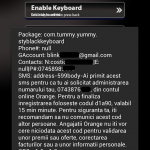
Clueful Detects Vulnerable Applovin/Vulna Apps

Bitdefender Labs malware researchers Vlad Bordianu and Tiberius Axinte have created a proof-of-concept exploit for the vulnerable Applovin ad-serving framework (also known as Vulna) versions 2.0.74 through 5.0.3 included. The exploit runs arbitrary code in the context of the affected Android app.
To exploit the vulnerable update function included in Applovin, an attacker needs to be able to respond to framework update requests originating from the target device. In the studied scenario, this is performed via a man in the middle HTTP injection attack at the wireless router level, although other attacks may also be practicable.
The attack is made possible by the lack of encryption in transit and the lack of an update authentication mechanism – the only verification that is performed is a simple integrity check, in which a hash (included in the header of the update server’s response) must coincide with the hash of the actual update package. Had the update process used HTTPS, the attack would no longer have been possible.
“We cannot say if the Google Play application review process will prevent the creation of other SDKs or individual apps that present such functionality in the future. Google should definitely give some attention to the issue, as otherwise a malicious programmer might publish a perfectly legitimate app with such a backdoor function and turn it into a data-stealing trojan later” commented Catalin Cosoi, Chief Security Strategist for Bitdefender.
The insecure update mechanism has been removed in the latest version of the Applovin SDK. Bitdefender Clueful can detect any apps which still use vulnerable versions of the SDK.

tags
Author

Razvan Stoica is a journalist turned teacher turned publicist and technology evangelist. Recruited by Bitdefender in 2004 to add zest to the company's online presence.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks