When Emails Attack: BEC Attack Examples You Can't Ignore

Phishing emails represent a major security risk for businesses, irrespective of their size. Given our daily dependence on email communication, both employees and high-ranking individuals are attractive targets for threat actors looking to infiltrate an organization's network or deceive unsuspecting users.
All it takes is one carefully crafted phishing email to enable intruders to steal login credentials, seize control of accounts, empty bank funds, or disrupt operations and systems significantly, resulting in serious financial and legal consequences. To add to this already significant issue, we expect that the growing popularity and capabilities of generative artificial intelligence (AI) tools like ChatGPT or Bard will further fuel Business Email Compromise (BEC) attacks. As we've previously discussed in our article “Why Generative AI Fuels Ransomware Attacks Through Language, Not Code,” generative AI empowers attacks through language rather than code, and BEC attacks are among the primary methods set to benefit from this new technology.
Whether it's the tool's capacity to adopt industry-specific language or its ability to mimic writing styles from previous examples, these attacks are poised to become more pronounced. According to the latest “Data Breach Investigations Report,” BEC attacks nearly doubled in the past year, and we foresee this trend continuing.
Another significant reason for the increasing frequency of BEC attacks is the rise of "soft" supply chain attacks. Threat actors can move from one victim to a more lucrative target by utilizing remote access methods, such as network federation, or by employing BEC attacks.
Cybercriminals may employ the compromise of a smaller company as a steppingstone to infiltrate larger, more lucrative targets. We've discussed this escalation of attacks before, highlighting that your significance to these threat actors doesn't always depend on the specific data or assets you possess, but rather on your connections. For instance, a small contractor with just five computers may not initially be an appealing target for ransomware affiliates. However, if they have a working relationship with a larger company, their value to threat actors suddenly skyrockets.
To protect your business, reputation, and finances, it’s crucial for you and your employees to stay updated on the latest phishing trends that threaten the livelihood of your organization. In this article, we will dissect some of the most common fraudulent and malicious day-to-day business emails you should watch out for.
Attachment Ambush: Sneaking Malware into Routine Emails
Your organization undoubtedly receives many electronic bills every month. This makes it easy for threat actors to drop malicious correspondence to trick you into deploying malicious software that lets them steal credentials and financial data or inflict severe damage to your network.
After infiltrating a company, threat actors often take a simple yet effective step: they check the "Sent Items" folder in an email client. If they find any emails about recent purchase orders, they simply forward an email to that same conversation, stating there was a mistake and sending an updated purchase order. This strategy is straightforward but works well because it builds on previous communication.
Researchers at Bitdefender Antispam Lab have caught several phony invoice/purchase order phishing emails targeting organizations in the past two weeks.
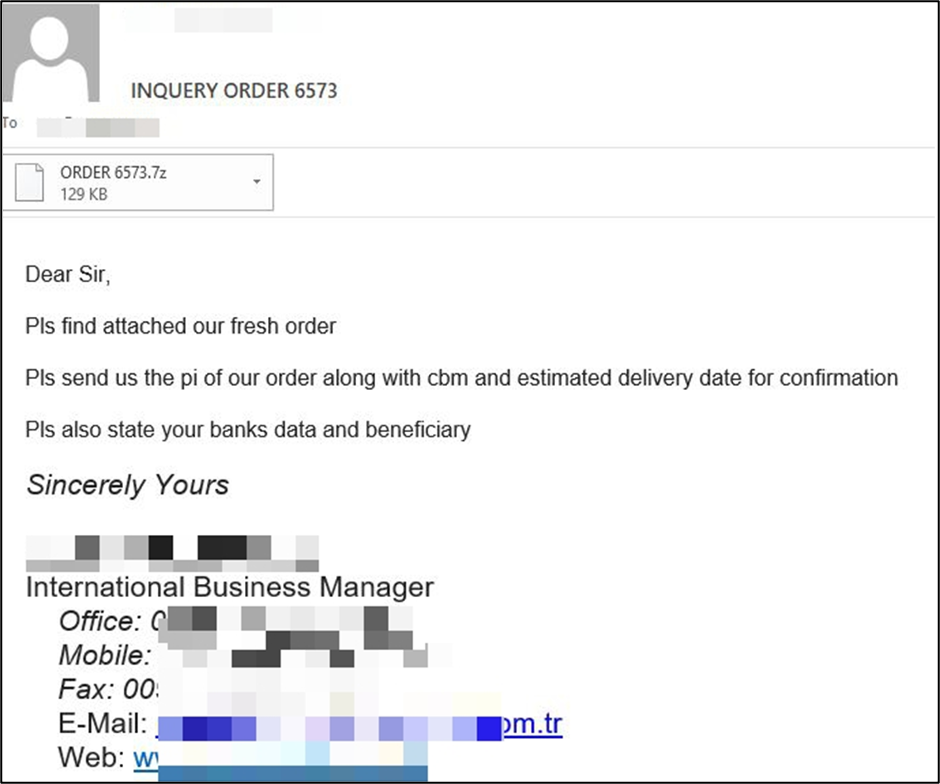
The above phishing email sample impersonates a textile manufacturer in Turkey and urges the recipient to review the attached “ORDER 6573.” The message may not seem out of the ordinary, but the attached .7z file hides a malicious payload that deploys a well-known remote access Trojan (Agent Tesla) onto the target device.
Agent Tesla is a popular data stealer used in the reconnaissance and data harvesting stages of more devastating attacks such as ransomware. The malicious software collects sensitive data from infected machines and exfiltrates stolen information via SMTP protocol back to an email account controlled by the attackers.
Below is another example of cybercriminals using a malicious attachment disguised as an invoice copy to compromise their targets. The attachment is also used to disguise a malicious payload that, once accessed, deploys Agent Tesla on the target’s system.
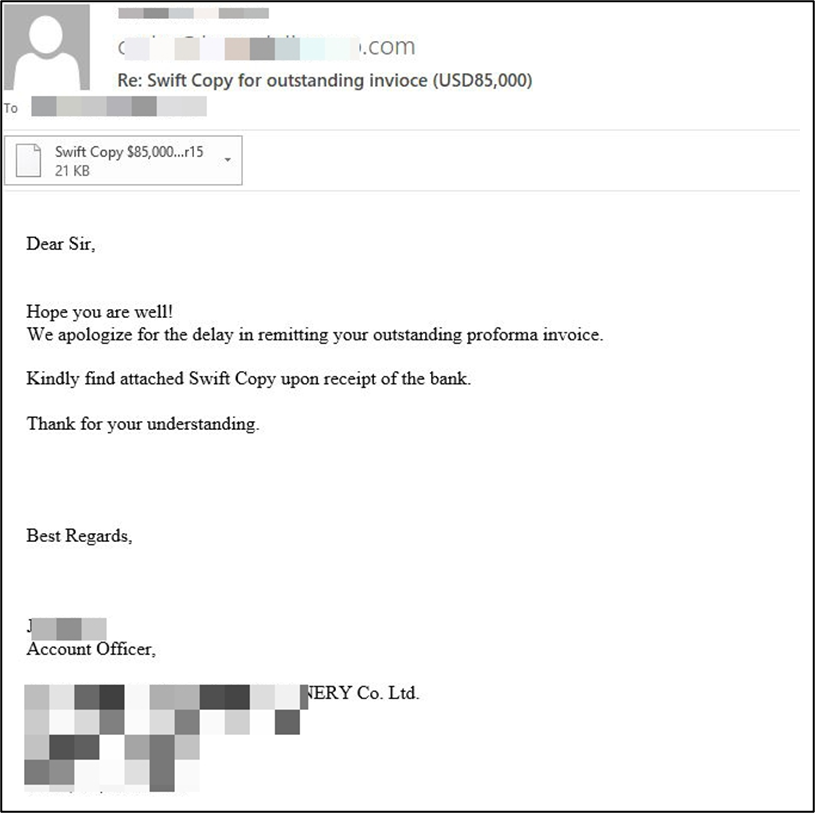
Remember, cybercriminals may do their homework before targeting you and your employees. They can research suppliers and individuals you work with to deliver highly convincing messages for maximum efficiency.
Beyond Attachments: How Emails Can Harvest Your Data
Not all intercepted phishing attempts targeting your business necessarily contain malicious attachments.
In this email below, scammers impersonate the Netherlands Chamber of Commerce (KVK) to steal personally identifiable information from entrepreneurs. Recipients are told their company is no longer active in the government-owned trade register and are urged to update their personal data by filling out a form.
