Technical Advisory: Why LockBit Ransomware on macOS Is Not a Significant Threat (Yet)

On April 15, 2023, MalwareHunterTeam shared the first proof that one of largest profit-sharing groups, LockBit, is developing a ransomware payload that is targeting macOS users. This was later confirmed by the group representative to BleepingComputer, who said that macOS encryptor is “actively being developed”. In this technical advisory, we evaluated the development stage of the ransomware to determine the level of threat it poses and whether it is fully prepared for actual deployment.
LockBit macOS variant analysis
Two variants have been discovered so far – the first from April 15, 2023, another similar sample was uploaded to VirusTotal on December 8, 2022, but remained unnoticed until April 16, 2023. The first Mach-O sample (Mach-O file format is a file format used by macOS operating system for executable files, object code, shared libraries, and core dumps) was part of an archive (MD5:cc01bae3f189d2d1d0fbb32c6a2d7ce1) that contained builds for multiple Linux architectures, including old ones such as PowerPC.
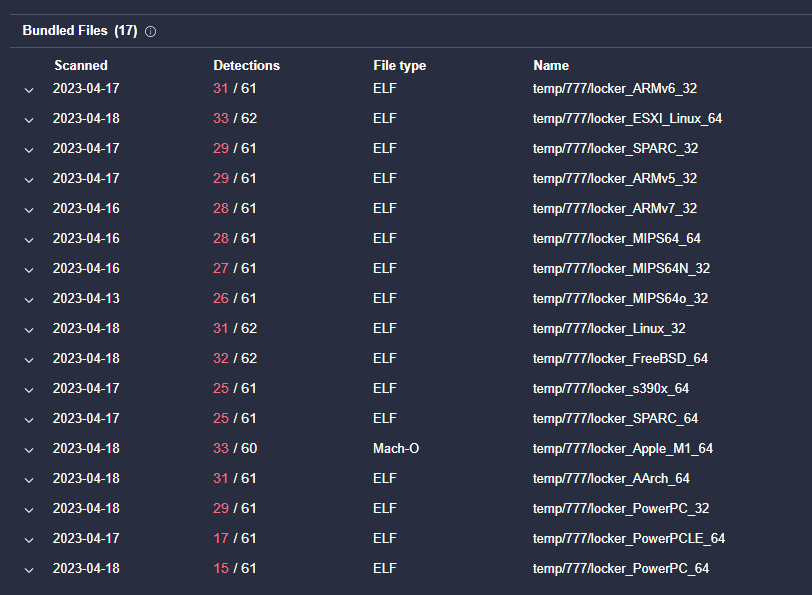
Fig 1: An archive with builds for different Linux architectures, including Apple M1
It is important to note here that both samples are compiled for Apple Silicon (Apple Silicon is the name given to Apple's custom-designed processors that power its Mac computers). This means that the samples available are not working on Intel processors, but they can run on both M1 and M2 chips.
Both files found have the identifier “locker”. The identifier in Mach-O files is one of the components of their digital signature and serves to uniquely identify an application in Apple's ecosystem. In legitimate projects, it typically follows the format of com.<company_name>.<project_name>.
M1 and M2 processors require all native code to have valid signatures, or the operating system will not allow the program to run by default. Samples collected did not have a valid Apple Developer ID, instead, they were using ad-hoc signing certificates. This kind of certificate is used during the development phase of an application. Theoretically, threat actors can bypass or disable the security mechanisms thought social engineering techniques, but by default these samples are not going to be executed. More information on macOS code signing can be found in official documentation.
After decrypting the malware sample, we have been able to extract the list of arguments that is supported:
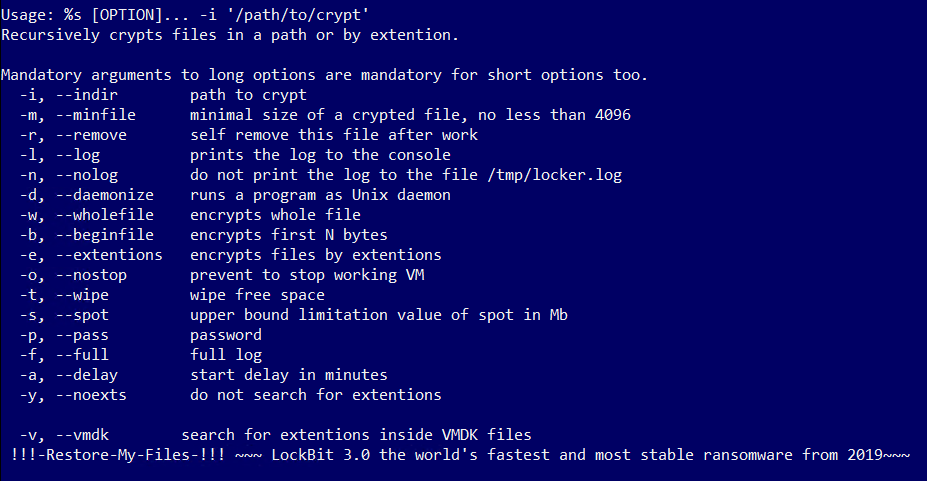
Fig 2: Command line arguments of LockBit malware for macOS
The description reflects that this is based on the LockBit 3.0 version that was first detected in the first half of 2022. We extracted a list of Tor browser links that LockBit ransomware had threatened to use to publish the data that they had stolen. These links are typically hosted on the dark web and are designed to provide a level of anonymity to the operators of the ransomware.
