Crypto-Doubling Scams on YouTube With a Twist: Cybercriminals Exploit The Attack on Donald Trump to Lure New Victims

Researchers at Bitdefender Labs are forever vigilant as they keep users up to date on the latest scams and internet perils that threaten their security and finances.
Stream-jacking attacks on YouTube used to conduct extensive crypto-doubling schemes are nothing new. Still, cybercriminals continue to improve and adapt their tactics to amplify their reach and success.
In a new crypto-doubling scheme, threat actors leverage the assassination attempt against former US President Donald Trump to lure new victims.
How the scam works
Our researchers have spotted dozens of hijacked YouTube channels that, since July 16, have been serving deep fake live streams of Elon Musk, purporting he will reveal insights into the assassination attempt.
While this is not specifically mentioned in the looped livestream videos, the channel descriptions provide additional insight into the Tesla CEO's alleged political affiliation and support.
“Elon Musk plans to provide about $45 million a month to a new political committee supporting former US leader Donald Trump as part of the presidential campaign #Tesla #Musk #Trump,” one of the descriptions reads.
Here’s a snippet from another hijacked channel:
“Former President Donald Trump was the target of an apparent assassination attempt Saturday at a Pennsylvania rally, just days before he was to accept the Republican nomination for a third time. Amidst a barrage of gunfire, a bloodied Trump, who reported being shot in the ear, was surrounded by Secret Service and hurried to his SUV, all while defiantly pumping his fist. Trump's campaign has since stated that the presumptive GOP nominee is doing "fine" after the shooting, which pierced the upper part of his right ear. The incident set off panic at the rally, with many attendees seeking cover from the unexpected violence. Billionaire Elon Musk reacted to the incident, stating Saturday evening that he "fully" supports Donald Trump. Musk's statement has added a new dimension to the unfolding events, as he also hinted at potential political endorsements in the upcoming election. #Tesla #Musk #Trump”
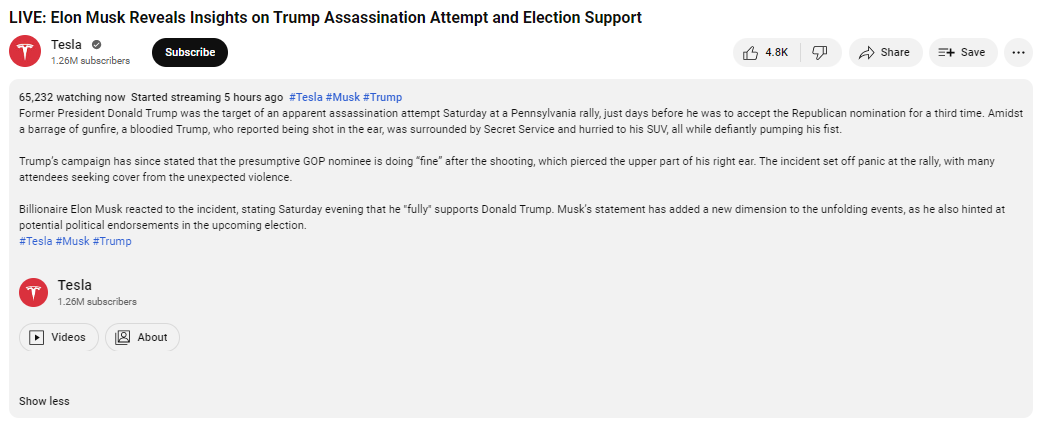
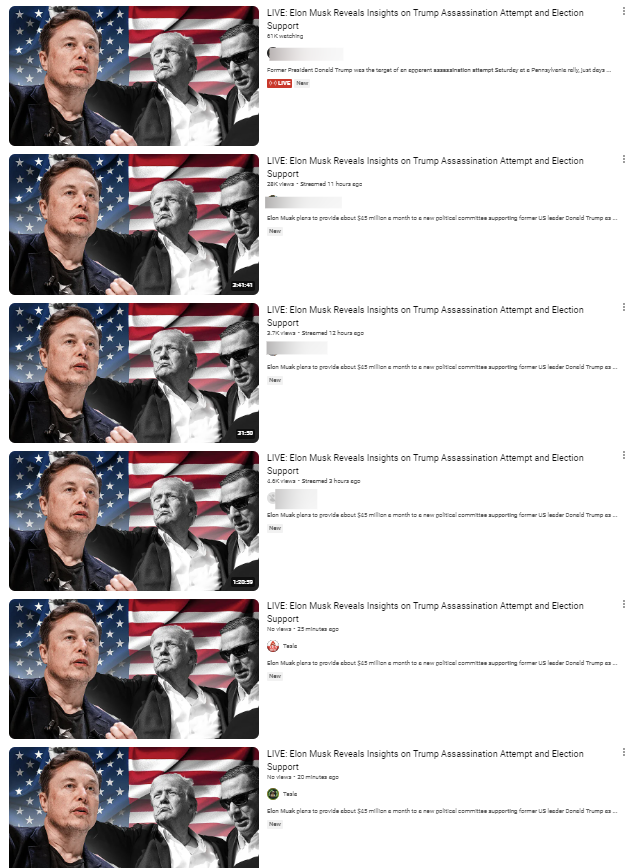
While not all the hijacked YouTube channels analyzed by our researcher Ionut Baltariu have had their names changed in the past 24 hours, some have been renamed “Tesla” or “Donald Trump Jr.”.
Additionally, the threat actors stripped some of the channels of their original videos and began livestreaming the same deepfake video promoting crypto-doubling offers under the name “Elon Musk Reveals Insights on Trump Assassination Attempt and Election Support.”
The potential reach of the scam is very troubling since one of the hijacked channels that began promoting the scams has 1.26 million subscribers. Other instances show a subscriber count of over 700,000 and in the lower ranges of 100,000.
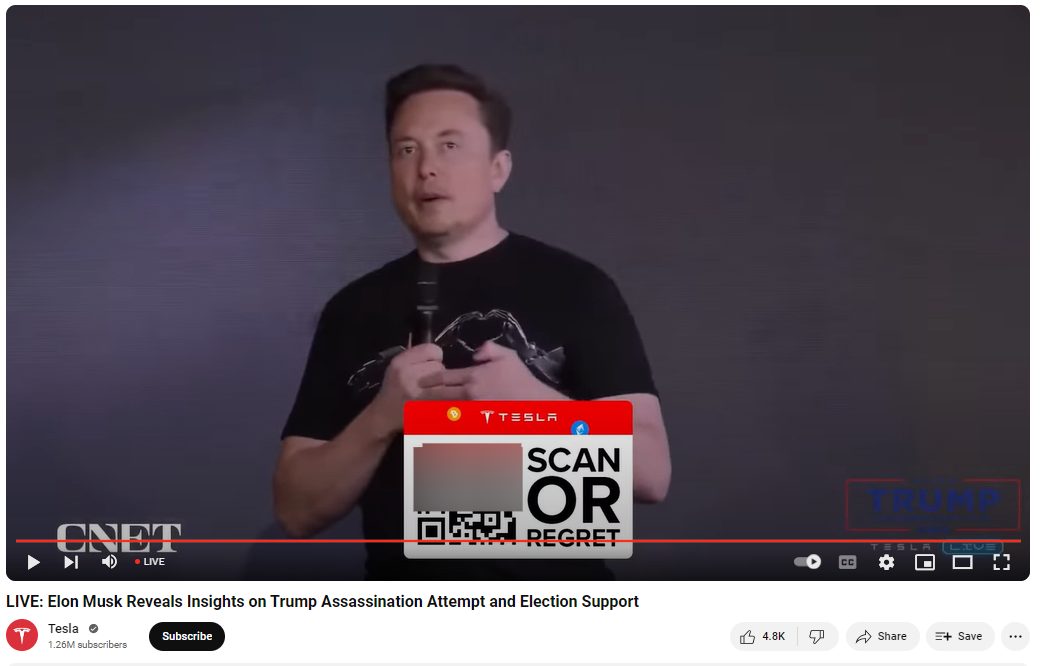
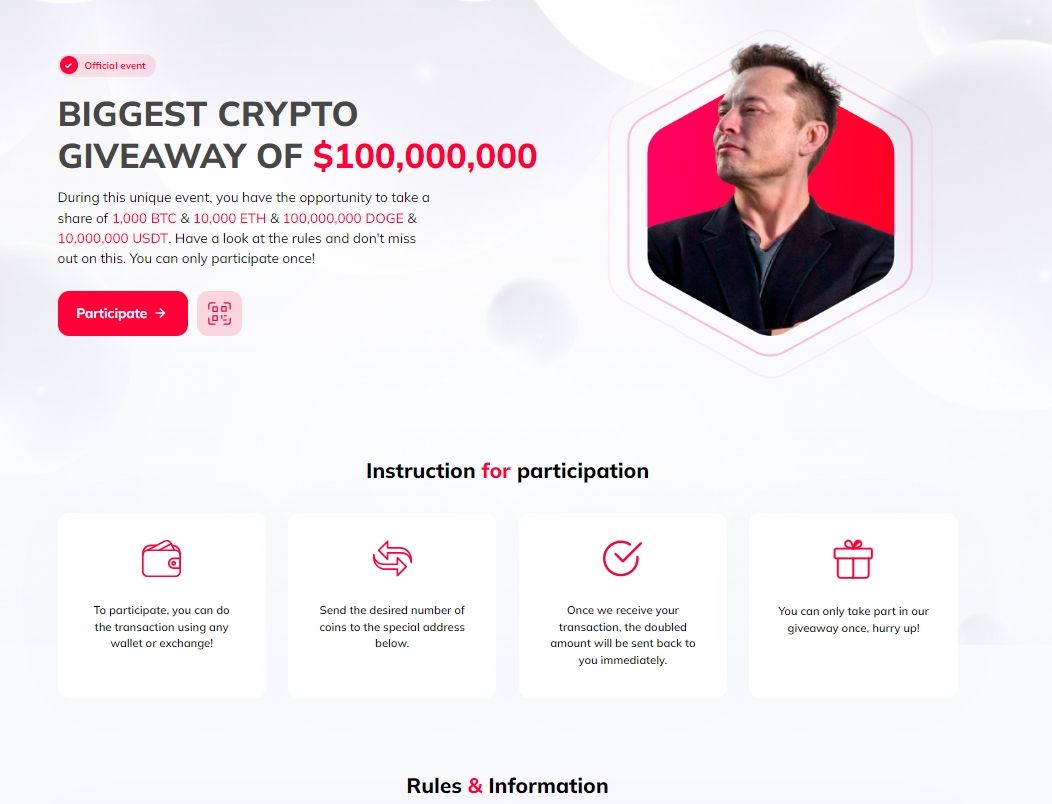
As previously stated, the broadcasts use the same looped deep fake video of Elon Musk encouraging his followers and the crypto community to participate in a giveaway by scanning the QR code embedded in the video.
Scanning the QR codes, which in some of the videos are positioned near a Donald Trump logo, direct users to fraudulent websites hosted on domains that resemble the name of the impersonated brand – in this case Tesla – or domains that associate both Musk’s and Donald Trump’s name.

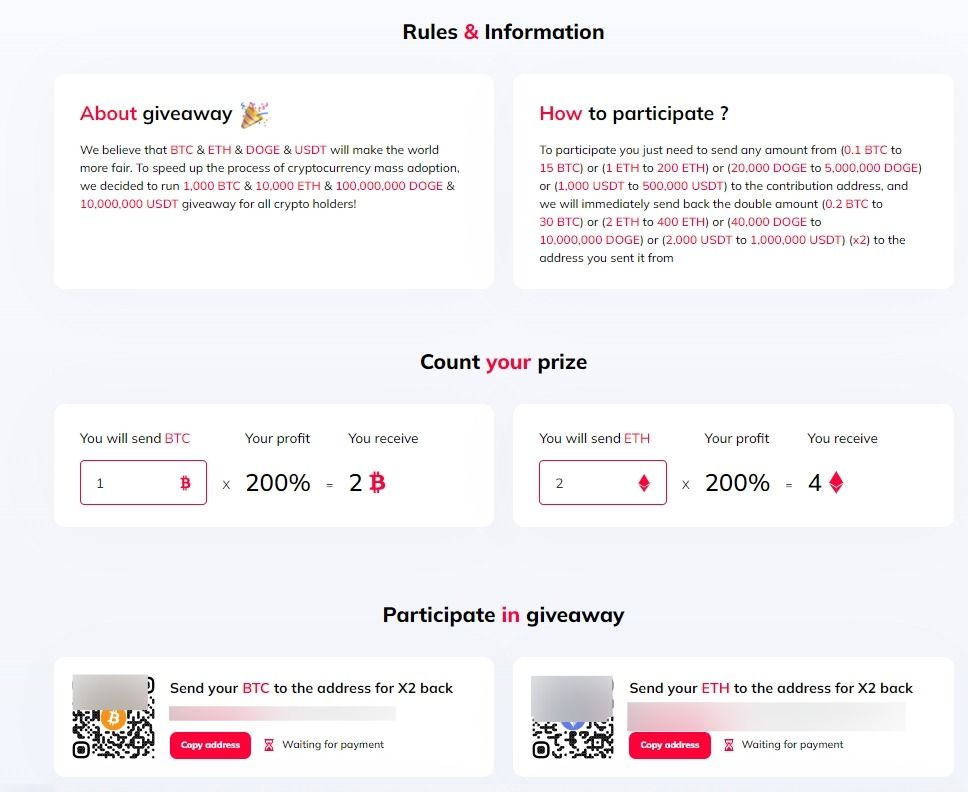
What can users do to protect against crypto-doubling scams
Vigilance and sticking to good cyber practices are key to preventing falling victim. We urge users to follow these recommendations to stay safe:
- Be wary of any videos and links with click-bait titles associated with Tesla or mentions of the attack on Donald Trump.
For this ongoing campaign, our researcher notes five malicious domains: musktrump[.]org, tesla-elon[.]gives, elomusk[.]finance, muskrise[.]io and taketesla[.]org – all of which are detected and blocked by Bitdefender anti-phishing and anti-fraud filtering systems.
- To keep YouTube accounts safe from hijackers, we recommend checking this dedicated guide.
- Scrutinize all messages and videos that promise you double return on your crypto investments
- Don’t scan QR codes in videos on YouTube that promise you too-good-to-be-true crypto giveaways
- Inspect YouTube channels that promote crypto giveaways for suspicious activity; some telltale signs include missing or deleted videos and closed comment sections
- Report suspicious activity to the platform or other relevant parties.
- Use a trusted and comprehensive security solution that can block phishing attempts and fraudulent links.
- When unsure about a QR code or promotion, request or link, use Bitdefender Scamio.
Send any texts, messages, links, QR codes, or images to Scamio, which will analyze them to determine if they are part of a scam. Scamio is free and available on Facebook Messenger, WhatsApp and your web browser. You can also help others stay safe by sharing Scamio with them in France, Germany, Spain, Italy, Romania, Australia and the UK.
If you are a content creator, your channel is your business and protecting it from hackers is essential. Bitdefender Security for Creators offers advanced hacking protection to safeguard your login credentials and personal data, ensuring you stay in control. It includes email phishing protection to guard you from fake sponsored offers, along with real-time monitoring of your YouTube channel that detects unauthorized access and suspicious activity. Don’t lose access to your account and your livelihood—stay protected 24/7 with a solution specially built to keep creators safe from cyber threats.
Note: The featured photo of this article was used by hijackers to promote their crypto-doubling scams on compromised YouTube channels.
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







