Uncertainty Around Twitter’s Blue Checkmark Fuels New Phishing Campaigns

Phishers are capitalizing on the mayhem surrounding Twitter’s plan to charge users for Verified status on the microblogging platform now owned by billionaire Elon Musk.
In typical phishing manner, the messages aim to scare users, telling them they’ll be stripped of their privileged rank if they don’t immediately confirm their identity with Twitter. On the other end of the line, scammers simply wait for the victim to punch in their user name, password and phone number.
‘Don’t lose your free Verified status’
Originally reported by TechCrunch, the rather crude campaign uses a Gmail address and a website disguised as a Twitter help form.
The email links to a Google Doc with another link to a Google Site, “likely to create several layers of obfuscation to make it more difficult for Google to detect abuse using its automatic scanning tools,” Zack Whittaker reports.
Twitter's ongoing verification chaos is now a cybersecurity problem. It looks like some people (including in our newsroom) are getting crude phishing emails trying to trick people into turning over their Twitter credentials. pic.twitter.com/Nig4nhoXWF
— Zack Whittaker (@zackwhittaker) October 31, 2022
The message targets existing blue checkmark holders with the promise that they’ll keep their Verified status for free if they supply their login data. As the screenshot in Whittaker’s tweet shows, the clumsy writing alone should sound alarm bells.
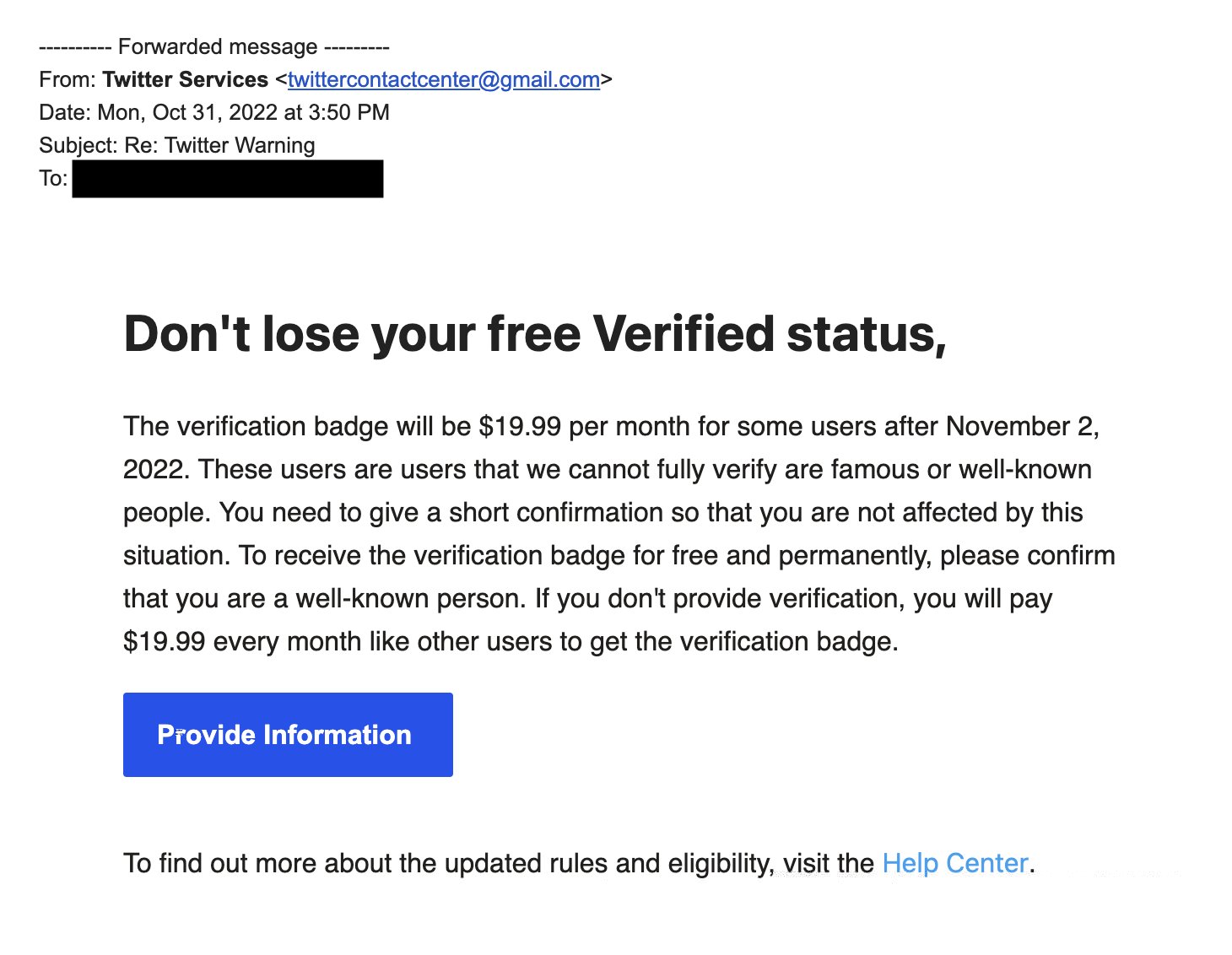
Image credit: TechCrunch
The fake form analyzed by the news site contained an embedded frame from a website with a Russian web host. Users who didn’t have multi-factor authentication switched on at the time this campaign ran were at risk, as the attacker only had to use the stolen credentials to take over the victim’s account, change their password, and lock them out.
Google has since taken down the links and accounts associated with this particular scam.
But it seems this is not the only phishing scam riding the hype around Elon Musk’s plan to bill users monthly for the Verified status checkmark.
Katie Nickels, director of intel at pen-testing firm Red Canary, was targeted with a similar phishing lure that threatened to remove her blue badge over concerns that her account was ‘inauthentic.’
Well that's a new phishing style I haven't seen before... (Please don't visit this link unless you're a malware analyst on a VM!) I just got notification I was added to a "Removal Notice" list by "Twitter". Sure Jan. pic.twitter.com/ueOvVvqj7j
— Katie Nickels (@likethecoins) October 29, 2022
Phishers have a knack for Twitter’s blue checkmark
This is not the first phishing campaign to leverage the fear, uncertainty and doubt surrounding Twitter’s controversial blue checkmark, recently described by Musk himself as a “lords & peasants system.”
Back in May, Verified Twitter users were targeted with a fake warning that their account was about to be suspended. Those who unwittingly followed through were taken to a fake login page that asked for their credentials not just once, but twice, to ensure the data was correct.
When the victim entered their multi-factor code, the attackers would steal the code and use it to take over the account – essentially defeating multi-factor defenses as well.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








