CIO’s agenda in 2016: Spend more on security to stop data leaks

More than half of C-level managers define the prevention of data leaks as the main priority for their organization in 2016, with business continuity/disaster recovery resilience and identity and access management coming second and third, according to a recent survey.
C-level managers are aware that industrial processes and intellectual property are increasingly valuable for third parties, as this information can help local companies gain a foothold in new markets and acquire new customers, along with their data. Data leakage and data loss prevention have become more important than incident response capabilities, security operations (e.g., antivirus, patching, encryption) or security testing (e.g., attack and penetration), as EY’s Global Information Security Survey 2015 shows.
Data loss prevention (DLP) contains all solutions or processes that identify confidential data, tracks it as it moves in the company and prevents unauthorized disclosure of data by creating and enforcing disclosure policies. Data loss is a particularly stressful for global companies that hold a large volume of personally identifiable information in different legal jurisdictions. Sensitive data can reside on a variety of devices (i.e. physical servers, virtual servers, databases, file servers, PCs, point-of-sale devices, flash drives and mobile devices) and move through various network access points (wireline, wireless, VPNs, etc.). A variety of solutions tackle data loss, data recovery and data leaks.
The Gartner CISO survey has confirmed since 2012 data loss prevention (DLP) as a top priority for CISOs. Growth in DLP is driven by demand for improved intellectual property protection, regulatory compliance and risks associated with adoption of mobility, cloud, the IoT, SaaS and virtualization. Marketing leaders must ensure their products address requirements for these drivers, Gartner says.
“As the maturity of an organization’s cybersecurity increases, it does become easier to demonstrate the value of these investments”, the report says. “Providing more accurate cost assessments for the harm that various cyber-attack scenarios will cause can help justify continued investment and vigilance. Each time your Security Operations Center (SOC) or internal threat intelligence analysts identify an attack in very early stages, it is possible to demonstrate the value of this to the business by extrapolating the damage that otherwise would have been caused had the scenario played out to its worst case. Similarly, the better your situational awareness, the easier it is to streamline and prioritize your spending. A lot of money is wasted on unnecessary controls or equipment that do not necessarily enhance your cybersecurity maturity in the areas where it is most needed.”
Some 49% of the respondents say up to 25% more funding is needed to protect the organization in line with management’s risk tolerance in 2016. Last year, Gartner predicted worldwide information security spending will grow 4.7% to reach $75.4 billion in 2015. According to a RAND Corporation study, the cost of managing cyber-security is expected to increase 38% over the next 10 years, reaching almost $100 billion, as companies spend more on cybersecurity tools. Worldwide spending on cybersecurity has passed the $70-billion-a-year threshold and is growing 10% to 15% annually. Many chief information security officers believe hackers may gain the upper hand two to five years from now, requiring stronger and more innovative defenses. CIOs are not entirely certain of all the methods malicious hackers use to infiltrate systems, and businesses do not want to disclose their safety measures.
The enterprise content-aware data loss prevention (DLP) market will see growth slow to 4 percent to 5 percent through to the end of 2019. Gartner market share data shows stable performance of the top vendors in this segment in 2014. Given the rise of channel DLP (C-DLP) and "DLP lite" solutions, Gartner expects the market will not exhibit such strong growth in its current form in coming years. Most established vendors in this space are transforming the way they deliver comprehensive DLP capabilities, and this transition period will likely impact growth in coming years.
An effective DLP program requires an understanding of: • What data you have • The value of your data • Your obligations for protecting that data • Where your data resides • Who accesses your data • Where your data is going • How you protect data • Your protection gaps and risks • How to respond to data leaks
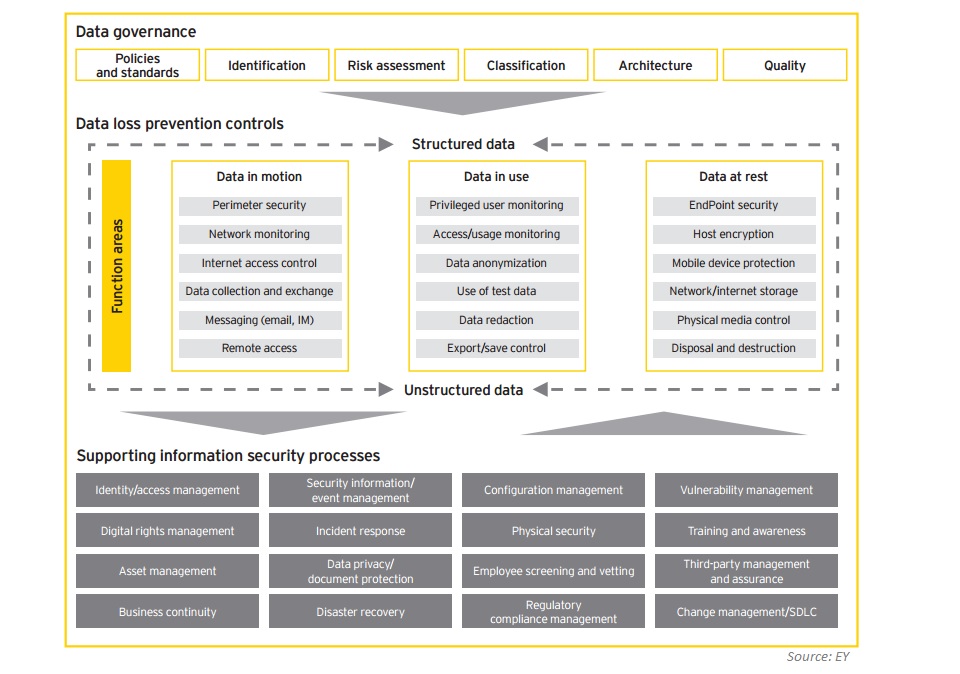
To effectively manage data loss risks, clear business objectives should be defined to drive the DLP program. These objectives should cover the following items as a minimum, as EY shows: • Prevent intentional or unintentional disclosure of sensitive data at rest, in use or in motion to unauthorized parties • Maintain adequate security and provide usability • Protect customer data and brand reputation • Protect personally identifiable information and intellectual property • Reduce the organization’s risk and cost of compliance
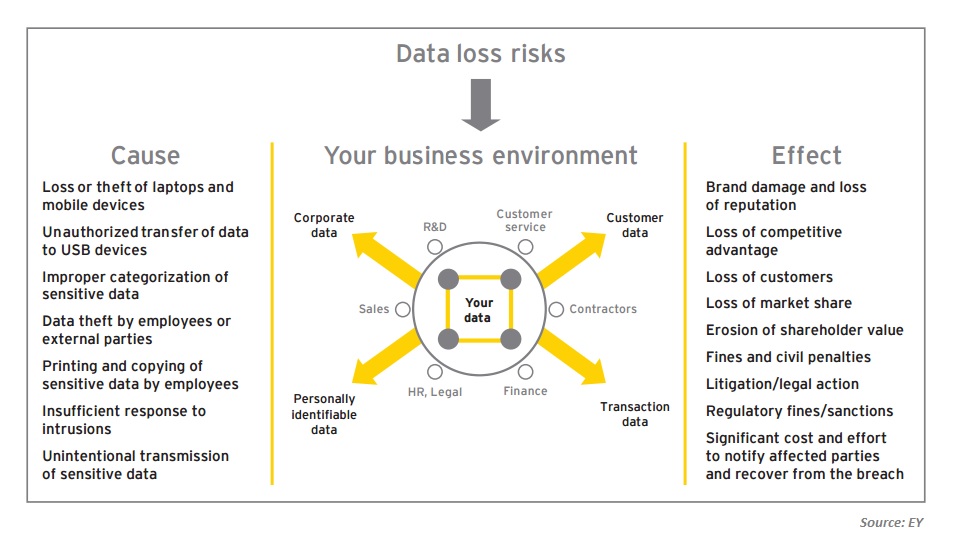
According to a recent post by TechTarget, DLP is a relatively new and immature technology, and also fairly expensive to install and maintain. One of the problems with DLP is that it can monitor users as they send data to unauthorized parties, but it is not efficient at stopping them. While it's possible to configure DLP products to block transmissions that trigger a filter, that will only catch about 80% of the data you should be stopping, said Mark Finegan, president of SIM2K, an Indianapolis consultancy. At best, this can breed complacency when a significant part of data is still leaking; at worst, it gives malicious employees real-time feedback about exactly what the filter does and doesn't catch, so they can adjust their methods. Digital rights management (DRM) or encryption could be useful alternatives to data leak prevention.
tags
Author

Former business journalist, Razvan is passionate about supporting SMEs into building communities and exchanging knowledge on entrepreneurship. He enjoys having innovative approaches on hot topics and thinks that the massive amount of information that attacks us on a daily basis via TV and internet makes us less informed than we even think. The lack of relevance is the main issue in nowadays environment so he plans to emphasize real news on Bitdefender blogs.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











