Sideloading Android Apps - Bane or Blessing for Android Users

The ability to install apps on Android phones is a strength of the operating system, and a feature that sets it apart from its main counterpart, iOS. Unfortunately, it also introduces a security weakness that attackers often try to exploit. There’s no reason to fear this feature if you follow a few simple rules, however.
One of the main ways attackers infect Android devices is through social engineering, by persuading people to install the malware themselves. The installation process is possible through sideloading, which means that an app is manually installed without involving the Google Play Store.
The official store offers a higher degree of protection, as Google scans all apps made available to users. A few might fall through the cracks, but installing third-party packages is a lot riskier.
What’s so good about sideloading?
There are numerous scenarios in which the ability to install apps manually is valuable. Sometimes, users might want to install an older version of an app because the newer ones no longer have support for a particular device. Or maybe they want to install an app that’s not available in their country or region. It’s also possible that an update for an app crashes on some devices or the developers remove helpful functionality.
No matter the reason, the ability to manually install an application can be beneficial. Also, the fact that it’s not enabled by default and that users can control each step of the process makes it secure enough to justify its continued existence.
The dark side of sideloading
The same feature that helps so many Android users is also a primary weapon attackers use in their campaigns. Criminals often focus their entire effort on persuading people to install third-party apps, usually by tricking them with some “legit” procedure to follow.
One of the more recent campaigns using this tactic was spotted just a few months ago, with attackers trying to trick people into installing fake apps that actually deployed Teabot and Flubot malware. This is a huge security problem, especially for users with unprotected devices or who don’t know that installing apps from outside the ecosystem is not recommended unless you know what you’re doing.
Knowledge is part of cybersecurity
Educating Android users about this particular feature and its problems is the first step towards better security on mobile devices. Since the option to install third-party apps is disabled by default on all new Android devices, a simple golden rule should help curb or defeat many active or future malware campaigns.
If you are ever presented, as a user, with a request to enable the “Install unknown apps,” always say no. Regular users never need to enable this option unless they already plan to install a package manually. Please remember that the option is available for any installed and capable app; it’s not a general setting.
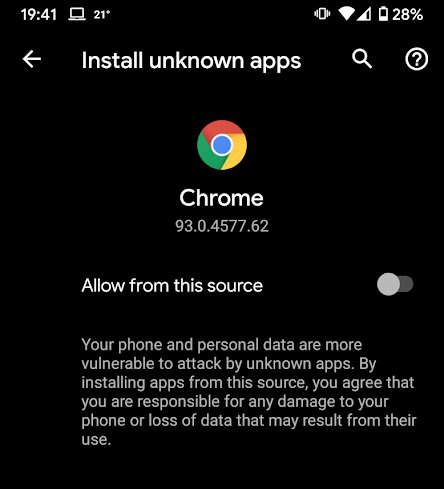
Of course, most, if not all, security issues would not exist on mobile devices also running the “Bitdefender Mobile Security & Antivirus,” including installing third-party packages, following up on malicious links, or downloading infected files, to name a few.
The solution to the problem raised by the “Install unknown apps” feature is not to eliminate it but to equip people with the right security tools and the knowledge to safely use their devices.
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








