Ethereum OS miners targeted by SSH-based hijacker

The increased popularity of emerging crypto-currencies such as Monero and Ethereum has put miners once again in the bad guys’ crosshairs. Illicit digital currency mining, either directly in the browser or via maliciously-delivered miners, is nothing new, but our honeypot systems have started flagging a different type of attack against Ethereum-mining farms.
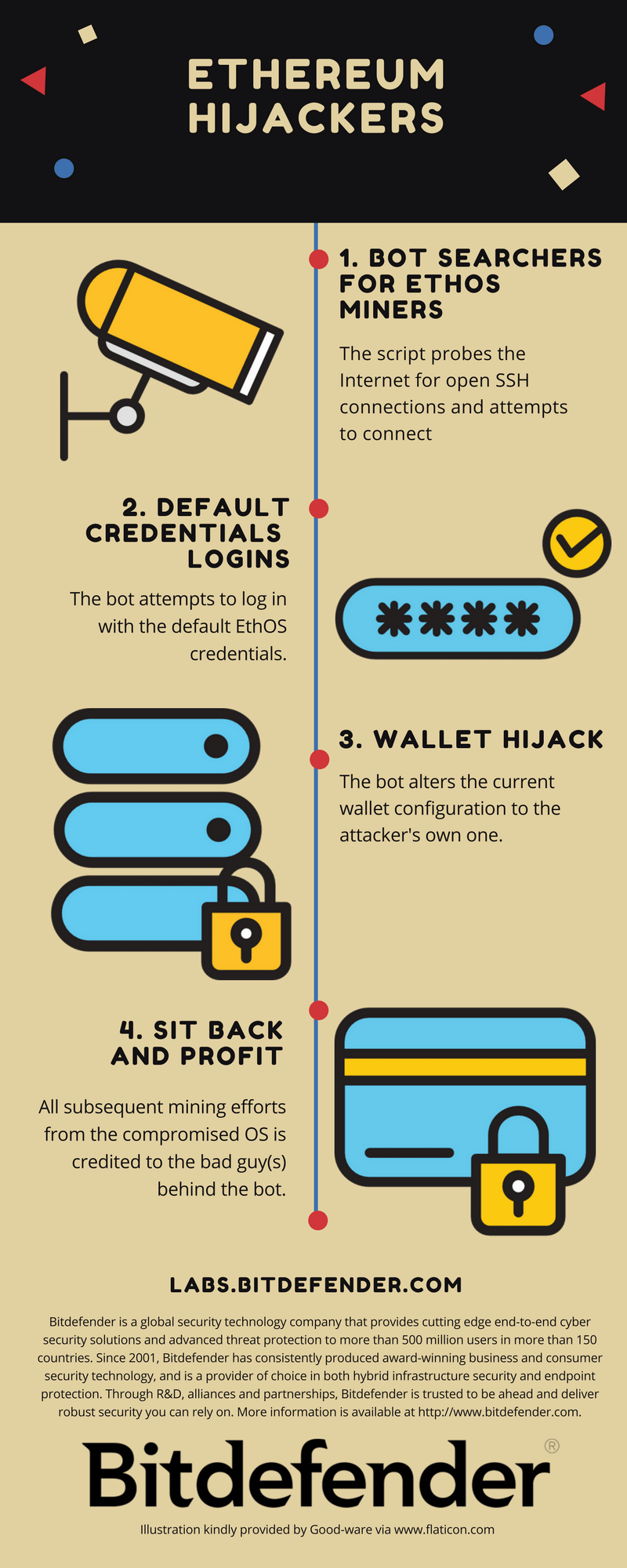
We detected the first attacks on Monday, when our SSH honeypots prompted us about a bot attempting to change the system configuration to hijack funds from Ethereum-mining operations.
If you are in the market, you probably know of an operating system optimized for Ethereum mining, dubbed EthOS. This commercial operating system can mine Ethereum, Zcash, Monero and other crypto-currencies that rely on GPU power. According to its creators, it currently runs on more than 38,000 mining rigs across the world. Like other specialized operating systems, it comes pre-loaded with the necessary tools, and a default username and password. After deployment, the user only needs to add a wallet for mining fees and, of course, change the default username and password.
Precisely this oversight is currently exploited in the wild. The bot scans for the entire IPv4 range and looks for open SSH connections. If found, it attempts to log in using the default username and password to the EthOS operating system: ethos:live and root:live.
If the login succeeds, it tries to change the existing configuration for Ethereum to hijack the mining process to the attacker’s Ethereum address. The wallet in this case (0xb4ada014279d9049707e9A51F022313290Ca1276) shows 10 transactions over the past days worth a total of $611 in Ether.
So, if you are running an Ether Miner based on Ethereum OS, make sure you have changed the default login credentials. If you haven’t done so, now would be a good time to check whether the miner is sending money to you, not hackers.
tags
Author
Right now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks













