Ouroboros Ransomware decryption tool

Ouroboros ransomware has been around for more than a year in various forms, operated by different cybercrime groups. Ouroboros, known to spread via Remote Desktop Protocol bruteforce attacks and deceptive downloads, has claimed a significant number of victims worldwide. We’re now happy to announce the availability of a new decryptor that can restore the .Lazarus, and .Lazarus+ file extensions to their original, unencrypted form.
Please note that this tool only works for the Lazarus and Lazarus+ extensions. The .Kronos variant is still under analysis.
How to tell if you are infected with this specific variant of Ouroboros
On an infected computer, most files are encrypted and renamed to the original file name plus the [ID=XXXXXXXXXX][Mail= * ].Lazarus or [ID=XXXXXXXXXX][Mail= * ].Lazarus+ strings. The ID consists of 10 random characters. Additionally, Ouroboros would create several ransom notes called Read-Me-Now.txt


If you are infected with this variant of Lazarus, you can download the decryptor right away. If you are interested in how Ouroboros works, you may want to read the next chapter.
Download the Ouroboros decryptor
Brief technical description
Affected files are encrypted with the AES 256 CBC algorithm based on the assembly aesenc/aesenclast instructions. This prevents the malware from running on older CPU models (pre-2010) that lack support for these instructions.
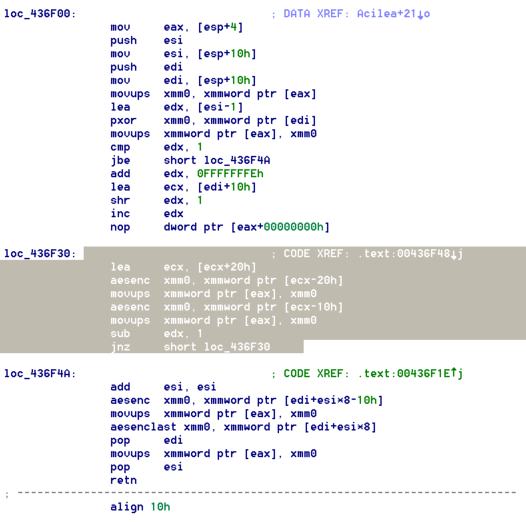
The initialization vector used for encryption is hardcoded rather than generated, and it changes with each version:
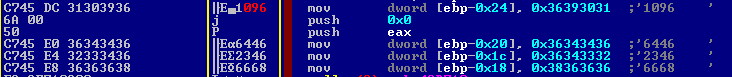
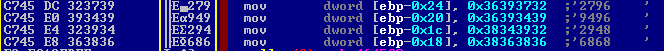
The key is constructed using a combination of two PRNGs (pseudo-random number generators), Mersenne Twister and IsaacRandom, starting from the following alphabet:

After key generation, the ransomware attempts to contact a server to send the key, along with user information. In case of no response, the key will be discarded and replaced with a hard-coded one:

How to decrypt your data
Step 1: Download the decryption tool below and save it somewhere on your computer.
Download the Ouroboros decryptor
This tool does not require an active Internet connection.
Step 2: Double-click BDOuroborosDecryptTool.exe and allow it to run elevated at the UAC prompt.
Step 3: Accept the End User License Agreement
Step 4: Select “Scan Entire System” if you want to search for all encrypted files. Alternatively, just add the path to the folder containing the encrypted files. We strongly recommend you also select “Backup files” before starting decryption, should anything unexpected occur during the process. Start decryption by clicking the “Scan” button.
At the end of this step, your files should be decrypted. The tool generates an operation log at the %temp%\BDRansomDecryptor\BDRansomDecryptor\BitdefenderLog.txt location.
If you need assistance, contact us at the feedback address listed in the tool. We kindly ask you to attach the above-mentioned log file to help you isolate potential issues and minimize response time.
Automated deployment across the network
The tool can also be executed via command line. Should you need to automate deployment of the tool inside a large network, you might want to use this feature.
- -help – provides information on how to run the tool silently (this information gets written in the log file, not on the console output)
- start – this argument allows the tool to run silently (no GUI)
- –path – this argument specifies the path to scan
- –test – this argument specifies the test path to a pair of original/encrypted files
- o0:1 – enable Scan entire system option (ignoring -path argument)
- o1:1 – enable Backup files option
- o2:1 – enable Overwrite existing files option
Command line examples:
BDOuroborosDecryptor.exe start -path:”C:\” -> the tool starts with no GUI and scans C:\
BDOuroborosDecryptor.exe start o0:1 -> the tool starts with no GUI and scans the entire system
BDOuroborosDecryptor.exe start o0:1 o1:1 o2:1 -> the tool scans the entire system, backs up the encrypted files and overwrites present clean files
Acknowledgement:
This product includes software developed by the OpenSSL Project, for use in the OpenSSL Toolkit.
tags
Author

The meaning of Bitdefender’s mascot, the Dacian Draco, a symbol that depicts a mythical animal with a wolf’s head and a dragon’s body, is “to watch” and to “guard with a sharp eye.”
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks
















