A US Hacker Blasted North Korea off the Internet Following Missile Tests

Last month, as North Korea's supreme leader Kim Jong-un oversaw a series of sabre-rattling hypersonic missile tests, cyber attacks disrupted the country's internet infrastructure.
The finger of suspicion pointed at nation states in the West, who might have launched the distributed denial-of-service attacks, which reportedly, at their height, took down "all traffic to and from North Korea."
However, in an interview with Wired, an independent hacker known only as P4x has claimed sole credit.
P4x claims that he was himself hacked by North Korean spies just over a year ago, as part of a campaign that deployed zero-day vulnerabilities against security researchers.
In that attack, North Korean hackers reached out to experts in the cybersecurity community via email, Twitter, and LinkedIn, posing as fellow researchers and offered to collaborate on investigations into new vulnerabilities.
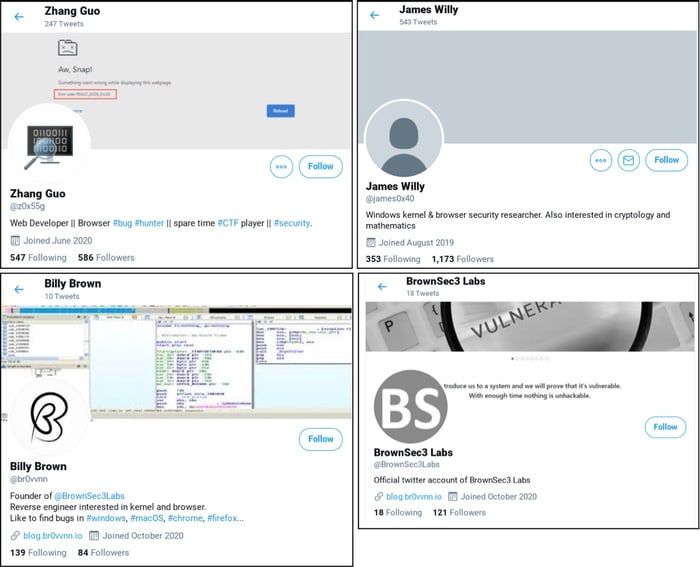
As I explained at the time, this was all a ruse to slip malicious backdoor code onto the targeted researchers' computers.
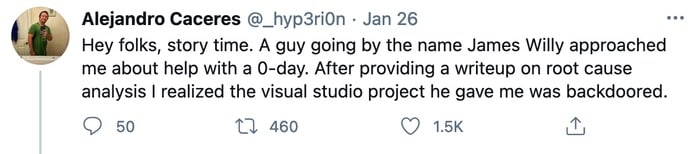
According to Wired, P4x says that last year's North Korean attack did not succeed against him but the thought of being personally targeted by state-sponsored hackers did leave him "deeply unnerved."
And P4x felt frustrated by what he viewed as a lack of any visible response from the US government.
And so the US hacker took matters into his own hands, and a year after he was targeted by North Korea he decided he would turn the tables:
"I want them to understand that if you come at us, it means some of your infrastructure is going down for a while."
Finding "numerous known but unpatched vulnerabilities" in North Korean computer systems, P4x was able to launch denial-of-service attacks on the servers and routers that form North Korea's - small by the rest of the world's standards - portion of the internet.
And, from the sound of things, it worked. For some hours, North Korea effectively dropped off the internet.
"When someone would try to connect to an IP address in North Korea, the internet would literally be unable to route their data into the country," security researcher Junade Ali told Reuters.
Should P4x have done it? Does the fact that North Korea was his target make the disruption accessible?
That's a debate for another time, but one thing that should be considered is that if a private individual launches an attack against the internet infrastructure of a rogue nation like North Korea, it's possible that they may also be interfering with ongoing efforts by legitimate agencies to spy and gather intelligence using similar vulnerabilities.
Maybe it's a better idea if all of us resist the urge to be an internet vigilante, and instead leave attacks on other states to our governments and intelligence agencies instead.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








