Tech Support Scams Threaten People with Fake Invoices for Services They Haven't Contracted; Here’s How to Stay Safe

Tech support scams are becoming more common, and it seems they are here to stay. Scaring people with huge invoices for recurrent payments hasn't quite seeped into the public consciousness, which means that users are not accustomed to viewing fake invoices with enough skepticism.
Email is the main vector for the most common attacks, such as phishing, scams, and malware. While many of them can be easily intercepted by security solutions, some more advanced schemes are not evident from the get-go; they might not include dangerous links or problematic attachments.
From fake invoices to fraudulent subscription notices, email scams are becoming increasingly sophisticated. Such scams can be difficult to identify, leading to financial loss or the compromise of personal information.
What Are Tech Support Scams?
Run-of-the-mill email scams can be defined as deceptive messages cybercriminals send to trick people into providing sensitive information, such as credit card numbers, account credentials, or personal data.
Tech email scamming, meanwhile, refers to fraudulent emails designed to deceive recipients by impersonating legitimate technology or service providers. The distinction is that these emails don't always try to scam the user from the start. They arrive in the form of fake invoices, subscription renewals, or payment confirmations, with attachments to prove it.
The goal is to persuade people to interact further with the attacker, not just to open a malicious link. The emails usually include attachments, like fake invoices in PDF format or image files. The messages appear legitimate, mimicking well-known companies, payment systems, or services, not to mention that they're brandishing known logos
Email scams can lead to identity theft, financial fraud, or the installation of malware on your device. The stakes are high, and the scammers's tactics use are constantly evolving.
Common Tactics Used in Email Scams
Scammers employ psychological tricks, also known as social engineering, to manipulate people into acting before they think. One of the most common methods is using unfamiliar or suspicious email addresses that could appear legitimate at first glance, but a closer look reveals they're unrelated to any recognized company.
Also, a common tactic is to create a sense of urgency. Emails often state things like: "You have 24 hours to cancel this transaction" or "Your account will be disabled if no action is taken." These scare tactics pressure recipients into clicking on a link or responding without determining whether the email is authentic or not.
Another tactic is sending fake payment confirmations. Emails with phrases like "Thank you for your payment of $745.44" are designed to make recipients panic. Seeing hundreds of dollars on a single transaction could prompt people to respond quickly, believing a mistake has been made somewhere along the line. The scammers rely on the surprise of an unexpected payment to push recipients to click on a link or open an attachment.
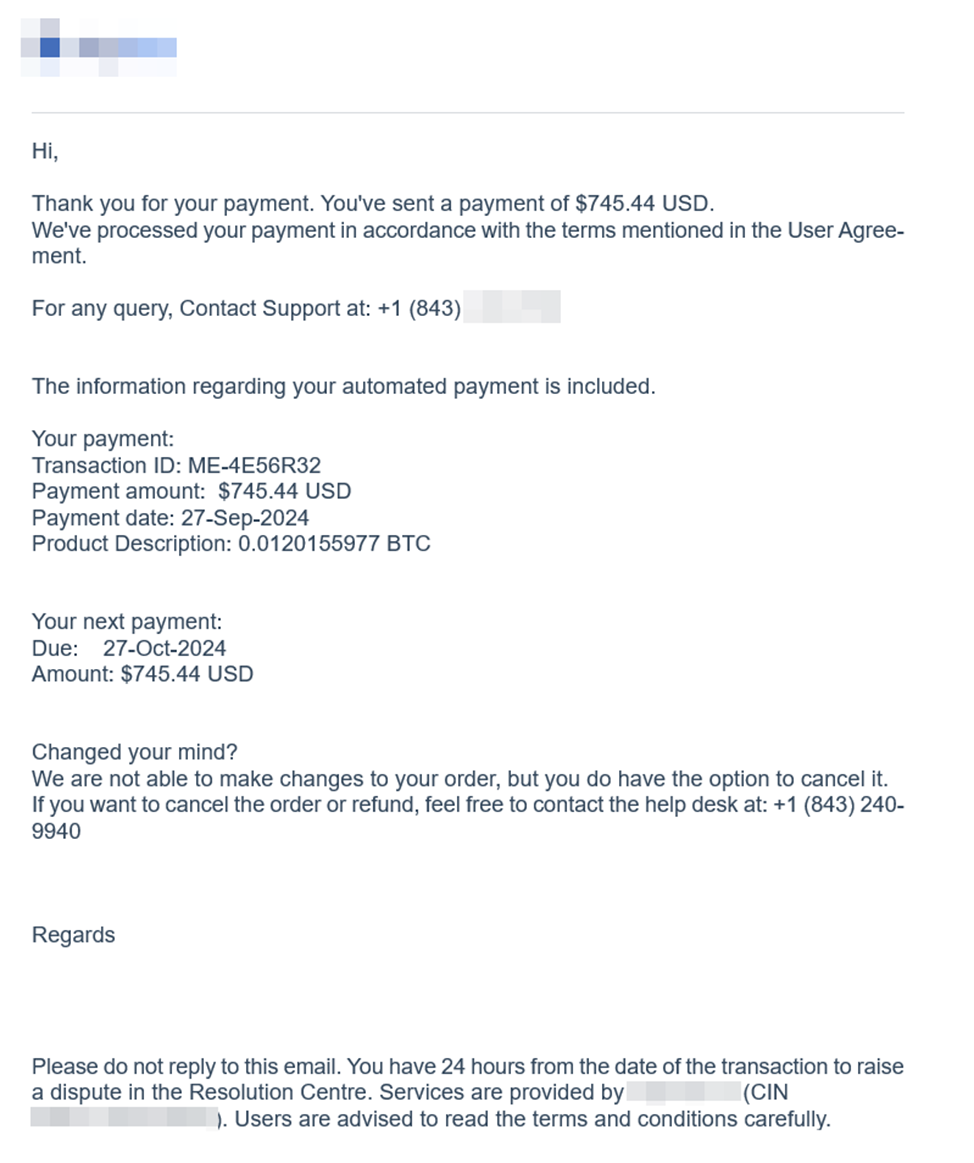
In this case, the target is informed of a substantial payment that's already been made, but we can also see that the Product Description has a strange number (0.0120155977 BTC). That's the same amount of dollars, but in Bitcoin. Likely, the attacker's hope is that it will also catch some crypto-enthusiasts as well.
Mismatched email addresses are another red flag. In many cases, the email's display name may claim to be from a reputable company, but the actual email address tells a different story. Double-checking the sender's emails a handy tactic that can be applied everywhere, not just in the case of these frauds.
Understanding Email Scam Attachments
Scammers often include attachments as part of their email fraud scheme, usually disguised as legitimate documents such as invoices, receipts, or subscription summaries.
Scammers sending attachments as supposed receipts or payment confirmations is becoming more commonplace. While these files might not be dangerous from a malware point of view, they often serve to convince the potential victim that the email is genuine, encouraging further interaction with the scam.
Another common tactic is the use of fake subscription confirmations. For instance, the attachment shown below is designed to look like a legitimate invoice from a well-known company. Recipients are tricked into believing they've been charged for a service they didn't order. The scam email urges them to contact a fake support line, where they might be asked to provide personal or financial information.
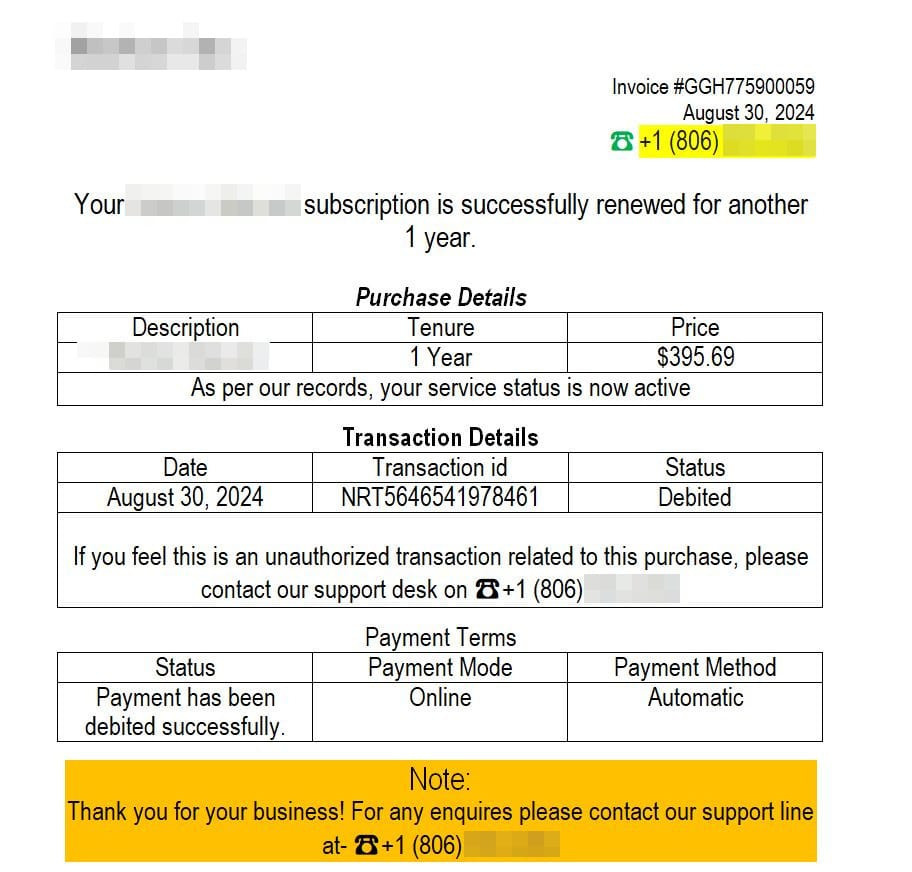
Even when attachments appear as simple image files, they can still contain dangerous scripts that install malware without your knowledge. Once malware is installed, scammers can steal your personal information, track your activity, or lock you out of your device.
How to Identify a Scam Email
Identifying a scam email can be tricky, but there are several red flags to look out for:
- Check the Sender's Email Address: Scam emails often come from addresses that don't match the sender's claimed identity. Domain names may look legitimate but don't belong to any recognized companies.
- Look for Poor Grammar and Formatting: Reputable companies maintain high communication standards. It may be a scam if the email contains grammatical errors, awkward phrasing, or strange formatting.
- Hover Over Links: Before clicking a link in an email, hover your mouse over it to see the actual URL. If the URL looks suspicious or doesn't match the official website of the supposed company, don't click it.
- Be Wary of Attachments: Unexpected attachments, especially those labeled as invoices or receipts, are common in scam emails.
- Too-Good-to-Be-True Offers: Emails offering you unexpected winnings, refunds, or other financial gains are generally scams. Legitimate companies rarely contact customers about such offers via email.
- Use Scamio, our free online scam checker tool. If you suspect someone is trying to scam you, check with Scamio, our AI-powered scam detection tool. Send any texts, messages, links, QR codes, or images to Scamio, which will analyze them to determine if they are part of a scam. Scamio is free and available on Facebook Messenger, WhatsApp, and your web browser.
Security Measures to Protect Yourself
To protect yourself from email scams, it's essential to implement good security habits:
- Enable Two-Factor Authentication (2FA): Two-factor authentication provides an additional layer of security for your email account. Even if hackers get access to your password, they'll be blocked from accessing your account without a second verification step.
- Install capable security solutions such as Bitdefender Ultimate Security: A reliable security solution helps you scan email attachments for malicious content and offers real-time protection by blocking harmful URLs, among many other features.
- Stay Informed: Knowledge is your best defense. Keep up to date with the latest phishing techniques and scam tactics to avoid falling victim to new tricks. Fake tech scam invoices are a good example of a new type of scam people need to be aware of.
- Be Skeptical of Unexpected Emails: Always verify emails that request immediate action, even if they appear to come from a legitimate source. Contact the company directly through their official website to confirm the email's authenticity.
Frequently Asked Questions (FAQs):
What should I do if I accidentally open a scam email attachment?
You should be fine if you don't give the attackers personal information. In many cases, the attachments in tech email scams are just regular PDFs or images. The security solution will prevent the installation of malware, but you should change your passwords if you unwittingly gave them to attackers through other channels.
Can scam emails steal my information just by opening them?
Opening an email alone usually won't result in information theft. The danger comes when you interact with links or attachments in the email. Always verify the legitimacy of the email before engaging with its contents.
How can I report a scam email?
Most email platforms have built-in features for reporting phishing or spam. User reports are extremely important.
How can I tell if an email is from a legitimate company?
Verify the sender's email address, check for proper grammar and formatting, and look for inconsistencies between the email content and the company's typical communication style. When in doubt, contact the company directly using their official website.
Is it safe to open an email from an unknown sender?
It's generally safe to open an email from an unknown sender, especially if you rock a Bitdefender security solution, but you should always be cautious about clicking links or opening attachments. If the email seems suspicious, don't engage with it further and report it as phishing.
Conclusion
Tech support email scams are a significant threat, mostly because they are still fairly new and people don't always recognize the danger. You can protect yourself from falling victim by staying vigilant and adopting proactive security measures. Whether it's scrutinizing the sender's email address, hovering over suspicious links, or avoiding unexpected attachments, every step you take reduces the risk of being scammed.
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsYou might also like
Bookmarks
