Ransomware Attacks on Home Users Are Frighteningly Common, Bitdefender Data Reveals. Here Are 3 Tips to Stay Safe at Home

Although the media focuses on ransomware attacks on businesses, many attacks still quietly unfold in the consumer space as well. Bitdefender data shows the most notorious names in ransomware now dedicate a considerable portion of their resources to hitting home users.
Bitdefender data collected between September 2021 and September 2022 shows that the 20 most-detected ransomware families or strains often rear their ugly heads in attacks on households.
For example, in September 2021 the infamous WannaCry was detected as the most common ransomware family to attack regular users, with a 36% share globally. In other words, WannaCry operators dedicated more than a third of their activity solely to targeting regular Joes and Janes.
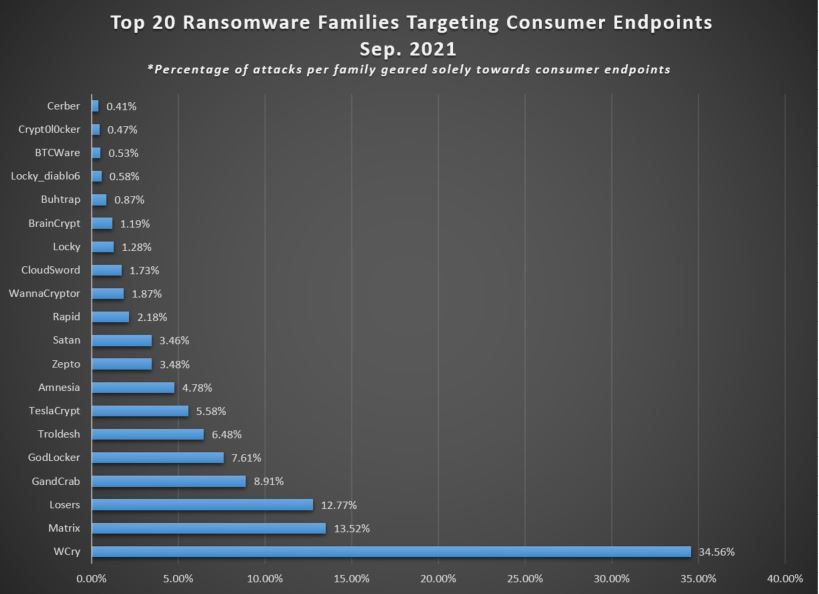
'WCry' and 'WannaCryptor' are variations of the infamous WannaCry, comprising a 36,43% share of ransomware attacks targeting consumer endpoints globally in Sept. 2021.
Credit: Bitdefender
A year later (second chart below), that figure jumped to 77%, meaning even fewer WannaCry campaigns focused on the big fish – all while not even making the top spot. CryptoShield operators take the lion’s share this year, with a whopping 82% of attacks geared towards the small fry.
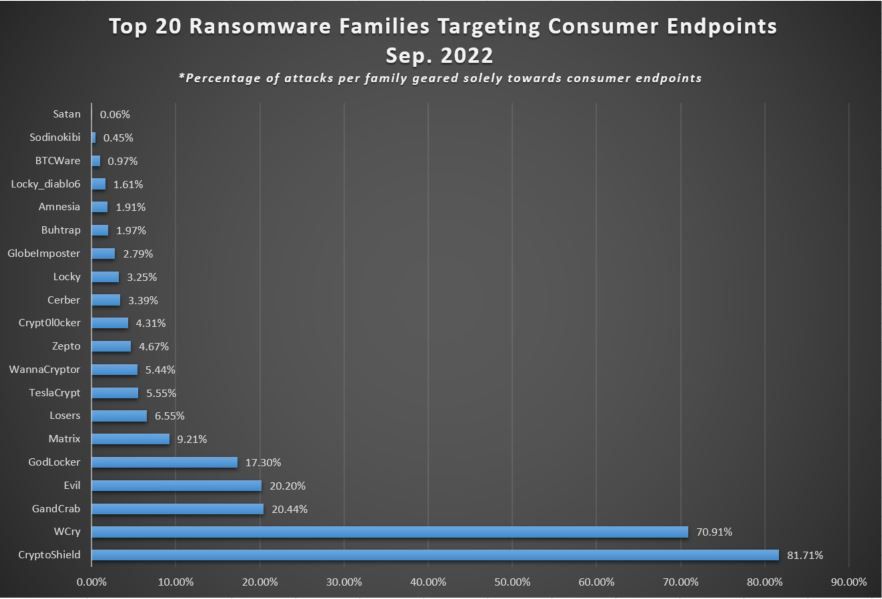
'CryptoShield' stands out as the most commonly-detected ransomware family targeting home users in Sept. 2022.
Credit: Bitdefender
The charts above list many other common names on the ransomware scene. A deeper analysis might warrant a separate article.
Ransomware attacks on common households
Most cyber-news headlines cover ransomware attacks on businesses, healthcare, governments, education, and critical infrastructures. And for good reason, too. These oft-crippling incidents affect millions of people at a time. Some rattle entire economies. But little do home users suspect just how often these threats lurk in shady places on the open internet, waiting to spring to life when someone clicks the wrong link.
As we discuss in our latest Consumer Threat Landscape Report, warez sites, torrents, and even legit-looking websites can harbor Trojans that phone back to base and fetch ransomware as a secondary payload to deploy on the victim’s computer.
Some hacking crews go straight for the kill, targeting vulnerable devices directly with their data-crippling malware. For example, QNAP customers have seen a fair share of attacks targeted at them in the past 12 months from a particular ransomware gang known as Deadbolt. Those wielding the malware specialize in exploiting misconfigurations and unpatched flaws in the Taiwan-made network attached storage devices.
Fighting ransomware at home
1. Practice good cybersecurity hygiene
Avoid pirated content! Don’t visit dodgy sites. Don’t run software downloaded off warez sites. And take torrents with a boulder of salt. Keep an eye out for scams, phishing and spam email. While most will try and steal your passwords, some will downright trick you into running the malware yourself. Always run official software from legit vendors. More often than not, it’s what you choose to do online that makes the difference between safety and danger.
2. Keep regular offline backups
It’s not unheard of to get infected with malware even if you practice good cybersecurity hygiene. It can happen simply by installing a tainted patch or utility app. That’s why it’s important to never let your guard down and back up your important files periodically. Keep those backups offline on a separate drive in case the worst happens.
3. Have AV running on your system
For maximum protection, keep a trusted security solution running on your system at all times. Bitdefender Total Security offers multi-layer ransomware protection, keeping you safe even when your eye is off the ball.
#NoMoreRansom
For the past six years, NoMoreRansom has helped victims get their files back through the efforts of 188 partners who pledged to curb the proliferation of ransomware. As a prominent contributor to this initiative, Bitdefender has submitted 13 decryption tools for 11 ransomware families. Downloaded roughly a million times, our free decryptors have helped private citizens and companies escape an estimated US $1 billion in ransom demands.

tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
Your Device ‘Fingerprint’ Will Go to Advertisers Starting February 2025
December 24, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks