Types of Security Protocols (And How They Protect You from Risks)

Security protocols keep the Internet safe and alive. They are made up of strings of operations that guarantee your data is safe and it stays that way until it reaches its intended recipient.
Because the Internet has evolved at such a breakneck pace and now inhabits every part of our lives, it is easy to lose sight of the security protocols that keep it stable and reliable.
Just as you are reading this, dozens of them are working in the background to make it possible for you to access the page, watch the videos and get a visual sense of their importance.
This guide serves both a reference for understanding security protocols but also as a small tribute to their unrivaled utility.
Types of Security Protocols
Internet security protocols perform a variety of functions that can be classified into four broad categories:
- Access Control protocols are tasked with validating a user’s identity. Their role is to make sure the right users get access to specific resources;
- Encryption Algorithms that turn plaintext (unencrypted information) into ciphertext (encrypted data) to keep it safe from snoopers, hackers, and scammers;
- Key Management protocols which handle encryption key creation, distribution, and maintenance;
- Message Integrity protocols that ensure no one without authorization can tamper with or modify that data two parties (people or computer systems) send back and forth.
These protocols are interconnected and work together all the time to maintain the confidentiality, accessibility, and integrity of your data. (Find out more about these three fundamental principles of information security in our guide about data encryption.)
Since the Internet is built in layers, the security protocols that power it also address various levels.
Security Protocols that Protect the Physical Layer
When it comes to cables, network adapters, modems and other physical equipment that keep you connected to the Internet, there are specific protocols that keep you safe from security and privacy risks.
To prevent malicious actors from interfering with the physical layer that powers the communication functions of a computer system, security professionals use Access Control protocols, such as biometric authentication, electromagnetic shielding or complex locking mechanisms.
They also take additional measures to ensure that events, such as power surges, floods, fires or accidentally unplugging power or network cables do not result in major outages that affect both individuals and entire companies.
Security Protocols that Protect the Data Link Layer
This layer ensures the transfer of data between electronic devices (modems, phones, printers, computers) that create, receive or transmit information over a network.
One of the security risks associated with this layer is that of MAC spoofing, where an attacker changes the MAC (Media Access Control) address of an Internet-connected device to trick the network into believing it is legitimate when, in fact, it is not.
This is where virtual Local Area Network (or VLAN) security protocols come into play through techniques such as MAC address filtering. Without these security protocols in place, a malicious actor could compromise the security of the entire network and all the devices connected to it.
Encryption Algorithms are another category of security protocols which make sure no one can read or interfere with information as it passes through the network. When the transmission route for the data is unsafe and at risk of compromise or unauthorized access, encryption protects the information from sender to receiver.
Security Protocols that Protect the Network Layer
This layer determines how your data gets sent to the receiving device (like your friend’s laptop). The task of the network layer is to assign the source of information and its destination (IP address) to the tiny data segments that travel across the Internet and reassemble on your friend’s laptop, so they can read it.
Few people realize the technical complexity behind receiving an email or sending a picture. Keeping Internet-based activities secure requires protecting these data segments (called packets) so no one can manipulate them or trick the system to send the information to an unauthorized recipient.
Security protocols that work at the network layer include IPSec and VPNs. Both IPSec (Internet Protocol Security) and VPNs (Virtual Private Networks) rely on a group of security protocols that work together to encrypt communication between devices, keeping data safe when you connect to public networks, such as unsecured Wi-Fis.
But not just any VPN will do. You will need a secure VPN you can trust, from experts with a track record of producing high-quality products and services.
Security Protocols that Protect the Transport Layer
The task of the transport layer is to deliver the data to its intended recipient, safely and error-free. To make sure that the entire process runs smoothly and securely, security experts must ensure that malicious actors do not gain access to information transmission protocols.
The TLS (Transport Layer Security) protocol is the current standard for ensuring privacy and data integrity between two or more computer systems that communicate with each other. It is another example of a protocol that uses encryption to keep data hidden from snoopers while it travels from sender to receiver.
TLS is a protocol that underpins many of the online activities you do every day, from email to instant messaging to video conferencing. TLS is most frequently observed in the lock symbol next to HTTPS websites (HyperText Transfer Protocol Secure).
Security Protocols that Protect the Session Layer
Once the data arrives at the session layer, it reassembles the data packets into the original files you sent. The same layer establishes how devices connected to the Internet have “conversations” with each other, how long they maintain this communication and when it ends.
Security protocols in the Access Controls category work here to filter unauthorized and malicious parties from accessing the data.
For example, as long as you are logged into your email account, you can send, receive, and manage your emails. Once you logged out of your account, security protocols working at the session level must ensure that no one else can access your emails.
If you use a weak password for your email account, you risk becoming the victim of a brute force attack, in which a cyber-criminal attempts (automatically) a large number of possible passwords to gain access to it.
This is just one example of the most common reasons for hackers to attack the session layer: collecting your personal data so they can then use it for illegal activities such as digital identity theft.
Security protocols include using a password manager to set and use strong passwords for your accounts while also keeping them safely stored and encrypted. Secure websites also put timers in place to limit the numbers of attempts a user can make at logging in - and establishing a session - so they can lock out bad actors before they do any damage.
Security Protocols that Protect the Presentation Layer
Data encryption and decryption happen at the presentation layer, making sure the recipient can access and use the information.
Because of its importance, there are various types of cyber-attacks that seek to compromise the security and privacy of the data before it gets encrypted.
For example, an encryption downgrade attack tries to force the system to discard the encrypted connection and use an unencrypted one that is typically preferred to ensure compatibility with older computer systems. If such an attack succeeds in forcing your computer to communicate via HTTP (Hypertext Transfer Protocol) instead of HTTPS (Hypertext Transfer Protocol Secure), then hackers will be able to see and harvest all the information you are transmitting.
This is yet another reason to use a premium VPN to protect your data regardless of the network to which you connect. Because it adds an extra encryption layer to all the information you transfer over the Internet to various websites, it significantly reduces the risk of attacks that aim to undermine your online privacy and security.
Security Protocols that Protect the Application Layer
On its way to you, data reaches the application layer, whose main job is to confirm that you are who you claim to be (the intended recipient), that the information you must receive is accessible, and to finally synchronize the data between you and the sender.
The application layer attracts the most potential intruders because it is the closest to you and the one you interact with every day. Cyber-criminals and snoopers attempt to gain access to it using methods such as:
- DDoS (Distributed Denial-of-Service) that aims to take a system offline - such as your favorite website;
- HTTP flood that seeks to block applications (email apps, video conferencing apps, file sharing apps) and force them to deny access to legitimate users;
- SQL injection whose goal is to give attackers access to information that was not meant to be displayed or seen by unauthorized users;
- XSS (Cross-site scripting) which allows cyber-criminals to inject malicious scripts into otherwise clean and trusted websites, using them to spread their malware to the systems of their victims.
Security protocols used at the application layer include SFTP (Secure File Transfer Protocol), PGP (Pretty Good Privacy) and SMP (secure messaging protocol).
SFTP (Secure File Transfer Protocol) ensures two computers can exchange almost any file securely, whether it is music, videos, images, documents or something else.
PGP (Pretty Good Privacy) is a secure program that enables users to encrypt their emails, files, and directories to increase their level of security and privacy.
A secure messaging protocol (SMP) makes it possible for remote users to send each other messages and files safely and without intrusion over an untrusted network.
Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring sensitive information securely.
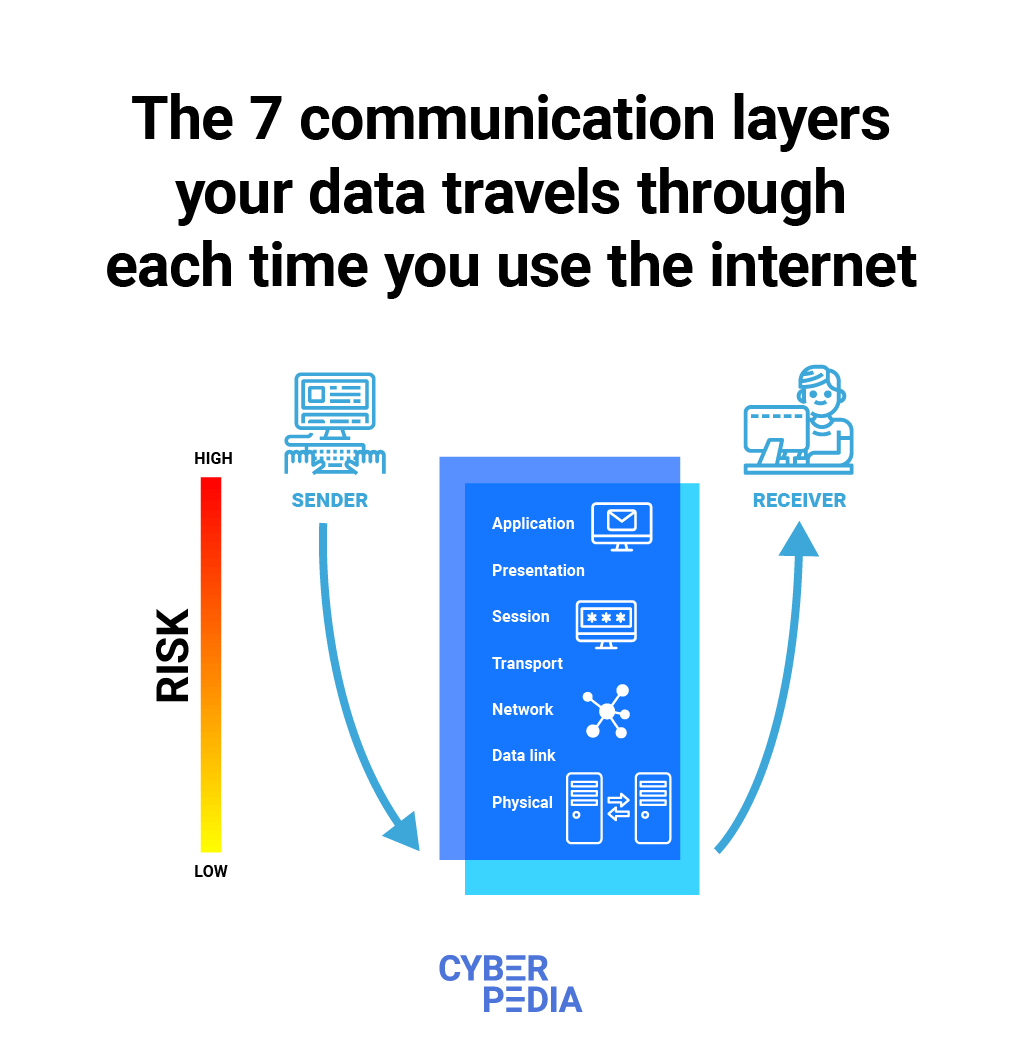
These seven layers of the Open Systems Interconnection (OSI) model give you a clearer idea of the complexity of operations that happen behind the scenes each time you use the Internet.
From your viewpoint, security protocols allow you to communicate using the Internet without being identified as someone attempting to attack people or institutions.
The list of security protocols is much longer, with examples such as WPA2 (Wi-Fi Protected Access 2), SSH (Secure Shell), and SET (Secure Electronic Transaction) plugging into various layers of communication with the sole purpose of strengthening the safety of our communication over the Internet.
Layered Security is the Best Security
Our cybersecurity experts recommend you build your online security and privacy in layers: a reliable password manager, a powerful antivirus solution, a secure VPN, and constant updates for all your apps and software.
Or even try an all-in-one protection mega-suite which includes them all.
By assembling these layers, you will be making the most of the security protocols built into them - and the constant improvements they receive through updates.
tags
Author
Choose what the experts use. Award-winning cybersecurity you can trust and rely on.
View all posts

