What are Private Data Leaks?

As a digital user, having your personal information exposed is almost inevitable. However, that does not necessarily mean you are in immediate danger. The severity of the threat depends on the nature of the disclosed data. For example, having your financial data leaked is much worse than having your age, or job title exposed.
Unfortunately, most people do not know how much the Internet knows about them until it is too late.
Find out why private data leaks happen, how to get notifications when your sensitive info gets exposed, and what to do next to improve your online security.
Our cybersecurity experts will help you build a lasting setup that works for you on a personal level and keeps you safe in the long run.
What Is a Private Data Leak?
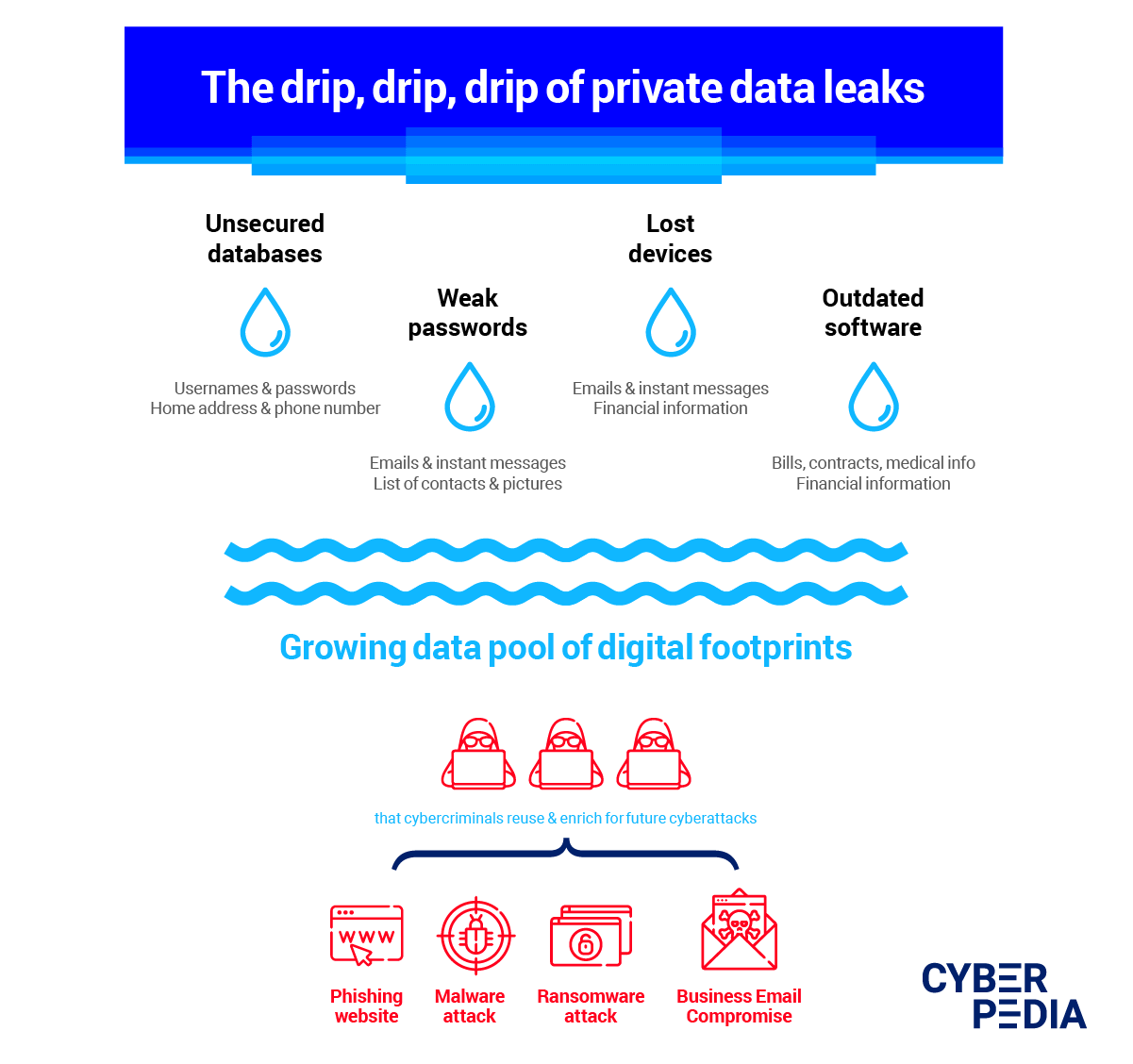
A private data leak is an accidental disclosure of information that exposes sensitive details which define your identity. This can include information such as your date of birth, your SSN, your emails, usernames and passwords, home address, phone number, and medical history.
These outpourings of Personally Identifiable Information (PII) are extremely harmful not just for the unsuspecting victims but also for our collective online privacy. Once out in the wild, malicious actors can leverage them for anything from social media impersonation to cyber-attacks and digital identity theft. What’s more, most times this data ends up on the Dark Web and gets repurposed over and over again.
How Do Data Leaks Happen?
The main difference between a data leak and a data breach is its motivation. While a data breach is premeditated and involves malicious hacking, social manipulation or a combination of both, data leaks are mostly accidental.
And if you are wondering “what is the most common cause of data leakage?”, the answer is poor data security practices. From weak passwords to unprotected databases and lost devices, these mishaps add up.
Because technology has become incredibly complex and interconnected, mistakes happen, whether they are human errors or tech glitches. Specialists do plenty of work behind the scenes to prevent this, but completely eliminating this risk is almost impossible.
Malicious hackers know this and use it to their advantage by actively exploiting both old and new vulnerabilities, whether they are related to human nature, software, hardware, or business processes.
Data leaks can also give attackers a clear picture of the vulnerable elements in their target’s defenses. That is why cyber-criminals are constantly on the prowl for inadvertent data spills, as they allow them to expand their data sets on potential victims and build a strategy for their next attack. Low-effort, high-potential return opportunities like these cannot go unnoticed.
What Happens If Your Personal Data Is Leaked?
Depending on the type of leaked information, you should watch out for these types of scams:
Phishing emails that try to trick you into:
- Clicking links that infect your computer with malicious software
- Opening malware-infected attachments that do the same
- Disclosing additional personal information such as your card’s PIN
- Going to websites that ask for financial details under a compelling pretense, and many more tactics that exploit your fear, excitement, or trust in other people or organizations.
Calls (vishing = voice phishing) that try to coax you into transferring money, revealing information, or otherwise acting to benefit the attacker.
Malicious actors may set up fake social media accounts in your name and use them to trick your family, friends, colleagues, and acquaintances into acting in any of the ways described above.
Social media impersonation can hurt your reputation, damage your relationships, and even affect your job or business.
However, one of the most damaging effects of private data leaks is digital identity theft. With deep knowledge of your online footprint, cyber-criminals gain invaluable insights about your life and assets. The more they know, the easier it is for them to steal your identity and use it to get credit cards, apply for loans, and even carry out illegal activities under your name.
Perhaps one of the most frustrating facts about private data leaks is they cannot be reversed. Once spilled online, your personal details get compiled with other information about you that is publicly available (on social media, search engines or public databases). All that data sits on servers that cyber-criminals control, gets traded on Dark Web forums, and goes on to live in backups and all sorts of repositories.
“Okay, but what can I do to fight back? How can I do anything against the cyber-criminals who do this for a living?”
By getting a partner who fights cyber-crime for a living. (Yep, we are talking about us!)
How Do You Check for Data Leakage?
You probably don’t want to be the last one to find out that your personal data ended up on the web. This is where alerts from Bitdefender Digital Identity Protection come into play.
The service monitors your most sensitive data starting with just an email address and phone number. It then automatically tracks your private information in legal and illegal collections of online data.
Once you set it up, you also get alerts for potential social media impersonators, new private data leaks and information breaches that reveal your personal details.
Additionally, you get expert recommendations so you can act quickly to limit the impact of these data spills (like changing your password or enabling two-factor authentication).
For example, if a data leak victim finds out their credit card information has just been made available on the Dark Web, they can immediately call their bank and cancel it before hackers get a chance to deplete their account.
Curious to see how it works? We created a guide that shows how to check if your personal information is exposed.
“Digital identity protection services alert customers when their private information has been leaked, so they can act quickly and avoid long-term damage. They make it easier to deal with the aftermath of a potential data leak, of having your data exposed online.”
Liviu Arsene (Senior E-threat Analyst, Bitdefender)
How Do You Stop Data Leakage?
There are many things you can do to keep private data leaks from flooding the Internet with your details.
The first step is understanding you have a digital footprint and it can have very serious implications on your life. Mapping, monitoring, and managing it is step two, which is closely tied to learning the practical aspects of protecting your online privacy.
“You have to interact with the Internet and you have to disclose information about yourself when you do so. But you can actually limit the impact of a potential data leak by providing only the information that’s mandatory for that service to work.
When you sign up for an account, a home address, for instance, is not mandatory, so we suggest that you don’t fill in that request. If you can do without adding your phone number to that service, it’s another thing that will not leak online in case of a data spill and so on.
You can minimize the impact of a potential data leak by sticking to the absolutely necessary things that you need to communicate about yourself.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
While you can never truly stop data leakage that involves your personal details, you can actively contribute to reducing your potential exposure.
How to Prevent Confidential Information Leakage
The checklist below includes some practical recommendations from our cybersecurity experts that you can apply straight away:
- Start moving your passwords to a password manager. You will only have to remember a single password and it will save you time, effort, and many annoying password resets. Most importantly, you will never (re)use weak passwords again because a password manager makes it super easy to generate long, complex passwords and automatically fill them in when you want to log in.
- Turn on two-factor authentication starting with your most important accounts. This extra step reduces the risk of account takeover and has a hugely positive effect on your online privacy and security.
- Set passwords for your essential devices to avoid malicious onlookers snooping in. This is especially useful in case you lose your devices or get robbed.
- Delete all unnecessary apps from your devices. It makes a huge difference to remove add-ons from your browser and keep only those you routinely use. Plus, it frees up space and makes your device faster.
- Delete online accounts that you do not use anymore. Out of sight may be out of mind for you, but cyber-criminals will dig those details up and find a way to use them against you.
- Disconnect third-party apps from your main accounts and applications. Going through this step might remind you of old accounts and shed a clarifying light on the kind of permissions some apps request.
- Keep a backup copy of all your important assets on an external hard drive or in the cloud, ideally encrypted. This may include pictures, documents, and all kinds of information you’d want to save if there was ever an emergency.
- Update all your software applications across your devices. It’s not that big of a hassle and it makes a world of difference as most updates include important security fixes or improvements.
- Tweak your web browser’s security and privacy settings and turn them up. Because most of your personal information runs back and forth through your browser, it’s a prime target for cybercriminals. Do not make it easy for them to snoop in on that data flow.
- Install a reliable security solution and just leave it to work in the background.
- Use a virtual private network (VPN), especially when you use Wi-Fi networks outside your home or office, or when using websites where extra safety is recommended (think medical and financial ones).
- Share files online securely through reputed services and avoid sending personal data via instant messaging platforms (IDs, documents, bank details, and especially passwords)
- Use secure online communication platforms that use encryption and do not share your data with third parties.
And don’t forget to set up Bitdefender Digital Identity Protection alerts in case you need to quickly take action to protect your data.
tags
Author
Choose what the experts use. Award-winning cybersecurity you can trust and rely on.
View all posts

