TunnelVision (CVE-2024-3661) is a recently discovered vulnerability that exploits a technique to bypass VPN encryption and leak traffic outside the secure tunnel. Here’s a breakdown of what you need to know:
Impact
An attacker can potentially steal your data, disrupt your internet traffic, or even modify it if they can manipulate your device’s DHCP (Dynamic Host Configuration Protocol). Leveraging DHCP, attackers can reroute your traffic outside the VPN tunnel. This vulnerability affects various operating systems including Windows, macOS, iOS but not Android.
Mitigations
- Enable the “Kill Switch” feature on your VPN. This feature stops all internet traffic if the VPN connection is briefly lost, preventing leaks.
- Update your VPN software and device operating system with the latest patches.
- Be cautious while using untrusted Wi-Fi networks, as attackers are more likely to exploit this vulnerability in such environments.
Is Bitdefender VPN vulnerable to TunnelVision?
We are aware of the TunnelVision technique and are able to confirm that the vulnerability cannot be materially exploited on any of the supported platforms while the Kill-Switch feature within Bitdefender VPN is active. To enable the Kill Switch, go to your username at the top of the Bitdefender VPN app, open the Privacy tab, and then toggle “Internet Kill-Switch” to the on position.
Windows & Android
If the Kill-Switch is disabled, then Windows and Android devices are still immune.
macOS & iOS
On the other hand, iOS and macOS devices are subject to certain restrictions imposed by Apple, which make it impossible for software vendors to implement all measures required to fully mitigate the TunnelVision exploit. Therefore, on macOS and iOS it is imperative that the Kill-Switch remain active at all times.
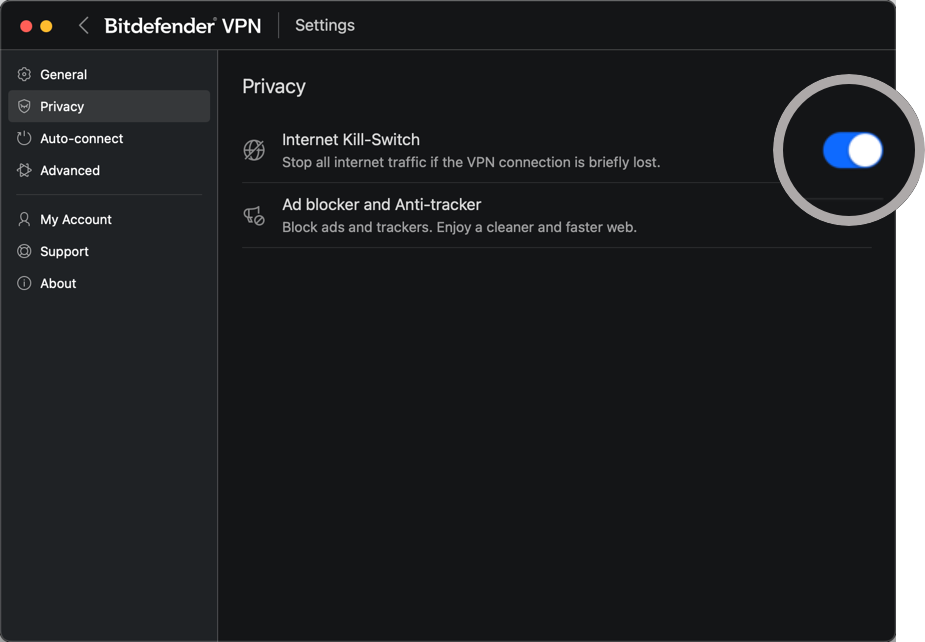
If the Kill-Switch is disabled, it is theoretically possible that connecting to a compromised Wi-Fi network could lead to traffic being routed outside the VPN tunnel. In this scenario, macOS devices will still encrypt all traffic making it virtually impossible for an attacker to obtain any useful information, however iOS devices would become vulnerable. For an added layer of security, we recommend relying on mobile data in favor of untrusted Wi-Fi’s whenever possible.