City of Dallas Hit by Royal Ransomware – Police Officers Return to Radios, Pen and Paper

A ransomware attack on Dallas (TX), one of the biggest cities in the US, this week compromised critical systems, including emergency services.
Hackers breached Dallas IT systems early Wednesday, affecting police communications and other services.
“Wednesday morning, the City’s security monitoring tools notified our Security Operations Center (SOC) that a likely ransomware attack had been launched within our environment,” city officials said in a statement.
The Mayor and City Council were notified of the incident in accordance with the City’s incident response plan.
“Subsequently, the City has confirmed that a number of servers have been compromised with ransomware, impacting several functional areas, including the Dallas Police Department Website,” the notice continues.
Police officers back to radios, pen and paper
According to CBS News, the attack forced 911 dispatchers to manually write down instructions for responding officers, while officers responded via personal phones and radios.
The City is now working with its “vendors” to prevent the spread, remove the malware from infected servers, and restore affected services, officials said.
The impact on City services for residents is limited, the statement says, adding that “should a resident experience a problem with a particular City service, they should contact 311.”
For emergencies, 911 is still available, the City says.
Royal ransomware
People familiar with the incident told news reporters that, during the attack, printers on the City of Dallas' network began spitting out ransom notes signed by the Royal cybercrime ring.
A photo of the ransom note signed ‘Royal ransomware’ was obtained by CBS Texas (reproduced below).
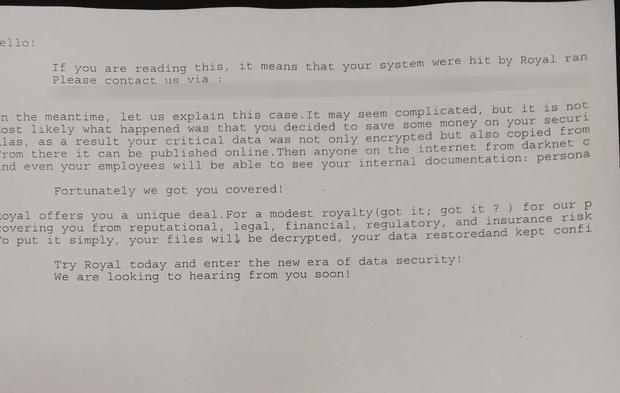
Credit: CBS News Texas
In typical fashion, the extortionists are threatening to leak data they said they stole from city servers prior to encryption. It’s unclear what (if any) such data was indeed copied before the malware started encrypting. Dallas officials make no mentioning of this possibility, but the attackers likely managed to copy at least some data before encryption.
The Royal hacking crew is said to be a respawn of the larger, now-defunct Conti cybercrime ring.
In February 2022, a Ukrainian security researcher obtained and leaked tens of thousands of messages from Conti internal gang chats, offering precious insight into the group’s Tactics, Techniques and Procedures (TTP).
In May of 2022, the US Department of State said it was offering a reward of up to $10 million for information leading to the identification or location of the operators of the Conti ransomware-as-a-service.
That same month, Conti announced through its official website that it was shutting down operations, though activity from its affiliates would allegedly continue.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








