Twilio reveals hackers compromised its systems a month earlier than previously thought

Readers will recall that cloud communications firm Twilio disclosed on August 7 2022 that hackers had accessed user data following a sophisticated social engineering attack that saw employees targeted with SMS-phishing ("smishing") text messages.
Attackers sent current Twilio staff and former employees SMS text messages that purported to come from the company's IT department, telling them that their passwords had expired.
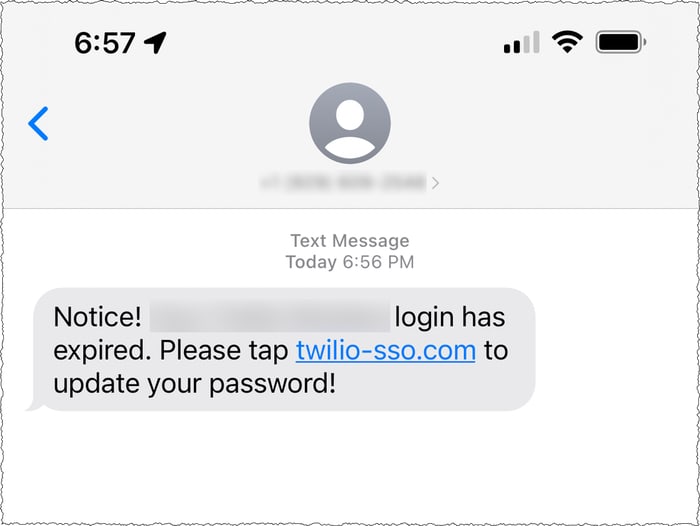
Clicking on the link in the messages had taken unsuspecting individuals to a fake Twilio login page, where they entered their credentials and allowed hackers to gain access to customer data.
Now, following the conclusion of an investigation into that incident, Twilio has revealed that the same malicious hackers had tricked an employee into providing their password through a voice-phishing attack on June 29 2022:
"Our investigation also led us to conclude that the same malicious actors likely were responsible for a brief security incident that occurred on June 29, 2022. In the June incident, a Twilio employee was socially engineered through voice phishing (or ‘vishing’) to provide their credentials, and the malicious actor was able to access customer contact information for a limited number of customers."
Of course, it matters little if a security incident was "brief" or not, if your attackers manage to get away with the information that they wanted.
And there are still some troubling things to read in Twilio's incident report. For instance, the company first announced that it had suffered a security breach on August 7 2022, but has only this week disclosed that it "last observed unauthorised activity" on its systems a full two days later on August 9.
Concluding its investigation into the breaches, Twilio says that 209 customers and 93 end users of its Authy two-factor authentication app had their accounts impacted by the attack.
The attacks against Twilio were part of a much larger campaign, dubbed "0ktapus" by security researchers, that compromised over 130 organisations.
The encrypted messaging service Signal, for instance, reported that approximately 1,900 of its users could potentially have been affected as a result of the Twilio breach, although their message history and contact lists would have remained safe.
Twilio says it has taken steps to reduce the efficacy of smishing and vishing attacks in future, by putting in place additional security measures including:
- Implementing stronger two factor precautions and distributing FIDO2 tokens to all employees;
- Implementing additional layers of control within our VPN;
- Removing and limiting certain functionality within specific administrative tooling;
- Increasing the refresh frequency of tokens for Okta-integrated applications;
- Conducting supplemental mandatory security training for all employees regarding attacks based on social engineering techniques.
Twilio says it is "very disappointed and frustrated" about the incident, and has apologised to customers. It says it is "making long term investments to continue to earn back the trust of our customers."
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








