Side-Loading OneDrive for profit – Cryptojacking campaign detected in the wild
Cryptojackers have become very lucrative for cybercriminals in recent years as the price of cryptocurrency soared. From data breaches to PUAs to warez downloads, coin miners and cryptojackers crop up steadily in our threat landscape reports.
However, to meet their financial expectations, cybercriminals are taking new approaches to planting and loading cryptojackers on victims’ computers. This is the case of an active cryptojacking campaign that uses a Dynamic Library Link (DLL) hijacking vulnerability in OneDrive to achieve persistence and run undetected on infected devices.
In this paper we describe a cryptojacking campaign in which the attackers exploit known DLL Side-Loading vulnerabilities in Microsoft OneDrive.
Key findings
- Bitdefender identified and documented a cryptojacking campaign exploiting known DLL sideloading vulnerabilities in Microsoft OneDrive.
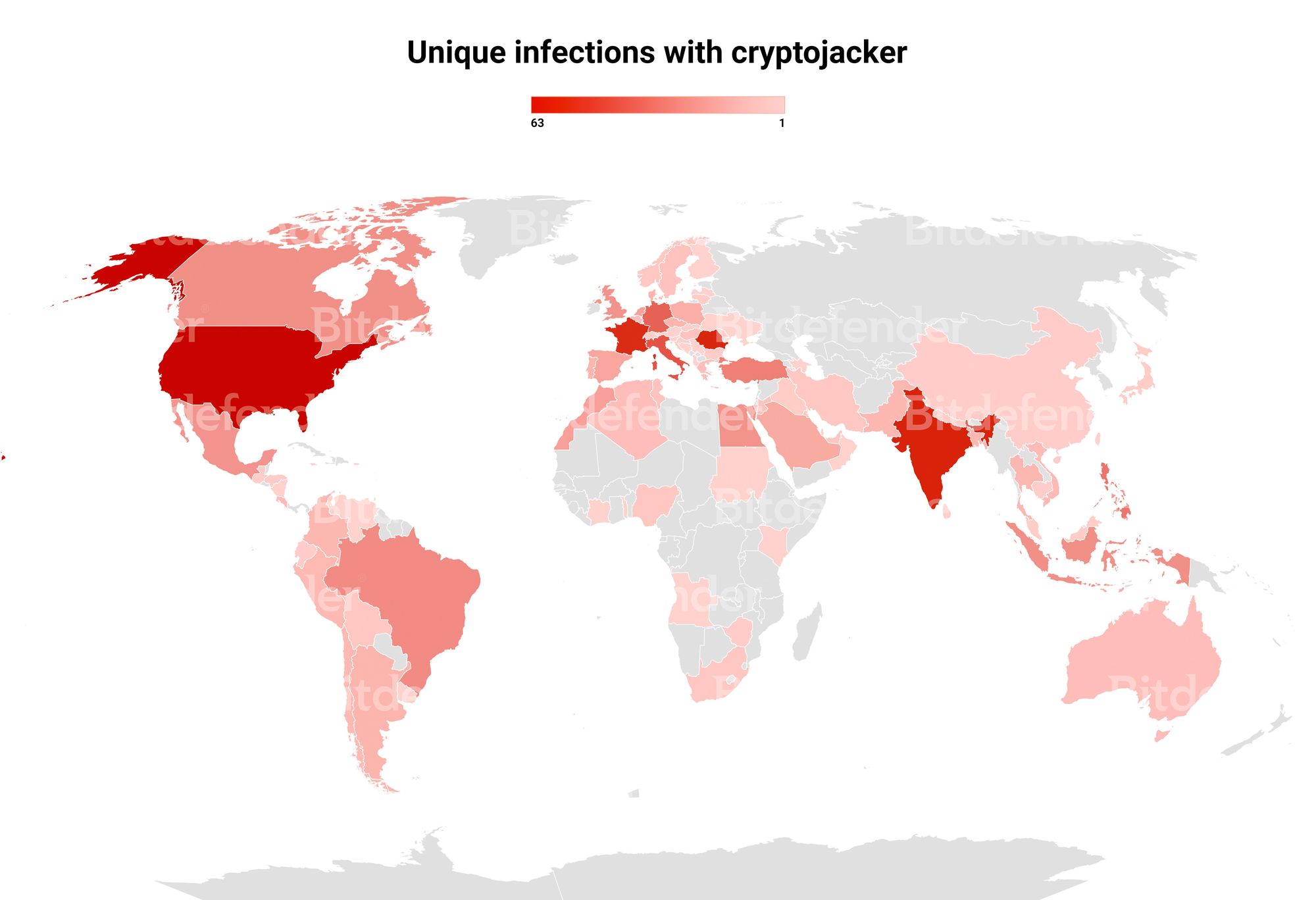
- Between May 1 to July 1, 2022 we detected over 700 instances of the cryptojacker using the DLL sideloading vulnerabilities.
Recommendations
Bitdefender recommends OneDrive users to ensure their security solution and operating systems are up-to-date; avoid cracked software and only download applications from trusted sources. Businesses should go further by tuning security solutions to monitor for DLL sideloading and applying IOCs to prevention and endpoint detection and response (EDR) solutions.
An up-to-date and complete list of indicators of compromise is available to Bitdefender Advanced Threat Intelligence users. The currently known Indicators of Compromise can be found in the whitepaper below.
tags
Author

As part of the Attack Research team, I spend my working hours investigating techniques used by malware and engineering detection methods for them.
View all posts
I'm a senior software engineer at Bitdefender. Passionate about malware behavior analysis, I am continuously looking for new tricks employed by malicious actors.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks

















