Technical Advisory: SeriousSAM – Windows 10 Flaw Can Be Used by Malicious Actors to Obtain Administrator Rights
Newer versions of Windows 10 (build 1809 - 2018-present) may be vulnerable to a local privilege escalation enabled by misconfiguration on the Security Account Manager (SAM) database file. SAM is a database file that stores password hashes for all local user accounts. (This file can be found in folder %SystemRoot%\System32\Config\SAM and it is mounted in registry under HLKM\SAM.)
Why is this a critical issue for all Windows machines using build 1809 and newer? Attackers with access to password hashes can use them in ‘pass-the-hash' attacks to escalate privileges and obtain administrative privileges on the local machine.
Background Context
On July 17, security researcher Jonas Lykkegaard discovered that registry files within Windows 10 can be accessed by members of the BUILTIN\Users group. While this misconfiguration seems to affect all registry hives (including SYSTEM and SECURITY), it could possess serious implications when trying to access the SAM registry hive file.
How to Check if Your Machine May Be Vulnerable
To check if your system may be vulnerable, follow these steps with elevated privileges:
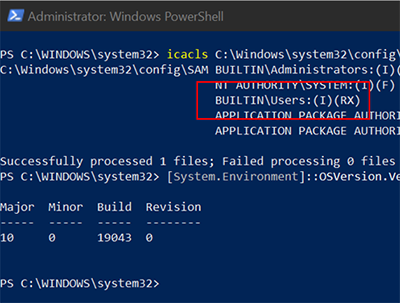
icacls c:\Windows\System32\Config\SAM
If you see BUILTIN\USERS:(I)(RX) in output, your system is vulnerable (RX identifies Read/Execute permissions).
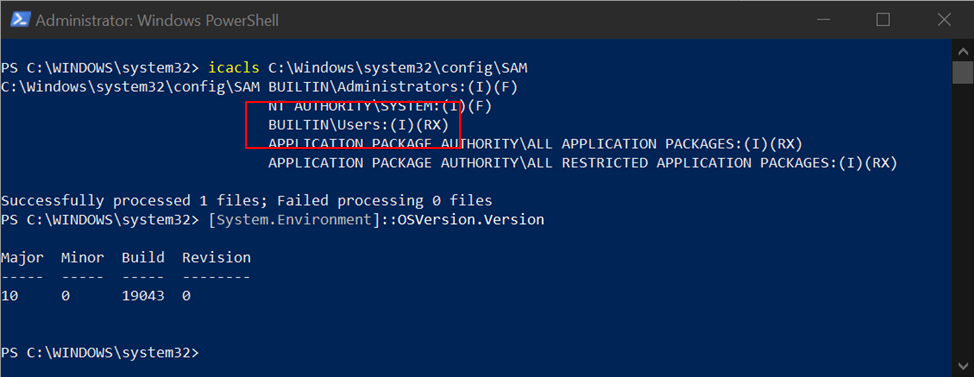
Vulnerable system (Windows 21H1)
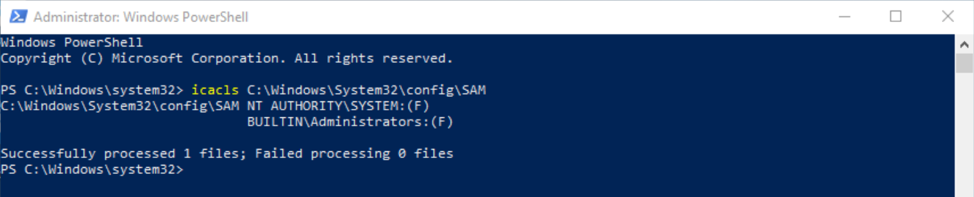
Correct permissions (Windows 10 build 1803)
During normal operation, the Windows kernel keeps an exclusive filesystem lock on this file. This function protects the file from being copied to another location while the operating system is running. However, a copy of this file is available through Windows shadow volume copy (VSS). VSS provides a shadow copy of this volume – including these sensitive registry hive files. If a VSS copy is available, a non-privileged user may access these files and extract password hashes.
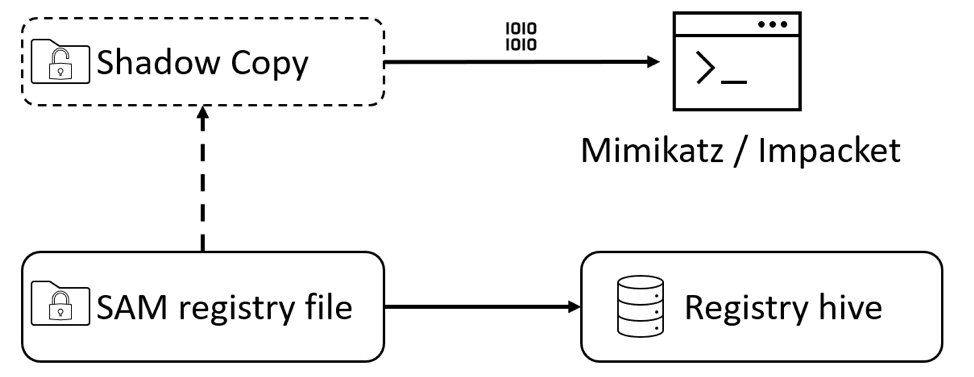
To confirm if VSS is enabled on your system, run the following command line with elevated privileges:
vssadmin list shadows
Machines without VSS will return the output No items found that satisfy the query. VSS is used by System Protection but can also be enabled for backup software and Windows Updates. Future software installations can also enable VSS to ensure a secure operating system in the future.
Proof of concept samples on accessing the SAM database have been provided by Kevin Beaumont and Benjamin Delpy.
Additionally, other registry hives on your machine (SYSTEM and SECURITY) may have misconfigured permissions. These hives may contain potentially sensitive data stored within the registry files, which could include cached Active Directory credentials or stored account passwords in SECURITY hive. This vulnerability could lead to attacks such as Silver Ticket, but may not be as easily weaponized as access to password hashes from the SAM database.
Recommended Actions
This is a critical security vulnerability, and we urge organizations to make sure all endpoints are up to date with the latest security updates applied and installed once the patch is available. Additional recommendations include:
- Ensure your system is up to date: Bitdefender Patch Management can help with quick scanning and management of the needed upgrades to prepare your system against this issue when the patch is available.
- System misconfiguration is a common reason endpoints get breached. Consider implementing an Endpoint Risk Analytics solution to detect, identify and remediate security misconfigurations. If you decide to implement this preventative step, make sure that it also includes permissions in recovery snapshots. Removing Access Control List (ACL) for Users on registry hive files does not automatically remove these permissions from shadow copies. Before taking any additional steps, validate the impact of deleting VSS on other system components.
- Continue to monitor your endpoints for suspicious activity, even after the previous steps have been conducted. Also, make sure your EDR solution can detect attempts to dump content of the SAM database.
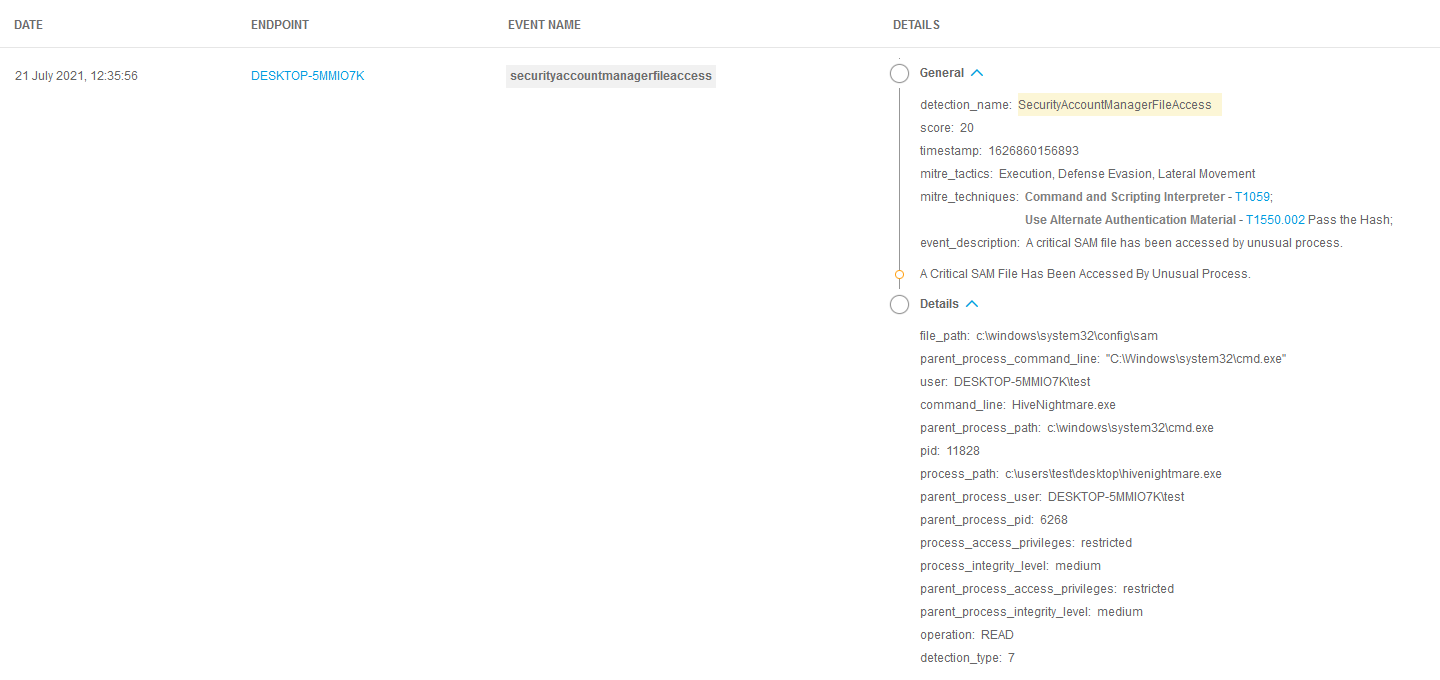
- If you have implemented Bitdefender EDR in your environment, look to see if there was a detection of
SecurityAccountManagerFileAccess– this alert is triggered when the SAM file is accessed by an unusual process.
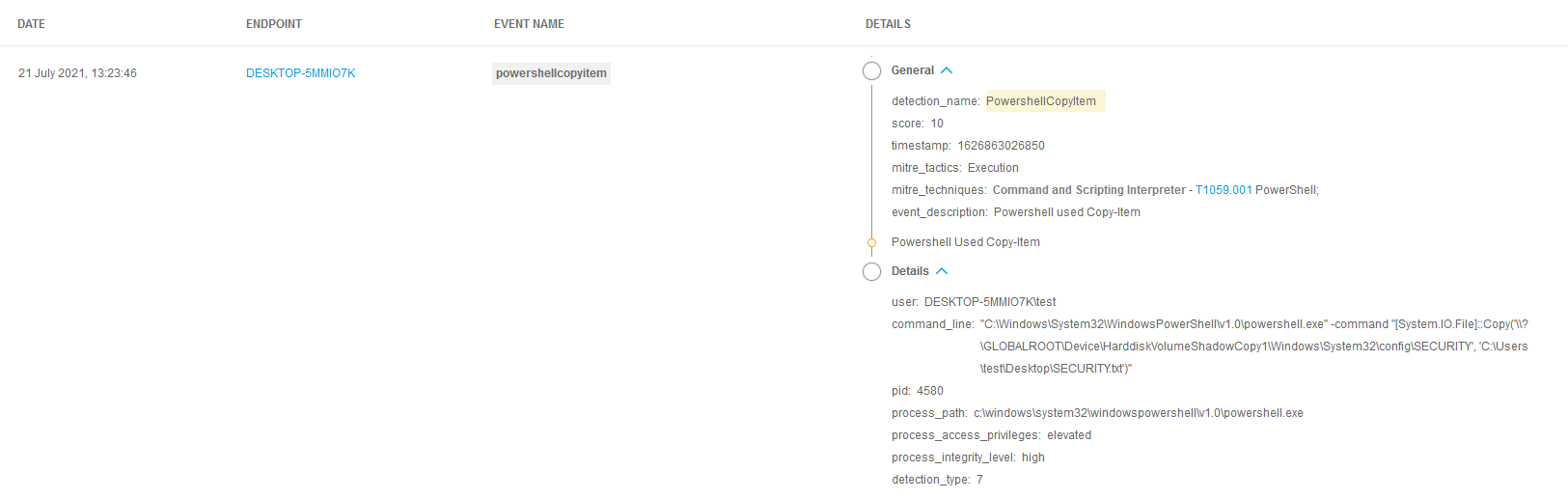
- Another alert is triggered in Bitdefender EDR when registry hive files are retrieved from the shadow volume copy.
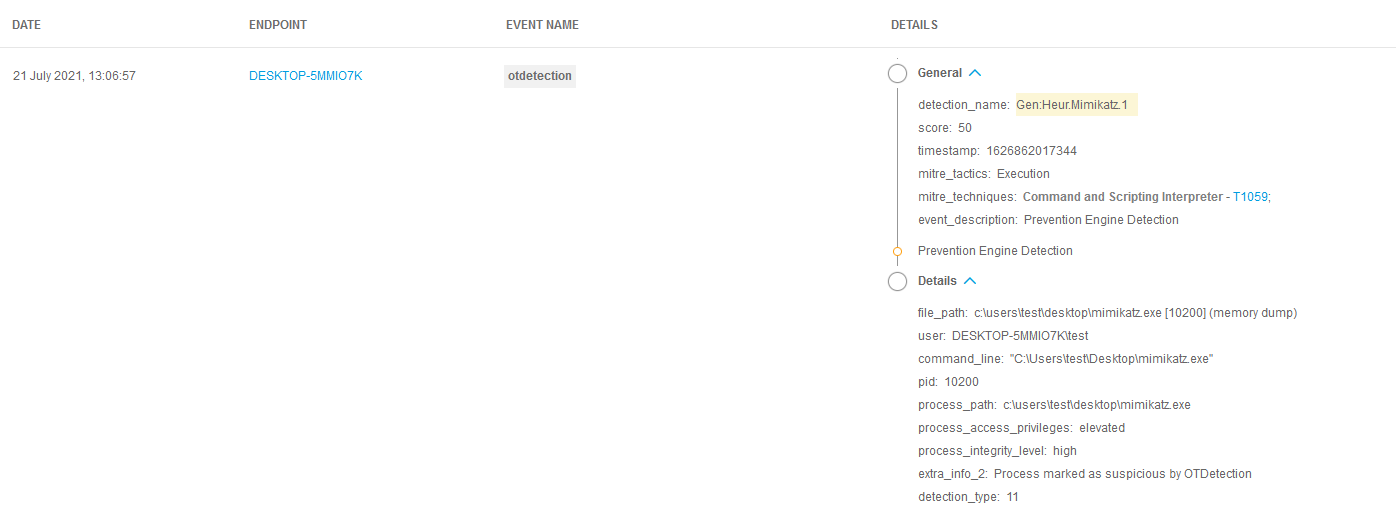
- Finally, while not directly related to this vulnerability, watch for detections in Bitdefender EDR related to tools that provide SAM dumping capabilities (for example Mimikatz using
lsadump::samor in Impacket withsecretsdump.py).
To learn more about how Bitdefender EDR customers are protected from these types of attacks, click here.
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











