Amazon moves to stop S3 buckets leaking business data

A long line of very public data breaches have made clear that businesses don’t need to be targeted by sophisticated hackers to have private and sensitive data splashed across the newspaper headlines.
Your company doesn’t need to be hit by a zero-day exploit for its customer database to fall into the hands of online criminals.
No, all you need is for a careless member of staff to upload your sensitive information onto a cloud server, and leave it accessible to anyone with an internet connection.
Time and time again, for instance, we have heard of blunders by multinational companies, government recruitment firms, defence contractors, and more, making the elementary blunder of leaving data on an unsecured Amazon Web Services S3 server that requires no password to access.
Such problems aren’t really caused by the cloud providers themselves, but by the organisations using them – failing to do everything in their power to ensure that the web “bucket” they are pouring data into has been properly configured.
Amazon Web Services (AWS) has clearly had enough of the bad press, and has announced this week a number of new featured to help customers keep their data as private as they intended.
Perhaps the most obvious new feature is a visible warning on the AWS dashboard, telling server administrators if one of their buckets has been left publicly accessible and might be leaking data to the internet.
The warning is displayed in the form of a bright orange “pill”:
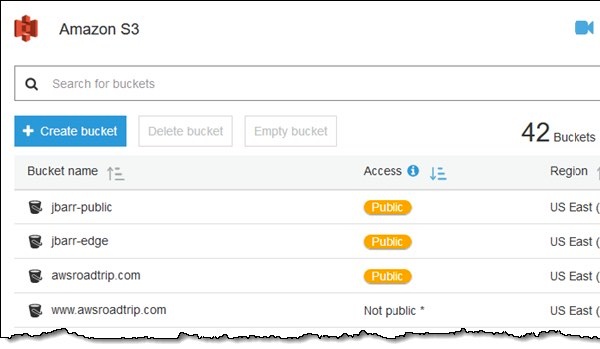
Visiting the permissions tab of a bucket makes Amazon’s advice even more obvious:
“This bucket has public access”
“You have provided public access to this bucket. We highly recommend that you never grant any kind of public access to your S3 bucket.”
The hope is clearly that system administrators will notice the warning and review access rights to their S3 buckets.
But Amazon hasn’t just stopped at displaying bright orange warnings.
As Amazon explains, you can now mandate that all data placed in a bucket must be stored in an encrypted form, without having to create your own policy to reject unencrypted objects.
Furthermore, you can now request daily or weekly S3 inventory reports that will include details on the encryption status of all stored data.
In short, it should be harder than before for companies to leave their data lying around for anyone surfing the internet to scoop up, and simpler for them to have put basic security in place.
That has to be a good thing –for the companies concerned, for their business partners and suppliers, and yes, for their customers as well.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s, having been employed by companies such as Sophos, McAfee and Dr Solomon's. He has given talks about computer security for some of the world's largest companies, worked with law enforcement agencies on investigations into hacking groups, and regularly appears on TV and radio explaining computer security threats. Graham Cluley was inducted into the InfoSecurity Europe Hall of Fame in 2011, and was given an honorary mention in the "10 Greatest Britons in IT History" for his contribution as a leading authority in internet security.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











