QNAP warns of new DeadBolt ransomware attack locking up NAS devices

Owners of NAS drives manufactured by QNAP have been advised that the company is "thoroughly investigating" reports that a new variant of the DeadBolt ransomware is targeting devices, locking up data and demanding victims pay a fee to extortionists.
According to QNAP, the NAS devices that have been hit by the attack to date are running an outdated version (4.x) of its QTS operating system.
Details are limited, but it appears that a security vulnerability in older versions of the QNAP QTS operating system have allowed unauthorised parties to gain remote access to device's across the internet.
Having gained access, the malicious hackers are able to run their DeadBolt ransomware across victim's drives, encrypting their documents, photographs, spreadsheets, movies, and other data.
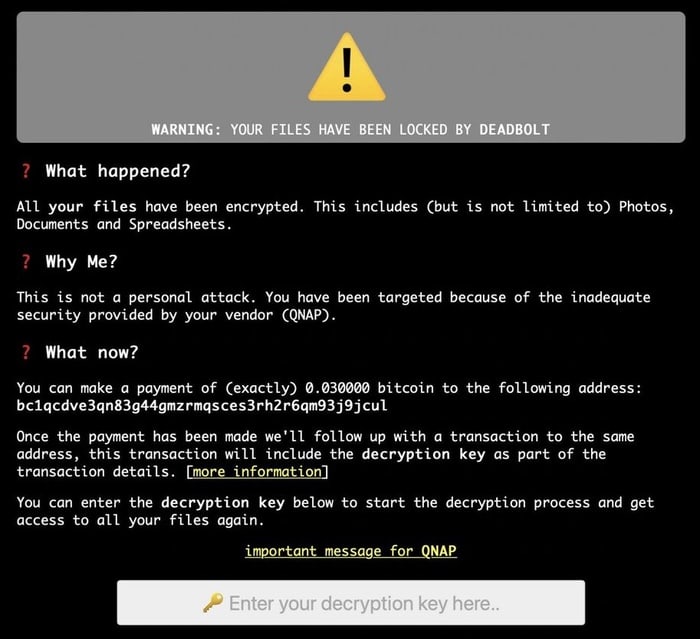
In an advisory published on its website, QNAP recommends that at-risk customers update QTS or QuTS hero to the latest version immediately.
However, the company says that if you are unfortunate enough to have already had your NAS drive compromised by the DeadBolt ransomware, to take a screenshot of the ransom note (including the Bitcoin wallet address to which you are being told to send the ransom) before you upgrade the device's firmware:
If your NAS has already been compromised, take the screenshot of the ransom note to keep the bitcoin address, then, upgrade to the latest firmware version and the built-in Malware Remover application will automatically quarantine the ransom note which hijacks the login page.
Updating QTS or QuTS hero can either be done via the NAS device's administrator interface, or via manually downloading the latest version from the official QNAP website.
This is not the first time that QNAP has warned its customers of ransomware attacks locking up their devices. In January, for instance, QNAP first warned that the DeadBolt ransomware was exploiting security holes in order to display a ransom note at login.
The DeadBolt ransomware was then seen targeting owners of another range of NAS drives, Asustor.
NAS drive owners would be sensible to defend their devices behind a firewall – unless they feel confident that a security vulnerability that could grant access to cybercriminals is not lurking deep inside.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








