Technical Advisory: Software Supply Chain Attack Against 3CX Desktop App

On March 29, 2023, security researchers documented a malicious campaign targeting 3CX Desktop App customers. 3CX Desktop App is a software application developed by 3CX, a Voice over Internet Protocol (VoIP) solutions provider with 12M+ daily users. This application is available for Windows, macOS, Linux, and mobile.
Update 7 of the 3CX Desktop App application for Windows and macOS was compromised by threat actors believed to be linked to North Korea. Trojanized versions of the 3CX Desktop App installers (.msi for Windows, .dmg for macOS) were published on the developer’s website. As of the writing of this article, the method by which this update was compromised remains unknown.
Description of vulnerability
The installer for Windows would extract the legitimate 3CXDesktopApp.exe (fully functional), but also the malicious libraries ffmpeg.dll and d3dcompiler_47.dll. When the application is executed, it uses a technique called DLL sideloading (read our DLL sideloading explainer) to load the malicious ffmpeg.dll library in memory.
ffmpeg.dll library decrypts the payload from the d3dcompiler_47.dll library and executes it as a shellcode. Malware is suspended for 1-4 weeks as a detection evasion technique, after this period it will try to download a .ico file from the domain githubusercontent[.]com (no longer available) and extract from it an address of a command & control (C2) server. This domain hosted multiple icon files, each associated with a different C2 domain.
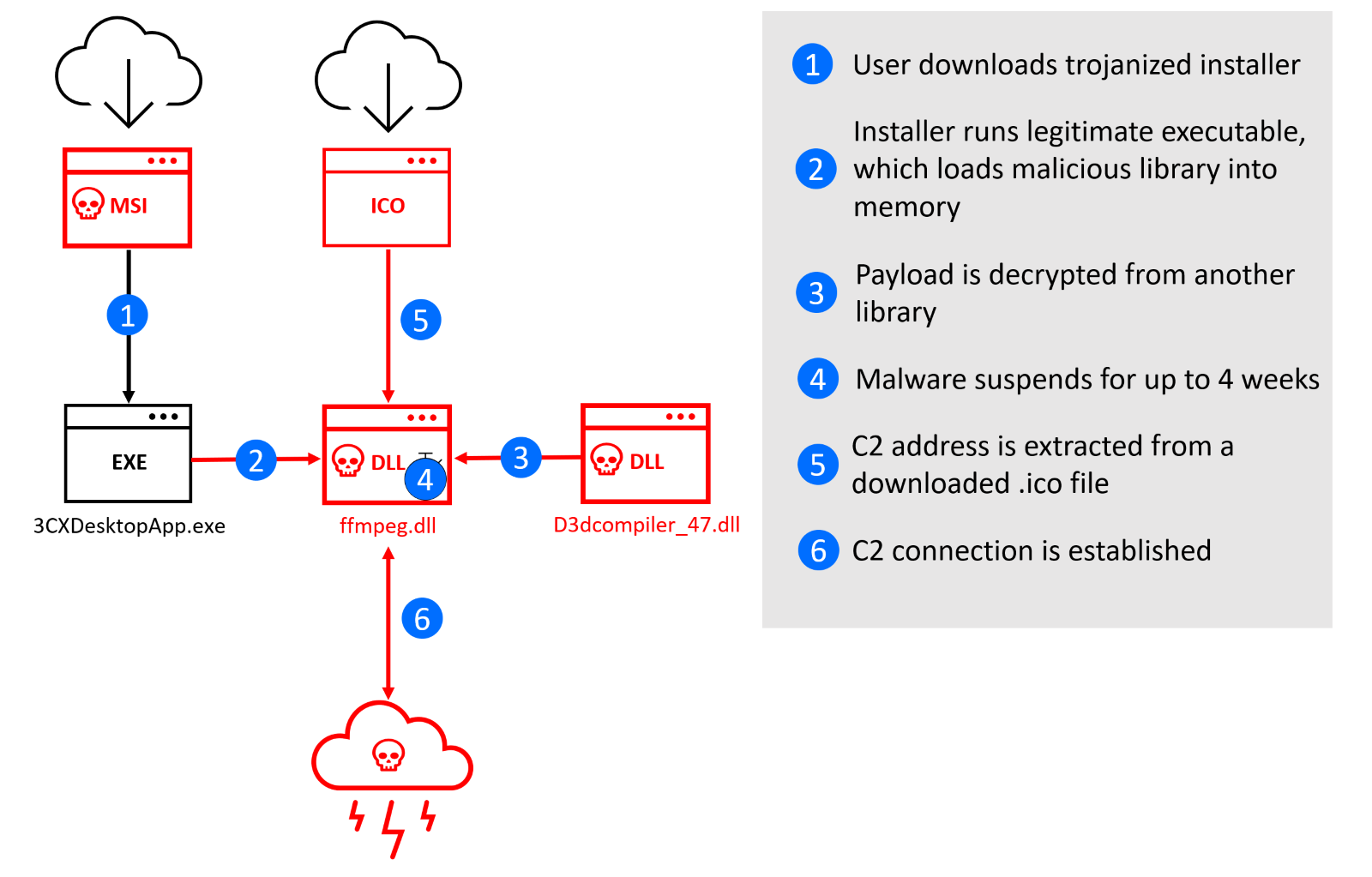
The installer for macOS is a simplified version of the trojanized installer for Windows. The malicious library libffmpeg.dylib includes an embedded list of hardcoded C2 servers. This list is identical for both Windows and macOS versions.
Multiple Windows and macOS versions of the software were affected:
- Windows – versions 18.12.407, 18.12.416
- macOS – versions 18.11.1213, 18.12.402, 18.12.407, 18.12.416
Conclusion and recommendations
Bitdefender continues monitoring the situation, but we haven’t detected any active exploitation attempts for our customers. Below are the detection names used in the Bitdefender GravityZone platform:
Windows
Trojan.SupplyChainAgent.ATrojan.SupplyChainAgent.BTrojan.SupplyChainAgent.C
macOS
Trojan.MAC.SupplyChainAgent.1Trojan.MAC.SupplyChainAgent.2
We also recommend 3CX customers stay up to date with the latest advisory, as the situation is still developing. Conduct an extensive infrastructure and software application audit to identify all systems where compromised software was deployed.
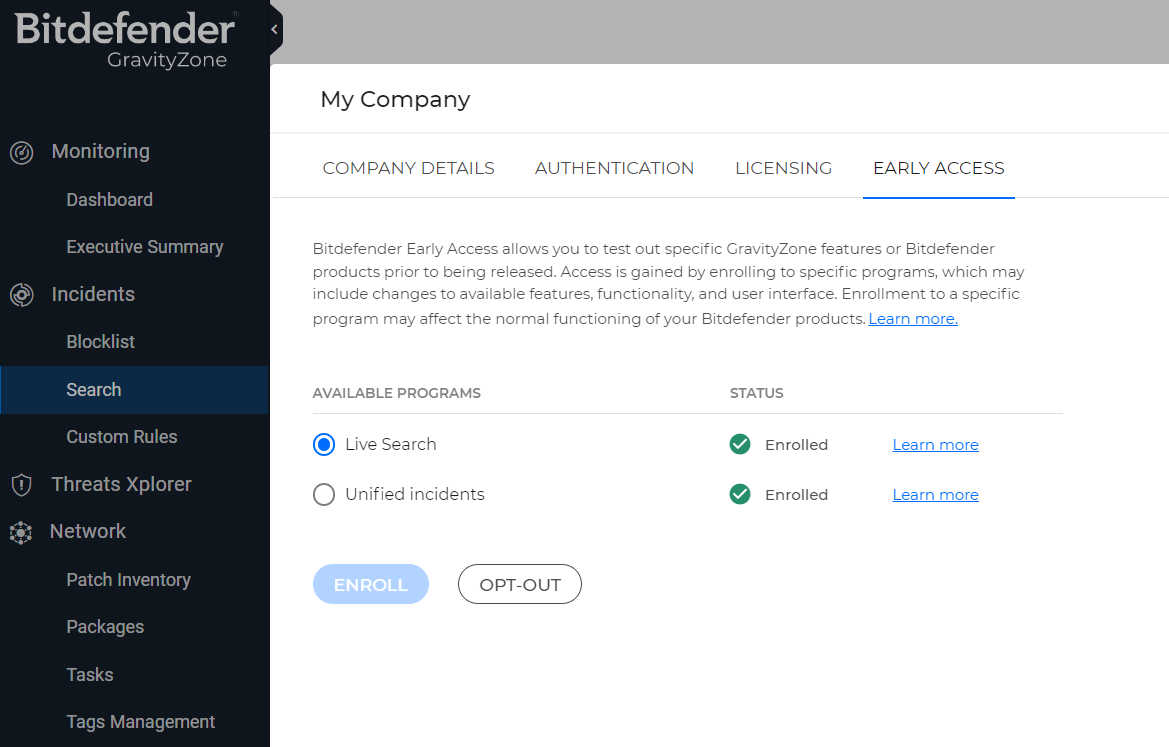
To locate the vulnerable versions of 3CX Desktop App software in your environment, you can use Live Search query feature of the GravityZone platform.
With Live Search, you can retrieve information about events and system statistics directly from online endpoints using OSquery, an operating system instrumentation framework that uses the SQLite query language. This is currently available for customers that have enrolled in the Early Access program available in GravityZone Cloud.
To enable Live Search - Log in to GravityZone. Click on your profile on the upper right side of the screen. From the drop-down menu, select My Company. Go to the Early Access tab. Select one of the programs available on the list. Click the Enroll below the table. Select Enroll to confirm. Your company will gain access to all the features, functionality, and interface changes included in the program.
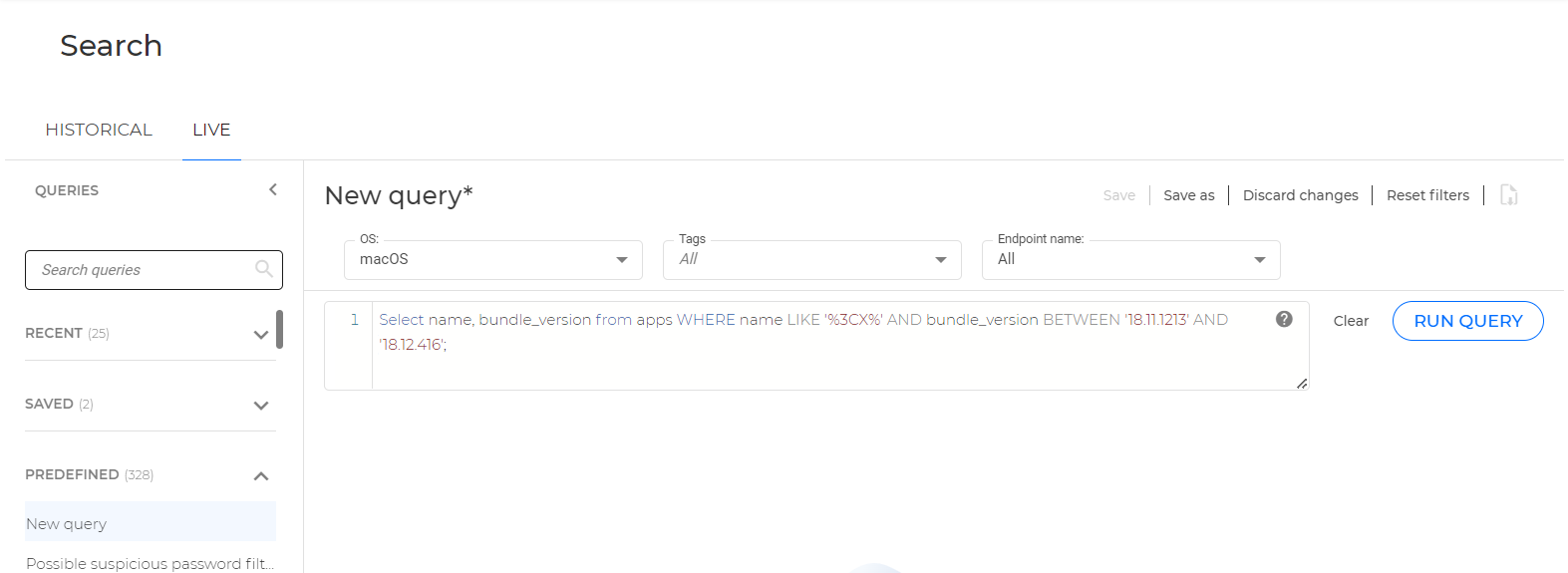
To locate compromised installations on macOS, use the following query: SELECT name, bundle_version from apps WHERE name LIKE ‘%3CX%’ AND bundle_version BETWEEN ‘18.11.1213’ AND ‘18.12.416’;
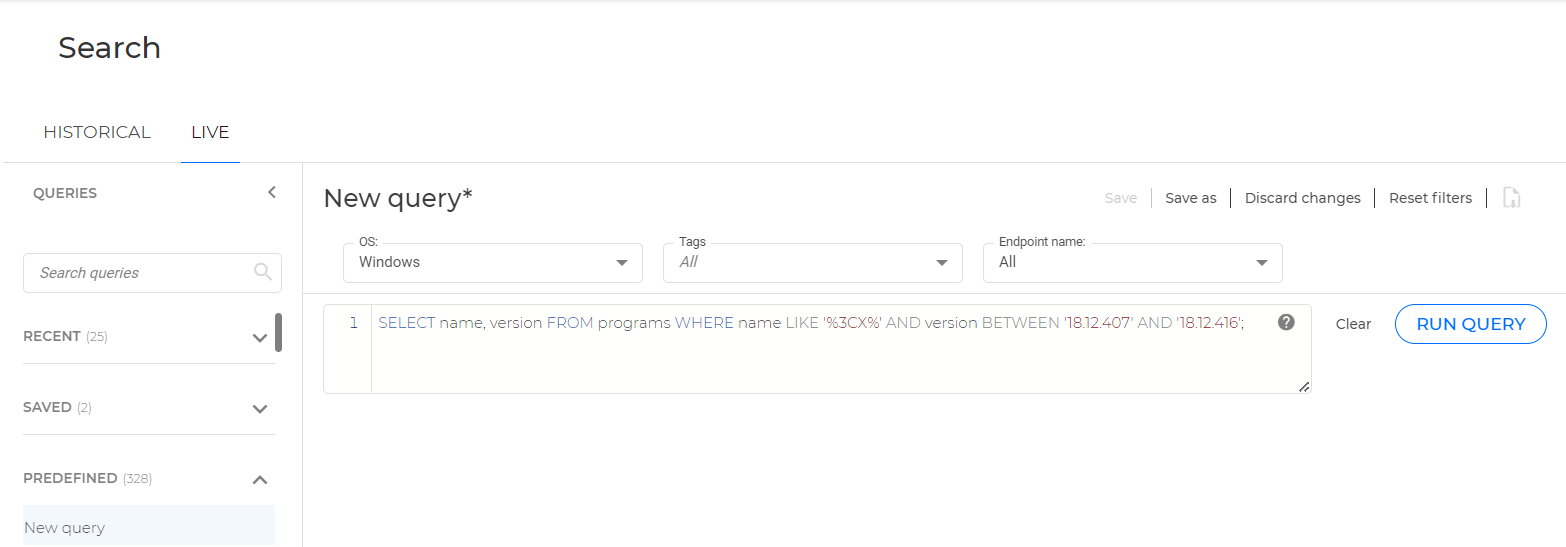
To locate compromised installations on Windows, use the following query: SELECT name, version FROM programs WHERE name LIKE ‘%3CX%’ AND version BETWEEN ‘18.12.407’ AND ‘18.12.416’;
Detection of compromised versions was also added to the GravityZone Endpoint Risk Analytics module:
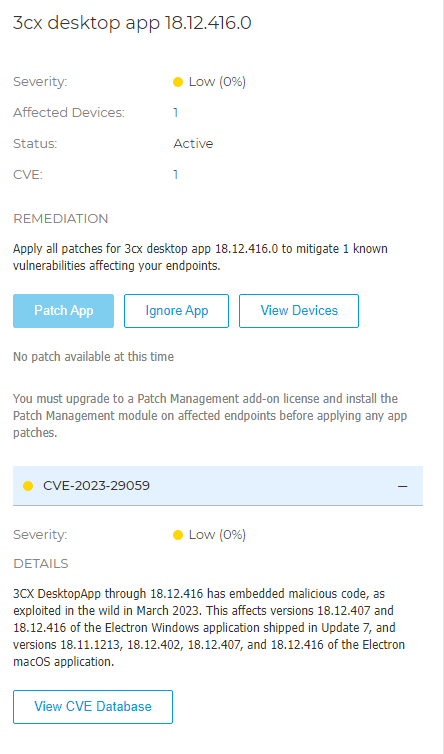
Actively monitor the infrastructure for potential exploitation attempts and respond accordingly. We strongly recommend implementing detection and response capabilities to detect any suspicious activity on the network and minimize the dwell time of adversaries. Bitdefender GravityZone XDR sensors detect suspicious activity and alert security teams to lateral movement attempts or the establishment of an external connection by the threat actor. This technology can be augmented by good security operations, either in-house or through a managed service like Bitdefender MDR.
Indicators of compromise
An up-to-date and complete list of indicators of compromise is available to Bitdefender Threat Intelligence users. The currently known indicators of compromise can be found in the table below.
Files
|
File Description |
SHA256 |
Detection Name |
|
Icon |
210c9882eba94198274ebc787fe8c88311af24932832a7fe1f1ca0261f815c3d |
Trojan.ICO.SupplyChainAgent.A |
|
Icon |
2487b4e3c950d56fb15316245b3c51fbd70717838f6f82f32db2efcc4d9da6de |
Trojan.ICO.SupplyChainAgent.B |
|
Icon |
268d4e399dbbb42ee1cd64d0da72c57214ac987efbb509c46cc57ea6b214beca |
Trojan.ICO.SupplyChainAgent.C |
|
Icon |
2c9957ea04d033d68b769f333a48e228c32bcf26bd98e51310efd48e80c1789f |
Trojan.ICO.SupplyChainAgent.D |
|
Icon |
4e08e4ffc699e0a1de4a5225a0b4920933fbb9cf123cde33e1674fde6d61444f |
Trojan.ICO.SupplyChainAgent.E |
|
Icon |
8c0b7d90f14c55d4f1d0f17e0242efd78fd4ed0c344ac6469611ec72defa6b2d |
Trojan.ICO.SupplyChainAgent.F |
|
Icon |
a541e5fc421c358e0a2b07bf4771e897fb5a617998aa4876e0e1baa5fbb8e25c |
Trojan.ICO.SupplyChainAgent.G |
|
Icon |
c13d49ed325dec9551906bafb6de9ec947e5ff936e7e40877feb2ba4bb176396 |
Trojan.ICO.SupplyChainAgent.H |
|
Icon |
c62dce8a77d777774e059cf1720d77c47b97d97c3b0cf43ade5d96bf724639bd |
Trojan.ICO.SupplyChainAgent.I |
|
Icon |
d0f1984b4fe896d0024533510ce22d71e05b20bad74d53fae158dc752a65782e |
Trojan.ICO.SupplyChainAgent.J |
|
Icon |
d459aa0a63140ccc647e9026bfd1fccd4c310c262a88896c57bbe3b6456bd090 |
Trojan.ICO.SupplyChainAgent.K |
|
Icon |
d51a790d187439ce030cf763237e992e9196e9aa41797a94956681b6279d1b9a |
Trojan.ICO.SupplyChainAgent.L |
|
Icon |
e059c8c8b01d6f3af32257fc2b6fe188d5f4359c308b3684b1e0db2071c3425c |
Trojan.ICO.SupplyChainAgent.M |
|
Icon |
f1bf4078141d7ccb4f82e3f4f1c3571ee6dd79b5335eb0e0464f877e6e6e3182 |
Trojan.ICO.SupplyChainAgent.N |
|
Icon |
f47c883f59a4802514c57680de3f41f690871e26f250c6e890651ba71027e4d3 |
Trojan.ICO.SupplyChainAgent.O |
|
macOS Installer |
5407cda7d3a75e7b1e030b1f33337a56f293578ffa8b3ae19c671051ed314290 |
Trojan.MAC.SupplyChainAgent.E |
|
macOS Installer |
e6bbc33815b9f20b0cf832d7401dd893fbc467c800728b5891336706da0dbcec |
Trojan.MAC.SupplyChainAgent.J |
|
Windows Installer |
59e1edf4d82fae4978e97512b0331b7eb21dd4b838b850ba46794d9c7a2c0983 |
Trojan.SupplyChainAgent.E |
|
Windows Installer |
aa124a4b4df12b34e74ee7f6c683b2ebec4ce9a8edcf9be345823b4fdcf5d868 |
Trojan.SupplyChainAgent.E |
|
macOS dylib bundle |
51079c7e549cbad25429ff98b6d6ca02dc9234e466dd9b75a5e05b9d7b95af72 |
Trojan.MAC.SupplyChainAgent.H |
|
macOS dylib bundle |
92005051ae314d61074ed94a52e76b1c3e21e7f0e8c1d1fdd497a006ce45fa61 |
Trojan.MAC.SupplyChainAgent.E |
|
macOS dylib bundle |
ac99602999bf9823f221372378f95baa4fc68929bac3a10e8d9a107ec8074eca |
Trojan.MAC.SupplyChainAgent.I |
|
macOS dylib bundle |
b86c695822013483fa4e2dfdf712c5ee777d7b99cbad8c2fa2274b133481eadb |
Trojan.MAC.SupplyChainAgent.J |
|
macOS dylib bundle |
e2d161a4a5280ca896acda9ced2ab5c84e100e81e5dd46bf5413eee206b1bfac |
Trojan.MAC.SupplyChainAgent.G |
|
macOS dylib bundle |
f7ba7f9bf608128894196cf7314f68b78d2a6df10718c8e0cd64dbe3b86bc730 |
Trojan.MAC.SupplyChainAgent.F |
|
libffmpeg (macOS Library) |
5009c7d1590c1f8c05827122172583ddf924c53b55a46826abf66da46725505a |
Trojan.MAC.SupplyChainAgent.C |
|
libffmpeg (macOS Library) |
87c5d0c93b80acf61d24e7aaf0faae231ab507ca45483ad3d441b5d1acebc43c |
Trojan.MAC.SupplyChainAgent.C |
|
libffmpeg (macOS Library) |
a64fa9f1c76457ecc58402142a8728ce34ccba378c17318b3340083eeb7acc67 |
Trojan.MAC.SupplyChainAgent.2 |
|
libffmpeg (macOS Library) |
fee4f9dabc094df24d83ec1a8c4e4ff573e5d9973caa676f58086c99561382d7 |
Trojan.MAC.SupplyChainAgent.1 |
|
d3dcompiler (Windows Library) |
11be1803e2e307b647a8a7e02d128335c448ff741bf06bf52b332e0bbf423b03 |
Trojan.Marte.SupplyChainAgent.C |
|
ffmpeg (Windows library) |
253f3a53796f1b0fbe64f7b05ae1d66bc2b0773588d00c3d2bf08572a497fa59 |
Trojan.SupplyChainAgent.J |
|
ffmpeg (Windows library) |
396350b12b7626d40d76b0c8814920e5692f5a396a3110432a4f361e93a2d881 |
Trojan.SupplyChainAgent.B |
|
ffmpeg (Windows library) |
7986bbaee8940da11ce089383521ab420c443ab7b15ed42aed91fd31ce833896 |
Trojan.SupplyChainAgent.E |
|
ffmpeg (Windows library) |
c485674ee63ec8d4e8fde9800788175a8b02d3f9416d0e763360fff7f8eb4e02 |
Trojan.SupplyChainAgent.K |
|
Final Payload |
2a22798543bd1f97dd5cd626ba9ac6de6d0a744f3cab01faf9dfc238b24e178b |
Trojan.SupplyChainAgent.A |
|
Final Payload |
693f96516f43561ba4ae10f2a08758b42cbf9c75cdafe3263169ff7f26dfd206 |
Generic.SupplyChainAgent.A.7C42B0E2 |
|
Final Payload |
6a0f637546684c90809cf264c22a861c9a07b1ca3b2ef6a359a14d612e392c1a |
Generic.SupplyChainAgent.A.79D82208 |
|
Final Payload |
82a2dafd6ce594f2cf8588f32585c71be2180fc4cf9a144e300b1692f3de5807 |
Trojan.SupplyChainAgent.D |
|
Final Payload |
851c2c99ebafd4e5e9e140cfe3f2d03533846ca16f8151ae8ee0e83c692884b7 |
Trojan.SupplyChainAgent.F |
|
Final Payload |
927668ad4016fcd09f172f9117d575a3a56cb10b1197b74b7e05f14b0d415d2e |
Trojan.SupplyChainAgent.D |
|
Final Payload |
aa4e398b3bd8645016d8090ffc77d15f926a8e69258642191deb4e68688ff973 |
Trojan.SupplyChainAgent.A |
|
Final Payload |
d67e6ba9be2ae522e05838285acefc2513b61f6ccae159027914a5813fb5f80f |
Trojan.SupplyChainAgent.A |
|
Final Payload |
e4dac5422cc1b7f6df6017d2568502fb02756694eeae7c10916314d66898c811 |
Trojan.SupplyChainAgent.A |
|
Final Payload |
f5fdefaa5321e2cea02ef8b479de8ec3c5505e956ea1484c84a7abb17231fe24 |
Trojan.SupplyChainAgent.A |
|
Final Payload |
b56279136d816a11cf4db9fc1b249da04b3fa3aef4ba709b20cdfbe572394812 |
Generic.SupplyChainAgent.B.E9148ED9 |
Domains
|
akamaicontainer.com |
|
akamaitechcloudservices.com |
|
azuredeploystore.com |
|
azureonlinecloud.com |
|
azureonlinestorage.com |
|
dunamistrd.com |
|
glcloudservice.com |
|
journalide.org |
|
msedgepackageinfo.com |
|
msstorageazure.com |
|
msstorageboxes.com |
|
officeaddons.com |
|
officestoragebox.com |
|
pbxcloudeservices.com |
|
pbxphonenetwork.com |
|
pbxsources.com |
|
qwepoi123098.com |
|
sbmsa.wiki |
|
sourceslabs.com |
|
visualstudiofactory.com |
|
zacharryblogs.com |
For the latest information on vulnerabilities such as this one, subscribe to Business Insights.
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










