UK police reveal they are running fake DDoS-for-hire sites to collect details on cybercriminals
There's bad news if you're someone who is keen to launch a Distributed Denial-of-Service (DDoS) attack to boot a website off the internet, but don't have the know-how to do it yourself.
Rather than hiring the help of cybercriminals to bombard a site with unwanted traffic or kick rivals out of a video game, you might be actually handing your details straight over to the police.
The UK's National Crime Agency (NCA) has revealed that it has created a number of sites that pose as "DDoS-for-hire" or "booter" services.
However, when users register for the site they are not given access to cybercriminal tools but instead their data is collated by NCA investigators.
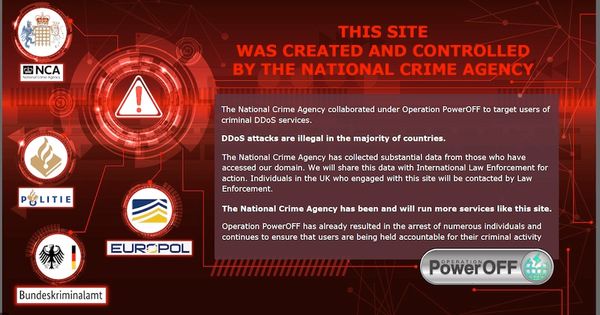
News of the DDoS-for-hire honeypots has come to light after the NCA chose to change the landing page of one "DDoS-for-hire" site to declare it had been suspended and users could expect to be contacted by law enforcement.
The National Crime Agency collaborated under Operation PowerOFF to target users of criminal DDoS services.
DDoS attacks are illegal in the majority of countries.
The National Crime Agency has collected substantial data from those who have accessed our domain. We will share this data with International Law Enforcement for action. Individuals in the UK who engaged with this site will be contacted by Law Enforcement.
The National Crime Agency has been and will run more services like this site.
Operation PowerOFF has already resulted in the arrest of numerous individuals and continues to ensure that users are being held accountable for their criminal activity.
What I like about the NCA's action is that it sows the seeds of uncertainty amongst those considering using a DDoS-for-hire service.
Put simply, you don't know anymore whether the booter service you are signing up for can be trusted to keep your details out of the hands of the police, or whether in fact your information is going straight into the hands of investigators.
“Traditional site takedowns and arrests are key components of law enforcement’s response to this threat. However, we have extended our operational capability with this activity, at the same time as undermining trust in the criminal market," explained Alan Merrett from the NCA’s National Cyber Crime Unit. "We will not reveal how many sites we have, or for how long they have been running. Going forward, people who wish to use these services can’t be sure who is actually behind them, so why take the risk?"
It's nothing new for law enforcement agencies across the globe to shut down websites that make it child's play for anyone to launch a DDoS attack.
For instance, five years ago, police arrested the administrator of webstresser[.]org, a DDoS marketplace, seizing control of its servers and database of over 136,000 users.
Many of Webstresser's suspected customers faced arrest and criminal charges as a result.
As the NCA has previously observed, those using DDoS-for-hire sites are often teenagers, noting that the number of attacks launched against school systems more than doubled from 2019 to 2020.
According to the NCA, the average age of those using a DDoS booter service is just 15 years of age, with the youngest recorded being only nine years old.
This is the reason why the NCA set up the Cyber Choices campaign, buying ads on search engines, and raising awareness amongst young people of the consequences of committing a cybercrime.
Let's hope the message is getting out there that the police are putting resources into investigating the customers of DDoS-for-hire services, and are prepared to bring them to justice.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








