Understanding the Roles in the Ransomware-as-a-Service Ecosystem: Who’s Targeting Your Data Security Gaps

Ransomware-as-a-service (RaaS) has surged in recent years, becoming a dominant model for deploying ransomware attacks, though many targeted and customized attacks still persist. Active ransomware groups have increased over 50% in the first half of 2024 and they’ve turned ransomware attacks into a lean and streamlined operation, running similarly to a small business, with salaries, performance reviews, and even recruitment referrals utilized to optimize operations.
Unfortunately, these developments make things harder for organizations who were already struggling to defend against ransomware attacks. However, by knowing how these groups tick and understanding what their organizational makeup is, security leaders can more effectively build cyber resilient strategies that help against these kinds of attacks. In this piece we intend to offer a deeper look into the organizational makeup of RaaS groups and help you defend more effectively against them.
The Anatomy of a RaaS Group
Ransomware criminal organizations are now working like streamlined software companies and service providers, with several key roles facilitating this efficient operation:
- Operators: These are more like entrepreneurs of an RaaS operation, overseeing deployment, management, supporting the financial infrastructure pre- and post-compromise, and ensuring the operation is updated and optimized for continued attacks.
- Affiliates: Affiliates are essentially professional hackers, operating as independent contractors. They get their hands dirty by leveraging access to deploy ransomware, navigating the network of a compromised organization, and ensuring the ransomware is deployed effectively. Affiliates can work with multiple operators and switch allegiances as needed..
- Initial Access Brokers: These are the penetration experts who initially identify a vulnerability within an organization, exploit that vulnerability, and set up access for an affiliate to close in.
- Developers: Developers build and maintain the software and technical infrastructure that support the exploitation of vulnerabilities, the compromise of organizations, and the deployment of ransomware. While some developers focus on malicious code, such as encryptors or EDR bypass tooling, others work on more conventional development tasks like building web portals or back-end systems to support the overall operation. It's also common for developers to work for multiple groups or sell their code to other ransomware operators, further fueling the cybercriminal ecosystem.
Beyond the core roles, the RaaS ecosystem includes a variety of other professionals who contribute to its success. These can range from negotiators, who step in post-compromise to maximize ransom payouts and escalate threats, to specialists in fields like data analytics, communications, or even public relations to manage the group's interactions (just take note of the Medusa ransomware’s online presence). This open ecosystem allows for a range of expertise to be applied in the service of the operation.
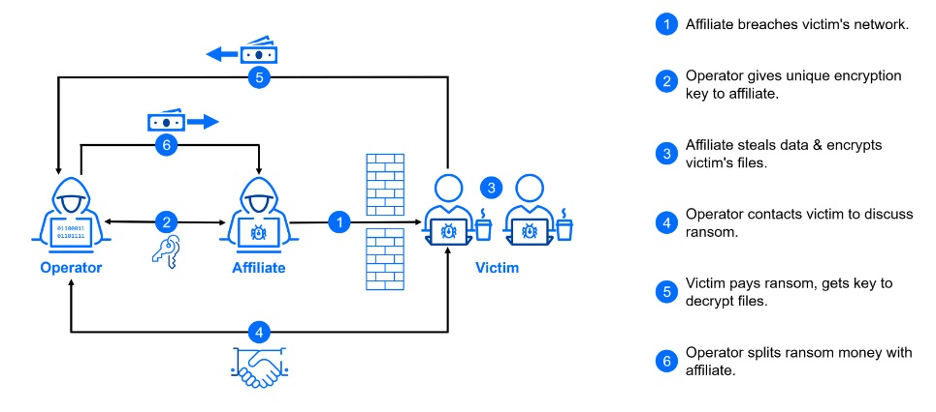
Typically ransomware profit sharing model.
Once a ransomware attack is successful, the majority of the payout typically goes to the affiliates, who are the key players in this ecosystem. The remaining profits are shared among other groups based on their contributions. In many cases, ransomware groups collaborate, but many threat actors work as freelancers, offering their specialized skills to multiple groups.
How RaaS Roles Are Evolving
As these RaaS groups evolve, we’re seeing initial access brokers and developers becoming more important and having an increasing influence in how these groups function. Initial access brokers typically don't wait to be hired. Instead, they proactively obtain access to multiple companies and environments, building a portfolio of compromised systems that they can offer to potential buyers.
On the other hand, developers can also serve as the owner and head of small RaaS groups and hire other developers who can write peripheral tooling and infrastructure to support attacks. This includes endpoint detection and response (EDR) bypass solutions or backdoor access solutions or infrastructure that may not even look like it's facilitating black hat hacking. This allows developers to hire other engineers that may not even know they’re working for a criminal hacker group or have enough doubt to take the job.
As these groups become more sophisticated, they can continue to refine their recruitment practices. Currently, they’re largely done via forums, recommendations, and closed systems but this may result in unproven hires. With more time, they’ll be able to hire actors who have already done the job and have a resume to back their skills up.
While RaaS groups are becoming more efficient and streamlined, there’s room for improvement, meaning organizations need to be ready.
What’s Being Targeting and Who’s at Risk?
In the past, ransomware groups targeted specific industries based on known vulnerabilities and common risk exposure across an industry’s organizations. However, this pivot to RaaS has shifted how organizations are being targeted. Rather than aiming at key industries, these groups are starting with vulnerabilities and searching for organizations who are using systems or devices with known vulnerabilities and targeting those who are unlikely to have patched the vulnerable devices. The most common targets here are edge network devices such as application firewalls, VPN devices, routers, and more.
These groups are leveraging automated scanning tools, looking for device usage and triaging from there. This is a big shift as vulnerable organizations are discovered much sooner and groups already know the way they’ll gain access and compromise an organization. This is because these threat actors are moving much more quickly to exploit known vulnerabilities. In the past, once a vulnerability was discovered and the proof of concept was published, threat actors were able to professionally weaponize them in about a month’s time.
These days, it takes about 24 hrs.
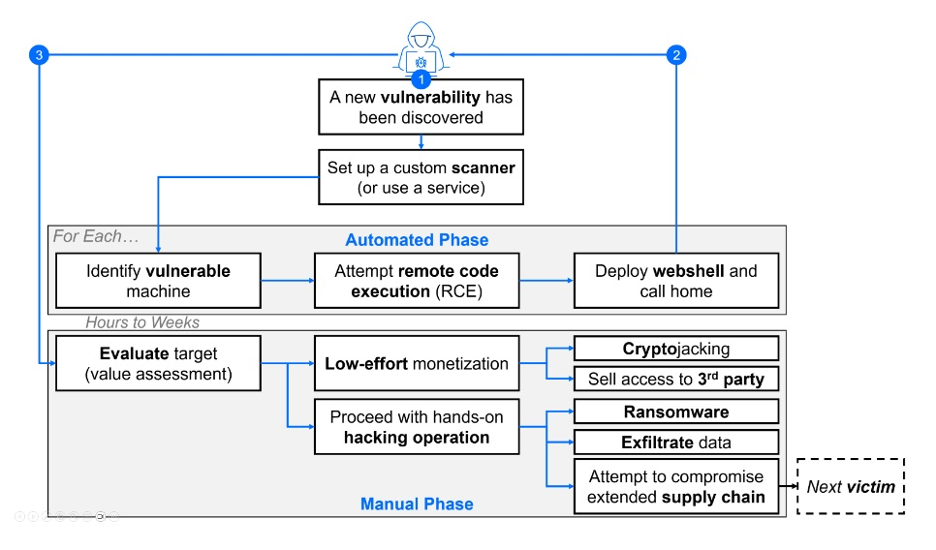
Example of ransomware attack stages.
This means any organization that can be affected by the vulnerability is at risk. Ransomware groups know this, which is why they’re starting with vulnerabilities and indiscriminately targeting susceptible organizations.
Strengthening Defenses Against RaaS
Any risk mitigation or defensive strategies need to start with awareness. There’s a lot of noise in cybersecurity and trends are moving faster than ever, making it difficult to know what information you need to act on. If organizations still think of ransomware as simply an encryption attack or that email is the most common vector, then they’re blind to what’s actually happening with these new ransomwares as a service groups.
Understanding that these groups are much more sophisticated, leveraging known vulnerabilities, and engaging in extortion attacks will help you develop more effective strategies. In the long-term, you should invest in cyber threat intelligence to know how these threat actors are targeting organizations and how their methods are shifting.
Against these current RaaS groups, vulnerability management and patch management is necessary given that edge network devices and their vulnerabilities are becoming the main entry point for these attackers. If you’re taking a “patch everything all the time” approach, then you’re likely to leave yourself at risk for critical vulnerabilities due to the speed at which these attackers are moving. It’s important to have a process for critical vulnerability management and prioritize your patching.
This starts with establishing your feeds of communication to be aware of vulnerabilities as soon as they’re published. CVEdetails.com is a good resource to start with (make sure you’re looking at CVSS scores for criticality) and CISA’s list of known and exploited vulnerabilities should also be a continuous feed. The vulnerabilities found here are must-patch vulnerabilities that ensure you’re not swept up in a ransomware group’s automated scanning and initial access brokerr’s viewpoint.
With these preventative measures in place, you can now invest in threat hunting, which allows you to discover a potential threat after they’re in your system. Fortunately, there is some time between an initial compromise and a complete compromise that allows an affiliate to deploy ransomware in an organization’s environment. Leveraging solutions like XDR, EDR, and MDR tools are necessary here, but it’s important to ensure that you’re solving for comprehension and visibility with your vendor. Even small gaps in visibility or detection capabilities are enough for a hacker to move laterally and evade detection.
Ultimately, an effective security leader must ensure their strategy is optimized for the ever-evolving threat landscape. Preparing for this new wave of ransomware attacks requires a shift in mindset, moving beyond traditional notions of ransomware and leveraging advanced tools and processes to combat these rising risks.
To gain a deeper understanding of how ransomware operators exploit organizational weaknesses, download our comprehensive white paper on ransomware defense. This in-depth resource offers actionable insights for identifying and addressing security gaps targeted by cybercriminals.
For additional context on the ransomware economy, our eBook, The Gig Economy Behind Ransomware, breaks down how ransomware groups operate and profit. Access both resources to strengthen your defenses and stay informed about the threats posed by RaaS actors.
tags
Author

Josue Ledesma is a writer, filmmaker, and content marketer living in New York City. He covers cyber security, tech and finance, consumer privacy, and B2B digital marketing.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks












