RIG Exploit Kit Swaps Dead Raccoon with Dridex

In January 2022, the Cyber Threat Intelligence Lab started tracking a RIG Exploit Kit campaign pushing Raccoon Stealer – a credential-stealing Trojan advertised and sold on underground forums as malware-as-a-service for $ 200 a month.
RIG Exploit Kit is known to be used in conjunction with stealers such as RedLine (documented by Bitdefender earlier in April). The campaign tracked by Bitdefender has taken an unexpected turn in February when Raccoon Stealer came to a temporary halt as one of the lead developers was killed in the Russian invasion of Ukraine.
Despite the stealer no longer being operational anymore, threat actors operating this RIG campaign have rapidly adapted by replacing Raccoon malware with Dridex to make the most of the ongoing campaign. The diagram below shows a drop in pushed payloads around Feb 20, but operations continue undisrupted despite the termination of Racoon Stealer in late March.
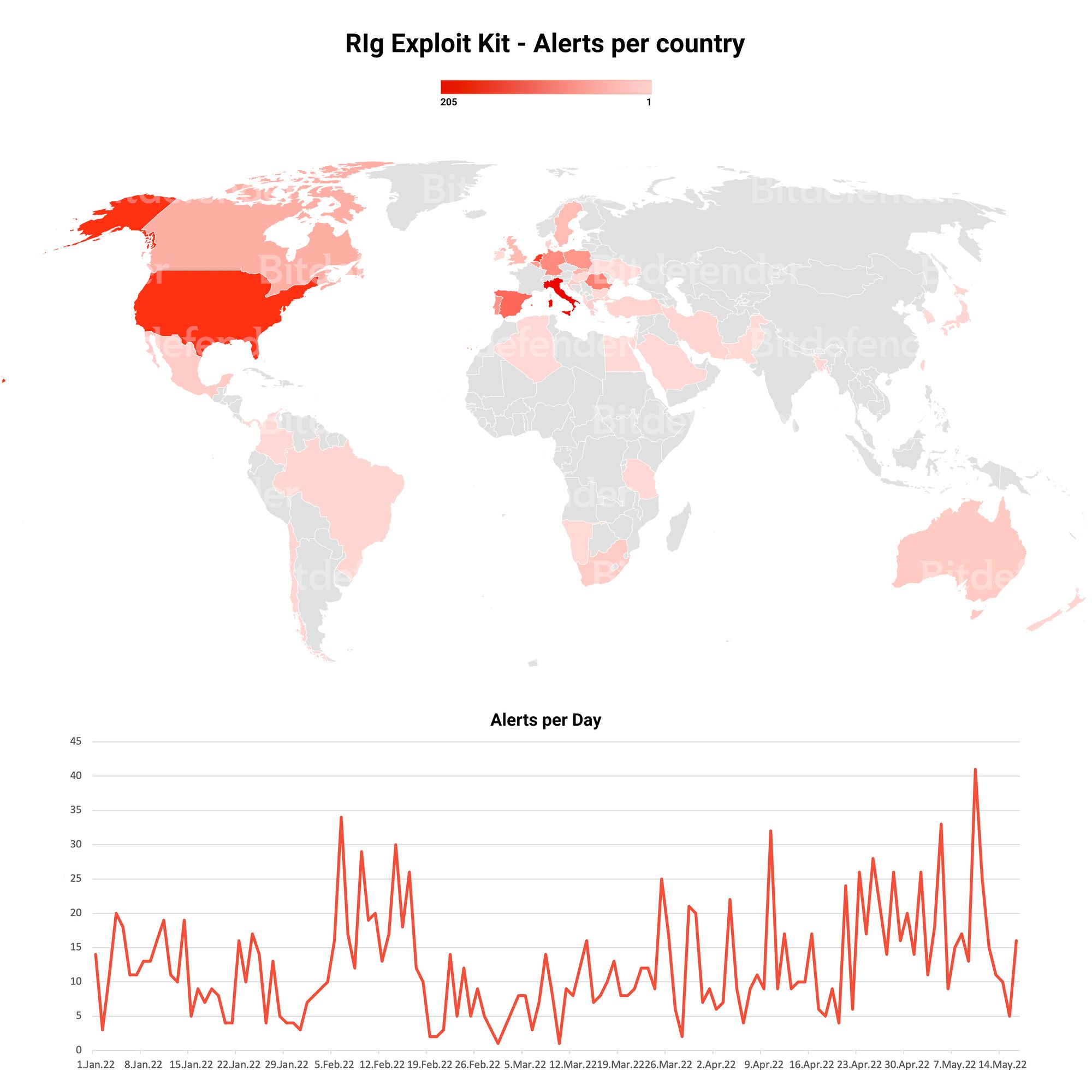
This once again demonstrates that threat actors are agile and quick to adapt to change. By design, RIG Exploit Kit allows for rapid substitution of payloads in case of detection or compromise, which helps cyber-criminal groups recover from disruption or environmental changes.
Despite the bumps in the road, Raccoon Stealer is not gone, it’s just on a break – the first one since 2019. If you want to learn more about it, we have a deep dive whitepaper available for download below:
tags
Author

Passionate about reverse engineering, Mihai worked on malware analysis and detection techniques in the past. Now he is doing research on exploit detection and mitigation for Windows applications.
View all posts
I am a security researcher in the GEMMA team, passionate about reverse engineering and malware analysis. In the spare time, I participate in CTF contests. I am also passionate about forensics.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks















