Deep Dive into a Cryptojacking Operation

A new cryptojacking campaign was recently discovered by our security researchers from Bitdefender Labs. This campaign is using a known DLL sideloading vulnerability in Microsoft OneDrive and deploying a cryptojacking module on infected machines. You can download a full research paper here: Side-Loading OneDrive for profit – Cryptojacking campaign detected in the wild, or read the summary in this blog post.
Threat actors used a technique known as DLL Sideloading to establish persistence and avoid detection. We wrote about this technique previously in our tech explainer article, and more details about this active exploitation can be found later in this blog post. DLL sideloading technique is especially useful when threat actors need to keep a low profile, and not surprisingly, it’s a natural fit for cryptojacking attacks.
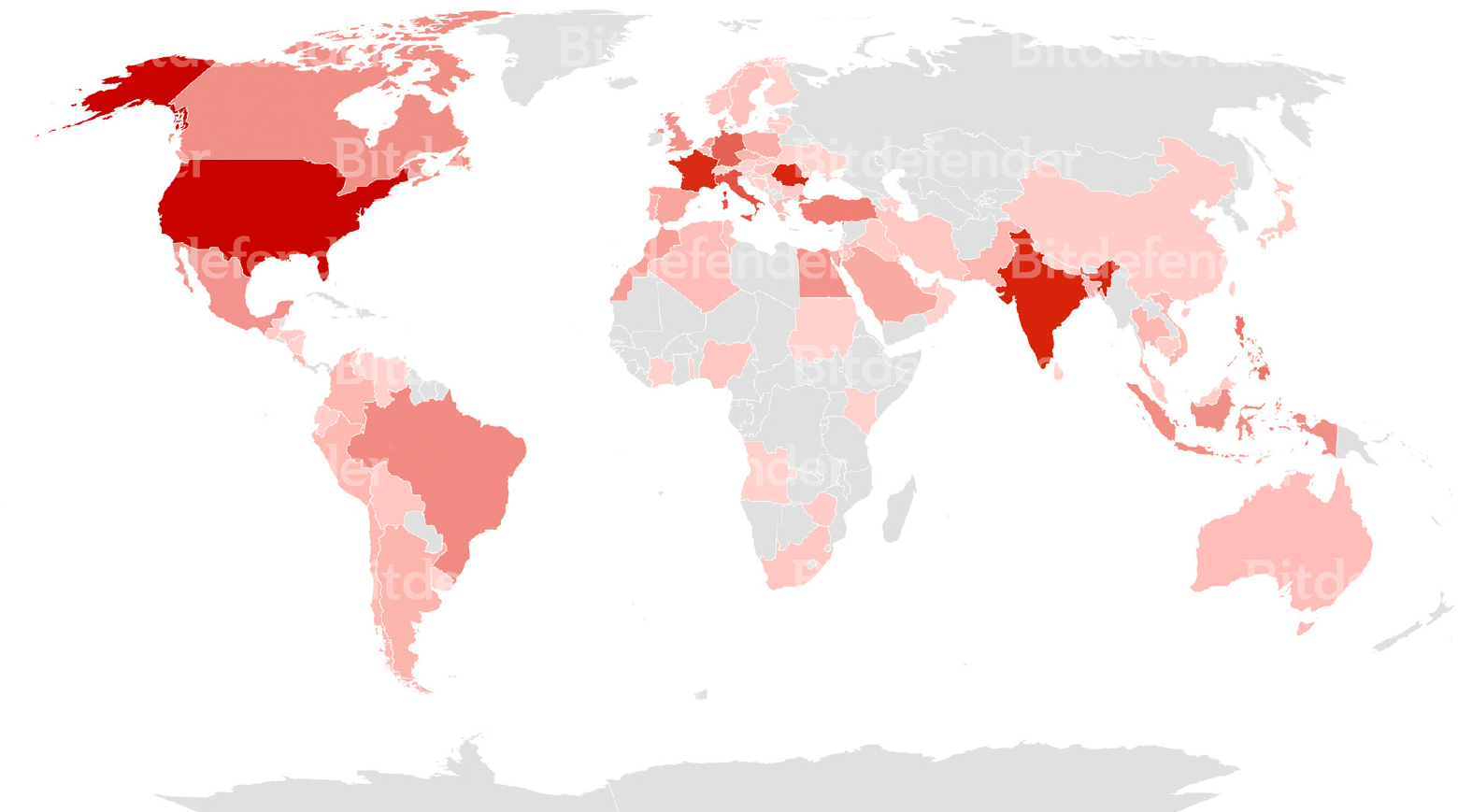
In the two months period from May 1st, 2022, to July 1st, 2022, Bitdefender detected around 700 similar cases of cryptojacking deployments all around the globe.
Cryptojacking is becoming an increasingly interesting profit-generating method for cybercriminals. It can be described as malicious crypto mining, a type of cybercrime motivated by profit. Threat actors hijack a computing resource and use it for mining cryptocurrencies without the knowledge of a victim. Another way to describe this threat is to think about it as threat actors siphoning part of the processing power and converting it into profit.
This is a low-profile attack and a quiet operation that can go undetected for a long time. Compare it to ransomware, which is very noisy and attracts the attention of law enforcement agencies and it is clear why some cybercriminals prefer the low-n-slow method rather than earning a quick buck (watch our video about dismantling one of these groups). For some ransomware groups, crypto mining can be a natural evolution from the ransomware business model, focused on passive continuous income with a lower risk of imprisonment.
Another advantage of cryptojacking for criminals is that both consumers and businesses can be targeted. Automated scanners and vulnerability exploitations are often used for these attacks (security breaches from this vector doubled in the last year) – attacks are opportunistic, feeding on whichever computing devices are available. These attacks can target end user PCs with graphic cards, virtual servers running in the cloud, but also mobile devices or IoT devices. After the Log4j2 vulnerability was discovered in late 2021, crypto miners were deployed in the first wave of attacks.
Ultimately, malicious crypto mining is profitable only in the world where mining itself is a profitable business. Alternative currency Ethereum already switched from the proof-of-work (mining dependent, heavy energy use) to the proof-of-stake approach (mining is no longer needed). But Bitcoin, the most popular cryptocurrency preferred by cybercriminals is still relying on a proof-of-work approach.
Another variable that is holding cryptojacking attacks back is the current state of cryptocurrencies, with many top cryptocurrencies falling 70% or more from the all-time highs a year ago. While ransomware payouts are mostly unaffected by this historically biggest crash of cryptocurrencies, income generated by cryptojacking attacks is directly tied to the value of cryptocurrencies. Or to be more accurate, the cryptojacking’s profitability is directly connected to the profitability of the mining industry overall, and the price of mining rigs is down by 70% this year. This trend can be explained by the lower value of cryptocurrencies, but also by surging electricity costs - a parameter that is irrelevant for cybercriminals but can further hurt victims.
Anatomy of an attack
The complete anatomy of an attack, including all known indicators of compromise (IOCs), is available in the full research paper: Side-Loading OneDrive for profit – Cryptojacking campaign detected in the wild. The following text is a summary of this research.
Initial compromise
This campaign is relying on commodity malware that is disguised as legitimate software – in our samples, we have seen file names like “Adobe Photoshop Setup.exe” or “Free_Macro_V1.3.exe”. This malware acts as a dropper – a malware installer responsible for deploying other malware on the compromised machine.
As a first step, the dropper validates if the compromised system is capable of crypto mining. It checks if the number of available CPU cores is more than 2 and if the display driver is installed and works properly. Unless you are running your computer with a basic driver (“Microsoft Basic Display Adapter” or “Standard VGA Graphics Adapter”), the dropper will start deploying other malicious code on a compromised system.
Droppers can be one-staged (malware code is contained within the dropper) or two-staged (malware code is downloaded by the dropper). In this case, the dropper was a combination of both approaches. The malicious library (secur32.dll) is extracted from the dropper memory and saved to folder %LocalAppData%\Microsoft\OneDrive\. The mining configuration file is also stored inside the dropper binary. But required crypto miners are downloaded from GitHub: lolMiner (for Ethereum and TON mining) and XMRig (for Monero mining). Both crypto miners are legitimate open-source projects, abused by threat actors for illegal mining.
The configuration file and both miners are stored in %LocalAppData%\Microsoft\, saved with random filenames, and encrypted with a password (unique ID for each machine). These random files are recognized by a static suffix that is added after a random string (“_s” for the configuration file, “_c” for XMRig miner, and “_g” for lolMiner).
Finally, the dropper will also ensure that OneDrive.exe is executed on each logon by adding two registry entries:
- REG ADD HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v OneDrive /t REG_SZ /f /d %LocalAppData%\Microsoft\OneDrive\OneDrive.exe
- • REG ADD HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run /v OneDrive /t REG_BINARY /f /d 020000000000000000000000
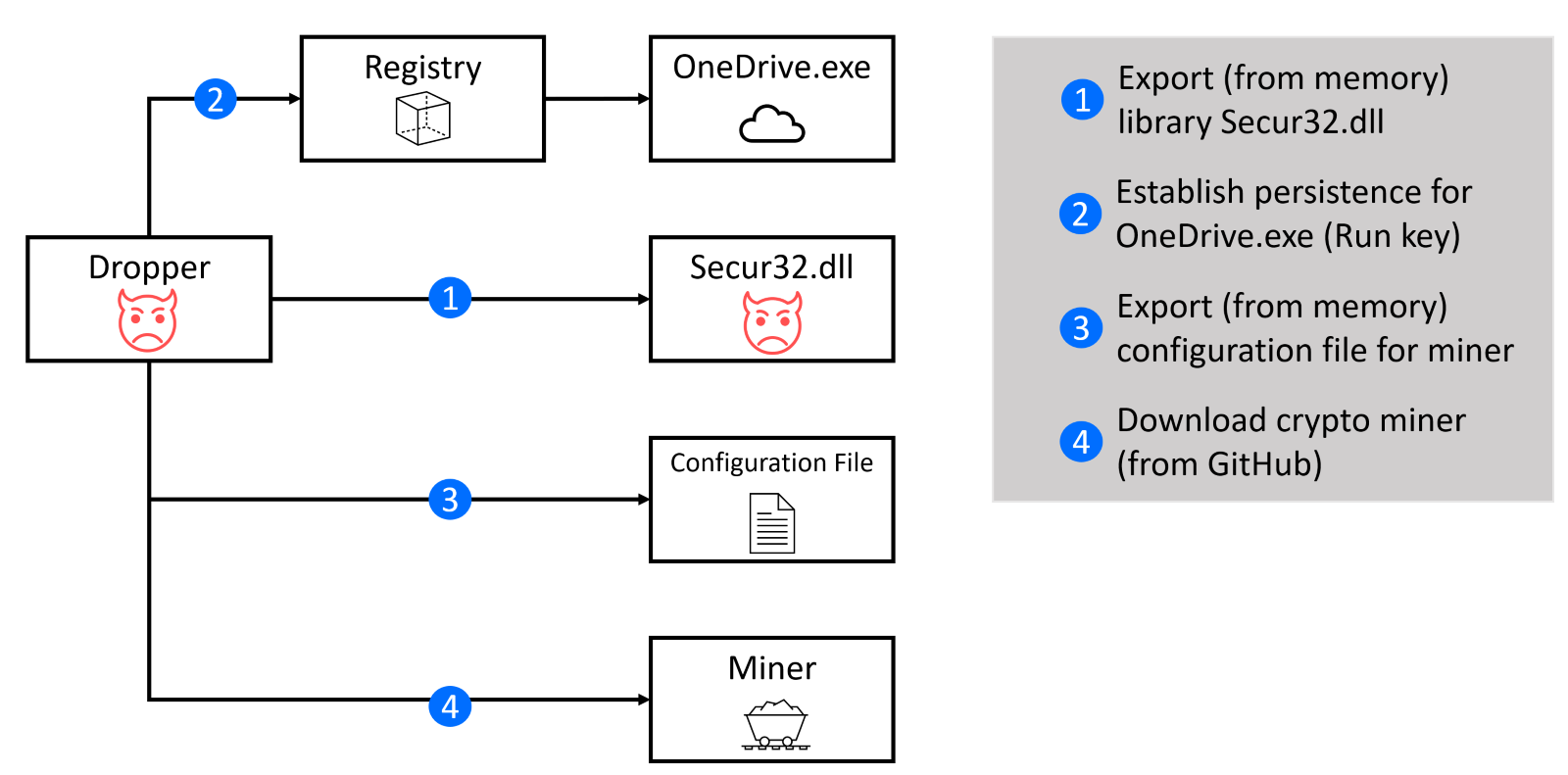
The actions by the dropper on a compromised system
Why the OneDrive.exe file? It is part of the defense evasion strategy that was adopted by this campaign.
Defense evasion
The malicious library secur32.dll is the main implant and it is loaded by a technique called DLL sideloading (read our recent tech explainer). It is active exploitation of Microsoft OneDrive where malware library is masquerading as one of the OneDrive libraries. Two processes are loading this library – OneDrive.exe (executed on log-on) and OneDriveStandaloneUpdater.exe (scheduled task). OneDrive updater is started by a scheduled task and is launched every 24 hours (default setting). This allows threat actors to establish persistence in the compromised system.
It is important to note that per-machine installation of Microsoft OneDrive is only partially vulnerable to this kind of attack, as the per-machine updater does not include the %LocalAppData% folder when searching for libraries. The OneDrive.exe triggered by the Run registry key however is still capable of sideloading the malicious library.
DLL sideloading is one of the techniques used in this campaign to avoid detection, but it’s not the only one. For example, a dropper and malicious library are not storing Windows API names in memory, as that could lead to malware detection based on the names of imported libraries. Instead, only the hash of the API name is stored inside the malicious executable. When malware needs to call a function, it enumerates all API functions, until an API name with a matching hash is detected.
Dropper stores the names of DLL files and the configuration for the crypto mining software in XOR encrypted form. Both configuration file and miner binaries are encrypted using a GUID of the compromised machine, and decrypted data is stored only in the memory of the infected machine (never touching the hard disk).
To further hide the workload, the process hollowing technique is used. With this method, a legitimate process is created in a suspended state, then the memory is replaced with malicious code. This process injection can hide malicious code in two processes – svchost.exe and conhost.exe. For the casual observer, the mining operation performed by these two trusted and well-known processes is completely invisible (aside from the higher load on the system).
The malware is also looking for the presence of process monitoring tools like Task Manager or Process Explorer – if they are detected, hollowed processes are killed and not restarted until these tools are closed.
