Phishing Scams: How to Identify and Avoid Them

The cybersecurity landscape is as complex as ever, with scammers employing advanced tools to prey on the sensitive information of companies and individuals alike.
New challenges arise as we switch to the online world and adopt marvels in innovation such as AI technology. These include advanced phishing scams that aim to empty victims of their money and confidential information.
We believe in tech for good, which is why we're here to help you outsmart online scammers and shield yourself against any phishing attempt. For this reason, we've put together this all-in-one guide to spotting and avoiding phishing scams. Let's get into it.
What Are Phishing Scams?
Phishing scams are illegal, deceptive, and fraudulent attempts by cybercriminals, such as scammers and hackers, to obtain and exploit sensitive information, including personal and financial data. A phishing scam occurs through an email or text message, a suspicious website, a voice message, and other means.
For example, you might receive an email that appears to be from a reputable company like your bank or a government agency. But beware—it's designed to steal your personal information.
Phishing attacks are popular among cyber scammers, who will use any opportunity to catch their victims off guard and steal their data. In fact, reports show that as of 2023, phishing is by far the most common form of cybercrime registered, affecting more than 298,000 people.
What Are Phishing Scams Trying To Do?
Phishing scams involve tricking you into disclosing confidential information. Scammers use various methods to appear convincing, such as forging email addresses and creating fake websites that mirror legitimate ones.
For example, you might receive an email that claims to be from your financial institution, urging you to click on a link to verify your account information. The link leads to a phishing website that looks nearly identical to the actual site, but inputs here are sent directly to the scammer.
Then, scammers will use your sensitive information to perform malicious actions, such as:
● Identity theft––this happens by obtaining your personal and financial information, like Social Security, national ID numbers, or account details, which can be used to steal your identity.
● Financial fraud––when scammers access your bank account numbers or credit card details to siphon off funds or make unauthorized purchases.
● Credential theft––by capturing usernames and passwords to hack into your accounts, scammers pave the way for larger and more damaging data breaches.
How to Identify Phishing Emails - Common Elements
Phishing attacks are designed to trick you into giving up sensitive information. Here are some common elements to watch out for:
● Urgent requests for personal information––Phishing emails often create a sense of urgency to prompt immediate action. Look for messages that demand quick responses or threaten consequences if you do not comply right away.
● Suspicious email domains––Always examine the sender's email address. While the display name might appear legitimate, the domain (e.g., @yourbank.com vs. @your-bank-secure.com) may have subtle differences.
● Poor grammar and spelling––Legitimate organizations have proofreading processes in place. Emails filled with grammatical errors, awkward phrasing, or spelling mistakes indicate a phishing attempt.
● Links to fake websites––Phishing emails frequently contain links that direct you to counterfeit websites. These sites can look almost identical to the legitimate ones. Hover over links to see the actual URL before clicking. If it looks suspicious, avoid it.
● Unsolicited attachments–Be cautious when handling unexpected attachments from unknown or suspicious senders. These attachments may contain malware designed to steal your data or harm your device.
● Too-good-to-be-true offers––Phishing emails may promise remarkable rewards or significant financial gains for minimal effort. If an offer sounds too good to be true, it probably is.
● Inconsistent branding––Look for inconsistent logos, colors, or design elements that do not align with the company's usual branding. Phishing attempts lack the polish of genuine corporate communications.
● Requests for sensitive information––Legitimate organizations don’t ask for sensitive information (like passwords or ID numbers) via email. Be wary if you receive such a request.
● Generic greetings––Phishing emails tend to use generic greetings like "Dear Customer" instead of your actual name. Authentic emails from companies you do business with use personalized greetings, more often than not.
Types of Phishing Scams
1. Email Phishing
Email phishing is the most common form of phishing, aiming at stealing credentials, prompting an action such as clicking a link, or delivering malware. Scammers send fraudulent emails designed to look like they come from a reputable company, a legitimate website, or a professional official.
Common characteristics include:
● Emails may claim your account is compromised or require immediate action with a sense of urgency, discouraging you from verifying the credibility of the information or the source.
● The sender's email address might mimic a legitimate domain but contain subtle differences, such as an added or missing letter, character, or symbol.
2. Spear Phishing

Spear phishing is a targeted phishing attack aimed at specific individuals within an organization or the company itself, using detailed information the scammer has gathered to make the email more convincing.
These emails often contain details about you, like your name or job title, while the phishing message looks well-structured. Such phishing attacks are difficult to spot, as they resemble internal emails, such as from the HR department, or mimic legitimate sources (almost) perfectly.
Look for suspicious email addresses, unreasonable urgency in the tone of voice, language errors, and other means of detection to spot a spear phishing scam.
3. Smishing (SMS Phishing)

Smishing is a type of phishing scam where cybercriminals use SMS text messages to deceive you into revealing personal and financial information. These messages often appear to come from delivery companies, present promotional offers or giveaway wins, ask for a donation, or check for an emergency that just happened.
As a rule of thumb, if you receive a text from an unfamiliar number, it should immediately raise a red flag. Phishing messages often contain links that redirect you to fake websites designed to steal your data, so never click on an unsafe link before verifying its legitimacy.
To accurately spot any phishing scam, use Scamio––the free AI-powered Bitdefender assistant that helps you detect and avoid phishing attacks by simply copying and pasting the potential threat into the detector.
4. Vishing (Voice Phishing)

Vishing, or voice phishing, occurs when scammers make phone calls to trick you into revealing personal or financial information. Typical signs include urgent requests for sensitive data and threats of legal trouble if you don't comply. Always verify the caller's identity before disclosing any information over the cell phone or asking to call their central branch of another phone number to reach them back.
With vishing, scammers pretend to be legitimate entities such as your bank or a government agency asking you to verify your information.
With the rise of AI deepfakes, this type of phishing attack has reached unprecedented heights, as scammers recreate the voice of close friends, family members, or familiar individuals to trick people into quickly sending out money to a source or revealing account numbers.
5. Clone Phishing

Clone phishing involves duplicating a genuine email and replacing links or attachments with malicious ones. Watch for minor variations in the sender’s email address and unexpected follow-up emails with new attachments or links to avoid falling victim to this type of phishing attempt.
If you receive an email that seems to be a follow-up to a legitimate conversation but with new, malicious attachments, double check the URL link and sender email, then scan the attachment.
6. Whaling

Whaling targets high-profile individuals, such as executives, through highly personalized attacks. Common tactics include posing as the CEO to request urgent fund transfers or as legal advisors threatening dire consequences.
● One notorious example of whaling happened in 2016, when a scammer posed as the FACC company's CEO, instructing an individual in the financial department to wire $42 million to the attacker's account.
● More recently, a Hong Kong finance professional at a multinational company was deceived out of $25 million by scammers using a deepfake of his London-based CFO during a video call.
Whaling is dangerous––always verify suspicious requests through multiple channels to avoid falling victim to such identity theft attacks.
7. Pharming

Pharming redirects users from legitimate websites to malicious ones without their knowledge. To spot scammers and phishing websites, always check the URL for accuracy and ensure it begins with 'https://'. Minor misspellings can also indicate a suspicious site.
With pharming, attackers alter the host file that maps domain names to IP addresses or the domain name system, redirecting users from legitimate companies to malicious sites.
Pharming happens through malware or unauthorized access installed on your computer, likely through a malicious email message you've clicked.
7 Examples of Phishing Scams to Watch Out For
Each form of phishing comes with its own dangers and red flags. However, some phishing emails, mobile device calls, or SMS texts are more common than others. Let's explore some common examples of phishing scams you should be aware of.
1. Fake financial institution notifications
You receive an email that looks like it's from Wells Fargo with the subject line: "Urgent: Verify Your Account Now." The email says, "Dear Customer, We've noticed unusual activity on your account. Please click the link below to confirm your details." The link directs you to a fake Wells Fargo login page where you type in your credentials, and they get stolen.
How to spot it:
● Check the URL. Ensure the web address matches the official bank URL.
● Verify with your bank by calling or visiting to confirm.
2. Phony account alert from a reputable company
You get an email from a sender appearing as "[email protected]" with the subject: "Apple ID Locked." The email states, "Your Apple ID has been locked for security reasons. Click here to verify your identity." This link takes you to a fake Apple login page. What you don't know is that the email address has been forged.
How to spot it:
● Check the sender’s email address for minor variations.
● Visit Apple’s official site directly to check your account status.
3. Government agency impersonation
An email appears from "[email protected]" stating: "Immediate tax refund available. Verify your identity to claim your refund now." It asks for your Social Security number and bank details through a provided link which steals your information.
How to spot it:
● The Internal Revenue Service, or financial institutions in general, don't initiate contact via email or ask you for such details.
● Verify independently by using the IRS official website or contact number.
4. False prize notifications
You receive an SMS saying, "Congratulations! You've won $1,000,000 in the Mega Millions Lottery. Click here to claim your prize," directing you to a page asking for your banking details to transfer the winnings.
How to spot it:
● It's highly unlikely to win if you haven't entered any competition.
● Go directly to the official site or call the institution if you must verify.
5. Bogus support requests
Tech email scams or support calls are popular, so be aware of calls from individuals pretending to be from, let's say, Microsoft Support, saying, "We have detected a virus on your computer. Allow us remote access to fix the issue." Then, these malicious actors proceed with installing malware on your computer.
How to spot it:
● Tech companies don't usually call you first. What's more–they don't ask for remote access to your computer.
● Hang up and verify, then call Microsoft directly using official contact details.
6. Malicious links in social media messages
Your friend’s Facebook account appears to send you a message saying, "Look at these funny pictures of you!" with a link. The link installs malware on your device.
How to spot it:
● Check the tone of voice or language. Does it match your friend's usual choice of words?
● Confirm with the person by reaching out to them via another method.
● Look at the link for signs of suspicious URL clues.
7. Mock investment or job opportunities
An email from "[email protected]" or "[email protected]" claims "Invest in our brand-new tech and double your money in a month! Transfer your funds to our secure account to get started." or "We love your LinkedIn profile. Reach out for this job opportunity we have for you."
How to spot it:
● Too good to be true? Promises of quick, high returns are suspect.
● Research independently. Verify the sender, the information, and peer reviews on forums through credible sources.
How to Avoid Phishing Scams
There are several ways to keep phishing attacks at bay, including treating any text message, email, or odd call with a healthy dose of skepticism. Most importantly, consider using anti-malware software to protect yourself from phishing scammers.
Stay informed about the latest phishing techniques
Regularly check the Anti-Phishing Working Group (APWG) website and sign up for alerts. This non-profit organization provides updates on emerging phishing threats and offers resources to help you stay one step ahead of scammers.
Use multi-factor authentication
Multi-factor authentication (MFA) adds an extra layer of security by requiring two or more verification methods to access your accounts. Enable MFA on your email, banking, and social media accounts.
Install and update anti-phishing software
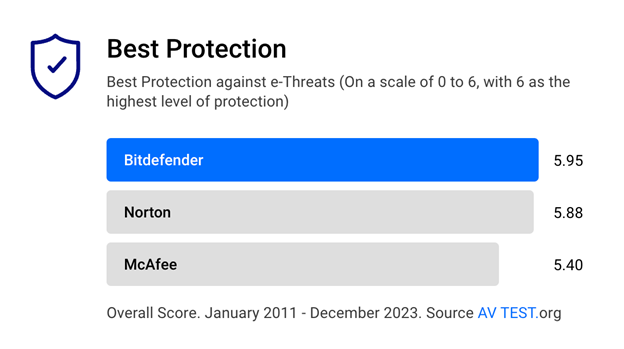
Use top-performing anti-phishing software like Bitdefender, which can alert you to malicious websites and emails. Regularly update our software to ensure you're protected against the latest threats.
Did you know that Bitdefender Total Security automatically detects and blocks fraudulent and suspicious websites that aim to steal financial data such as passwords or credit card numbers?
Regularly Monitor Your Financial Statements
Check your account statements frequently for any unauthorized transactions or suspicious activity like large transactions, odd online payments, or physical payments made outside your current location. Early detection allows for better reporting and mitigation. Set up alerts with your bank to notify you of any unusual transactions.
Protect your email inbox and phone number
Filter out spam and phishing emails. For Windows users with Microsoft Outlook and Mozilla Thunderbird, activate Bitdefender Antispam. Apple users should report suspicious emails by forwarding them to [email protected] for investigation by Apple. Make sure to include the full header information.
Regarding your phone number, upload it to the Do Not Call Registry if you want to dodge phone calls from scammers.
What to Do If You Fall Prey to a Phishing Attack
Report phishing scams to the Anti-Phishing Working Group by forwarding any suspicious emails to [email protected]. If your work email has been compromised, reach out to your IT or cybersecurity department ASAP.
Disconnect from the internet and secure your device by scanning it with antivirus software, then contact your financial institution to report the incident and freeze your accounts. Update compromised credentials and set stronger passwords to avoid repeating this incident.
Don't Let Scammers Get to You––Protect Yourself from Phishing Scams with a Foolproof System
With a global average cost per data breach around $4.45 million, it's time for both organizations and individuals to take this evolving issue seriously.
Here are key takeaways to help you prevent phishing attempts:
● Phishing scams are on the rise, and scammers are getting smarter. Your concerns are valid and you should treat them with urgency, even in case of false alerts.
● Keep up to date with the latest phishing techniques.
● Use multi-factor authentication for added security.
● Use proper software to spot and avoid such scams and keep it updated.
To enhance your defense against phishing scams, consider integrating Bitdefender into your security stack. We offer advanced protection by identifying and blocking phishing attempts in real-time, keeping your sensitive data safe.
Try Bitdefender––the foolproof system against cyber threats that keeps your digital experience secure.
FAQs about Phishing Scams
How do phishing scams work?
Phishing scams trick you into providing personal or financial information using deceptive emails, text messages, emails, calls, social media accounts, or websites. Scammers pose as legitimate entities to create urgency or fear, prompting clicks on malicious links.
What do phishing scams steal?
Phishing scams steal sensitive data, such as usernames, passwords, Social Security numbers or national ID numbers, bank details, or other important information. The stolen data is then used for identity theft or financial fraud.
What are the most common signs of phishing scams?
Common phishing signs include unexpected information requests, urgent language, suspicious email domain addresses or websites, and poor grammar. The provided links direct to fake sites, which you can spot by hovering above the URL or testing the legitimacy through free tools like Scamio.
tags
Author

The meaning of Bitdefender’s mascot, the Dacian Draco, a symbol that depicts a mythical animal with a wolf’s head and a dragon’s body, is “to watch” and to “guard with a sharp eye.”
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








