Rafel RAT: A Pest Invading Droid Systems

Mobile security is facing a major challenge in the form of Android malware. Picture a smartphone, an essential part of daily life, becoming a tool for cybercriminals. Attackers are drawn to Android systems for several reasons: a massive user base, extensive customization options, and flaws in Android’s update and security processes. With such high stakes impacting user and system data, understanding these threats is crucial to staying protected. Attackers are irresistibly drawn to Android due to its vast user base. With over three billion users globally, Android offers a lucrative opportunity for large-scale cyberattacks. This far exceeds the iOS user base, which stands at just over one billion. The sheer volume of potential targets makes Android an attractive playground for cybercriminals, eager to exploit its reach for their malicious endeavors.
While Android offers more customization options than iOS, this can be a double-edged sword. Unintentional security gaps, such as unchecked features or or inactive verification mechanisms, can significantly increase risks. For example, allowing applications to run from unverified sources or having permissions granted automatically without user input would increase a user’s likelihood of malware exposure.
Unlike iOS, Android systems experience inconsistent updates and security fixes due to manufacturer-specific issues like delayed or fragmented patch cycles. These inconsistencies can leavevulnerabilities unaddressed across various Android devices. Consequently, the Android OS has seen a spike in targeted attacks, including those launched with the aid of remote access trojans (RATs) like Rafel RAT.
Rafel RAT: A Stealthy Threat to Android Devices
Rafel RAT is an Android malware with an open-source design and the ability to camouflage its application type, often masking as a common BlackMart application. BlackMart, also known as BlackMart Alpha, is an application marketplace where users can download Android applications; the applications available are typically pirated, free versions of the commercial offerings found on the Google Play Store that are embedded with malwareAn active GitHub repository has the source code and elements needed to build Rafel RAT and launch an attack.
Rafel RAT targets out-of-date Android operating systems, specifically mobile phones and tablets, making it a convenient and powerful tool for a bad actor’s campaign. Check Point Software uncovered that common targets are devices with Android versions 11, 5, and 8. While this means that devices older than Android 11 are the most vulnerable to a Rafel RAT infection, devices with newer OS versions may be susceptible to this attack. User failure to push software/firmware updates or delays in rolling out security fixes are two causes that could result in a newer device becoming vulnerable.
Malware-as-a-Service (MAAS) is a subscription model that allows criminal organizations to purchase malware from various markets and use it to benefit their operations. While Rafel RAT does not fall into the MAAS model due to its open-source nature, that may change in time as its design and usage evolves.
The Infection
The graphic below illustrates the steps involved to get Rafel RAT onto a victim’s system. A phishing campaign is one method to initiate the first step in the process of downloading Rafel RAT to a target device. Once a user clicks a malicious object or link in an email, the download occurs, and an installation process follows. It is worth noting that an Android device does not need to be rooted for the download and installation process to occur.
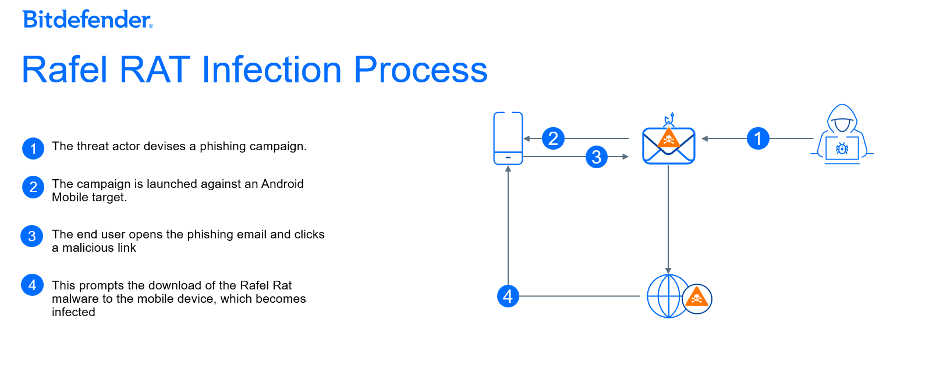
Figure 1: The initial infection
Once Rafel RAT finishes installing, it activates a process to request permissions; a prompt may appear for the user to accept permission to enable notifications and allow access to several settings and applications. After the user hits allow on the prompts to grant permissions, the attacker has elevated permissions to access the following Android services: System and Storage, Camera and Microphone, Contacts, Calls, and Messages.
Equipped with access to these services, the bad actor can steal device, caller, and account information such as credentials and take control of the device, including the ability to lock it and set a new PIN. It is important to note that while the Rafel RAT attack may disrupt the user’s ability to start and stop applications or processes and can lead to data loss due to an attacker’s targeted deletion of files, the total loss of device functionality is not an outcome that is associated with this attack.
After step three in the process, the attacker has two options. They can either proceed with 4A: Deploy Ransomware, or the more common choice, 4B: Establish an addition route alongside the C2 server to continue exfiltrating data and intercepting authentication codes.
Basic Capabilities
When looking at the design of malware, the ideal Android malware will operate in a fashion like other malware types; Rafel RAT gains access to a target system, alters the system’s settings, establishes a connection with the attacker network, and exfiltrates the data and other assets that it collects in the process.
Advanced Capabilities
The table below defines Rafel RAT’s greater capabilities which distinguishes it from other common Android trojans.
 |
Ransomware panel. This panel allows the attacker to introduce a malicious payload (ransomware) and encrypt device data. |
 |
Message interception functionality: Rafel RAT can intercept SMS messages, including 2FA codes. It typically captures 2FA codes from the target device and passes them on through a Discord message. While Rafel RAT can obtain data from user text messages, Authenticator Apps are not a common attack vector. |
 |
Hidden and background processes: Rafel RAT can run hidden processes in the background to load other malicious objects on a victim device. |
 |
Surveillance: Since Rafel RAT can take control of a phone, and exploit permissions to log phone keystrokes and capture photos and video. |
Figure 2: Additional functions
Ransomware Functionality
It is important to note that while Rafel RAT’s ransomware panel incorporates the ability to launch a ransomware attack, Rafel RAT itself is only a vehicle to deliver that weapon. Rafel RAT is malware that is primarily designed to spy on victims and steal data and communications. The graphic below expands on the chain of actions that occur after the phishing campaign.
Anti-Analysis Capabilities
Rafel RAT does not employ packing or obfuscation techniques to conceal its malicious attributes. However, Rafel RAT has emulation detection properties, which will prompt it to disrupt or stop malicious processes in instances where an analysis or testing environment is detected. As a result, researchers must exercise due diligence when selecting methods to analyze Rafel RAT samples and bypass emulation detection.
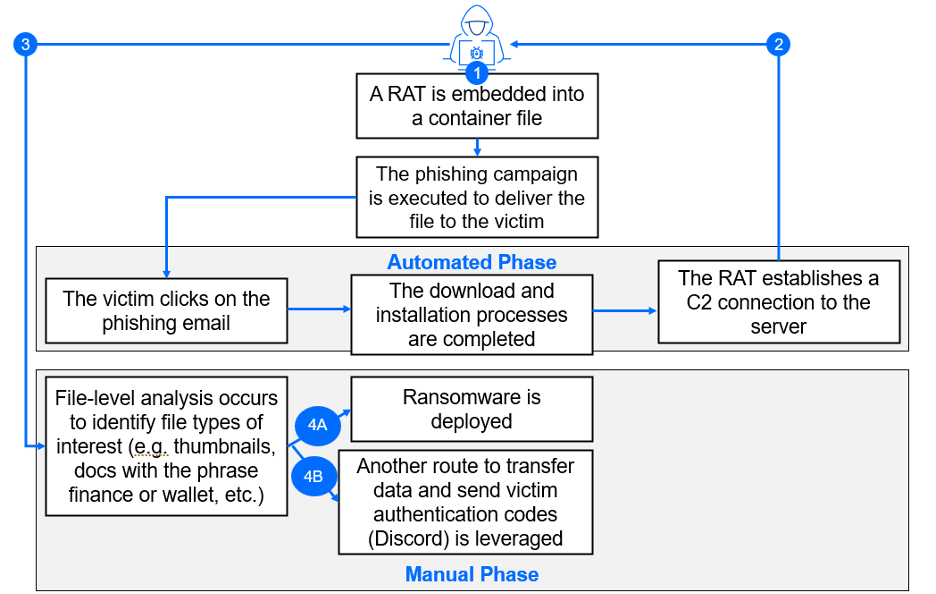
Figure 3: Rafel RAT attack structure.
Conclusion and Recommendations
Rafel RAT poses a great threat to Android users, especially those who have devices using Android versions older than 11. Victims of cyber espionage and data theft are commonplace in the current threat landscape. As a result, users must exercise caution when accessing unknown or suspicious links and applications. They should stay informed to identify the signs of a malware infection and understand best practices to maintain good cyber hygiene.
Users concerned that their Android device is infected may monitor their device for the following changes:
- Sudden Restrictions (impacting the use of the phone, apps, or change of permissions)
- Inconsistent Battery Life
- Unprompted Screen Locks
- Slowing of Device Performance
- New Applications and Services
- Missing Files or Directories
An organization that implements best practices can reduce the risk of falling victim to a Rafel RAT attack. These practices include incorporating threat intelligence, patch management, and mobile device security processes into a mature information security program.
Advanced Threat Intelligence: The right threat intelligence solutions can provide critical insights about attacks. Bitdefender IntelliZone is an easy-to-use solution that consolidates all the knowledge we've gathered regarding cyber threats and the associated threat actors into a single pane of glass for the security analysts, including access to Bitdefender’s next-generation malware analysis service. If you already have an IntelliZone account, you can find additional structured information under Threat IDs BD8svvodp8, BDuq18888y, BDgo7ejvh8, BDqnetx899, BDsd3agxn3, BDgl4j8m5n, and BDdvnaspz1.
Mobile Device Management: Organizations who use a MDM solution to enforce system and application security requirements can minimize the risk of a vulnerable device being exploited.
Mobile Threat Defense: MTD or Mobile Threat Defense adds another type of protection for a mobile ecosystem on top of MDM. Unlike MDM, the purpose of Mobile Threat Defense is to protect mobile devices from cyber threats and attacks thereby safeguarding sensitive data and maintaining user privacy. It is the only solution responsible for eliminating cyber threats.
For more information about Bitdefender Mobile Security and solutions available to protect your devices and data, please refer to the links below:
- Bitdefender GravityZone Security for Mobile official site: GravityZone Security for Mobile
- Bitdefender GravityZone Security for Mobile Solution Brief: GravityZone Security for Mobile Solution Brief
- Bitdefender GravityZone Security for Mobile Datasheet: GravityZone Security for Mobile Datasheet
Indicators of Compromise
| Domains |
|---|
|
bazfinc.xyz |
|
casperbc.com |
|
districtjudiciarycharsadda.gov.pk |
|
raas.site |
|
uni2phish.ru |
|
zetalinks.tech |
| MD5 |
|---|
|
21c2de1ee0ea905c3c9ed6ab1bb09ced |
|
4a40410e3ed082aa20d4eaa508ed451d |
|
4e604e03cba3ad8da5f1ebbd7ba100bb |
|
578ab3fb6d1b6313f106518128053931 |
|
94bca3926cd70f60d54be7218dd7ac55 |
|
d92eecc462e59f3e2061a6a568935b96 |
| SHA1 |
|---|
|
14596ae969626eecdb7aa5d73a1b89dd0fbc53f8 |
|
3229106dee092e03d7344e398e57e47961e1df8c |
|
3b6fceace06f575f4ce1791a7f6c35e35b1ee703 |
|
9b9ac365f701904533d21465f4e55a38e2f093c4 |
|
ace5a4e3ab9a2d25ce475ef88ddc1d3a27cacb9e |
|
b0a58d44603f9b184cf26bf5b265644f9843faef |
| SHA56 |
|---|
|
344d577a622f6f11c7e1213a3bd667a3aef638440191e8567214d39479e80821 |
|
442fbbb66efd3c21ba1c333ce8be02bb7ad057528c72bf1eb1e07903482211a9 |
|
5148ac15283b303357107ab4f4f17caf00d96291154ade7809202f9ab8746d0b |
|
9b718877da8630ba63083b3374896f67eccdb61f85e7d5671b83156ab182e4de |
|
c94416790693fb364f204f6645eac8a5483011ac73dba0d6285138014fa29a63 |
|
d1f2ed3e379cde7375a001f967ce145a5bba23ca668685ac96907ba8a0d29320 |
tags
Author

Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










