Akira Ransomware: A Shifting Force in the RaaS Domain

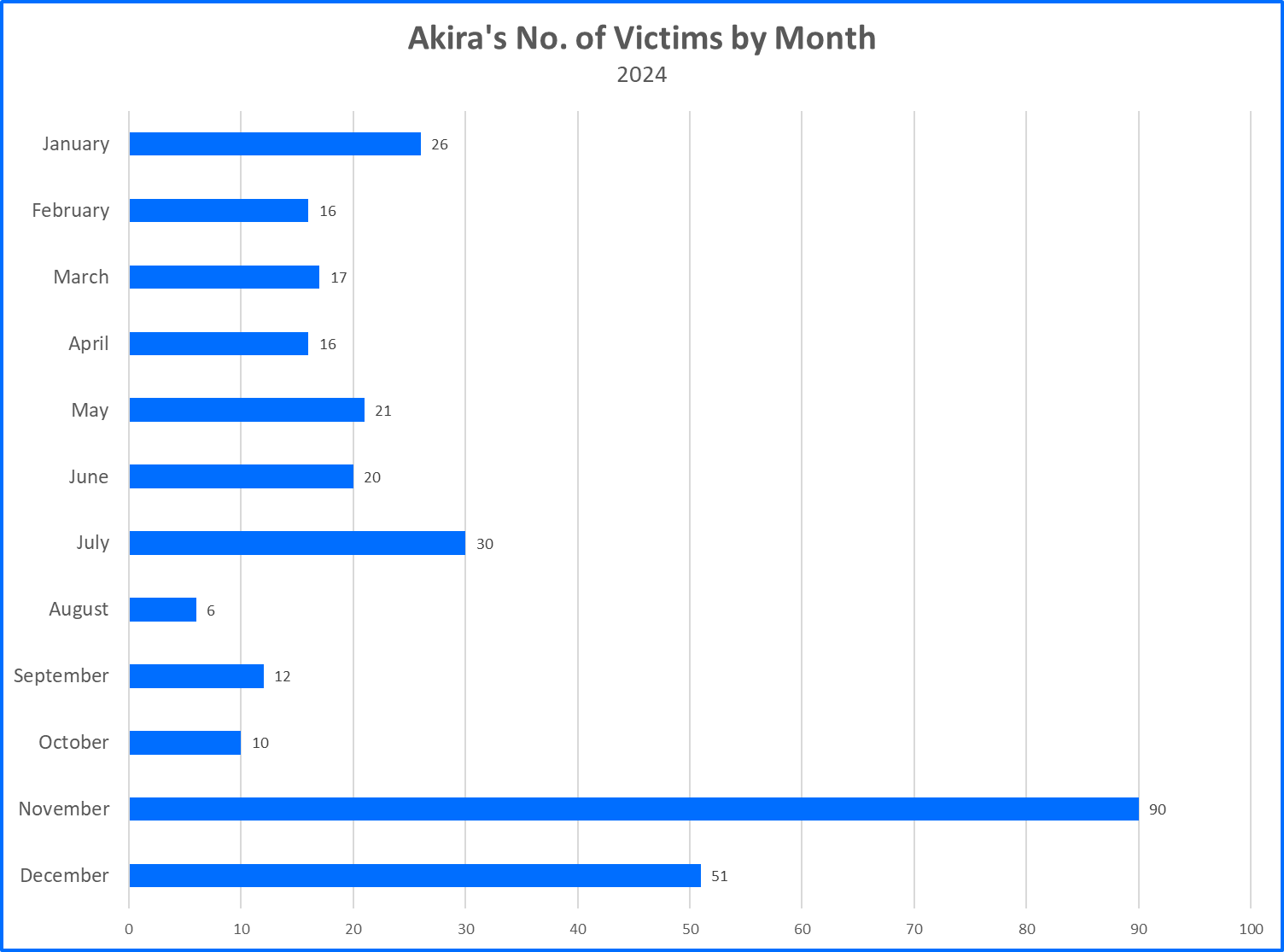
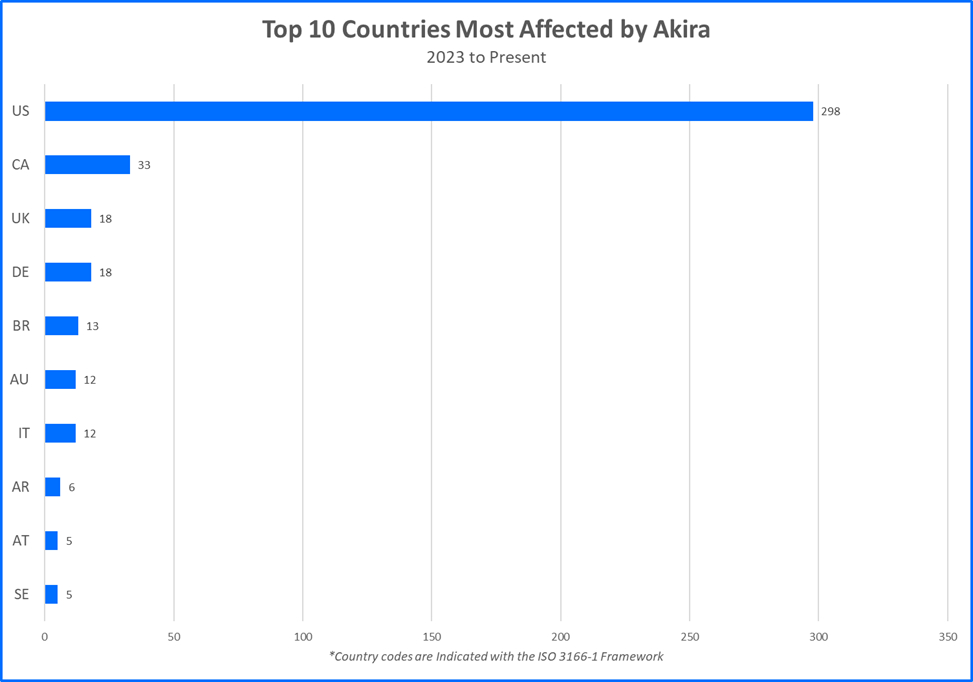
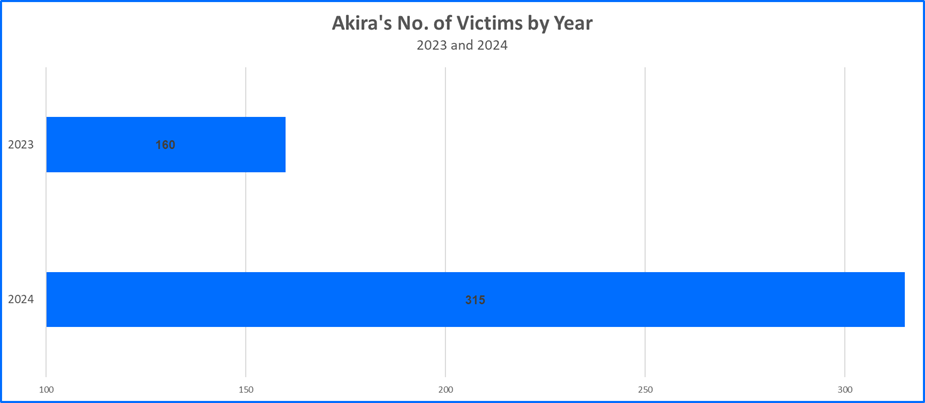
Akira is a Ransomware as a Service (RaaS) group that emerged in March of 2023. Since then, the group has engaged in a high volume of campaigns, particularly in the last year. In April of 2024, it was estimated that Akira acquired a sum of more than 42 million USD in ransom payments. In 2024 alone, more than 300 attacks have been reported. The graphs below depict Akira’s total number of victims by year, the number of Akira victims by month in 2024, and the top countries affected by Akira to date.
Victimology and Affiliation
Akira’s victims span a range of organizations, including manufacturing companies, engineering and agricultural firms, financial service providers, and higher education institutions. Many of Akira’s victims include organizations based in Western countries, such as the United States, which makes up the largest victim demographic, followed by Canada, the United Kingdom, and organizations based in Germany.
The name Akira may evoke fond memories for some of an action-packed science-fiction anime film of the same name that was released in 1988. However, no operational or other cultural references have been identified to link the ransomware actor’s motives and movements with that of a Japanese or East Asian cybercrime syndicate. Instead, Akira is a threat actor that is likely associated with Russia. This development came about once security analysts discovered that Akira’s malicious code was designed in a manner to prevent it from running on systems that were equipped with a Russian language keyboard. Correspondence with Akira members was found on Russian forums in 2022. While there has been a reduction in the use of underground forums in favor of other semi-anonymous options like Tox and Telegram, many ransomware groups maintain accounts on hacker forums and criminal marketplaces in an effort to reach potential affiliates and garner further interest.
Targeting Multiple OSes and Developing Different Payloads
Akira has an extensive history of altering the types of payloads they use in their operations. In March of 2023, when Akira incidents were first discovered, Akira launched ransomware attacks that targeted Windows systems. The encryptor associated with these attacks was built in C++ and appended .akira to affected files. Shortly after April of 2023, the group shifted gears to launch attacks with a Linux payload designed to encrypt VMware ESXi servers.
In August 2023, Akira deployed Megazord to attack Windows systems. This variant differed from the previous version that targeted Windows systems since it was compiled in Rust and appended the .powerranges extension to encrypted files rather than .akira. Around the same time, Akira developed a payload to attack VMware ESXi servers and Linux systems using an iteration of the ransomware known as Akira v2.
In April 2024, Akira returned to form, using a ransomware payload written in C++ to encrypt victim data and append the .akira extension to affected files.
Akira v2
Unlike its former iterations from early 2023, Akira v2 is written in Rust and is designed to locate files to encrypt based on specific parameters. The Akira v2 ransomware also appends .akiranew to affected files. Since file encryption can be more tailored to a specific file type, the data that can be encrypted extends beyond the file types reported in past iterations that have been targeted by Akira ransomware, e.g., ade, .ckp, .ddpl, .edb .sq, and .vdh--these are file types associated with database project files, optical media, the Exchange mailbox database, and virtual hard disks.
The encryption of files, specifically those ending in .edb and .vdh can result in greater consequences as .edb is a file type that stores data pertinent to Microsoft’s Exchange server environment. And, .vdh is a virtual hard disk file that interacts with virtualization software. In spite of the fact that a range of common document and database file types that are pertinent to manage virtual machines on Windows or Linux hosts, including .vdi, .vmdk, vmem, .vmsn, vmsd, .vmx, .vhdx, .vsv, .avhd, .vmrs, .vhdx, .avdx and .vmcx can be encrypted upon discovery, the customization capability to find other files makes the ransomware lethal.
The Present: Is This a Post v2 Era?
Akira v2 would see a resurgence following spring of 2024. However, in October of 2024, reports documented further changes to Akira’s tactics with a strain that would move up to join Akira’s Rust-based v2 amongst the number of rising Akira incidents. Several changes were implemented by the threat actor to the ransomware strain, including a return to code written in C++ and the use of ChaCha8.
While fewer instances of the v2 iteration and Megazord may occur since the initial reports of their detections, those versions are still identified in the wild. It’s important to also note that other ransomware groups such as Cicada3301 and Qiilin have used ransomware payloads written in Rust to make both disassembly and malware detection actions far more challenging.
Akira’s Data Leak Site and Ransomware Note
Akira’s data leak site features a command line interface. A user can input commands on the data leak site such as leaks to generate a listing of information leaked and news to return information about oncoming leaks or victims.
URLs are included in the Leaks area on the data leaks site, enabling users to access the stolen content. Users who want to download the leaks may do so via a torrent client. Archive files containing leaks are also provided, some leaks are password protected. However, passwords are supplied with information about each torrent.
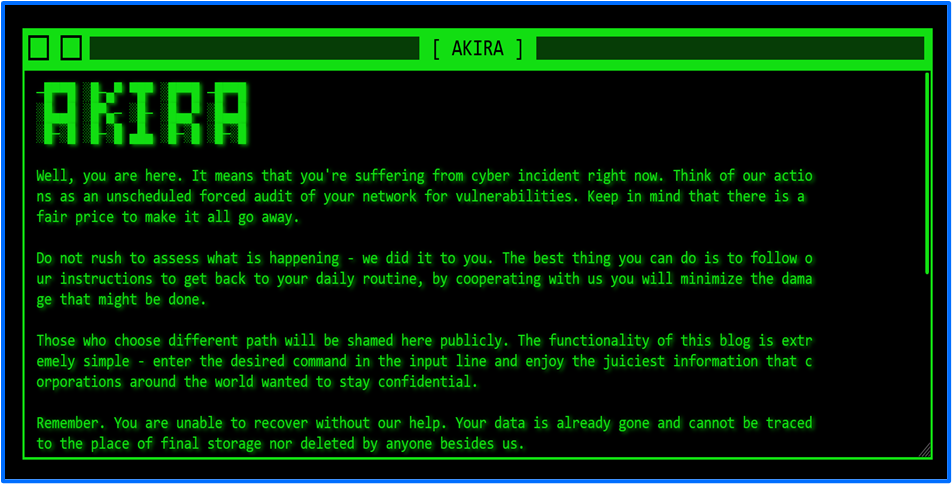
Figure 1: Akira's Data Leak Site - Entry Page
Figure 2: Landing Page of Chat Correspondence Channel for Victims
In past ransomware notes, Akira has directed victims to communicate with them for more information, linking a web page and providing a unique Chat ID.
The use of such a Chat ID seems to have fallen out of favor, possible due to the current functionality of Akira’s main web site which includes a contact us argument in its command line interface that accepts names and message content which is delivered to support.
Akira encourages victims to contact them for more details on how to recover from an incident, providing a name and email via the data leaks site’s command line interface. The threat actor mentions that a sample test decryptor can be made available to affected organizations who contact them directly.
The contents of Akira’s ransomware note indicate a willingness to understand an organization’s revenue and negotiate if needed, which is illustrated in the following excerpt:
Moreover, we have taken a great amount of your corporate data prior to encryption , for now let\’s keep all the tears and resentment to ourselves and try to build a constructive dialogue...Dealing with us you will save A LOT due to we are not interested in ruining your financially.
We will study in depth your finance, bank & income statements, your savings, investments etc. And present our reasonable amount to you. If you have an active cyber insurance, let us know and we will guide you how to properly use it. Also, dragging out the negotiation process will lead to failing of a deal.
Tactics
The following section provides further information on the tactics used by Akira and the mappings of those patterns to the MITRE ATT&CK Framework.
Initial Access
Known for exploiting common vulnerabilities, including those affecting remote access tools and external applications, Akira has established initial access by targeting flaws in firewall and VPN products and cloud services.
This year, the notable vulnerabilities leveraged in Akira’s attacks included CVE-2024-37085 and CVE-2024-40711, which affect ESXi servers and Veeam’s backup service respectively. The threat actor has used tools like Veeam-Get-Creds and Veeam Hax to obtain and manage the leak of credentials to Veeam servers.
Environments comprised of SonicWall products equipped with the SonicOS were also hit by Akira ransomware this year; CVE-2024-40766 is the vulnerability that was exploited in those attacks.
Akira has also established initial access by leveraging compromised credentials or obtaining them through other means e.g., an Initial Access Broker.
Discovery
Akira performs essential discovery and host reconnaissance activities by deploying tools such as IP scanners and Adfind to initiate queries that obtain data on the Active Directory ecosystem.
Akira is also capable of discovering running processes, security tools, and the target system’s language. These tasks are typically performed by leveraging interactions with Microsoft’s APIs.
Execution
A ransomware file is dropped to a victim machine; malicious executables such as w.exe and win.exe were associated with encryption capabilities in Akira’s campaigns in addition to .ELF files that were used to target Linux systems.
Persistence
Akira establishes persistence by creating registry keys and modifying host settings. In attacks that first exploit leaked credentials and weaknesses impacting the Domain Controller, the threat actor sets up Domain accounts to maintain a stronger presence.
Lateral Movement
Akira’s creation of accounts, such as a backup account associated with Veeam, and their use of tools to extract credentials aid them in performing lateral movement actions.
Defense Evasion
Akira ransomware is able to detect and evade debuggers; it is also characterized by elements of encoding, including Base64 encoding and obfuscation to conceal files and processes. In a recent iteration of Akira, a component was introduced that restricts its execution in an analysis environment; that component is the use of a unique Build ID.
Inhibition of System Recovery
Akira is capable of removing volume shadow copies; that is an action that can be accomplished via a PowerShell script. The script references a command that removes the volume shadow copies after locating them via an interaction with WMI. Organizations that use backups that are not assessed at the file level and rely on volume shadow copies will face a detrimental loss if they fall victim to an Akira ransomware attack.
The Linux ESXI ransomware variant also allows the attacker to invoke a vmonly command to limit the scope of their attack to virtual machines and a stopvm command to terminate active virtual machines.
Impact
Encryption and exfiltration are the resulting actions in Akira’s ransomware attacks. Tools such as WinSCP and Rclone are used by the threat actor to exfiltrate data.
What’s to Come?
As Akira ransomware continues to hit organizations worldwide, it is important for organizations to monitor their ecosystems for patterns of compromise and stay informed about the different active strains of Akira ransomware. That includes not only v2 and Megazord, but the latest ransomware code as well. Akira experienced great growth in its incidents per month shortly after the first half of 2024. We expect this growth pattern to continue into 2025.
Recommendations
Implement backup and recovery measures: Schedule regular backups, ensure that they are tested and maintain backups on a system separate from the main network. It is advised that backups are stored in an offline location and/or cloud environment
Establish Network Protection controls: Enforce Network Attack Defense and network segmentation: Segment networks to limit lateral movement outcomes if an endpoint is compromised and ensure that critical systems do not interact with resources. that may have a wide attack surface
Perform patch management: Regularly assess patches and updates to deploy, prioritizing them based on their impact to organizational assets.
Implement Email Security Solutions: Use email filtering solutions to block malicious emails, attachments, and links Add further protection by enabling attachment sandboxing; this allows a scan to run in real time, proactively identifying ransomware contained in attachments before the attachment is delivered to a user.
Execute an Incident Response Plan: Rapid response is a vital part of ransomware protection and mitigation. A timely, proactive approach is significant when performing incident response actions. Ensure that the security team has the people, processes, and technologies in place to thoroughly investigate and respond to an incident, e.g., blocking IPs, stopping processes, or isolating hosts to cut off an attacker’s access to critical data and resources and preventing further exploitation.
Deploy Endpoint Detection and Response (EDR) solutions: Use EDR and/or MDR technologies that leverage active monitoring using both behavioral and heuristic-based detections to ensure that initial infection vectors are accurately detected and escalated for investigation. Enable real-time threat detection and automated responses to allow counter measures such as block and isolation actions to be executed against devices compromised in a ransomware incident.
Leverage Operational Threat Intelligence: The right threat intelligence solution can provide critical insights about attacks. Bitdefender IntelliZone is an easy-to-use solution that consolidates all the knowledge we've gathered regarding cyber threats and the associated threat actors into a single pane of glass for the security analysts, including access to Bitdefender’s next-generation malware analysis service.
If you already have an IntelliZone account, you can find additional structured information under Threat IDs that include: BD1v4nw4su, BDcrena0eu, BDc7c2411y, BD80wyffwi, BD0sod05yv, BDx5nkwaqw, and BDqy7jftkp.
Secure Remote Access: Enforce multi-factor authentication (MFA) for all remote access points, including VPNs and RDP. Use a VPN or secure access gateway for remote users instead of exposing RDP directly to the Internet.
Indicators of Compromise
Akira (Windows Executable File)
| SHA256 Hashes |
|---|
|
88da2b1cee373d5f11949c1ade22af0badf16591a871978a9e02f70480e547b2 |
|
566ef5484da0a93c87dd0cb0a950a7cff4ab013175289cd5fccf9dd7ea430739 |
|
ccda8247360a85b6c076527e438a995757b6cdf5530f38e125915d31291c00d5 |
|
87b4020bcd3fad1f5711e6801ca269ef5852256eeaf350f4dde2dc46c576262d |
|
78d75669390e4177597faf9271ce3ad3a16a3652e145913dbfa9a5951972fcb0 |
|
2c7aeac07ce7f03b74952e0e243bd52f2bfa60fadc92dd71a6a1fee2d14cdd77 |
|
988776358d0e45a4907dc1f4906a916f1b3595a31fa44d8e04e563a32557eb42 |
Megazord
| SHA256 Hashes |
|---|
|
dfe6fddc67bdc93b9947430b966da2877fda094edf3e21e6f0ba98a84bc53198 |
|
28cea00267fa30fb63e80a3c3b193bd9cd2a3d46dd9ae6cede5f932ac15c7e2e |
|
c9c94ac5e1991a7db42c7973e328fceeb6f163d9f644031bdfd4123c7b3898b0 |
|
0c0e0f9b09b80d87ebc88e2870907b6cacb4cd7703584baf8f2be1fd9438696d |
|
95477703e789e6182096a09bc98853e0a70b680a4f19fa2bf86cbb9280e8ec5a |
Akira: (Linux Executable File)
| SHA256 Hashes |
|---|
|
3805f299d33ef43d17a5a1040149f0e5e2d5db57ec6f03c5687ac23db1f77a30 |
|
abba655df92e99a15ddcde1d196ff4393a13dbff293e45f5375a2f61c84a2c7b |
|
a546ef13e8a71a8b5f0803075382eb0311d0d8dbae3f08bac0b2f4250af8add0 |
tags
Author

Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks