What is the Dark Web? And Is Your Personal Info There?
Do you know if hackers are trafficking your personal data on the Dark Web?
After reading this guide, you will have a strong understanding of how data transactions on the Dark Web impact your privacy and security.
Plus, you will get reliable advice from Bitdefender cybersecurity experts to help you minimize any negative impact.
What Is the Dark Web? A Definition
The Dark Web is often portrayed as an inscrutable part of the Internet shrouded in mystery, so let’s debunk it.
The Internet is incredibly vast and much bigger than we can imagine. In fact, what we can access (the surface web, known as the World Wide Web), represents just 10% of what is really out there.
Most of the content online sits on the Deep Web, which is not accessible via search engines, like the world wide web is. That is because the Deep Web hosts information that is private for a range of reasons, mainly security and privacy related.
The Dark Web vs the Deep Web
You may not realize it, but you use the Deep Web every day. From databases to intranets to websites waiting to be launched, Deep Web content is usually hidden behind a username and password or other security measures to keep it safe. This includes items like email, financial and social media accounts, databases operated by private and public organizations, medical and legal documents, etc.
That is why the Deep Web is not the same as the Dark Web, even though you may see the two terms used interchangeably - which is incorrect.
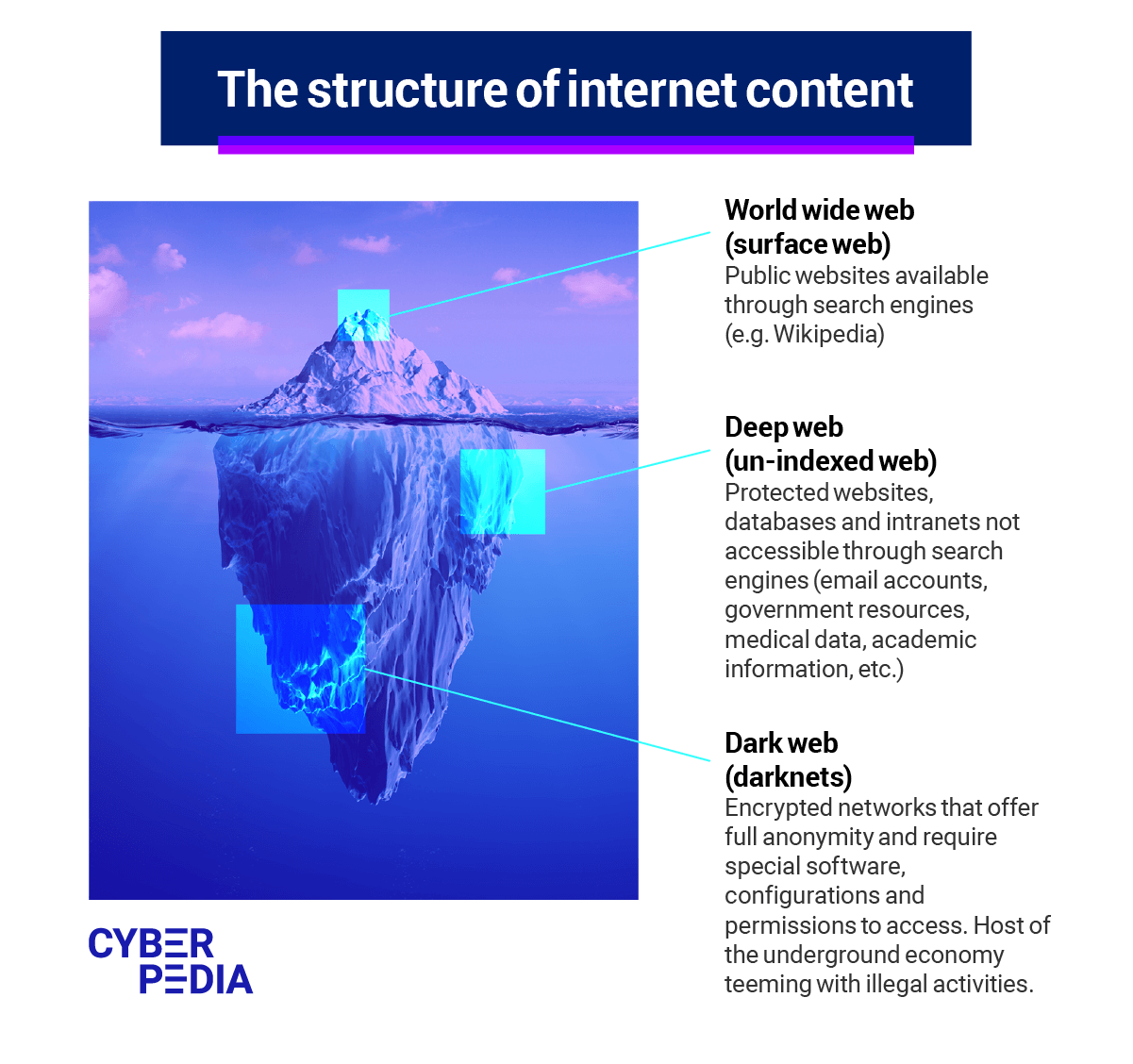
The Dark Web is a tiny fraction of the Deep Web and there are a few things that make it a specific “place” on the Internet.
This collection of websites sits on networks called “darknets” that require specialized software to access. Darknets use complex, layered encryption systems to keep their users’ identities and locations anonymous. Exploiting this capability, Dark Web users communicate and share data confidentially, without being tracked by private companies or public organizations, including the government and law enforcement.
This confidentiality combined with the anonymity that cryptocurrencies provide has created a convenient environment for illegal activity. That is why the Dark Web is mostly associated with criminal acts, from financial fraud to other types of cyber-crime.
The Dark Web is indeed the place where malicious actors sell, trade, and otherwise share illegal collections of data and illicit goods. This includes stolen information and personal details leaked through data breaches such as credit card data, medical data, SSN, username and password combinations, home addresses, and many, many more details.
And, yes, some of your data is most likely already in those illegitimate websites, forums, blogs, and data repositories.
Why Is Your Information on the Dark Web?
Because, as our cybersecurity experts have validated through decades of research and practice, your data has a price.
“You can look at your personal data as something malicious hackers directly exploit or use as soon as they get a hold of it. It’s also something they can trade with other cybercriminal organizations.
Personal data is commoditized. It has a price. Your medical data, your financial history, your credit card data, your online shopping preferences – they all have a price and there’s always an interested buyer.”
Liviu Arsene (Senior E-threat Analyst, Bitdefender)
Since your data means money for malicious actors of all kinds, it is their goal to harvest as much of it as possible. If you’re wondering “how does one’s personal information get on the Dark Web?”, the answer includes data breaches, scams, and a very diverse range of cyber-attacks (phishing through email, private messages and voice calls, social media impersonation, malware infections or digital identity theft).
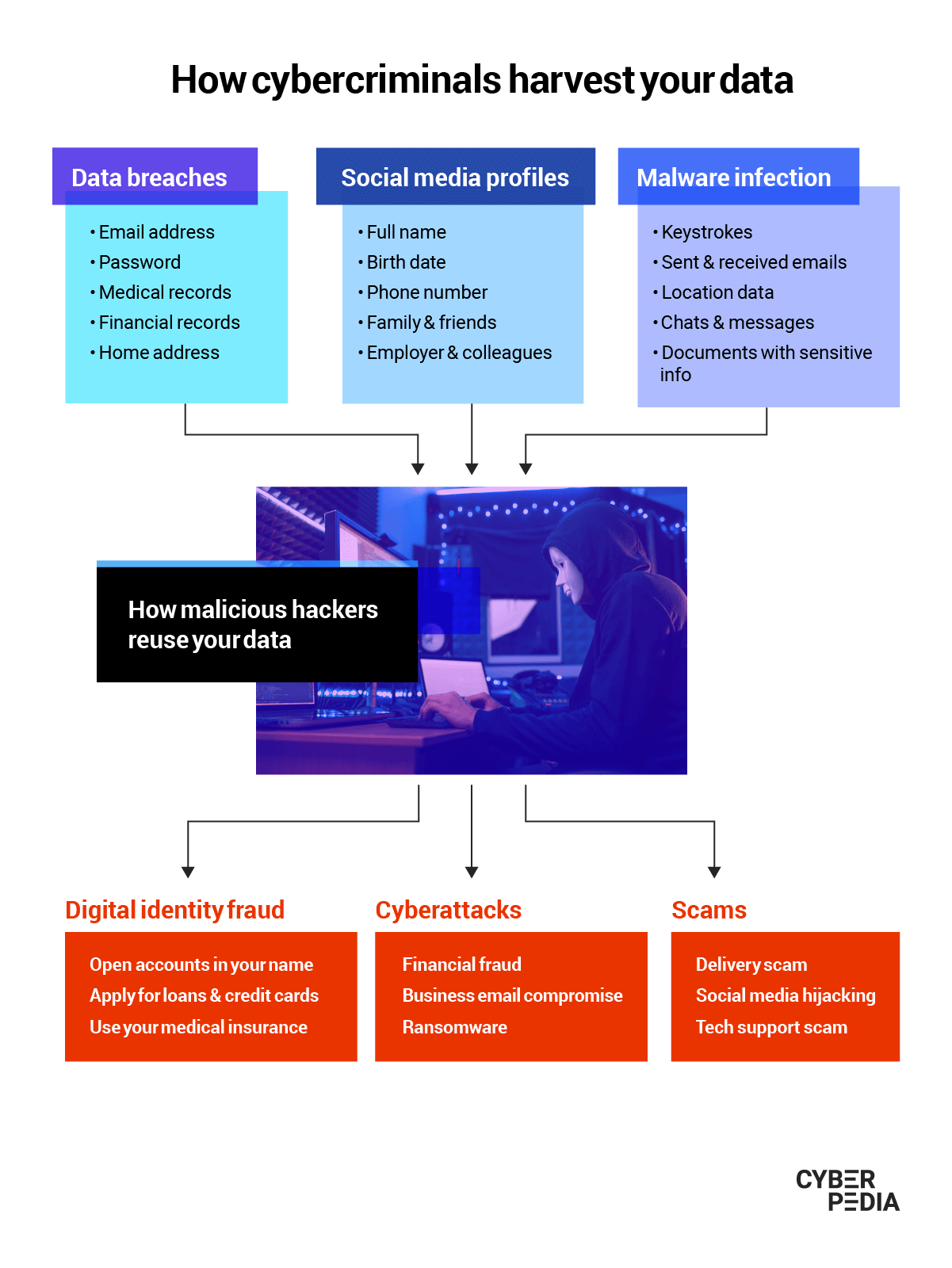
Depending on the size of your digital footprint and your online privacy setup, your personal data may be leaking in small drips or flooding onto the Dark Web. As it pools together, hackers use it to fuel other criminal operations, combining details and reusing them for subsequent attacks.
This is true for all threat actors, no matter if they are lone hacktivists, organized cyber-crime, or nation-state operations. Personal data is a valuable currency.
So, realistically, how likely is it to have your information on the Dark Web? The answer is: very likely.
How to Find Out if Your Information is on the Dark Web
All you need is a service that automatically checks the Dark Web for you. Bitdefender Digital Identity Protection scans the Dark Web to find if your personal information was exposed. It also helps you take action to protect your data.
What Is Dark Web Monitoring?
Dark Web monitoring is a service provided by Bitdefender Digital Identity Protection, along with an ongoing audit of your digital shadow and constant checks for impersonators.
When you first log into Bitdefender Central after activating your subscription, the service immediately starts mapping your digital footprint.
It then asks you to validate if certain usernames, email addresses, and other personally identifiable information is – or have been – yours. This Accuracy Check helps the service better understand your online fingerprints so it can track it to the farthest corners of the Web.
At the same time, the service starts automatically combing through data repositories hosted on darknets, looking for personal information associated with your identity (SSN, emails, phone numbers, usernames, etc.). When it finds a match, you immediately get an email notification.
Each warning for data leaks also includes the type of information exposed and the essential steps to limit your exposure.
How to Get Your Information Removed from the Dark Web
Bitdefender Digital Identity Protection doesn’t just tell you that your personal information is exposed. You also get action prompts directly in your online dashboard, such as “change your password” and “enable two-factor authentication.”
When you follow them, you reduce the risks of account takeover. You also keep scammers and cyber-criminals from setting up new accounts using your personal data and using them for fraud.
Unfortunately, there is no way to permanently remove your information from the Dark Web. Sometimes it is difficult to remove it from the Deep Web, or even from the World Wide Web, in spite of these two being governed by regulations that give you “the right to be forgotten” (e.g. GDPR).
Your best bet is to slowly but consistently build a cybersecurity setup that combines reliable tools (digital identity protection, antivirus and VPN) with ongoing self-education.
You are already doing great work in this area, so we encourage you to keep at it.
tags
Author
Choose what the experts use. Award-winning cybersecurity you can trust and rely on.
View all posts