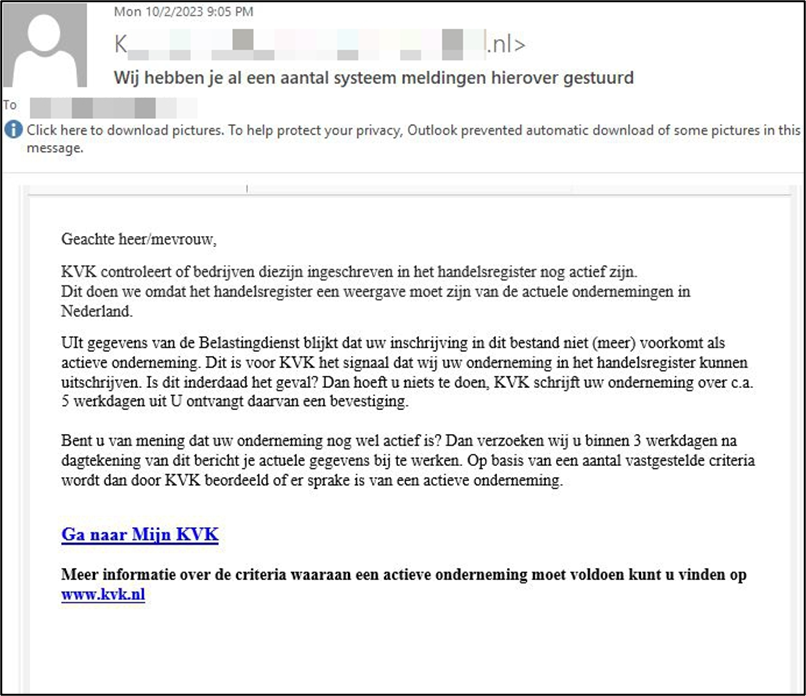
“The Chamber of Commerce checks whether companies registered in the trade register are still active,” a machine-translated version of the email reads. “We do this because the trade register must reflect the current companies in the Netherlands. Information from the tax authorities shows that your registration no longer appears in this file as an active company.
“Do you believe that your company is still active? Then we request that you update your current details within 3 working days of the date of this message.”
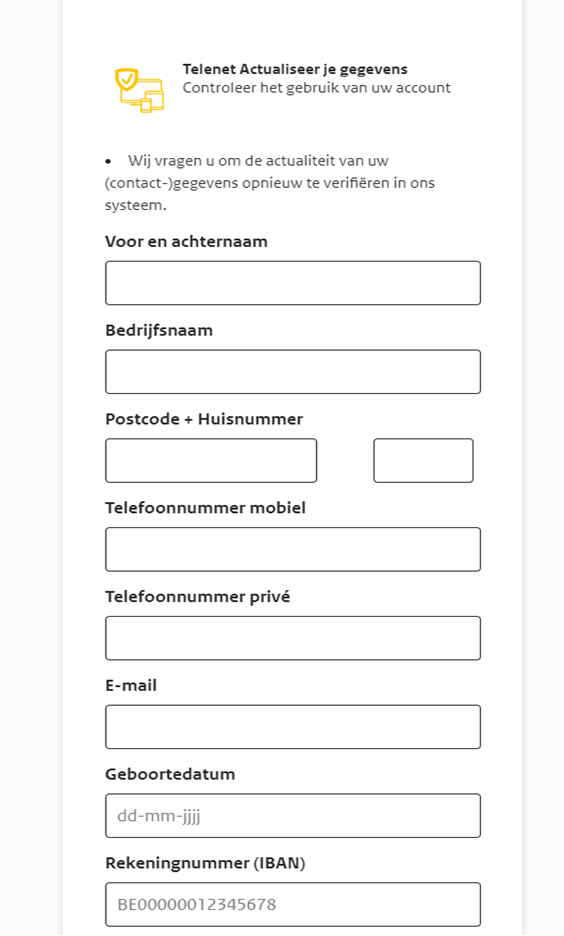
Recipients are required to fill out their name, company name, zip code, house number, mobile telephone number, private telephone number, email address and date of birth. Once collected, the scammers can use the data to better target you and your business and conduct fraud.
The Human Element: Manipulating Recipients through Authority and Urgency
We’ve seen how cybercriminals use generic deceptive emails to obtain sensitive information and compromise networks, but sometimes, phishing emails are more specific to the recipient.
Spear phishing emails rely on a couple of tactics to dupe their victims. Specifically, attackers impersonate a familiar level of authority within the organization and transmit a sense of urgency in an attempt to get the user to overlook their normal judgment or protocols.
