US offers $10 million reward for information about Russian military hackers implicated in NotPetya attack

The United States has made it $10 million harder to keep your mouth shut, if you happen to have any information about the Russian military hackers who masterminded the notorious NotPetya cyber attack.
NotPetya struck in June 2017, spread via a poisoned update to a Ukrainian accounts program widely used by businesses in the country.
Victims found their data scrambled by the ransomware.
One high profile victim was Pavlo Rozenko, who at the time the deputy prime minister of Ukraine. He posted on Twitter a photograph of his PC – mid-way through being encrypted by NotPetya.
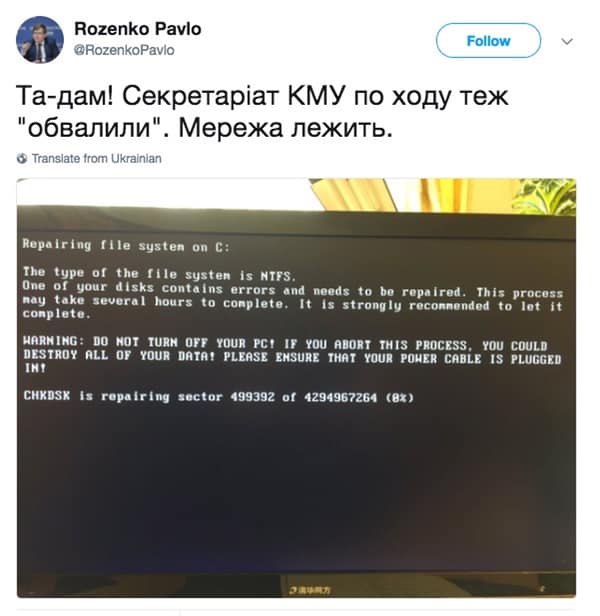
Victims, however, were not limited to Ukraine. NotPetya struck power plants, airports, and government computers in dozens of countries. Victims included pharmaceutical firm Merck, law firm DLA Piper, container ship operator Maersk, and British advertising company WPP.
In its announcement about the reward, US authorities revealed that NotPetya had cost American organisations almost $1 billion in losses.
And now the US authorities is trying to gather as much information as it can about those it alleges were involved in NotPetya's creation and propagation - and isn't afraid to offer a large amount of money to get it.
“These cyber intrusions damaged the computers of hospitals and other medical facilities in the Heritage Valley Health System (Heritage Valley) in western Pennsylvania, a large U.S. pharmaceutical manufacturer, and other US private sector entities," declared the US State Department.
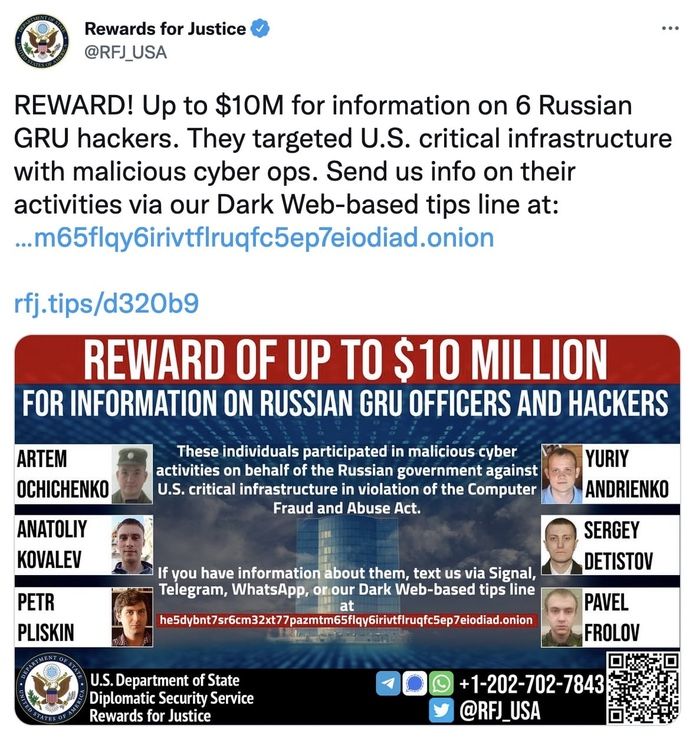
The six men named by the United States authorities are GRU officers Yuriy Sergeyevich Andrienko (Юрий Сергеевич Андриенко), Sergey Vladimirovich Detistov (Сергей Владимирович Детистов), Pavel Valeryevich Frolov (Павел Валерьевич Фролов), Anatoliy Sergeyevich Kovalev (Анатолий Сергеевич Ковалев), Artem Valeryevich Ochichenko (Артем Валерьевич Очиченко), and Petr Nikolayevich Pliskin (Петр Николаевич Плискин).
A federal grand jury indicted the six Russian officers in October 2020, on counts of conspiracy to conduct computer fraud and abuse, conspiracy to commit wire fraud, wire fraud, damaging protected computers, and aggravated identity theft.
But accusing individuals of committing a crime is very different from actually having them in your grasp, and ensuring that they one day face justice on US soil.
Clearly the United States is keen to know more about the men and their activities. Whether offering such a large reward is likely to result in the men being apprehended by the US authorities is open to debate, but it could certainly make their lives and freedom of movement more difficult.
The Russian military hacking group associated with the men has been implicated in a series of cyber attacks against Ukrainian critical infrastructure and government departments.
To assist in its collection of intelligence about the hackers, the US authorities are asking for information to be sent to it via Signal, Telegram, WhatsApp and a special tips line on the dark web.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
Your Device ‘Fingerprint’ Will Go to Advertisers Starting February 2025
December 24, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








