How Sandbox Security Can Boost Your Detection and Malware Analysis Capabilities

Zero-day exploits, advanced persistent threats (APTs), and other complex cyber threats have played a huge role in recent high-profile attacks, like the MGM Resorts attack or the Bank of America data breach.
With threat actors expanding their arsenal, security professionals must follow suit. Employing sandbox security is one of the best responses to today’s complicated threat landscape. It can protect organizations from modern security risks, and elevate their threat intelligence.
What is Sandbox Security?
Sandbox security solutions use virtual machines to detonate files in a safe environment and analyze their behavior. It’s a type of dynamic malware analysis, with a lot of applications that can be broadly separated into two categories: detection and malware analysis.
In detection, sandbox environments are very useful to stop zero-day threats, or APTs that would escape straightforward detection methods. Static analysis can’t reveal everything about a file, so detonating it in a secure environment can reveal more about seemingly harmless files. This information can be used to filter suspicious programs and protect endpoints, gateways, or appliances.
In malware analysis, sandboxing is used by researchers and security professionals that want to understand potentially malicious code or malicious software. By letting the unwanted application run its course in sandbox environments, security operations center (SOC) and security analysts can observe the different attack stages of a threat, even if an anti-malware solution might’ve stopped it.
This lets security professionals understand common tactics, techniques, and procedures (TTPs) employed by threat actors and harden their defenses.
Different Types of Sandbox Environments
Generally, there are two types of sandboxing environments: cloud, or on-prem.
Cloud sandboxing is the industry standard today. It’s easier to use, especially for a remote team, and it’s much more scalable. Since it’s usually hosted by a security company, it’s also cheaper to maintain, and it provides advanced threat context for any file.
On-premises sandboxing gives you more control over the set-up, and total privacy out of the box. However, a lot of cloud sandboxing solutions can offer the same level of privacy by anonymizing information and deleting files after detonation in the sandbox environment.
On-prem sandboxing demands more engineering resources, higher hardware requirements, and it’s harder to update. In contrast, cloud sandboxes have better detection, they’re highly scalable, easier to integrate, and cost less to maintain. Given the advantages of cloud sandboxes, we’ll focus on them for the rest of the article.
How Sandboxing Works
The process of scanning a file in a sandbox is different based on your provider, but it’ll generally feature these steps:
- File submission through a UI or API call.
- Prefiltering of the file to get a quick verdict.
- Detonation in an appropriate virtual machine.
- Event logging and automatic analysis of the file’s behavior.
- Returning a verdict to the user, in a human-readable format.
For reference, here’s an overview of how the Bitdefender sandbox works:
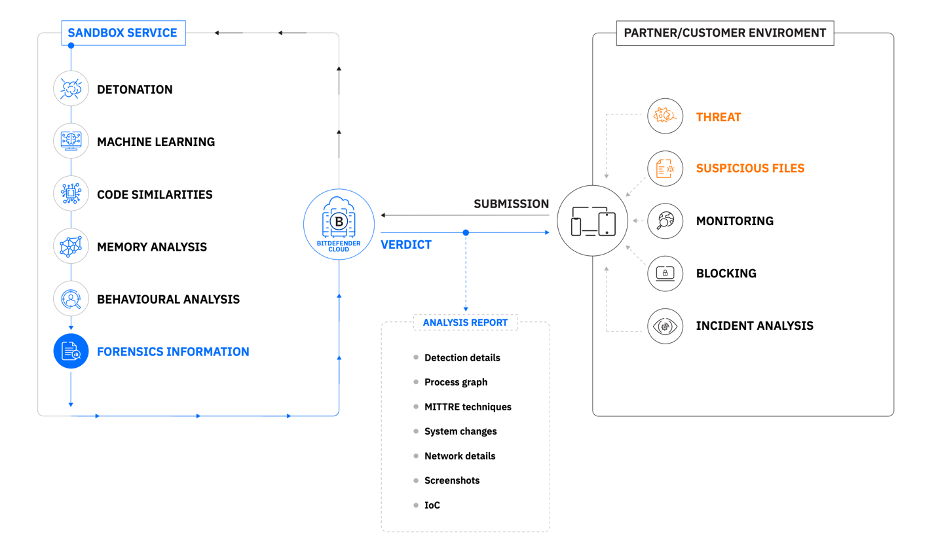
Sandbox environments simulate a host machine’s physical hardware, and the end user’s operating system. However, advanced malware can sometimes recognize it's being detonated in a secure virtual machine, and obfuscate malicious intent.
That’s why it’s important to pick a reliable sandbox software provider, that can recognize sandbox evasion techniques, and guarantee proper detonation in the sandbox environments.
Benefits of Sandbox Security
One of the biggest perks of sandbox security is improved protection. It’s very hard to stop advanced threats like APTs or zero-days with simple signature-based detection, or even common patterns.
The only way to stop potentially malicious software consistently is dynamic malware analysis. Executing malicious code will reveal information that would be harder or impossible to obtain otherwise, like file system changes, writes to memory, executed API instructions, and plenty more.
Besides improved detection, malware sandboxing is also indispensable to SOC analysts and security researchers. It can provide insights into malware intent, relevant IoCs and IoAs, common TTPs , and useful context for threat actors.
Thanks to these detection and analysis benefits, sandbox security is key for modern security posturing.
Crucial Features Every Good Sandbox Has
If you’re interested to invest in a reliable sandboxing solution, you’ll want a solution that can offer:
- Permissible rate limits: If you can’t submit a lot of files to a sandbox, your detection and analysis capabilities will be limited too.
- Efficient prefiltering: Prefiltering is an important feature if you want quick verdicts, and reliable alert triage.
- Qualitative threat detection engines: The best sandboxes employ advanced anti-malware technologies to detect threats.
- Deep and relevant reporting: Sandboxing is only useful if you can get actionable information on malware behavior and IoCs.
- Ease of integration: Whether you submit files via API or a user interface, good sandboxes are easy to integrate.
- Balance between execution time, verdict quality and report depth: A good sandbox can adapt the execution time to different use cases, running just as much as it’s needed for a quick verdict, or letting a file execute for longer to get detailed forensics.
How to Use a Sandboxing Environment
The way you’ll use a sandboxing environment depends a lot on the provider you pick, whether you choose cloud or on-prem, and your use case.
If you want to automate sandboxing for malware detection, API calls to the sandbox service are the best choice. For manual analysis, drag-and-drop submissions in a user-friendly interface are better. Either way, submitting suspicious code, suspicious files, or URLs for sandbox testing is usually straightforward.
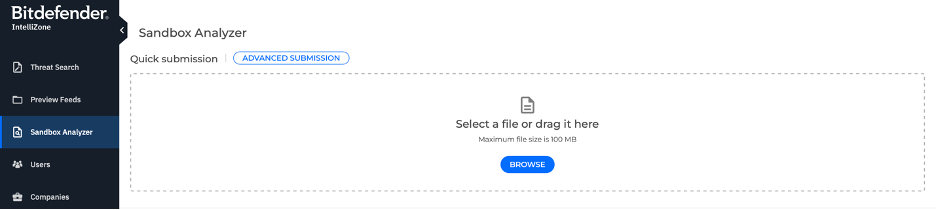
For example, Bitdefender lets users access its sandbox service via API, or the IntelliZone platform. There, you can submit URLs and files for sandboxing.
Once our analysis is over, reports can be downloaded in a human-readable format:
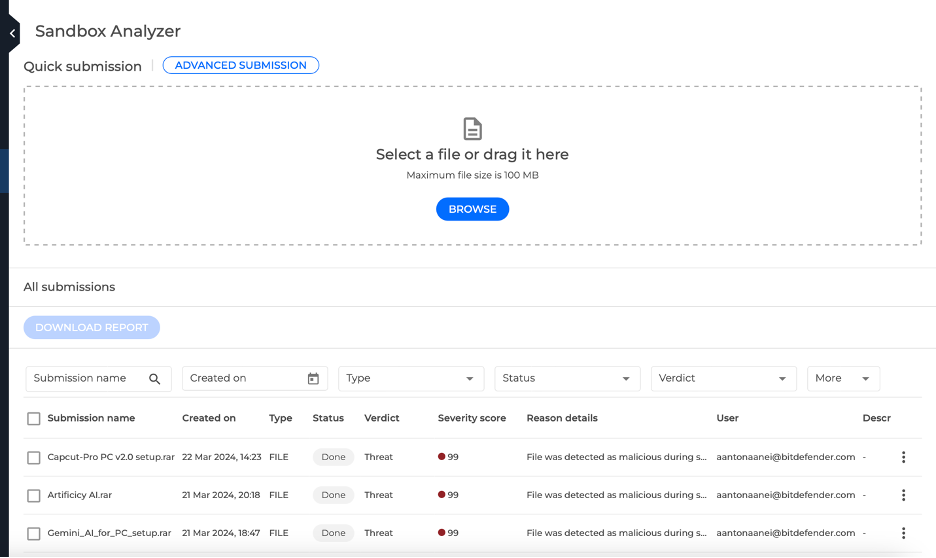
IntelliZone centralizes all of Bitdefender’s advanced threat intelligence in a single pane of glass. If you want to find out more about it, and try it for free, check out our Threat Intelligence portfolio.
How Bitdefender Can Help
Bitdefender’s sandboxing technology offers best-in-class protection against breaches, data loss, and all the costs associated with cyberattacks. It’s a highly scalable, powerful and isolated environment to run in-depth analysis of any suspicious file or URL.
Our malware detection engine is constantly at the top of independent industry tests. The over 99,9% detection rate from third parties like AV-Test is maintained across operating systems.
Bitdefender's sandbox also features an innovative prefiltering system.
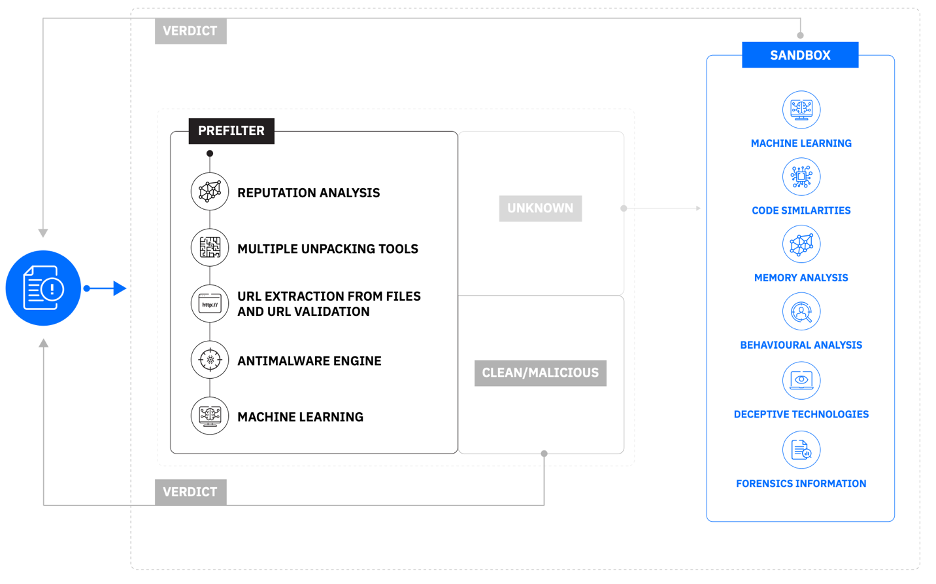
This cloud prefilter is useful to reduce the number of detonated files, triage alerts easier, and get quick verdicts.
If a file is sent to the sandbox, users can expect a comprehensive analysis report in minutes. Scanning and detonation is completely offloaded to the cloud, so the client’s system resources are freed up.
A unique perk of Bitdefender’s sandbox is that execution time is dynamic, based on the file’s behavior. This guarantees the best balance between quick verdicts and appropriate detonation.
Bitdefender’s sandbox report features a lot of actionable data, like general information about the threat actor:
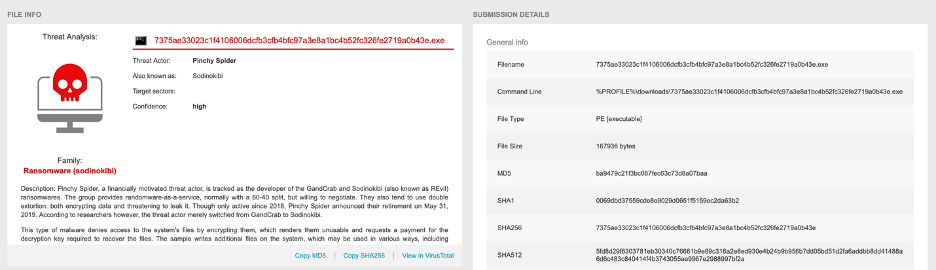
A detailed description of the file’s behavior:
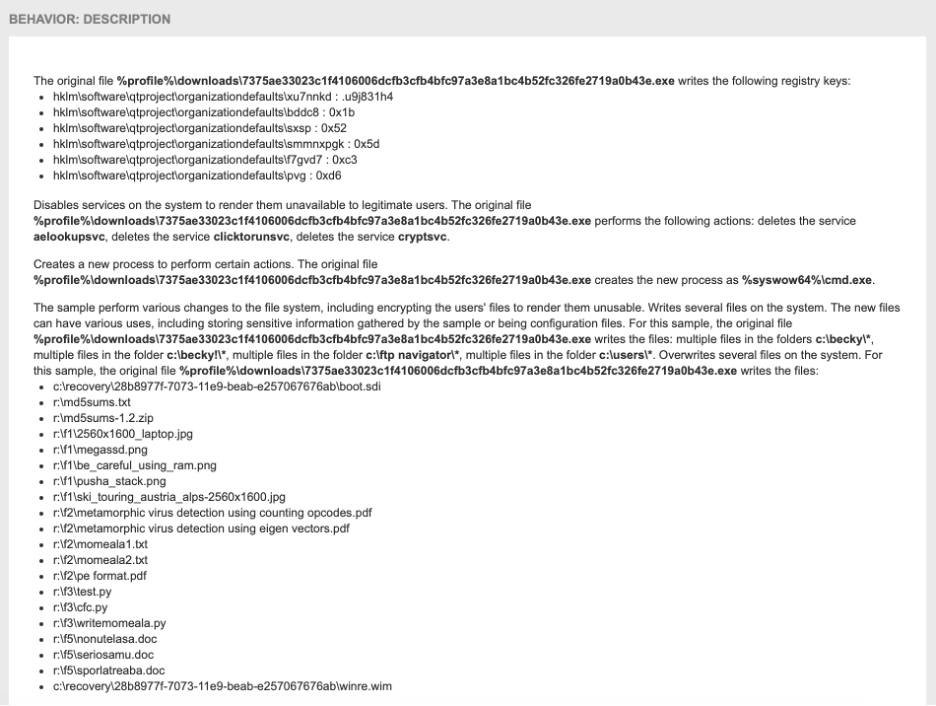
And a lot of other summaries, like a list of system changes, MITRE ATT&CK framework references, and even a geographic breakdown of a file's network activity:
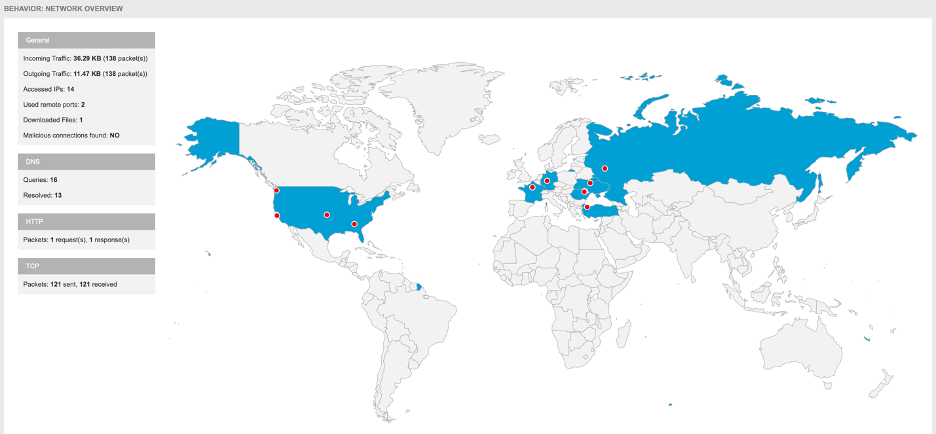
The reports also feature screenshots of the malicious file in action, detailed IoCs, and graphs breaking down its behavior:
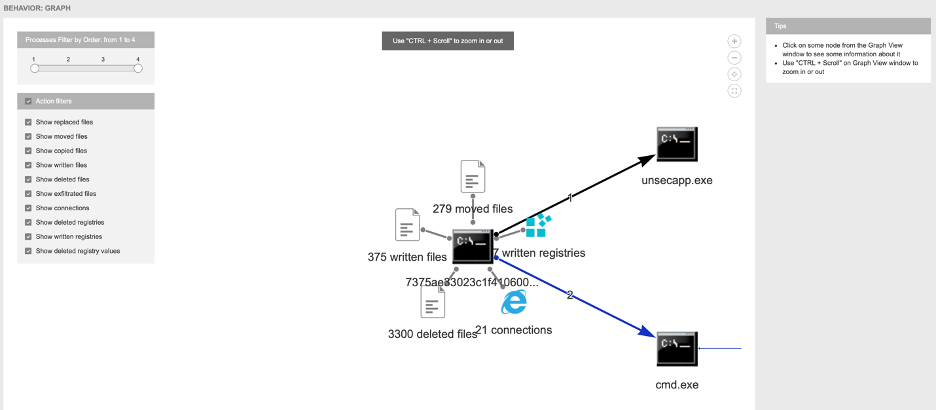
These reports are delivered by a robust service with easy API integration, high scalability, permissible rate limits and tailored privacy options.
It’s a complete package that helps security teams protect any operating system against modern threats. Moreover, it’s an extremely valuable tool to execute untrusted code in an isolated environment.
Evaluating the Bitdefender sandbox security solution is free of charge and includes technical support. For more information, reach us here.
tags
Author

Theodor Porutiu is a Technical Marketing Architect with a knack for writing engaging content and communicating complicated topics in simple terms. He enjoys short hikes and long gaming sessions in equal measure, and he gets really hyped about a different open-source project every week.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