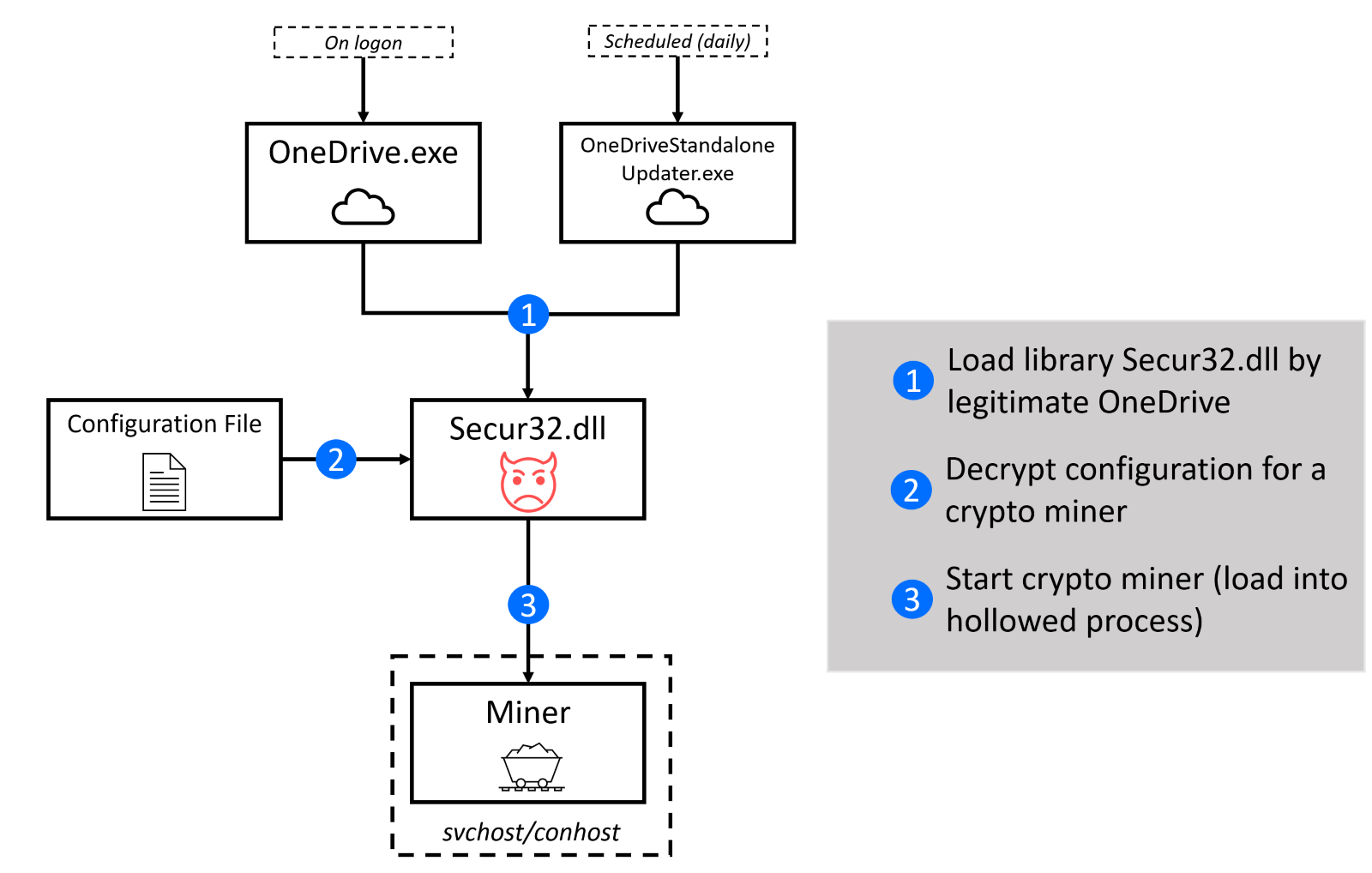
After triggered, the malicious library proceeds with crypto mining
Conclusion & recommendations
This campaign is using a combination of techniques to avoid detection and keep the illegal mining operation a secret. All these techniques help malware to blend in with the processes that normally run on a system, allowing threat actors to keep a low profile and continuously generate profit.
The best protection against modern cyber-attacks is a defense-in-depth architecture. Start with reducing your attack surface and employing automated controls to prevent most security incidents. Choose a security solution that uses multiple layers of security, including IP/URL reputation for all endpoints, and protection against fileless attacks.
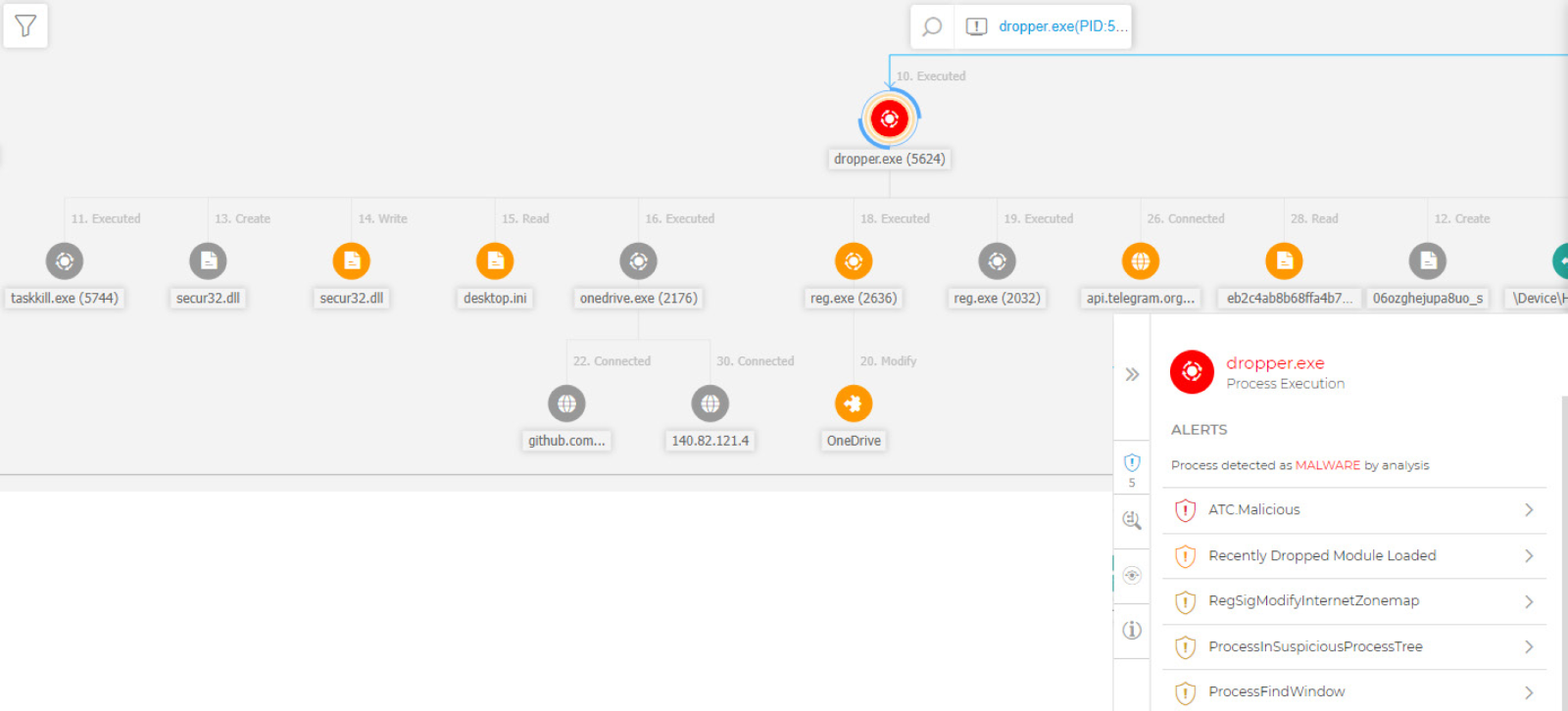
Dropper malware detection as seen in Bitdefender GravityZone console
Finally, for the few incidents that get through your defenses, lean on security operations, either in-house or through a managed service, and leverage strong detection and response tools. There are multiple suspicious actions detected by Bitdefender XDR, including (but not limited to):
- Dropping the malicious secur32.dll
- Using
taskkill.exeto stopOneDrive.exeprocess - Malicious library sideloaded by
OneDrive.exe(or updater) process - Using
reg.exeto add OneDrive to startup (establishing persistence) - Process hollowing
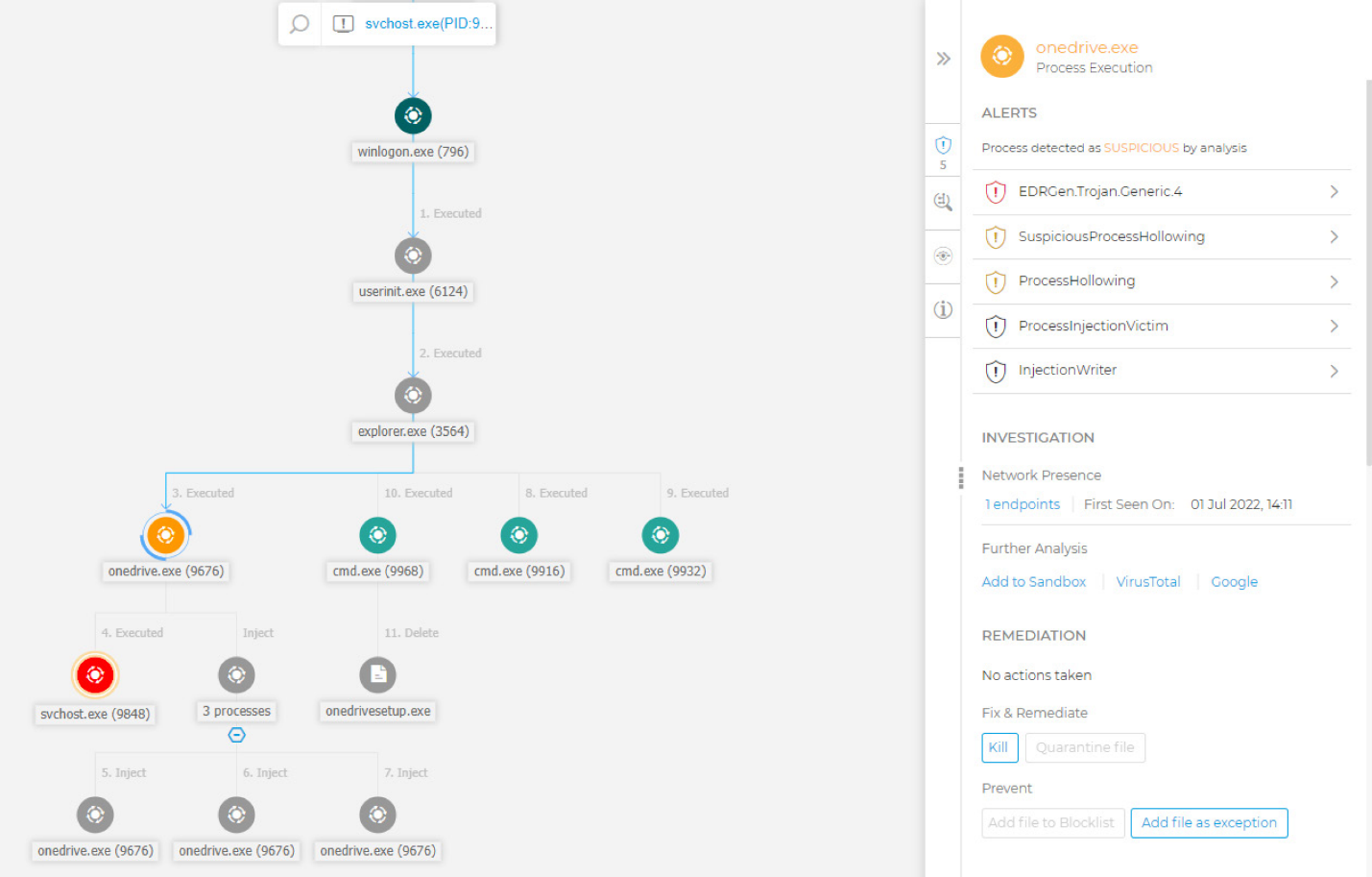
Suspicious behavior detected by Bitdefender EDR module
Learn more about Side-Loading OneDrive for profit.
We would like to thank Bitdefenders Balint Szabo and Janos Gergo Szeles (sorted alphabetically) for their help with putting this report together.
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











