AI meets next-gen info stealers in social media malvertising campaigns

The impact that AI has on society has steadily crept into the darkest nooks and crannies of the internet. So much so that cybercrooks are hitching free rides on the AI bandwagon by leveraging the increased demand of AI-powered software for content creators.
Cybercriminal groups constantly adapt their operating methods and tools to stay a step ahead of potential victims. Highly focused on enhancing their deceptive practices, threat actors have, unfortunately, found a most reliable and powerful ally in artificial intelligence.
Bitdefender researchers are keeping a close eye on these deceptive efforts and exploits regarding the rising popularity of generative artificial intelligence software to keep consumers aware and help protect their devices, data and money.
Over the past year, Bitdefender Labs has seen a motley crew of AI-powered illicit operations conducted by threat actors over social media, from stream-jacking attacks that delivered crypto-doubling schemes on YouTube to audio deep fakes that overflow on Meta’s social platforms.
This paper focuses on nefarious activities that take advantage of the demand and supply of some of the most popular generative AI software to attack users from across the globe.
Key findings:
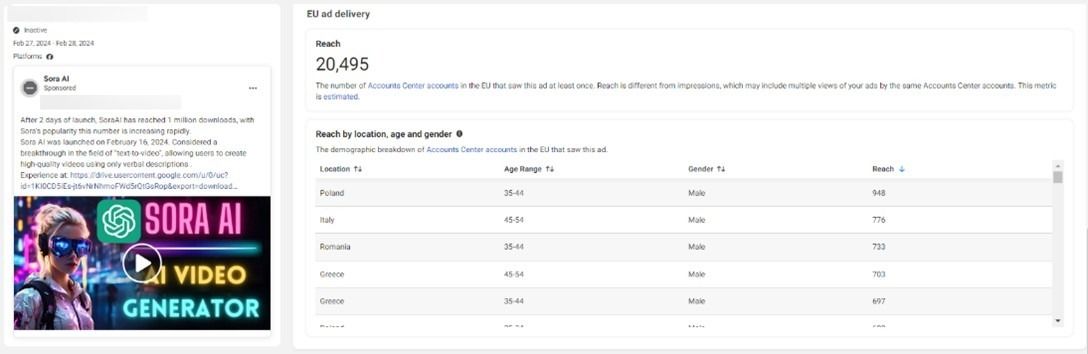
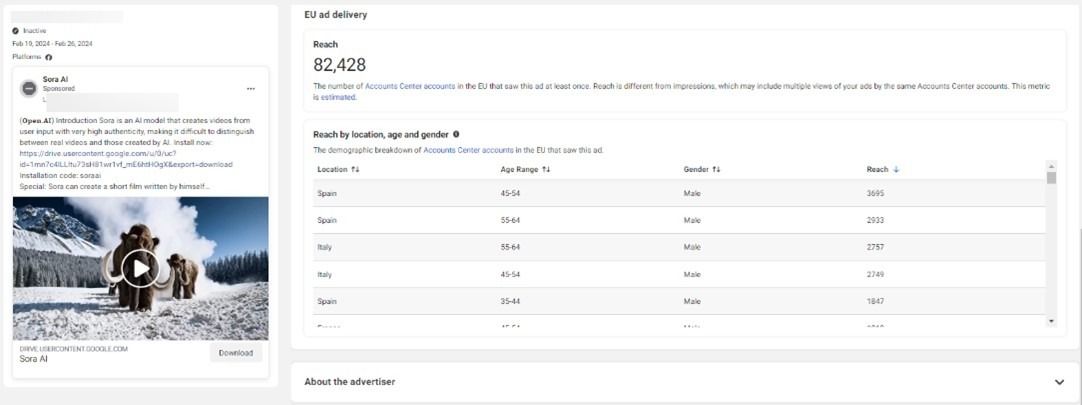
- Cybercrooks have taken over Facebook profiles to run sponsored malvertising campaigns impersonating Midjourney, Sora AI, DALL-E 3, Evoto, ChatGPT 5 and many others
- The malicious pages on Facebook are meticulously designed to trick users into downloading purportedly official desktop versions of popular AI software. The cybercriminals behind these campaigns regularly change and adapt the malicious payloads in an attempt to avoid further detection from security software
- The links direct users to malicious webpages that download a variety of intrusive stealers to harvest sensitive information from compromised systems, including credentials, autocomplete data, credit card information, and even crypto wallet information.
- The analyzed campaigns employ malicious ads that contain links to executable files that serve Rilide, Vidar, IceRAT, Nova Stealers. The entire batch of malicious software is often offered as malware-as-a-service by threat actors on specialized forums and channels.
- The malvertising campaigns have tremendous reach through Meta’s sponsored ad system and have actively been targeting European users from Germany, Poland, Italy, France, Belgium, Spain, the Netherlands, Romania, Sweden, and elsewhere.
- The ads use convincing descriptions alongside generated AI videos and photos to lure potential users into accessing malicious payloads
- One particular Facebook page impersonating Midjourney with a whopping 1.2 million followers was active for nearly a year until it was shut down on March 8, 2024. Since then threat actors have continuously set up more fraudulent pages to deliver malicious ads to users.
- The Midjourney malvertising ad campaign was directed towards male Facebook users aged 25 to 55 and had an ad reach of approximately 500,000 individuals from Europe (demographics and reach of the campaign were obtained by tracking Meta’s Ad Library catalog)
Organizing the attacks
Threat actors are actively spreading malware through Meta’s sponsored ad system.
The malicious campaigns begin with cybercriminals taking over an existing Facebook account. Once compromised, the crooks begin to change descriptions and cover and profile photos, making the page seem as if it is run by well-known AI-based image and video generators.
The cybercriminals then begin boosting the legitimacy of the page with news, AI-generated photos and advertisements that contain descriptions of enhancements of the impersonated AI service and links that give users free access or trials for the tool.
The point of the malicious campaign is to trick individuals into accessing a malicious link and downloading malware onto devices.
Although many of the malicious ads inspected by Bitdefender researchers urged individuals to download the purported new version of the AI tool from Dropbox and Google Drive links – which is undoubtedly a huge red flag – the campaign impersonating Midjourney used a different approach.
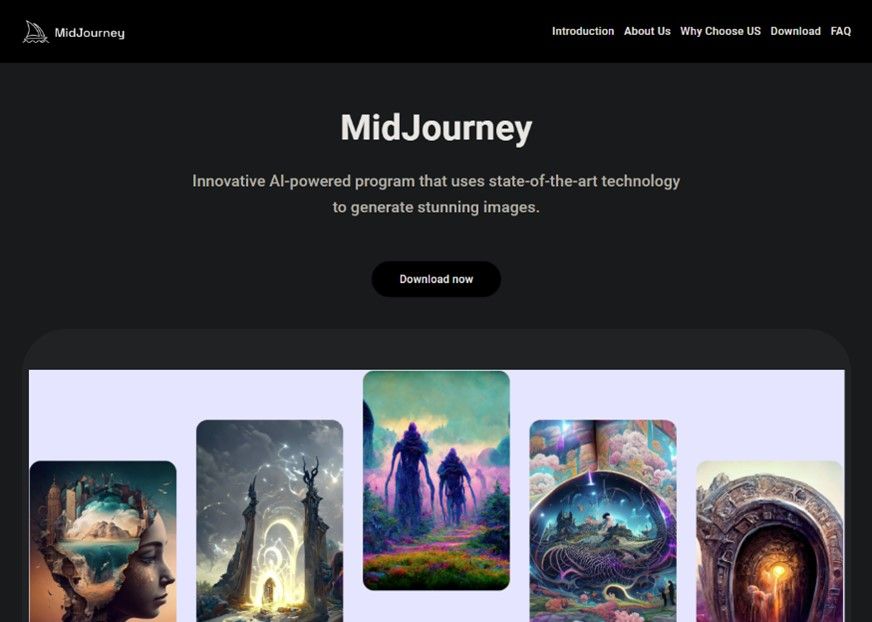
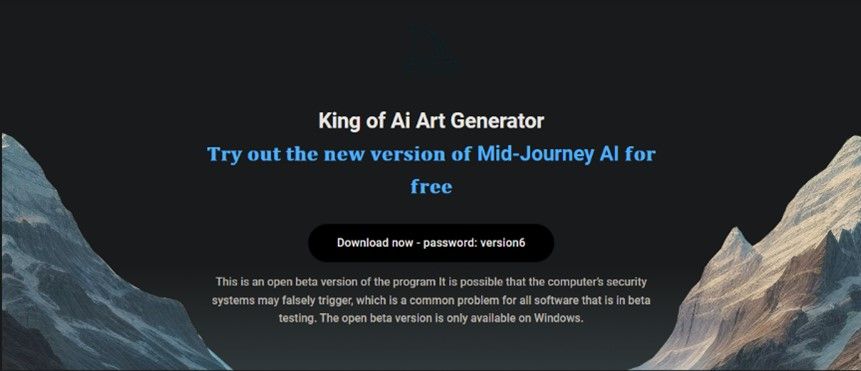
Cybercriminals created over a dozen malicious websites mimicking the official Midjourney landing page to lure users into downloading the latest version of the service via a GoFile link.
Threat actors serve a four-course menu of info stealers
Cybercriminals have created a highly engaging distribution system for malicious software through the Malware-as-a-service (MaaS) business model that enables any malicious individual to conduct sophisticated and cost-efficient attacks and other nefarious activities.
This includes stealing sensitive information, compromising online accounts, committing fraud, disrupting operations, or demanding ransom after encrypting data on a compromised system.
The malvertising campaigns analyzed by our researchers have been distributing an assortment of malicious software that poses severe risks to consumers’ devices, data and identity. Users who’ve interacted with the malware-serving ads could have unknowingly downloaded and deployed harmful files onto their devices: Rilide Stealer, Vidar Stealer, IceRAT (written in JPHP) and Nova Stealer.
Rilide Stealer V4
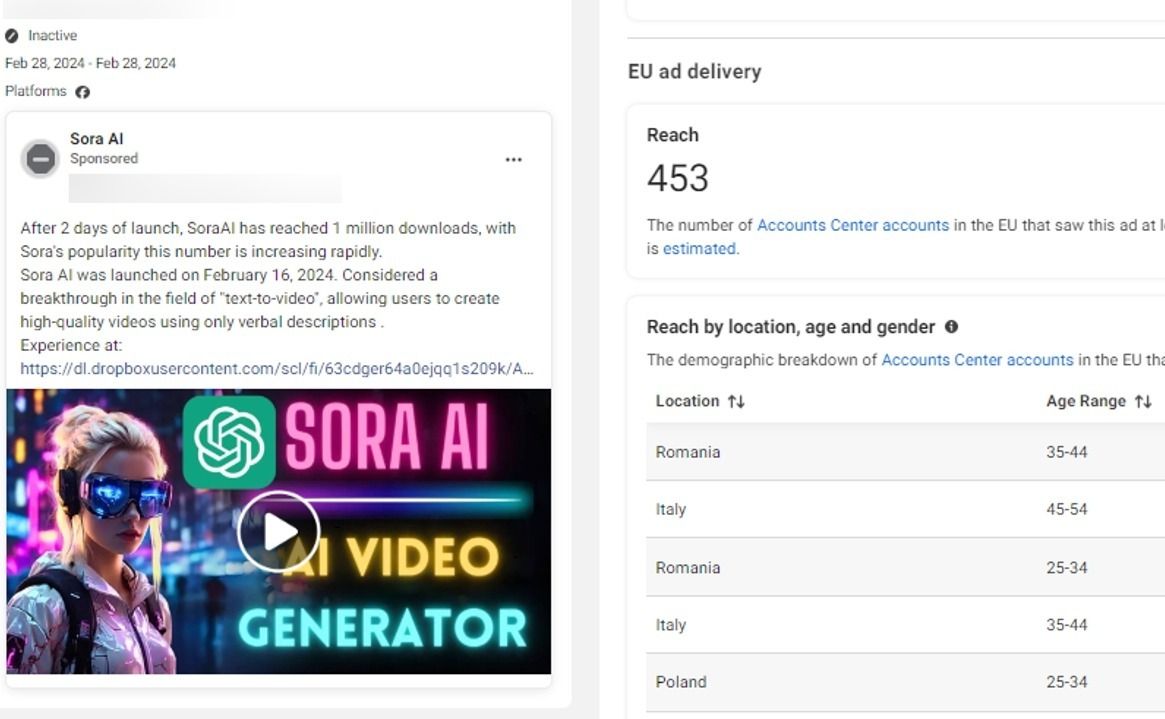
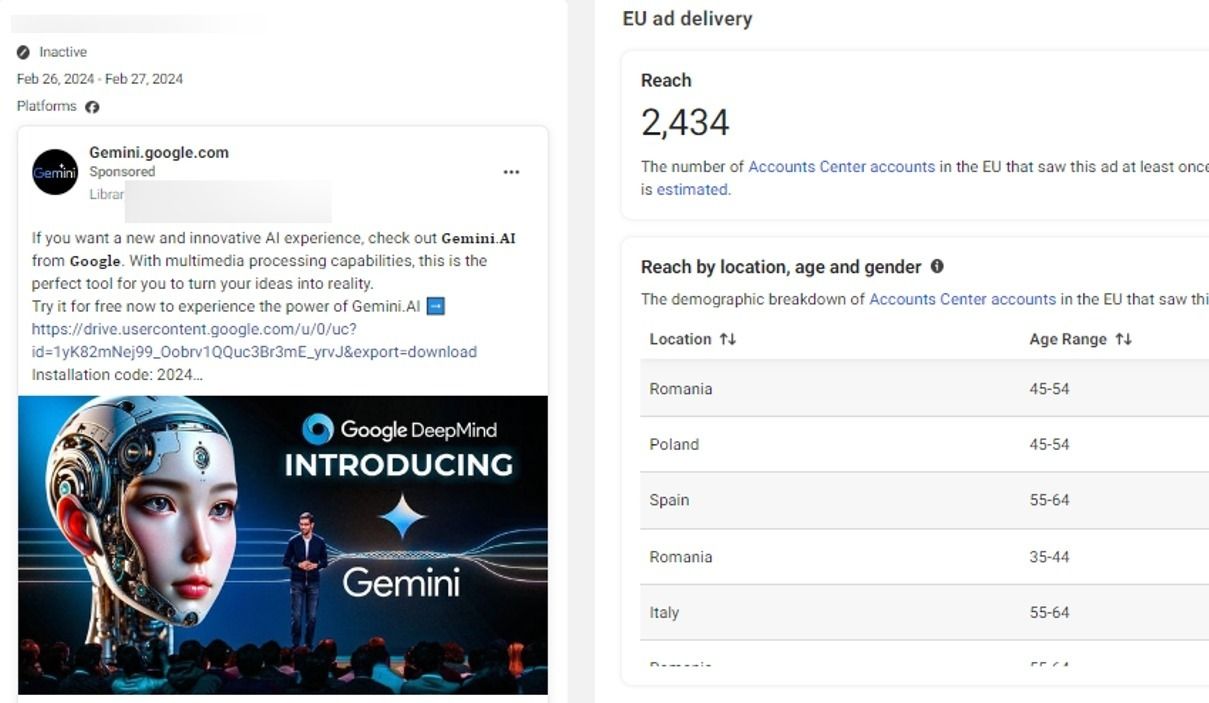
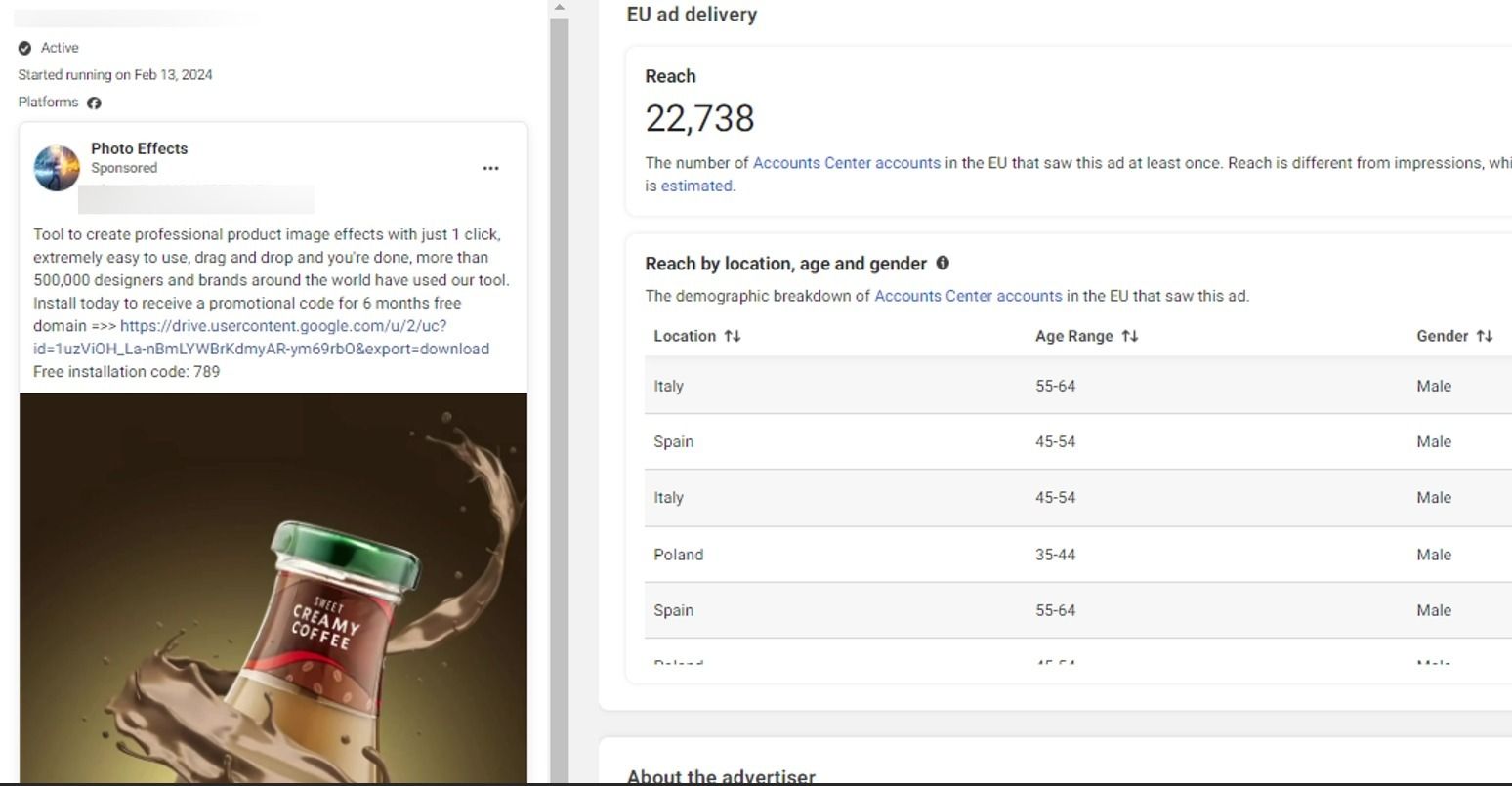
Researchers at Bitdefender Labs have spotted an updated version of the Rilide Stealer (V4) in various sponsored ad campaigns impersonating AI-based software or photo editors including Sora, CapCut, Gemini AI, Photo Effects Pro and CapCut Pro.
The malware known as Rilide is a malicious extension that targets Chromium-based browsers, including Google Chrome, Opera, Brave and Microsoft Edge, and enables threat actors to monitor browsing history, capture login credentials, and even withdraw crypto funds by bypassing 2FA through script injections.
What’s new for Rilide V4:
- The malicious extension mainly targets Facebook cookies
- It masquerades as a Google Translate Extension
- The threat actor uses better obfuscation techniques to hide the true intent of the software. The so-called app installer for the AI software immediately opens the official webpage of the impersonated AI image generator to fool users. At the same time, it begins loading the malicious extension onto the victim’s browsers.
Indicators of compromise
Malicious hashes
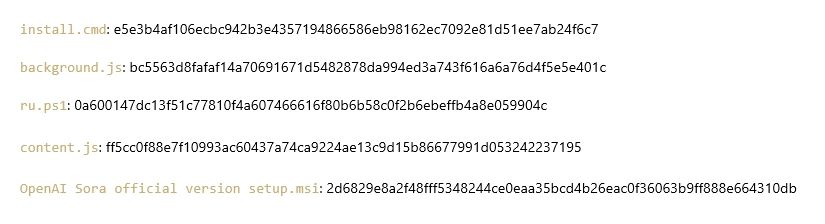
- 2d6829e8a2f48fff5348244ce0eaa35bcd4b26eac0f36063b9ff888e664310db - OpenAI Sora official version setup.msi - Sora
- a7c07d2c8893c30d766f383be0dd78bc6a5fd578efaea4afc3229cd0610ab0cf - OpenAI Sora Setup.zip - Sora
- e394f4192c2a3e01e6c1165ed1a483603b411fd12d417bfb0dc72bd6e18e9e9d - Setup.msi - Sora
- 021657f82c94511e97771739e550d63600c4d76cef79a686aa44cdca668814e0 - Setup.msi - Sora
- 92751fd15f4d0b495e2b83d14461d22d6b74beaf51d73d9ae2b86e2232894d7b - Setup.msi – Sora
- 32a097b510ae830626209206c815bbbed1c36c0d2df7a9d8252909c604a9c1f1 - Setup.msi - Sora
- c665ff2206c9d4e50861f493f8e7beca8353b37671d633fe4b6e084c62e58ed9 - Setup.msi - Sora
- 0ed3b92fda104ac62cc3dc0a5ed0f400c6958d7034e3855cad5474fca253125e - Capcut Pro For PC.setup.msi - Capcut
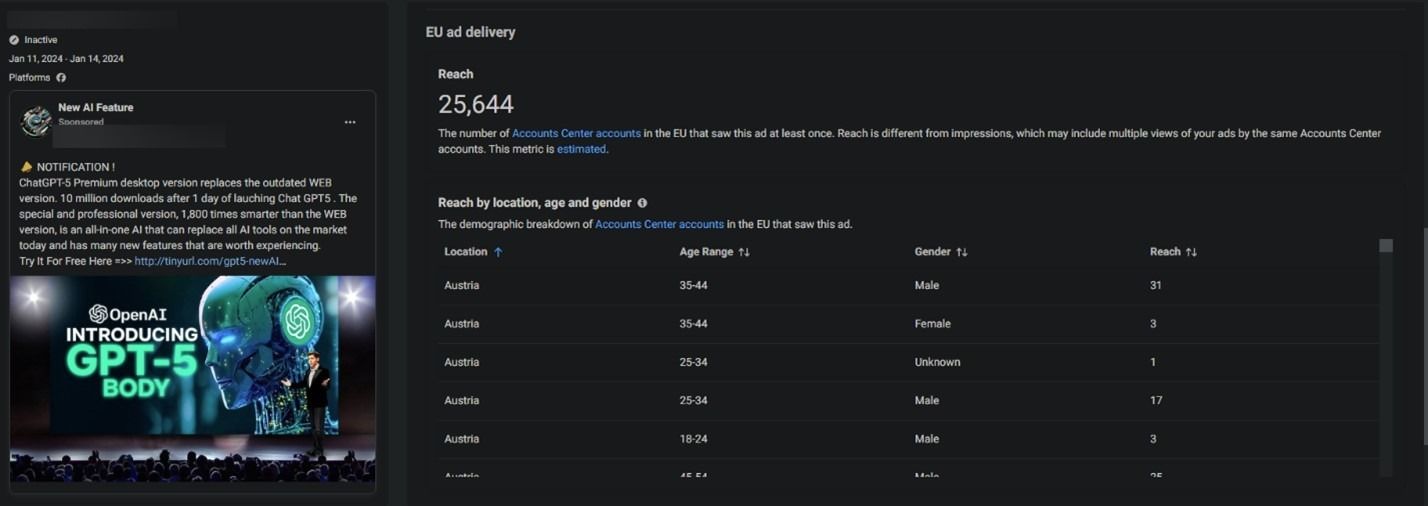
- 757855fcd47f843739b9a330f1ecb28d339be41eed4ae25220dc888e57f2ec51 - OpenAI ChatGPT-4.5 Version Free.msi - ChatGPT
- 3686204361bf6bf8db68fd81e08c91abcbf215844f0119a458c319e92a396ecf - Google Gemini AI Ultra Version Updata.msi - Gemini AI
- d60ea266c4e0f0e8d56d98472a91dd5c37e8eeeca13bf53e0381f0affc68e78a - Photo Effects Pro v3.1.3 Setup.msi - Photo Effects
- bb7c3b78f2784a7ac3c090331326279476c748087188aeb69f431bbd70ac6407 - Photo Effects Pro v3.1.3 Setup.msi - Photo Effects
- 0ed3b92fda104ac62cc3dc0a5ed0f400c6958d7034e3855cad5474fca253125e - AISora.setup.msi - Sora
Analysis of OpenAI Sora official version setup.rar – Rilide V4 sample
The malicious application that poses as AI-related software (although it mixes different LLMs, such as OpenAI, Sora, or Gemini, throughout its files) installs a browser extension that steals credentials, tokens, and cookies from Facebook accounts.
- Contains a MS Installer (.msi): "OpenAI Sora official version setup.msi"
- It tries to install to C:\Program Files (x86)\Google\Install (regardless of whether Google software has been previously installed)
Folder contents:
New Folder #%d1
- 88kus.xlsx
- Gemini.png
New Folder #%d2
- account_manager (20).xls
- account_manager (21).xls
- account_manager (22).xls
- list_page (3).xlsx
nmmhkkegccagdldgiimedpic
- background.js
- content.js
- favicon.png
- manifest.json
- ru.ps1
install.cmd logo.ico
Microsoft.VisualC.Dll
OpenAI Sora official version setup.msi
System.Deployment.dll
System.Web.DynamicData.Design.dll
nmmhkkegccagdldgiimedpic - a browser extension
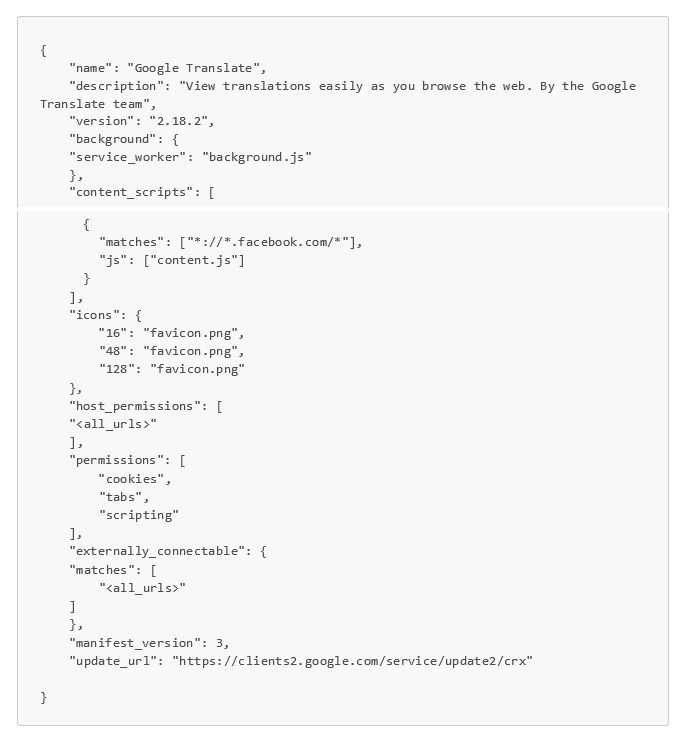
manifest.json:
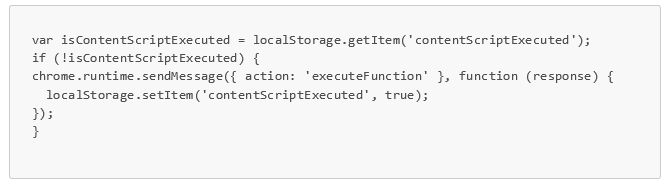
content.js:
background.js: The file is too large and obfuscated to include it here. It appears to steal credentials, tokens, cookies, etc. It also contains multiple references to financial accounts/wallets.
ru.ps1
1. Attempts to stop the processes of the following browsers: Chrome, Edge and Brave
2. Opens the following URL: "hxxps://gemini[.]google[.]com/app" (to appear legitimate) using the three browsers (if they are installed), while also loading the malicious extension.
It seems that the purpose is to open "Gemini" to trick the user (believing it is a legitimate application), but the main purpose is to use the extension to steal sensitive information from Facebook.
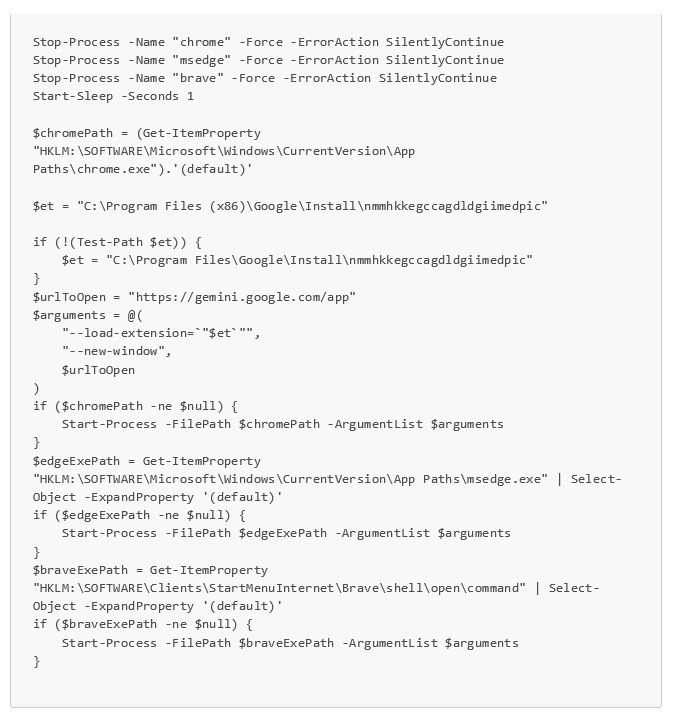
install.cmd
XLSX files
The purpose of these files is unclear at the moment - they appear to contain Facebook account names, alongside with specific monetary information and more - partially included in the screenshots below:
88kus.xlsx
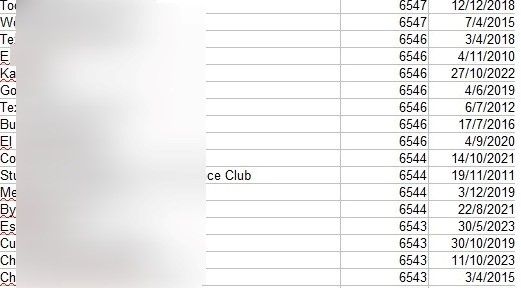
account_manager (20).xls

Indicators of Compromise
Vidar Stealer
Vidar is another prolific infostealer sold by the same malware-as-a-service model through ads and forums on the dark web and Telegram groups. The stealer can exfiltrate personal information and crypto from compromised devices.
The distribution system of Vidar Stealer has evolved across the years, from traditional spam campaigns and cracked software to malicious Google Search ads. And now It’s making rounds on social media platforms and delivered through sponsored ads on Meta’s platform.
Indicators of Compromise
Malicious hashes
- 6396ac7b1524bb9759f434fe956a15f5364284a04acd5fc0ef4b625de35d766b- g2m.dll - MidJourney
- 76ed62a335ac225a2b7e6dade4235a83668630a9c1e727cf4ddb0167ab2202f6- Midjourney.7z - MidJourney
IceRAT (written in JPHP)
Despite its name, this malicious software operates more like a backdoor than a remote access Trojan on the compromised device. IceRAT infections act as a gateway for secondary infections such crypto miners and information stealers that latch onto login credentials and other sensitive information from victims.
Indicators of Compromise
Malicious hashes
- aab585b75e868fb542e6dfcd643f97d1c5ee410ca5c4c5ffe1112b49c4851f47- Midjourneyv6.exe – MidJourney
- b5f740c0c1ac60fa008a1a7bd6ea77e0fc1d5aa55e6856d8edcb71487368c37c- Midjourneyv6ai.exe – MidJourney
- cc15e96ec1e27c01bd81d2347f4ded173dfc93df673c4300faac5a932180caeb- Mid_Setup.exe – MidJourney
- d2f12dec801000fbd5ccc8c0e8ed4cf8cc27a37e1dca9e25afc0bcb2287fbb9a- Midjourney_v6.exe – MidJourney
- f2fc27b96a4a487f39afad47c17d948282145894652485f9b6483bec64932614-Midjourneyv6.1_ins.exe – MidJourney
- f99aa62ee34877b1cd02cfd7e8406b664ae30c5843f49c7e89d2a4db56262c2e - Midjourneys_Setup.exe – MidJourney
- 54a992a4c1c25a923463865c43ecafe0466da5c1735096ba0c3c3996da25ffb7 - Mid_Setup.exe – MidJourney
- 4a71a8c0488687e0bb60a2d0199b34362021adc300541dd106486e326d1ea09b- Mid_Setup.exe - MidJourney
Nova Stealer
A new entry on the threat landscape is Nova Stealer, an intrusive and highly proficient info stealer with numerous capabilities, including password exfiltration, screen recordings, discord injections, and crypto wallet hijacking, among others. The malicious payload is offered as Malware-as-a-Service by the threat actor, who goes by the handle Sordeal.
Indicators of Compromise
Malicious hashes
- fb3fbee5372e5050c17f72dbe0eb7b3afd3a57bd034b6c2ac931ad93b695d2d9- Instructions_for_using_today_s_AI.pdf.rar - AI and Life
- 6a36f1f1821de7f80cc9f8da66e6ce5916ac1c2607df3402b8dd56da8ebcc5e2- Instructions_for_using_today_s_AI.xlsx_rar.rar - AI and Life
- fe7e6b41766d91fbc23d31573c75989a2b0f0111c351bed9e2096cc6d747794b- Instructions for using today's AI.pdf.exe - AI and Life
- ce0e41e907cab657cc7ad460a5f459c27973e9346b5adc8e64272f47026d333d- Instructions for using today's AI.xlsx.exe - AI and Life
- a214bc2025584af8c38df36b08eb964e561a016722cd383f8877b684bff9e83d- 20 digital marketing tips for 2024.xlsx.exe - Google Digital Marketing
- 53714612af006b06ca51cc47abf0522f7762ecb1300e5538485662b1c64d6f55 - Premium advertising course registration form from Oxford.exe - Google Digital Marketing
- 728953a3ebb0c25bcde85fd1a83903c7b4b814f91b39d181f0fc610b243c98d4- New Microsoft Excel Worksheet.exe - Google Digital Marketing
The Midjourney Saga
AI tools are all over the internet. Some are free, some offer free trials, and others run on a subscription plan. Enter Midjourney, one of the most prominent generative AI tools that lets users craft images from text inputs.
With a growing user base of over 16 million as of Nov. 2023, Midjourney has been a fan-favorite among cybercriminal gangs as well over the past year.
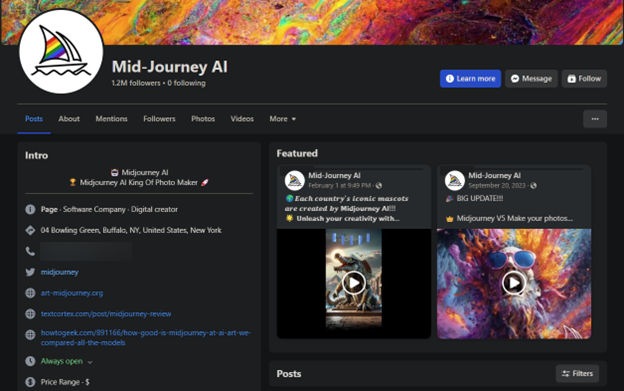
Since at least June 2023, cybercriminals have conducted massive ad campaigns impersonating the AI-powered art generator to serve malware to unsuspecting users.
Just a single Facebook page using the name Mid-Journey AI with a following of 1.2 million had an ad reach of over 500,000 individuals in Europe before being taken down on March 8, 2024.
Note: It’s unclear if Meta took down the impostor page following multiple reports by victims or official Midjourney developers.
The malicious page with 1.2 million followers appears to have been taken over on June 28, 2023, when the attackers changed the original name of the compromised Facebook profile page. The individuals managing the page were spread worldwide, according to information from our researcher’s analysis.
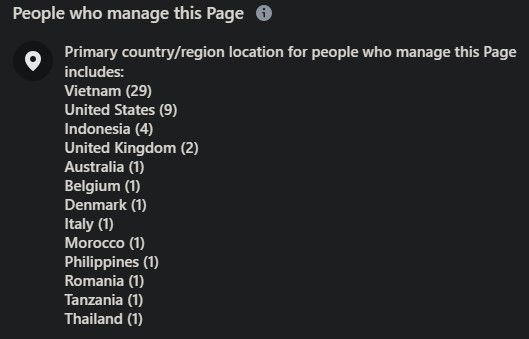
Before the demise of the impostor Midjourney page on Facebook, Bitdefender Labs had a chance to carefully inspect and catalog the malicious advertisement campaigns running through it.
At first glance, it appears that the cybercriminals behind the campaign invested time and resources to boost the popularity and reach of the malicious page, posting highly engaging content expanded by hundreds of likes and user comments. Again, we can’t confirm whether all of the AI-generated images showcased in their ads were stolen from different content creators and other official websites.
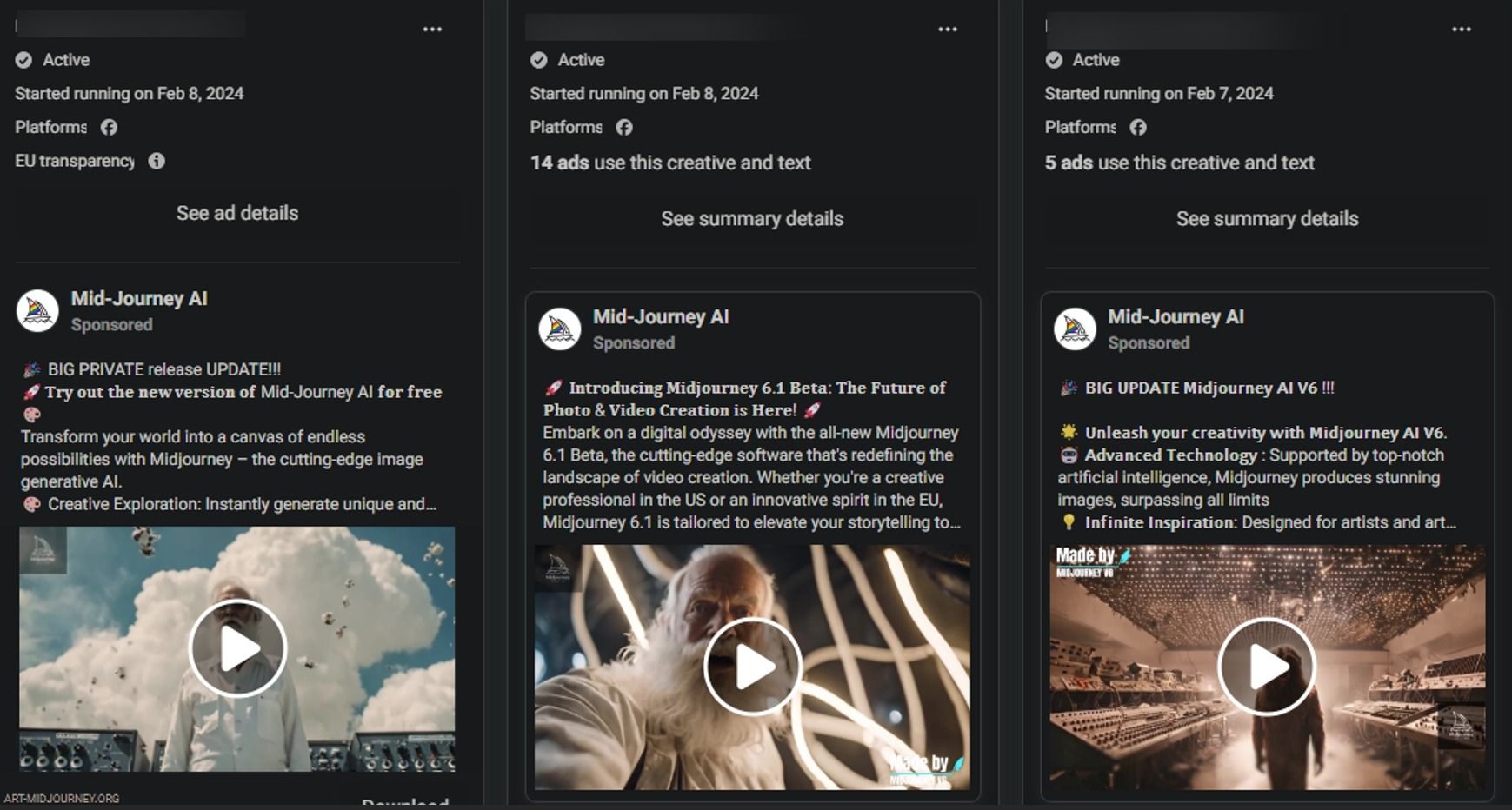
The threat actors went above and beyond to tailor their ads, showcasing their creative side with custom ads for France, Germany, and Spain that featured AI-reimagined images of national mascots.
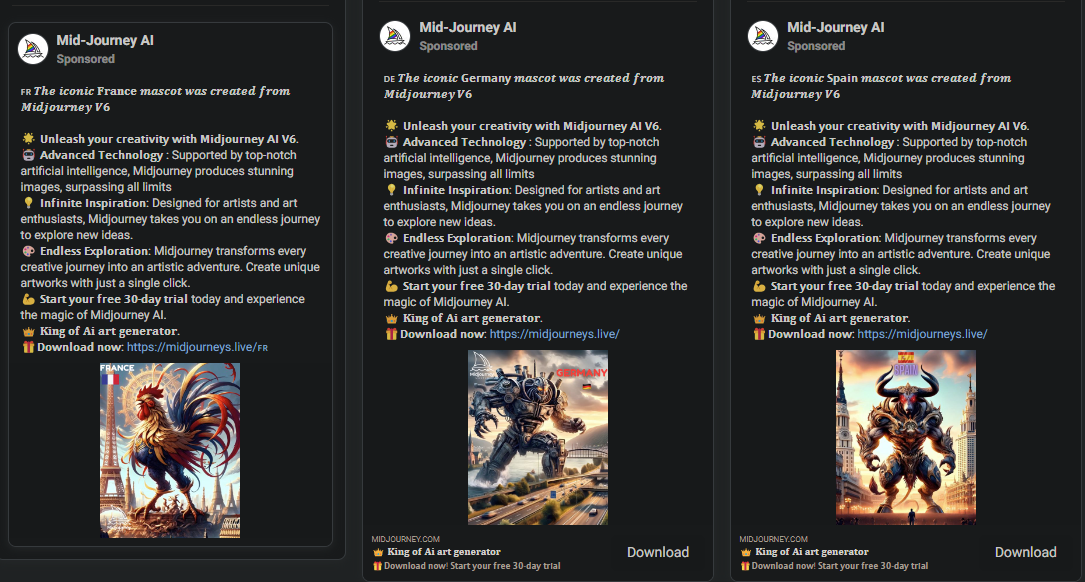
Other ads attempt to lure users interested in the NFT marketplace with a chance to create NFT art and even monetize their generated images after minting their artwork through a blockchain.
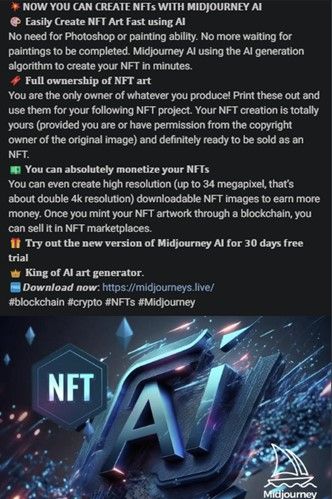
Although the imposter page boasting over 1.2 million followers was recently shut down, our research has shown that cybercriminals acted quickly to set up a new page impersonating Midjourney between March 8-9, 2024. The page was also set up after taking over another user’s Facebook account, who also commented in the review section of the page warning other users that the account was hacked. Since we began our investigation, we noticed an additional four Facebook pages attempting to impersonate Midjourney, some of which were also removed from the platform.
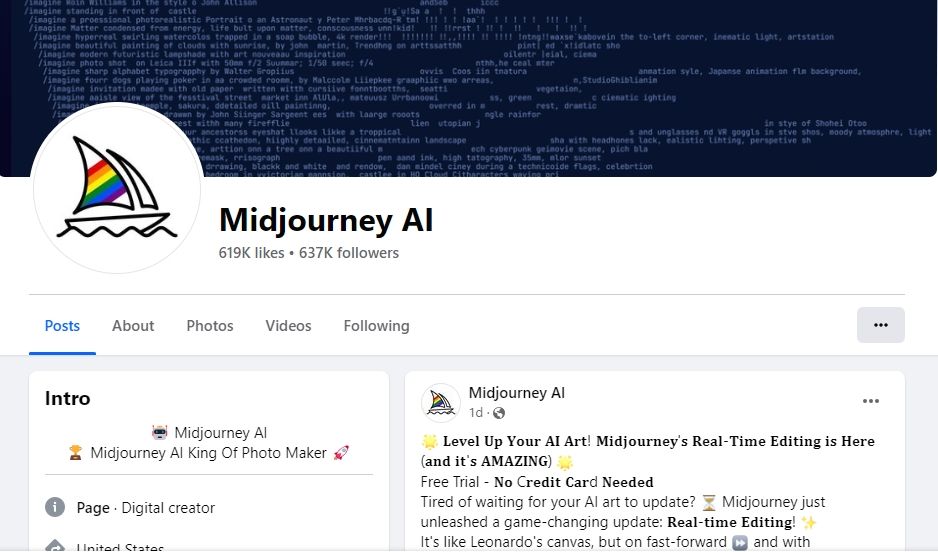
The latest malicious page impersonating Midjourney appears to have been taken over by the attackers on March 18 when the cybercriminals changed the original name of the original Facebook page. As of March 26, the scam profile has 637,000 followers (as seen below).
MidJourney Fake Website
Indicators of compromise
- 159.89.120.191
- 159.89.98.241
Malicious Domains
- https://aimidjourney[.]agency/
- https://aimidjourney[.]org/
- https://getmidjourney[.]tech/
- https://aimidjourney[.]online/
- https://midjourneys[.]world/
- https://mid-journey[.]pro/
- https://deepface[.]pro/
- https://ai-midjourneys[.]org/
- https://aimidjourneys[.]com/
- https://ai-midjourney[.]pro/
- https://aimidjourney[.]tech/
- https://get-midjourney[.]site/
- https://midjourneys[.]online/
- https://midjourneys[.]site/
- https://ai-midjourney[.]net/
- https://midjourneys[.]co/
- https://aimidjourneys[.]org/
- https://mid-journey[.]life/
- https://midjourneys[.]live/
- https://midjourneysai[.]us/
- https://midjourneys[.]tech/
- https://midjourneyais[.]us/
- https://mid-journey[.]tech/
- https://ai-midjourney[.]info/
- https://art-midjourney[.]art/
- https://art-midjourney[.]org/
- https://ai-midjourneys[.]com/
- https://ai-midjourneys[.]net/
- https://aimidjourney[.]space/
More malicious pages and ads
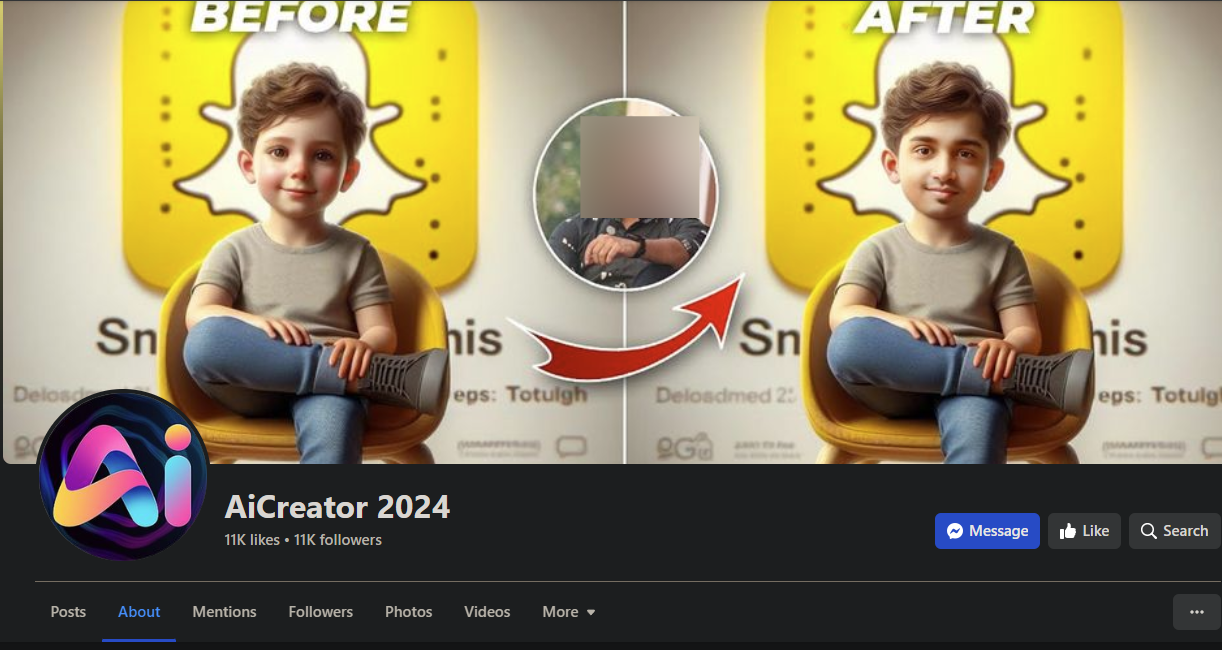
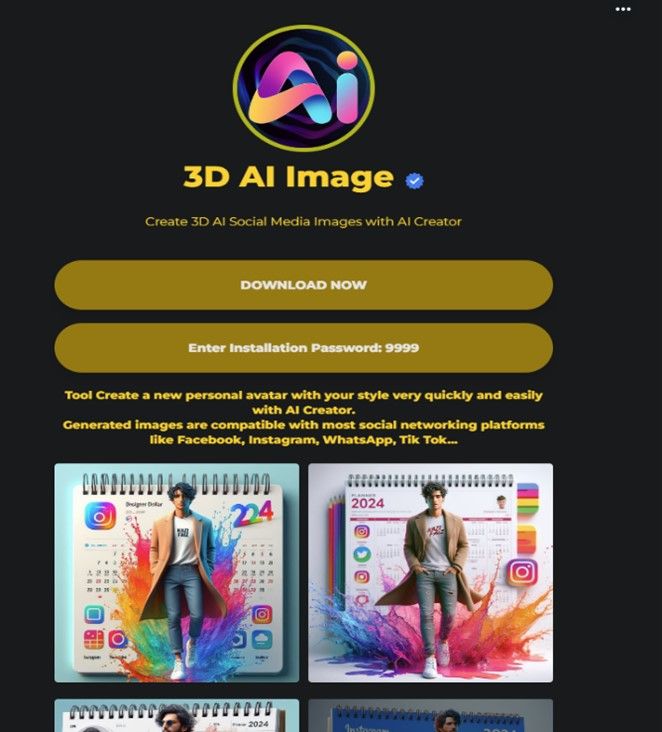
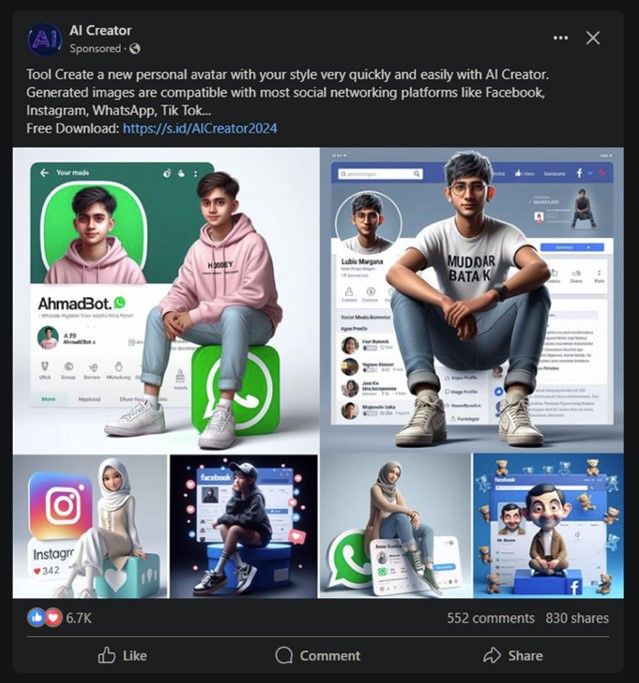
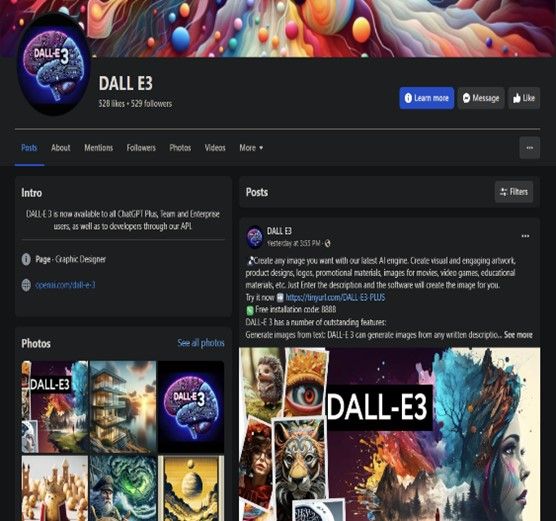

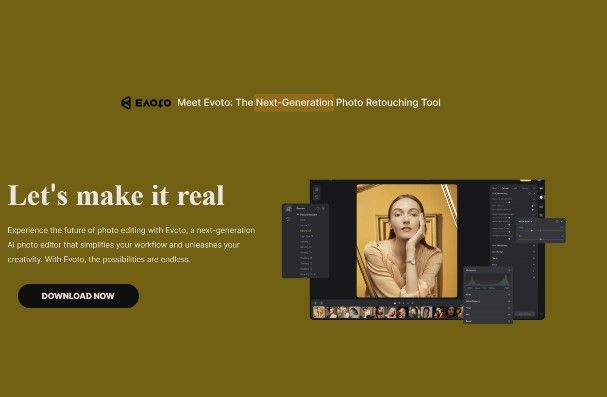
Info Stealer activity and best practices to avoid compromise
Info-stealer activity has risen sharply over the past couple of years, with cybercrooks propagating stealer attacks through email spam, legitimate-looking apps, Google search advertising and other schemes over social media.
The success of malicious data stealers that exfiltrate sensitive information from web browsers, emails, messaging apps, and even crypto wallets works seemingly on a malware-as-a-service model, allowing even the most low-level cybercrook to conduct elaborate attacks.
How to prevent Info-Stealer infections
- Use a trustworthy security solution. Bitdefender’s industry and award-leading protection against e-threats of all kinds, from viruses to Trojans and all the way to ransomware, prevents even the most evasive malware intrusion from damaging your device and data.
- Employ a layered security approach. A comprehensive security solution with multi-layered protection features not only detects malware but prevents you from landing on a malicious webpage, stopping any intrusive download that can impact your security and privacy.
- Keep software and operating systems up to date. Skipping updates and patches can significantly impact your device and online security. Use Bitdefender security solutions to conduct a full vulnerability assessment on your Windows device. With just one click, you can immediately check for outdated and vulnerable software, missing security patches, or unsafe system settings that you immediately fix.
- Stick to good cyber hygiene and don’t click on suspicious links, pop-ups or download software from unsafe or unknown sources.
- Only download applications from official stores and websites
- Enable two-factor authentication to avoid malicious actors from gaining access to your online accounts to steal your data and money
- Have a chat with Scamio, our AI-powered scam detector online or via Facebook Messenger. You only need to describe the details of a potential scam, send suspicious links, or upload screenshots and QR codes to receive recommendations and thwart potential security threats.
An up-to-date, complete list of indicators of compromise is available to Bitdefender Advanced Threat Intelligence users. Currently known indicators of compromise can be found in the dedicated list below:
tags
Author

With more than 15 years of experience in cyber-security, I manage a team of experts in Risks, Threat Intel, Automation and Big Data Processing.
View all posts
Andrei is a graduate in Automatic Control and Computer Engineering and an enthusiast exploring the field of Cyber Threat Intelligence.
View all posts
I'm a software engineer with a passion for cybersecurity & digital privacy.
View all posts
Since 2016, Andrei deals with analysis and recovery of various cyber threats, with a keen focus on ransomware attacks. His current research interests include cryptography, malware and exploitation.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks


















