Mac webcam hijack flaw wins man $100,500 from Apple
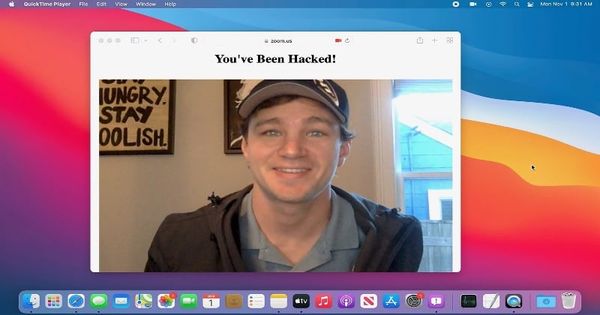
An independent security researcher has received a $100,500 bug bounty from Apple after discovering a security hole in the company's Safari browser for macOS that could allow a malicious website to hijack accounts and seize control of users' webcams.
Georgia Institute of Technology's Ryan Pickren, who is also the founder of BugPoC, uncovered a universal cross-site scripting (UXSS) flaw in Apple's Safari browser that could lead to serious security problems.
As Pickren explains in a technical blog post, the attack begins by tricking a potential victim into opening what they believe to be an innocent-looking .PNG image file.
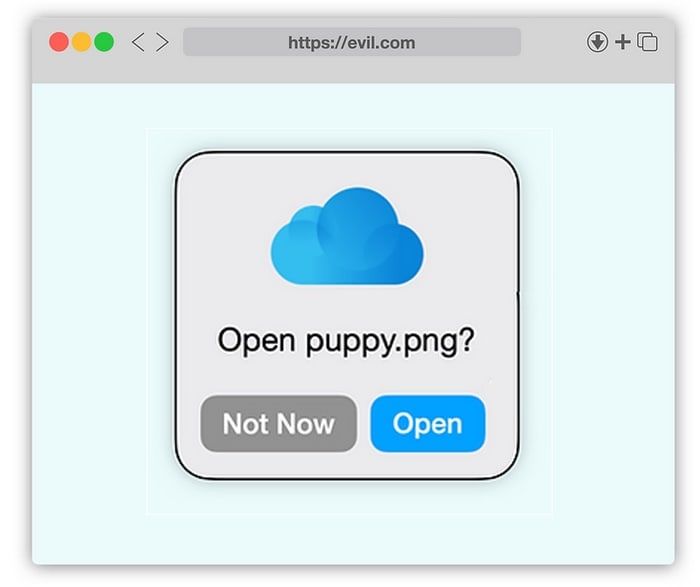
However, by exploiting features built into Apple iCloud and Safari that are trusted by macOS, unsuspecting users can end up with a malicious file running on their Mac, rather than opening a harmless image.
The end result is that an attacker could seize control of Safari, access any accounts that the user is logged into, and even access users' microphone and webcam.
In his blog post, Pickren describes how the UXSS attack could be used by an attack to inject arbitrary code into websites. For instance, JavaScript could be injected onto a trusted video chat website like Zoom to turn on the webcam.
Of course, such an attack doesn't prevent a Mac from displaying a green "on" light beside their webcam, but you have to wonder how many people would notice.
In addition, and perhaps more conventionally, an attacker could access any files stored locally on the victim's Mac.
Pickren's discovery is ingenious, and he pieced together a variety of flaws and features of macOS to "punch a hole in the browser":
"...the bug gives the attacker full access to every website ever visited by the victim. That means in addition to turning on your camera, my bug can also hack your iCloud, PayPal, Facebook, Gmail, etc. accounts too."
The good news is that there is no indication that anyone discovered the flaw before Pickren responsibly disclosed the problems to Apple in mid-July 2021. Security patches have now been issued for all of the vulnerabilities, preventing future exploitation.
The researcher appears to have, at least in part, built his latest webcam hijack on the foundations of a previous webcam-hijacking vulnerability he found a year ago, that netted him $75,000 from Apple.
As a student Pickren managed to earn 15 million air miles through the United airlines' bug bounty program, donating half to Georgia Tech and a further 2.5 million more to Make-A-Wish America.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks