Europol Shuts Down Hackers’ Favorite VPN Service
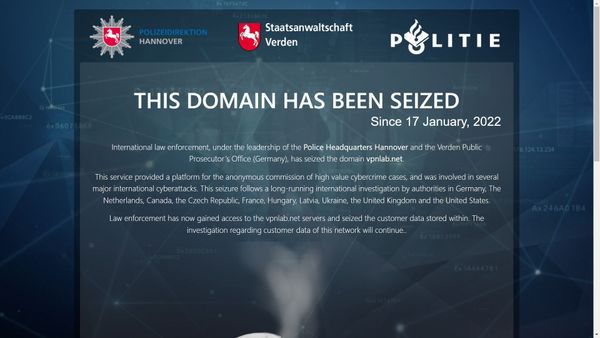
Europol earlier this week coordinated joint action to take down VPNLab.net, a VPN service frequently used to carry out cyberattacks anonymously.
The operation, on Jan. 17, involved simultaneous action from law enforcement agencies in 10 countries: the Netherlands, Germany, the Czech Republic, France, Ukraine, Latvia, Hungary, the UK, Canada and the US.
Authorities seized 15 VPNLab.net servers and took the service’s main website offline, rendering the platform inaccessible. They also notified more than 100 businesses that were potential cyberattack targets and are working with them to mitigate their exposure. Authorities didn’t disclose the names of the companies.
“Law enforcement took interest in the provider after multiple investigations uncovered criminals using the VPNLab.net service to facilitate illicit activities such as malware distribution,” according to a Europol press release.
Ukraine’s Cyber Police said that attackers used VPNLabs.net in more than 150 ransomware attacks and got roughly €60 million ($68.3 million) in ransom payments.
Threat actors frequently use VPN services to obfuscate critical data, such as their actual location and identity, and cloak their Internet activity by routing traffic through private, encrypted tunnels.
Compared to consumer-grade services, VPN solutions used in crime are generally slower due to the multitude of encryption layers and times they bounce connections.
VPNLab.net was a service established in 2008 that hackers often relied on to carry out cyberattacks. One of the most attractive features of this provider was double VPN, a feature that bounces the connection through two VPN servers in different countries instead of one.
The service was advertised on the dark web as relatively cheap, with an OpenVPN-based infrastructure and 2048-bit encryption. Reportedly, attackers used the service to set up infrastructures and communications in ransomware campaigns and deploy malware to the targeted systems without fear of detection.
tags
Author

Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








