Ransomware via a call centre? BazaCall means no email attachment or link required for infection
Unsuspecting users of Office 365 are being tricked by a cybercriminal gang into calling a bogus call centre, with the eventual intention of installing ransomware onto their computers.
Microsoft has warned that fraudulent emails are being sent out, attempting to trick users into calling a phone number operated by a cybercrime group.
Examples shared by experts at Microsoft include emails that pose as coming from a photo editing service or recipe website.
On some occasions the emails may not purport that the trial is about to expire, but instead claim to be confirmation that a software license has been purchased.
Various social engineering disguises are used to encourage unsuspecting users to call, including claims that a trial subscription is expiring and an individual's credit card will soon be automatically charged.
The important thing to recognise here is that the emails do not have an attachment, and do not have a link for the user to click on. Instead they merely offer a phone number for recipients to call if they wish to make a query.
Users trained to be wary of unsolicited links and email attachments may believe that calling a phone number is safe - after all, what's the worst that can happen?
And if you do call the number, you are put through to a human-operated call centre for a website. There may even exist a website which appears legitimate.
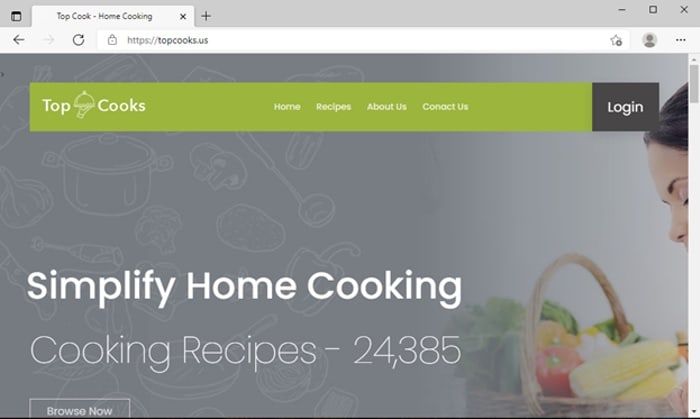
So it's quite understandable that you may believe that you are speaking to a legitimate organisation, but in fact the website and call centre has been set up by BazaCall's operators.
As security experts warn, the call centre agent then tells the caller to visit the account page of the website and download a macro-enabled Excel spreadsheet in order to cancel the subscription.
Microsoft's experts claim that the call centre support agents may even talk the intended victim through ignoring warnings if any are displayed by their security software as the spreadsheet is downloaded, in order to ensure that malicious code can be run.
People are much more likely to do something dangerous to their computer's health when told to by another human than by a computer it seems.
Once opened the Excel spreadsheet claims to be protected, and tells users to "Enable Content" in order to view its contents.
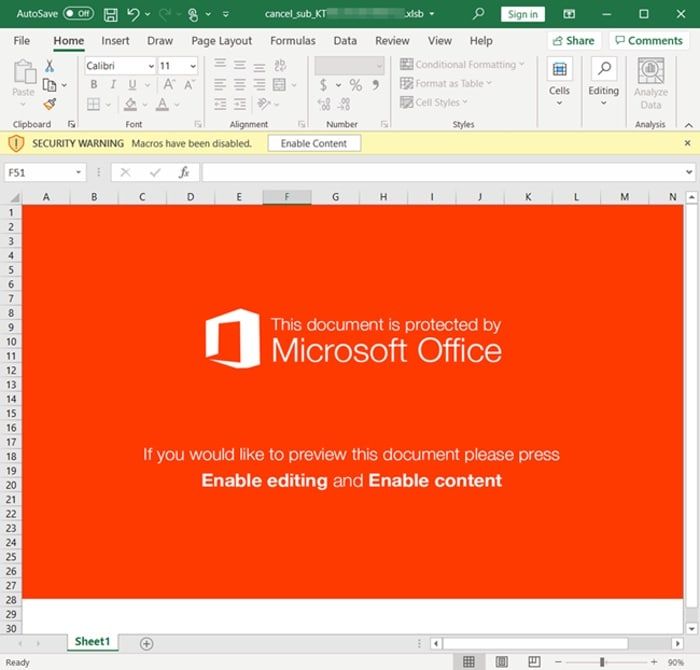
This is a fairly typical social engineering trick often users by malicious hackers to trick users into circumventing security features built into Office products.
The eventual aim is for the macro code hidden within the Excel spreadsheet to download the BazaLoader malware from the internet, and create an opening through which a malicious attacker can control the user's PC.
Often the intention might be to steal information from the compromised PC, but the remote access can also be used to activate ransomware.
Microsoft's experts say that the planting of ransomware has made BazaCall more dangerous than previously consider, and notes that it has seen attackers exfiltrating data or installing ransomware within 48 hours of initial contact with an unsuspecting user:
"Apart from having backdoor capabilities, the BazaLoader payload from these campaigns also gives a remote attacker hands-on-keyboard control on an affected user's device, which allows for a fast network compromise. In our observation, attacks emanating from the BazaCall threat could move quickly within a network, conduct extensive data exfiltration and credential theft, and distribute ransomware within 48 hours of the initial compromise."
Be sure to tell your friends, families, and work colleagues that it's not just emails with linsk and attachments that pose a danger - there's also real risk in the emails that may only contain a phone number as well.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








