TOR links for data exfiltration actions.
Medusa’s ransomware uses asymmetric RSA encryption to encode targeted files and directories which include a copy of Medusa’s ransomware note. The extensions of files in those paths are modified and end in .medusa or mylock; the extensions that reference launching a program, program dependency, or shortcut such as .exe, .dll, or .lnk are usually excluded from the encryption process to ensure that some utilities remain active and functional.
Lateral Movement
Medusa typically obtains credentials as a result of exploiting the vulnerable server and extracting credentials from LSASS. Medusa establishes lateral movement by using bitsadmin to transfer malicious files from their webshell to victim hosts. They can also use other tools, such as PSExec for the same purpose.
Defense Evasion
While common means to counteract a defense or recovery measure such as leveraging WMI to delete backups and volume shadow copies exist, Medusa also has a more sophisticated measure in play. After a malicious version of an RMM is installed on a host, vulnerable drivers are also loaded. The drivers are instrumental in identifying services tied to anti-malware solutions and other security software.
The drivers enumerate active processes, cross-referencing them with a provided list, and stop the specific processes that are a match. One report documents that Sophos endpoint products are impacted by this anti-malware bypass technique. Currently, Medusa’s resources that combat anti-malware detection and other security technologies are capable of killing more than two hundred processes.
Ransom Markers/Datasets
Identifying documentation and information exchanged between the ransomware group, victims, and other affected parties is important to clarify and anticipate their actions. The contents of a Medusa ransomware note are displayed in the following images. It shows that victims are informed on what happened and given the means to contact the ransomware group directly if they wish to restore access to their data and systems and prevent their data from being exposed.
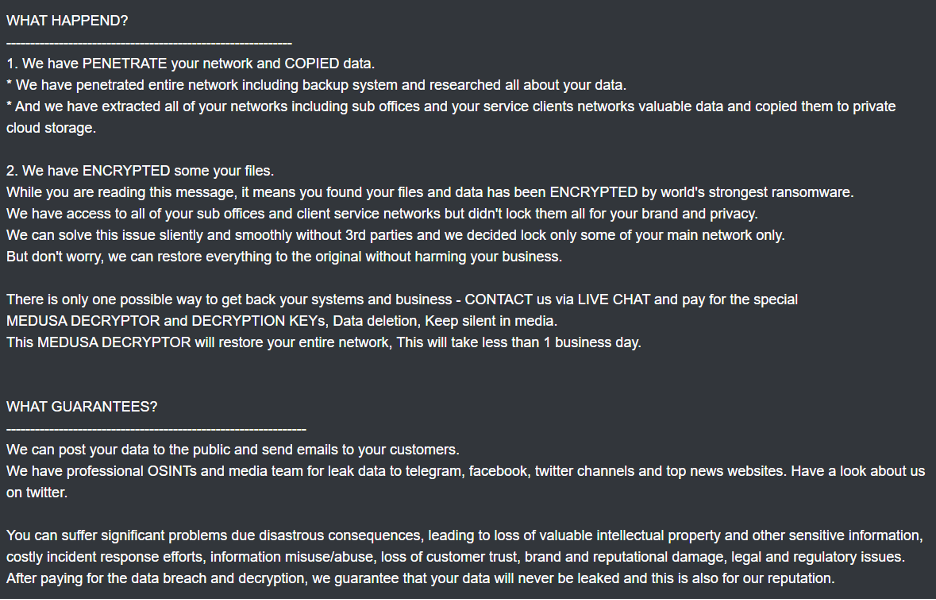
Figure 13: Medusa ransom note excerpt 1.
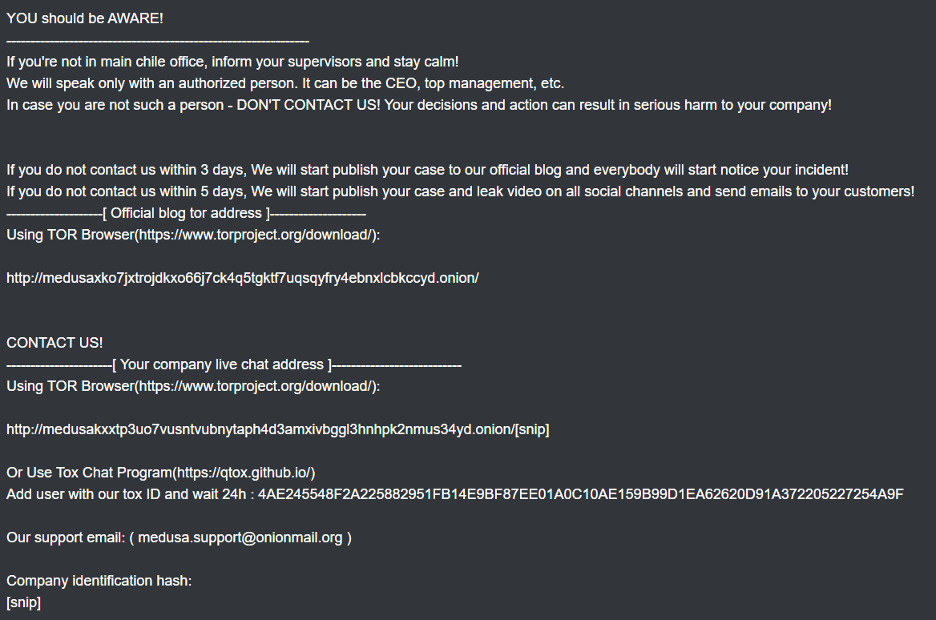
Figure 14: Medusa ransom note excerpt 2.
Conclusion
While Medusa has cultivated an image that has transformed the perceptions associated with ransomware operators and anonymity, recognizing their methods of communication across time along with their current capabilities is crucial to understand the group’s strengths and their recent shortcomings. Medusa has shown growth and versatility and will continue to challenge both investigative analysis and incident response efforts.
Recommendations
There are multilayered strategies that an organization can implement to help guard against a ransomware attack. An organization may incorporate best practices into their security strategy including addressing gaps in prevention, protection, detection, and response security measures.
The right threat intelligence solutions can provide critical insights about attacks. Bitdefender IntelliZone is an easy-to-use solution that consolidates all the knowledge we've gathered regarding cyber threats and the associated threat actors into a single pane of glass for the security analysts, including access to Bitdefender’s next-generation malware analysis service. If you already have an IntelliZone account, you can find additional structured information under Threat IDs that include:
BDtqpfqhza, BD98p5roln, BDzvmi5tqg, BD9aahgwjl, BDk6g4uxx0, BDlfcgc1p5, BDnaoq2i64, BDagc6055o, BD3la9cb6l, BDyx55wmzy, BDepqx44v2, BDjmwroq3w, BD29rjx4uw, BDufoxxr8t, and BDf8tfdbb4.
Security practices that fall under prevention such as Patch Management and Risk Management serve an organization well to complete fundamental actions that mitigate issues such as using out of date or vulnerable system components. Protection security practices, including but not limited to Network Protection, Malware Protection, and Ransomware Protection are also instrumental in keeping both sensitive data and system resources secure.
Lastly, practices defined in detection - Incident Investigation and Forensics and Threat Response – aid organizations in maintaining continuous practices to identify activities and IOCs to investigate and measures to respond to events and incidents as they occur.
For additional insights, we have a comprehensive whitepaper dedicated to ransomware that is regularly updated to reflect the latest trends and threats. In addition to providing in-depth information on ransomware, it includes a detailed mapping of the Bitdefender portfolio to various stages of a ransomware attack, offering insights into how our solutions can help organizations effectively prevent, detect, and mitigate ransomware incidents.
Indicators of Compromise
| IP Addresses |
|---|
|
103.217.41.10 |
|
194.28.50.70 |
|
198.54.123.60 |
|
45.61.185.34 |
|
176.123.9.68 |
|
103.131.70.228 |
|
91.219.236.204 |
|
193.178.169.19 |
| SHA-256 |
|---|
|
4d4df87cf8d8551d836f67fbde4337863bac3ff6b5cb324675054ea023b12ab6 |
|
657c0cce98d6e73e53b4001eeea51ed91fdcf3d47a18712b6ba9c66d59677980 |
|
736de79e0a2d08156bae608b2a3e63336829d59d38d61907642149a566ebd270 |
|
7d68da8aa78929bb467682ddb080e750ed07cd21b1ee7a9f38cf2810eeb9cb95 |
|
9144a60ac86d4c91f7553768d9bef848acd3bd9fe3e599b7ea2024a8a3115669 |
| SHA1 |
|---|
|
5d5027305deb2cb2fd263fea9a6011af |
|
35dfc1fcb06fe31264a3fc7ff307e166 |
tags
Author

Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks









