The Lifecycle of Stolen Data: From Theft to Profit

With the recent news of AT&T’s data breach, stolen company data is very top of mind at the moment. Unfortunately, it’s just the tip of the iceberg. The year 2023 marked a record for number of data breaches and individuals impacted, with 3,205 data compromises affecting 353 million people in total.
But what actually happens when a data breach occurs and sensitive information is actually leaked? What are the specific dangers to an organization once that information is exposed?
This article dives into the lifecycle of stolen data, exploring how threat actors exploit leaked information and providing actionable strategies for organizations to protect themselves effectively.
How Company Data is Compromised
Sensitive data can be stolen in multiple ways and is often the primary objective for many threat actors and cybercriminal groups. Among multiple methods, data can be compromised via:
- Malicious Software: Malware and trojans can lurk within networks and devices, exfiltrating data and evading detection.
- Unauthorized Access: Account compromise attacks accomplished via brute-force attacks, credential theft, phishing, or social engineering can provide the keys to the kingdom, especially if organizations aren’t limiting account privileges or permissions.
- Vulnerability Exploits: The explosion of SaaS applications has increased the attack surface of any given organization significantly, making vulnerability management a loftier challenge. This means threat actors have an easier time exploiting known vulnerabilities to compromise organizations and their data.
Even ransomware groups are turning to data exfiltration to increase their chances of getting paid. Traditionally, ransomware encrypted an organization’s data, shutting a company out of their own network or assets. Now, ransomware groups are threatening to leak and expose sensitive data, knowing it could lead to further reputational, legal, and financial damage.
At Bitdefender, we’ve seen ransomware groups take months to compromise and exfiltrate data until they’re sure they have enough to impact a company. This way, even if the victim has backups and is unwilling to pay, ransom groups can threaten to release and expose the data.
This new approach to ransomware is largely why the rate and cost of ransomware payouts have been steadily increasing over the last decade.
Once threat actors have their hands on an organization’s data, they can now monetize it. In many instances, they turn to the dark web.
Profiting from Cybercrime on the Dark Web
The dark web is a hidden part of the internet that’s accessible through specialized browsers. It’s designed for complete anonymity and infamous for facilitating the purchase of illicit content, services, and goods like drugs and stolen data. A quick dive into the dark web can surface numerous entities selling data like credit card information, Social Security numbers or bulk data from a company compromise. 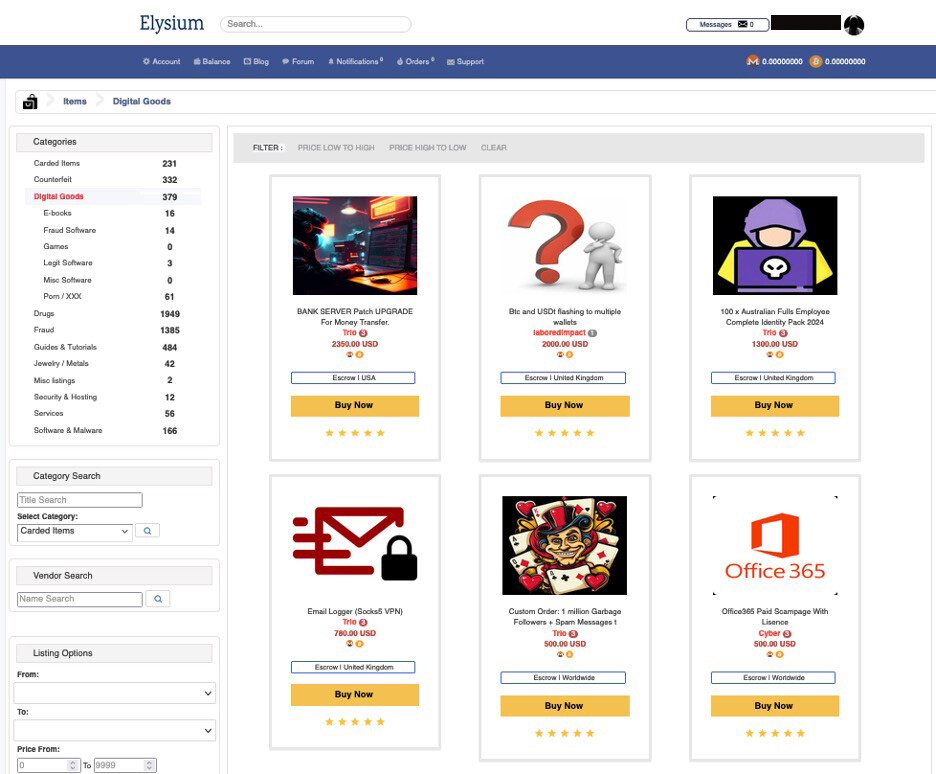
Example of hackers selling data.
The dark web is often the first place threat actors go to sell stolen data, sell access to stolen data or sell access to compromised accounts or companies. Compromised companies are big-ticket items and driving the surge of ransomware we’re seeing.
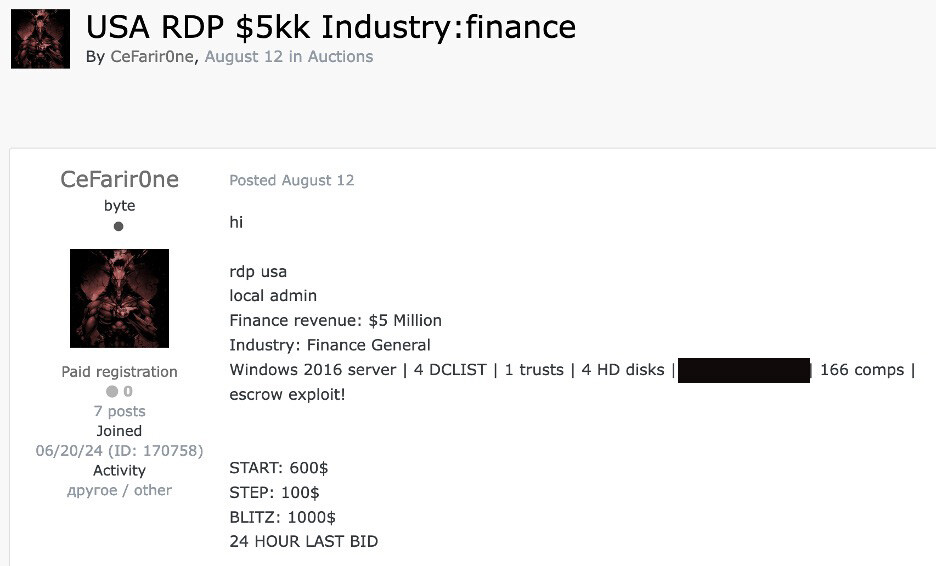
Nearly 70% of ransomware attacks result in payments, so access to a company can result in further ransomware attacks. With such a high payment rate, threat actors are highly incentivized to monetize that access because it’s an easy sell.
Depending on what’s being sold, it can be presented at a fixed market price or sold via an auction to the highest bidder. Over the years, we’ve discovered that the dark web has evolved and become more efficient and frictionless to utilize, facilitating transactions and further incentivizing data theft.
For example, deposits are no longer needed to enter marketplaces, removing a barrier for anyone who might be interacting with the dark web for the first time. The emergence of cryptocurrency has also facilitated dark web activity because it makes it easier for individuals to cover their tracks, mask their activity, and stay relatively anonymous.
Even after the takedown of major marketplaces, single-vendor marketplaces emerged in their place, becoming a decentralized crime hub that made it difficult for law enforcement agencies (LEAs) to track and take down. These days, with LEA activity at a low point, consolidated marketplaces with validated and reviewed vendors are beginning to pop up, making it even easier for buyers to do business with trusted vendors.
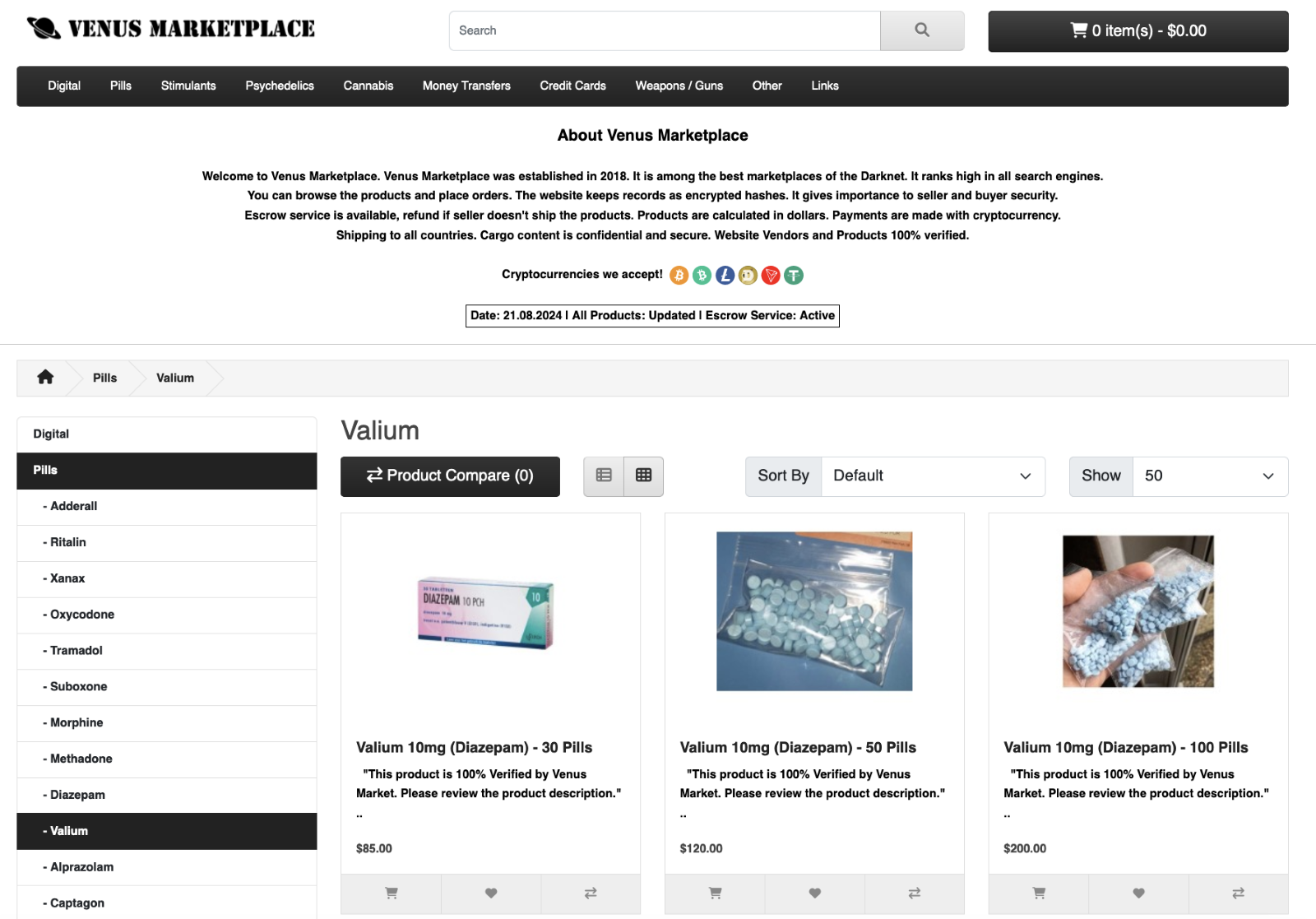
Example of dark web marketplace known as Venus Marketplace.
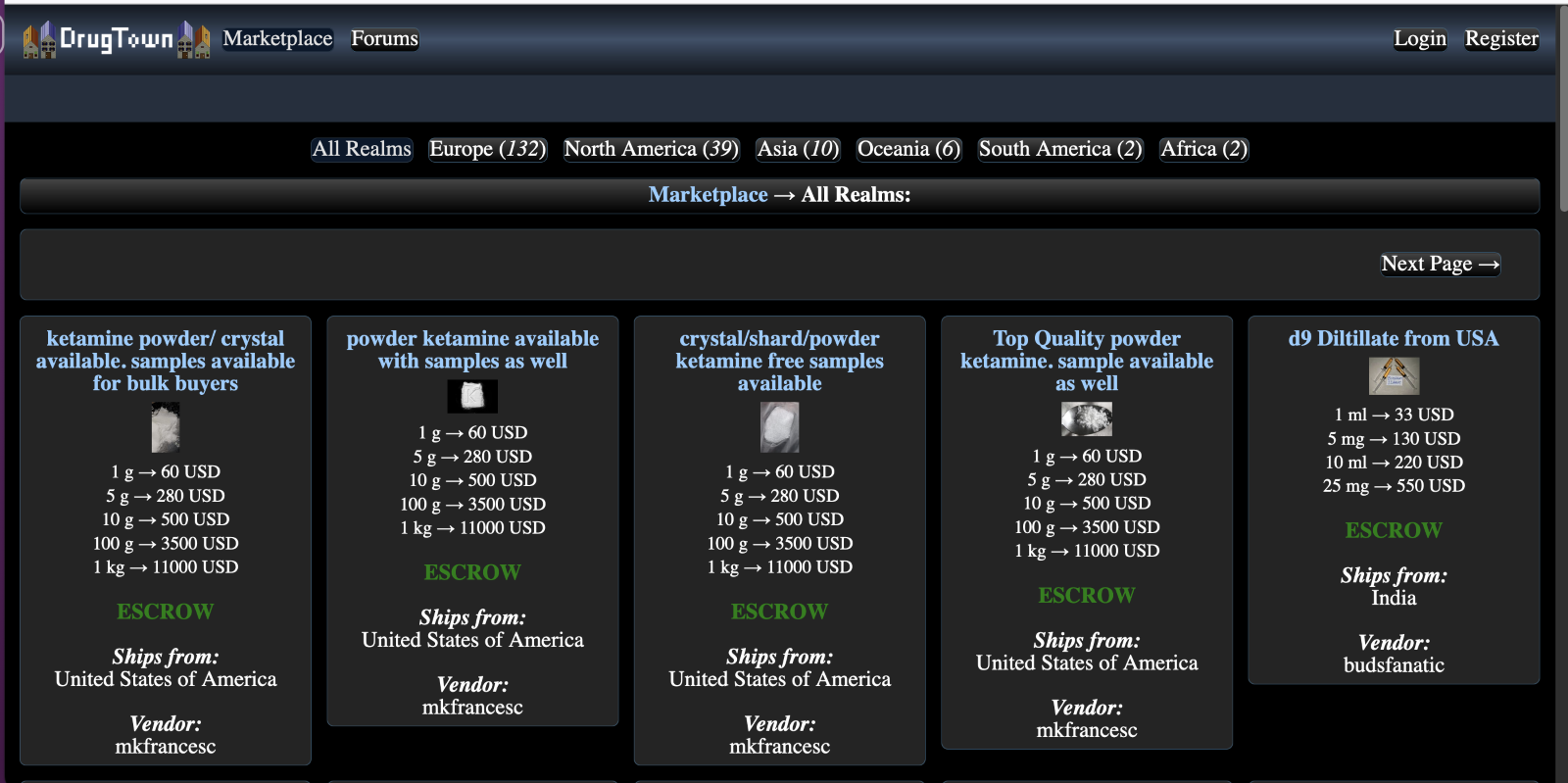
Example of dark web marketplace known as DrugTown.
All these advances are making data theft even more lucrative because it’s easier to utilize marketplaces, sell data (or access to data), and stay away from LEAs. It’s become so easy these days that even low-level scavenger hackers can flourish. They take advantage of instances where data breaches are posted on public, non-dark web sites such as hacker forums. The data is eventually deleted as GDPR is invoked to take down the stolen information.
Scavenger hackers, however, can easily take that data for free before it’s taken down, and sell it on the dark web alongside the responsible party, potentially at a lower price. This makes the information even more available to bad actors.
Stolen Dark Web Data and Its Role in Future Cyberattacks
Once a company’s stolen data makes its way to the dark web, they’re exposed to any number of threat actors who bought the data or access to it. This can lead to even more compromises and further attacks such as:
- Account compromise via stolen credentials
- APT attacks via access to compromised accounts
- Spearphishing and BEC attacks via stolen PII
- Stolen funds via stolen bank account details
- Identity theft attacks via PII
Threat actors essentially skip the hard work of hacking and compromising accounts by purchasing data on the dark web, which is part of the reason why organizations who suffer a data breach are 67% more likely to get attacked again within a year.
This is especially concerning when it comes to password/email combinations from other data breaches. Because passwords are often reused, threat actors can take stolen credentials from one company and utilize it on another company with some amount of success.
How Organizations can Protect Themselves from Leaked Data
To better protect themselves, organizations need to focus on two main priorities:
- Preventing a data breach from happening in the first place.
- Preventing data on the dark web, whether from your organization’s compromise or another organization’s compromise, from being used to attack your organization.
For the first priority, detection, visibility and response tools such as Extended Detection and Response (XDR) solutions and MDR services can help. These can see whether an unauthorized user has access to your systems or data, spot anomalous or suspicious activity that may be an indication of compromise. Having full, comprehensive visibility is crucial here so you’re managing all your endpoints, systems, and assets while ensuring your data is kept secure and isn’t falling into the wrong hands.
Utilizing these tools and vendors goes a long way towards cyber resiliency. Hackers looking to steal data or take advantage of already-leaked information are looking for easy ways in. An organization with a robust detection and response solution in place is likely to dissuade a less sophisticated attacker.
However, no security leader should think that they can prevent a data breach – a better strategy is to assume it might happen and act accordingly. This brings us to our second priority.
To help ensure past and future data breaches don’t come back to haunt your organization, you must be proactive and creative. One of the most important things you can do is encrypt your sensitive information. When it comes to password data, you need to salt your encrypted passwords. This ensures that even if the data is exfiltrated, it’s useless to hackers.
You can also plant fake information to see where it may end up. This can be done via automated tools and may alert you to an active compromise and may also flag potential threat actors who have your organization in their crosshairs. Seeing your planted information pop up on the dark web is a clear indication that something has gone wrong and allows you to stay proactive rather than reactive.
Security awareness training is a critical component as well that must be an ongoing effort. Even at Bitdefender, we have training for all our employees that’s conducted annually. This helps employees maintain good security hygene, spot potential attacks such as phishing and social engineering attacks, and creates a culture of security that minimize negligence and accidents that can lead to a data breach.
Ultimately, the most effective due diligence requires a mix of tools, solutions and processes to prevent exfiltration and minimize damage in case stolen data is used against your organization.
tags
Author
Josue Ledesma is a writer, filmmaker, and content marketer living in New York City. He covers cyber security, tech and finance, consumer privacy, and B2B digital marketing.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks