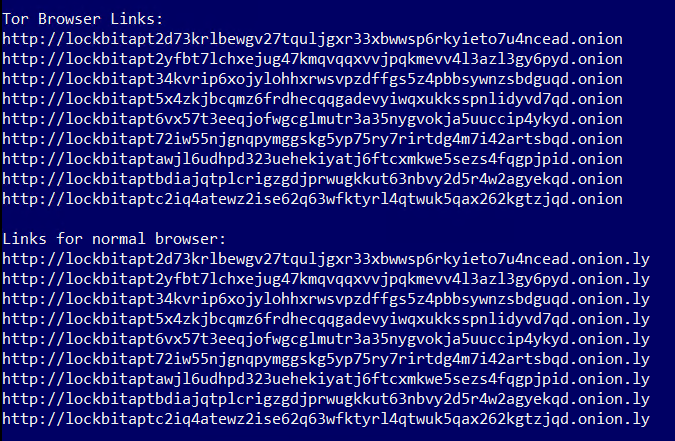
Fig 3: Tor Browser links where stolen data will be published
In addition to the list of Tor browser links used by LockBit to threaten the publication of stolen data, the ransomware note also contains a list of links that could be used to chat with the ransomware representatives. These links are often included in the ransomware note and are designed to facilitate negotiation between the victims and the operators of the ransomware.
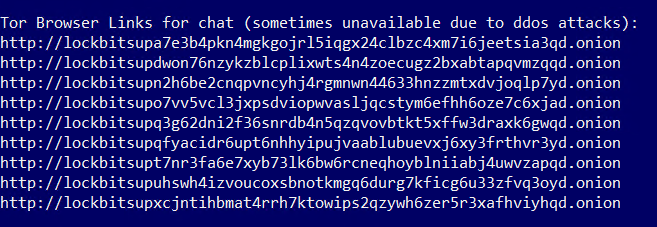
Fig 4: Tor Browser links for contacting LockBit
During our analysis, we came across a set of file names that were associated with the Windows operating system.
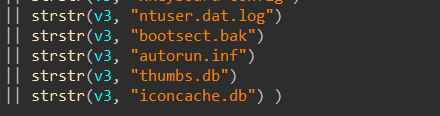
Fig 5: Windows-specific files are referenced throughout the code
This finding strongly suggests that the initial codebase of the malware was developed with Windows in mind. The presence of these file names indicates that the developers may have repurposed existing Windows-specific code for use in the macOS version of the malware. This is a common tactic used by cybercriminals to speed up the development process and reduce the time and resources required to create new malware variants.
In addition to the file names that we identified as being related to Windows operating systems, we also discovered that the malware contained several hardcoded extensions such as ".exe", ".dll", and ".bat". These file extensions are specific to Windows and are not used in macOS. This further confirms our initial finding that the malware was originally developed for the Windows platform and later repurposed for other operating systems.
It is worth noting that while the presence of Windows-specific file extensions in the malware is an indication of its origins, these leftovers do not necessarily have any impact on the ransomware's functionality. The malware can still be configured to encrypt all files in a specific folder, regardless of their extension, as it is not limited to the hardcoded list of extensions. In fact, many ransomware strains do not rely solely on file extensions to identify the files they need to encrypt. Instead, they use more advanced methods such as file signatures or content analysis to identify and encrypt specific file types.
The library used for encryption is called Mbed TLS, an open-source C-language project available on GitHub. This library supports both encryption of entire files, or only partial encryption of the first N bytes of each file. This behavior can be controlled using arguments --wholefile or --beginfile.
The ransomware also includes logging capabilities and collects information about processor, volumes, all system files or running processes. Information related to the encryption process is also collected, such as the total number of encrypted files and virtual machines, or time spent on encryption. Not all functionality is necessarily working on macOS devices, as some of the required commands (such as vim-cmd, lscpu, or esxcfg-scsidevs) are only available on Linux or ESXi hosts.
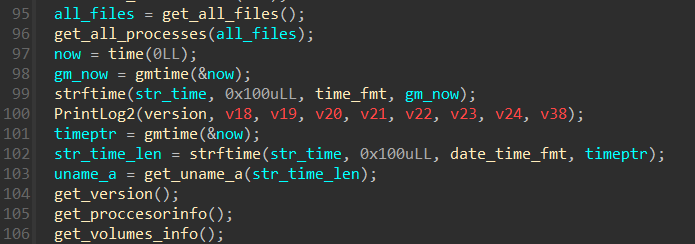
Fig 6: Part of the code for logging capabilities
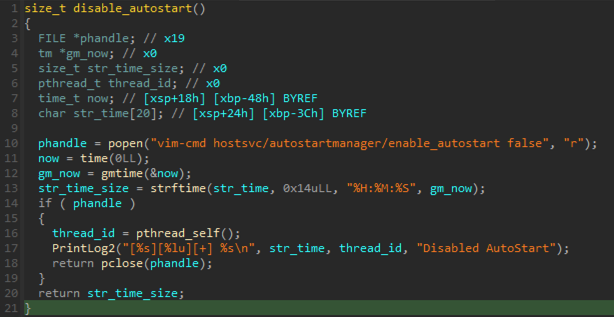
Fig 7: Example of code that is not functional on macOS
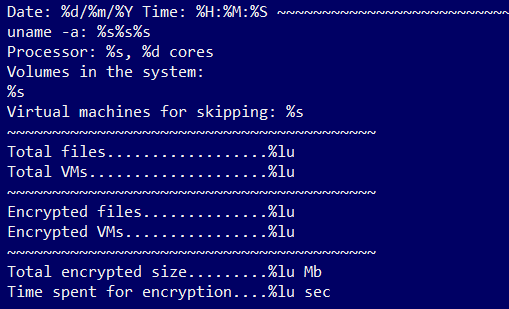
Fig 8: Logging capabilities related to encryption
In general, the LockBit ransomware samples do not have any significant references or indications that suggest they are specifically designed to target the macOS operating system. The only apparent reference to macOS is the existence of a variable named apple_config, which is decrypted at the beginning of the ransomware's execution. Aside from this variable, there are no other functions or symbols in the samples related to macOS.
Upon analysis of the LockBit ransomware code, it was found to be buggy and contain several flaws, such as buffer overflows (you can read more in this excellent write up from Patrick Wardle). These flaws cause the ransomware to prematurely exit or crash, preventing it from encrypting any files on the targeted system. During our testing, the malware terminated immediately, failing to encrypt any files on the disk.
Initially, the LockBit ransomware code was created to target Windows systems and later modified to operate on Linux. Now, the Linux version of the code has been repurposed to function on macOS. The macOS variant is heavily based on the Linux code, leading us to speculate that the adaptation is a prototype to test if the code would compile and function on macOS.
Conclusion
In summary, our assessment indicates that LockBit ransomware designed for macOS is still in its developmental stage and not yet prepared for widespread deployment. However, it is concerning that bigger criminal organizations are considering macOS as a target. Despite common belief, macOS is not immune to malware, and with the increasing popularity of macOS, we have seen a rise in the number of malware attacks targeted at macOS in recent years.
The malware code is an adaptation of the Linux variant of LockBit ransomware that was first detected in Q4 2021. Targeting Linux was an expected move for threat actors as many critical servers (including hypervisors) run on it, and any disruption to its availability (via ransomware) could have grave consequences for businesses. On the other hand, the situation for macOS is not as straightforward, as Mac servers are not as prevalent, and the automation of ransomware deployment is not as accessible as it is on Windows platforms. From a business perspective, macOS is a more attractive target for data exfiltration as it is frequently used by higher-paid positions that handle sensitive information, and its security is often overlooked.
Although the current iteration does not pose a substantial threat, it serves as a reminder to review security measures and protocols for Apple devices on your network.
We would like to thank Andrei Lapusneanu and Alexandru Grosu for help with putting this advisory report together.
Indicators of Compromise
An up-to-date and complete list of indicators of compromise is available to Bitdefender Advanced Threat Intelligence users. The currently known indicators of compromise can be found in the table below.
Files
|
MD5 |
Detection Name |
Description |
|
8facf23309fde7100ea0969238bd6a3e |
Trojan.MAC.Ransom.E Gen:Variant.Ransomware.MAC.LockBit.1 |
Mach-O ARM64 binary executable |
|
abf01633960dd77c6137175a21fccf34 |
Trojan.MAC.Ransom.D Gen:Variant.Ransomware.MAC.LockBit.1 |
Mach-O ARM64 binary executable |
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks









