Hide and Seek IoT Botnet Learns New Tricks: Uses ADB over Internet to Exploit Thousands of Android Devices

Hide and Seek, a new IoT botnet discovered by our honeypot system in early January, has quickly gained notoriety after amassing over 90,000 devices in a large botnet in a matter of days. While the first variant performed brute force attacks over the Telnet service to jack into devices, later updates involved new command injection exploits in a device’s web interface, which extended the botnet’s capabilities to IPTV cameras.
The newly identified samples add functionality by exploiting the Android Debug Bridge (ADB) over Wi-Fi feature in Android devices, which developers normally use for troubleshooting. While it’s traditionally disabled by default, some Android devices are shipped with it enabled, practically exposing users to remote connections via the ADB interface that’s accessible using the TCP port 5555. Any remote connection to the device is performed unauthenticated and allows for shell access, practically enabling attackers to perform any task in administrator mode.
Exposing this protocol over the internet without authentication is baffling and troublesome — it’s not a vulnerability in the Android operating system itself, but rather a feature the vendor may have simply neglected to disable when shipping devices.
The ‘root’ of all evil
While exposure of Android devices via the ADB over Wi-Fi feature was reported in early June, it has yet to be fixed. First abused by a cryptocurrency miner in early June, the issue is more troubling as it enables attackers to silently install and execute functions with unauthenticated “root” – or administrator mode – privileges on some devices.
The Hide and Seek botnet already packed a vast arsenal for compromising internet-connected devices, and this recent addition may enable it to amass at least another 40,000 new devices, according to a quick search on Shodan. While most potentially affected devices seem to be in Taiwan, Korea and China, some appear to be in the United States and the Russia.
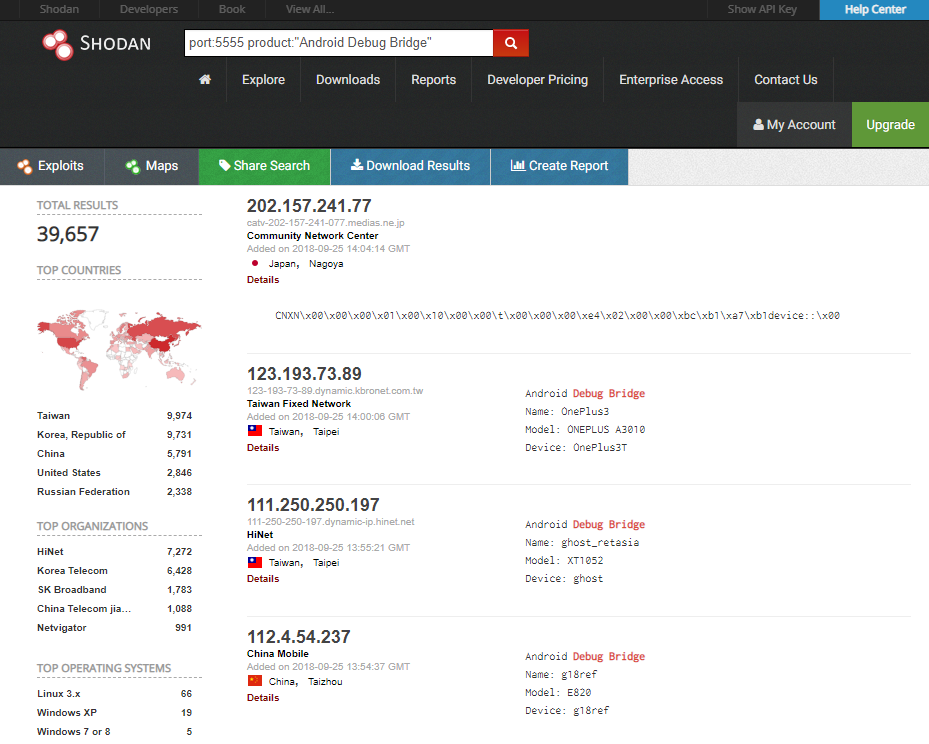
Some of these devices may directly face the internet, while others may be hidden behind routers. However, this does not make them immune, as routers are among the most vulnerable internet-connected devices, accounting for 59.45 percent of the top 10 most-vulnerable devices, according to Bitdefender research.
This means the number of potentially affected devices could be significantly higher, possibly enabling the Hide and Seek botnet to amass tens of thousands of more new bots than the 40,000 estimated by Shodan.
It’s safe to say that not just Android-running smartphones are affected — smart TVs, DVRs and practically any other device that has ADB over Wi-Fi enabled could be affected too.
Considering the evidence at hand, we speculate the botnet operators are constantly adding new features to “enslave” as many devices as possible, although the true purpose of the botnet remains unknown.
For more information regarding the investigation and analysis of the Hide and Seek botnet, you’re more than welcome to attend the Virus Bulletin 2018 summit between 3-5 October at the Fairmont The Queen Elizabeth hotel in Montreal, Quebec, Canada. Bitdefender researchers Adrian Șendroiu and Vladimir Diaconescu will host a Red Room session entitled “Hide’n’Seek: an adaptive peer-to-peer IoT botnet,” revealing intimate details of the activity and investigation of the IoT botnet.
The samples used for this piece of research can be identified as c9dd9705188dd8644839415b6cb2ffbec7e9b5a2 and 6c7db81bfbec5ce2600f1a7d6ab976a7c2d7cc55.
tags
Author
Liviu Arsene is the proud owner of the secret to the fountain of never-ending energy. That's what's been helping him work his everything off as a passionate tech news editor for the past few years.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks