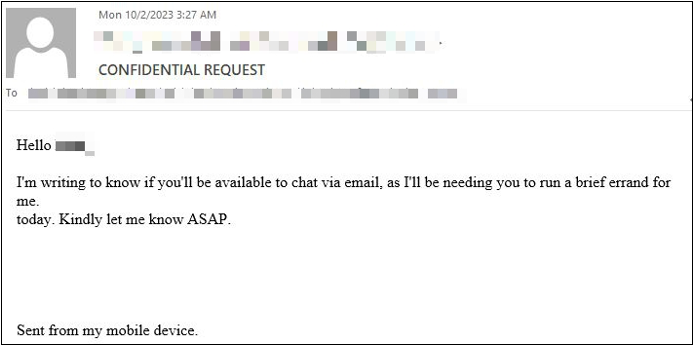
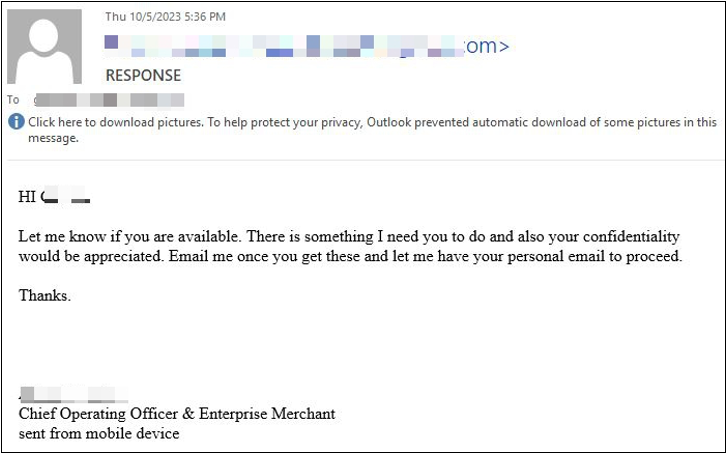
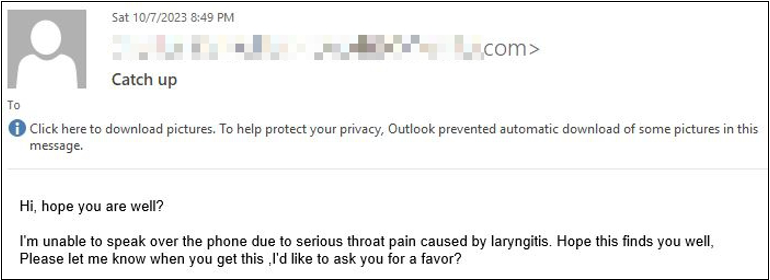
In the samples below, cybercrooks impersonate the recipient’s boss or manager in an attempt to commit fraud. The requests are usually accompanied by a personal or business favor, which may include purchasing gift cards or prepaid debit cards and conducting wire transfers. Additionally, the attackers always mention that the request is confidential, ask you to switch to a different messaging platform or make up an excuse for why they cannot speak with you directly over the phone (health issues such as laryngitis).
Samples of spear phishing emails:
Conclusion and Recommendations
Small and large organizations alike can be targeted by these phishing emails, and their convincing and inconspicuous nature makes them a highly lucrative scam.
Identifying the warning signs of phishing emails targeting your business and employees can save your organization’s reputation and money.
Below are five signs you’re dealing with an attempted BEC attack:
- Urgent requests and notifications to verify accounts and update information during less expected times such as the holiday season, end of the work schedule and weekends
- Bogus email address with unfamiliar domain and misspellings
- Requests to act immediately and open attachments or click on links
- Claims that a financial account has been blocked or compromised and that payments have been suspended
- Requests for payment or change of payment details, typically accompanied by subject lines such as “quick request”, “confidential request”, “important payment”
While many companies have emphasized employee training and education, which continues to be important, it's crucial to complement these efforts with robust technology solutions. Relying solely on end-users is not sufficient. Implement a defense-in-depth approach and deploy multi-layered security measures:
- Email Protection – Whether your email system is on-premises or cloud-based, ensure that you have a robust email protection solution in place. This should include advanced spam filters, malware scanners, and anti-phishing technologies.
- Malware Protection – Deploy endpoint security solutions that are capable of detecting and blocking malicious email attachments. These solutions should include advanced threat detection and sandboxing capabilities.
- IP/URL/Domain Reputation - Implement IP, URL, and domain reputation filters on all endpoints to block access to malicious or compromised addresses. These filters can act as a second line of defense, preventing users from accessing known dangerous sites.
- Detection and Response Capabilities - Despite your best efforts, it is still possible that modern threat actors will make it past your prevention and protection controls. This is where your detection and response capabilities come into play. Whether you get these capabilities as-a-product (EDR/XDR) or as-a-service (MDR), the purpose is to minimize the time when threat actors remain undetected.
We would like to thank Viorel Zavoiu and Victor Vrabie for their help with putting this report together.
tags
Author

Alina has been a part of the Bitdefender family for some years now, as her past role involved interfacing with end users and partners, advocating Bitdefender technologies and solutions. She is a history buff and passionate about cybersecurity and anything sci-fi. Her spare time is usually split between her two feline friends and traveling.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










