World Economic Forum Outlines Core Principles for Businesses Seeking to Reduce Cyber Risk

An optimistic new report by the World Economic Forum predicts businesses will prioritize security in a bid to ensure longer-term success. The reason? A rapid increase in cyberattacks and pressures escalating from changes prompted by COVID-19.
A copy of the report, obtained early by Help Net Security, outlines a major imbalance between “time to market” pressures and “time to security” requirements for new products and services. According to Algirde Pipikaite, the Cybersecurity Lead of the World Economic Forum, companies are feeling the pressure to win over consumers from a security standpoint.
“With the rapid increase of cyberattacks, companies need to prove to consumers the security of their data,” Pipikaite said. “As the market shifts due to the rapid technology adoption in all spheres of our lives, we expect to see more investment in companies prioritizing security and their longer-term success.”
The report lists several core cybersecurity principles, pointing to how companies and investors can significantly reduce cyber risk to remain competitive. These principles are broken down by category.
Organizational principles include a robust cybersecurity culture, cybersecurity governance and cyber resilience. On the Product side, WEF lists privacy & security by design as core principles to win customers’ trust. And to stay competitive in the long run, WEF recommends investing in Infrastructure areas like third-party security and data governance.
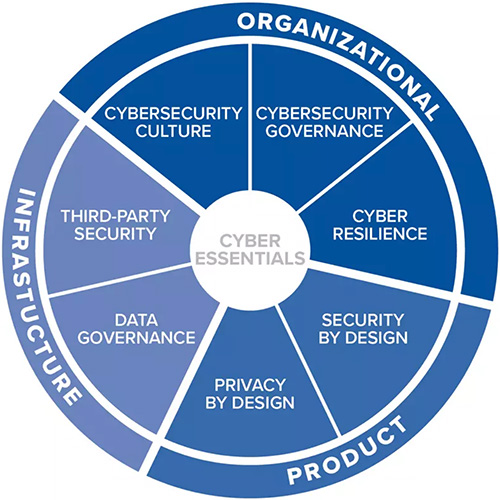
Timely implemented, these principles promise “a robust cybersecurity framework encompassing organizational, product and infrastructure security,” WEF analysts say.
“We see two types of early-stage companies: the ones that treat cybersecurity as a checkbox compliance issue, and the ones that understand that it is fundamental to maintain the trust of clients,” according to Craig Froelich, CISO at Bank of America, who is quoted in the report. “If an emerging company fully commits to cybersecurity, then its commitment will be rewarded by market confidence and consumer trust.”
WEF researchers say these “cyber essentials” must be custom-fit to each organization based on size, nature and type of product, outlining some practical steps for their implementation and validation.
tags
Author
.jpg)
Filip is an experienced writer with over a decade of practice in the technology realm. He has covered a wide range of topics in such industries as gaming, software, hardware and cyber-security, and has worked in various B2B and B2C marketing roles. Filip currently serves as Information Security Analyst with Bitdefender.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










