Bitdefender Threat Debrief | February 2025

It’s the start of the new year! Ransomware maintains a strong presence in the threat landscape and in 2025, we can expect threat actors to continue to evolve. As a result, it’s important for organizations to remain cognizant of current threats, new trends, and the potential impact those threats may have on their assets and information systems. Doing so aids an organization in making informed decisions as they identify relevant risks to their environment and take steps to mitigate them. We analyzed data from ransomware group websites from January 1 to January 31, identifying a total of 522 claimed victims.
Now, let’s explore the notable news and findings since our last Threat Debrief release.
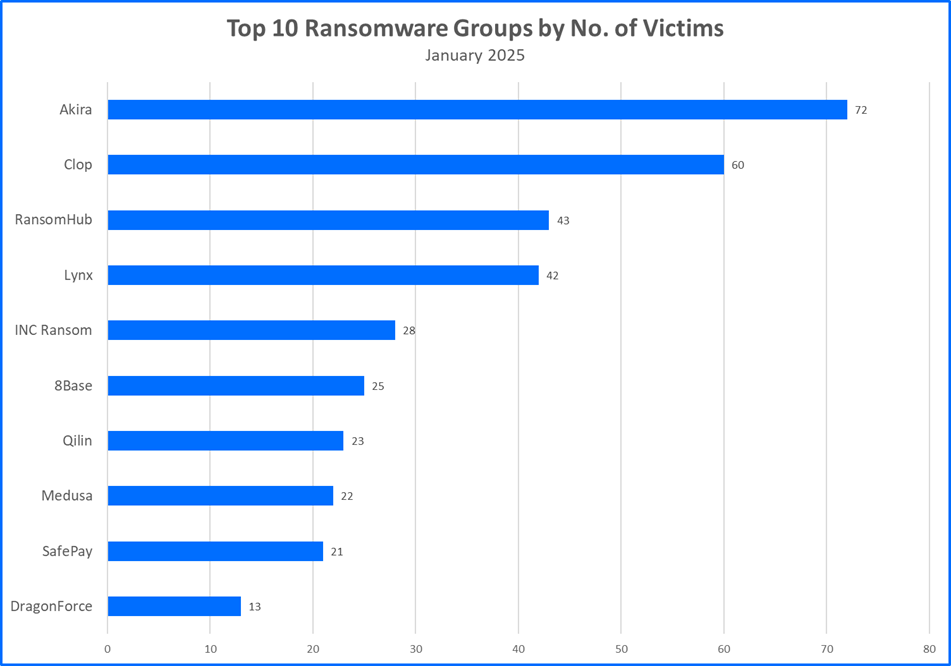
- Akira claims the most victims in January: The ransomware group claimed more than 300 victims in 2024 and they have potential to claim just as many victims (if not more) by the end of 2025. As Akira approaches 575 victims, they are gradually catching up to RansomHub’s 665+ claimed victims.
- Clop remains amongst the Top 10: Clop is a ransomware group that continues to exploit CVE-2024-50623and CVE-2024-55956 which impact Harmony, LexiCom, and VLTransfer products. Organizations are advised to review the recommended actions for those vulnerabilities to ensure that the software they use is the latest patched version. At the time of this release, Clop has claimed a total of more than 660 victims. While at first, this progression may help in demonstrating that Clop’s victim count is close to and/or likely to exceed RansomHub’s, this assumption is questionable and may be re-examined. Some of Clop’s victims have in fact come forward to deny claims of any attacks.
- Operation Talent results in the seizure of critical marketplaces: An international investigation in January led to the takedown of Nulled and Cracked. The marketplaces, which date back to 2015 and 2016, were used to exchange illegal goods such as stolen data, malware, and other materials. Backed by Europol, several federal entities contributed to the investigation efforts, including the U.S. Department of Justice, the Federal Bureau of Investigation, General Inspectorate of Romanian Police, and the German Federal Criminal Police Office. Operation Talent culminated in the seizure of 17 servers and assets totaling €300,000 or $312,480.00 and two suspects were also arrested.
- GD LockerSec claims responsibility for multiple breaches: The ransomware group GD LockerSec has been associated with incidents impacting organizations in the government, education, and technology sectors. Information pertaining to GD LockerSec’s capabilities is limited and there is a small number of reported incidents. However, there are rules of engagement that are defined in the group’s ransomware note. GD LockerSec asserts that they prohibit attacks against the following territories: China, the Commonwealth of Independent States, Cuba, and North Korea. The group allegedly refrains from attacking non-profit organizations like hospitals. In time, as more updates are published on GD LockerSec’s actions, keeping track of their claims and evaluating how their tenets correspond with persistent patterns in victimology or TTPs could yield interesting results.
- An AWS Living Off the Land tactic spells trouble for Amazon S3 buckets: Codefinger is associated with campaigns that leverage victim Amazon Web Services’ account credentials and the AWS server-side encryption scheme to compromise S3 buckets. The attacker first gains access to the victim’s account and identifies Customer Provided keys that have write and read permissions enabled for S3 buckets. The attacker encrypts the buckets; once encryption is underway, the key is not retained in a manner that allows the victim to extract it and perform decryption. The key is modified and represented as hash-based message authentication code. Then, a ransom note is added to all directories and the S3 Object Lifecycle Management API is configured to delete S3 buckets in the span of one week. Organizations are advised to take essential steps to prevent this type of attack; this can be accomplished by assessing their IAM policies and disabling the server-side encryption (SSE-C) settings for S3 buckets.
- GhostGPT gives threat actors another AI tool to play with: Generative AI tools that are intended to automate components of the weaponization and exploitation phases of a cyberattack have been in play for several years now. GhostGPT has joined the ranks of tools like WormGPT and HackerGPT. A user can input instructions into GhostGPT without experiencing conventional prompting restrictions and thus generate responses to design templates to execute a Business Email Compromise (BEC) and other scams. GhostGPT provides functionalities that support not only the creation of malicious scripts and social engineering emails, but also access to Telegram bots.
- 7-Zip flaw allows users to bypass MOTW and open files stored in archives: Mark of the Web (MOTW) is an attribute in the metadata of a file that indicates whether the file originated from outside of the user environment or from the Internet. This feature, native to Windows, is assessed to determine how a file should be executed. When a user opens a file, the MOTW is recognized and that allows a pop-up to appear. The user then confirms if they’d like to proceed with opening the file; if the file is compatible with Microsoft Office, it is rendered in the Protected View. CVE-2025-0411 is a vulnerability that allows a user to open the contents of an archive file without validating that the MOTW is present. An attacker can send a malicious archive file to a user. Then, the user accesses that archive with an affected version of 7-Zip. The MOTW attribute is not maintained across the archive’s contents once they’re extracted and run. Users are advised to update 7-Zip to the latest version, 24.09, to mitigate this flaw.
- The Lynx affiliate panel is unveiled: Lynx is a ransomware group that has engaged in double extortion since summer of 2024. The group’s affiliate panel was recently discovered by a team of security researchers who revealed that a high percentage (80%) of the group’s funds are provided to Lynx’s affiliates. The panel is unique in that it includes a stuffers feature that allows affiliates to share a unique method to authenticate others they may collaborate with when launching attacks. Lynx’s affiliate panel also has a range of binaries to select in campaigns that target Windows and Linux OSes. The Windows and Linux iterations of Lynx have properties that match a significant portion of INC Ransom’s code. Additionally, Lynx ransomware uses Curve25519 Donna and AES-128 encryption.
Top 10 Ransomware Families
Bitdefender's Threat Debrief analyzes data from ransomware leak sites, where attacker groups publicize their claimed number of compromised companies. This approach provides valuable insights into the overall activity of the RaaS market. However, there is a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and might be unreliable. Additionally, this method only captures the number of claimed victims, not the actual financial impact of these attacks.
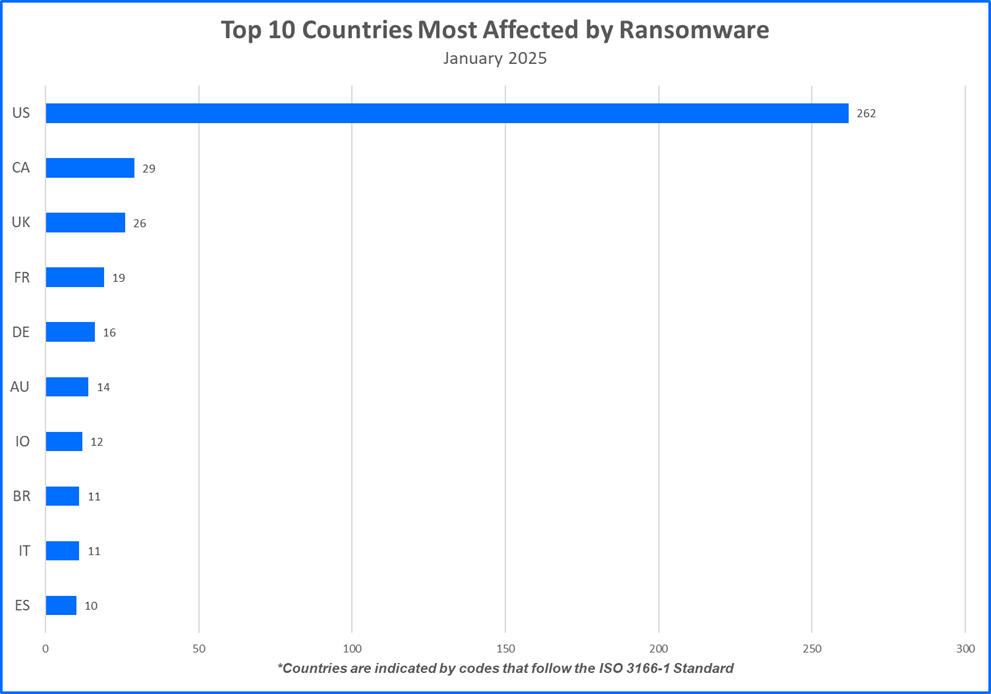
Top 10 Countries
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. This often means focusing on developed countries. Now, let’s see the top 10 countries that took the biggest hit from these attacks.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Vlad Craciun, Mihai Leonte, Andrei Mogage, and Rares Radu (sorted alphabetically) for their help with putting this report together.
tags
Author

Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks









