Tens of Thousands of Compromised Android Apps Found by Bitdefender Anomaly Detection Technology

Bitdefender researchers used a recently announced industry-first app anomaly detection technology incorporated into Bitdefender Mobile Security to uncover a hidden malware campaign living undetected on mobile devices worldwide for more than six months.
Bitdefender researchers believe that this mobile malware has been thriving undisturbed for an extended period of time in the absence of behavior-based detection capabilities on Android.
Unknown Threat at a Global Scale
Upon analysis, the campaign is designed to aggressively push adware to Android devices with the purpose of driving revenue. However, the threat actors involved can easily switch tactics to redirect users to other types of malware, such as banking Trojans to steal credentials and financial information or ransomware. To date, Bitdefender has discovered 60,000 completely different samples (unique apps) carrying the adware and we suspect there is much more in the wild.
The malware has been live since at least October 2022 and is noteworthy because without the new app anomaly technology – it most likely would have been able to stay undetected. Because of the high number of unique samples discovered, the operation is most likely fully automated.
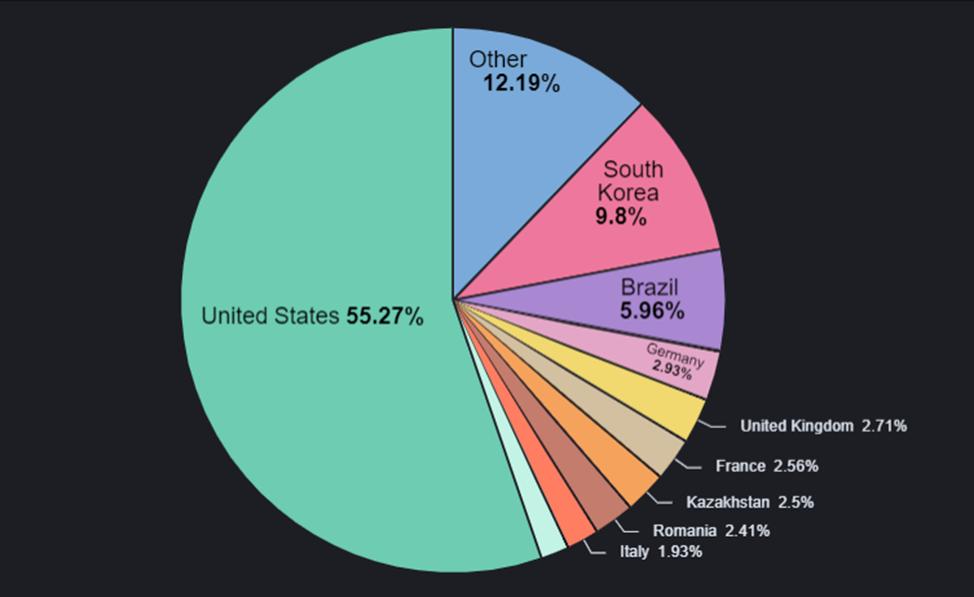
The distribution worldwide is all the more impressive given that it's not in any official stores. The malware's operators, however, still need to persuade users to download and install third-party apps, so they've disguised their threat on highly sought-after items you can't find in official stores, even if they were legitimate. In other situations, the apps simply mimicked the real ones published in the Play Store.
Here are some of the types of apps mimicked by the malware:
- Game cracks
- Games with unlocked features
- Free VPN
- Fake videos
- Netflix
- Fake tutorials
- YouTube/TikTok without ads
- Cracked utility programs: weather, pdf viewers, etc
- Fake security programs
The distribution is organic, as the malware appears when searching for these kinds of apps, mods, cracks, etc. In fact, modded apps are a hot commodity, with websites dedicated entirely to offering these types of packages. Usually, modded apps are modified original applications with their full functionality unlocked or featuring changes to the initial programming.
For example, when the user opens a website from a Google search of a “modded” app, they would be redirected to a random ad page. Sometimes, that page is a download page for malware disguised as a legit download for the mod the user was searching for.
As an example, take the following case:
- At 09:43:31, the user accessed hXXp://modsofapk[.]com/appcoins-wallet-mod-apk/download1/
- Immediately after, at 09:43:32 it was redirected to hXXp://1yesterdayx[.]com/worjt1e6a5efdf4388a30895ddce35539e28e199d821e?q=appcoins%20wallet%20mod%20apk%20v2.9.0.0%20(free%20purchased/premium%20cracked), a website meant to serve the malware
Hidden Android apps are entering a new era
Since API 30, Google removed the ability to hide the app icon on Android once a launcher is registered. However, this only applies if you register a launcher in the first place. To circumvent this, the application does not register any launchers and relies on the user, and the default Android install behavior, to run for the first time. When installing a downloaded application, the last screen in the procedure will be an "Open"app.
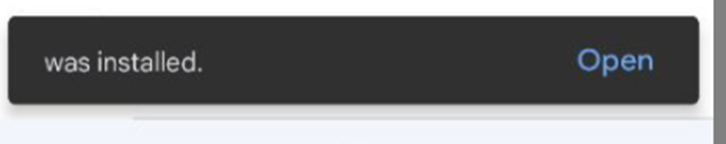
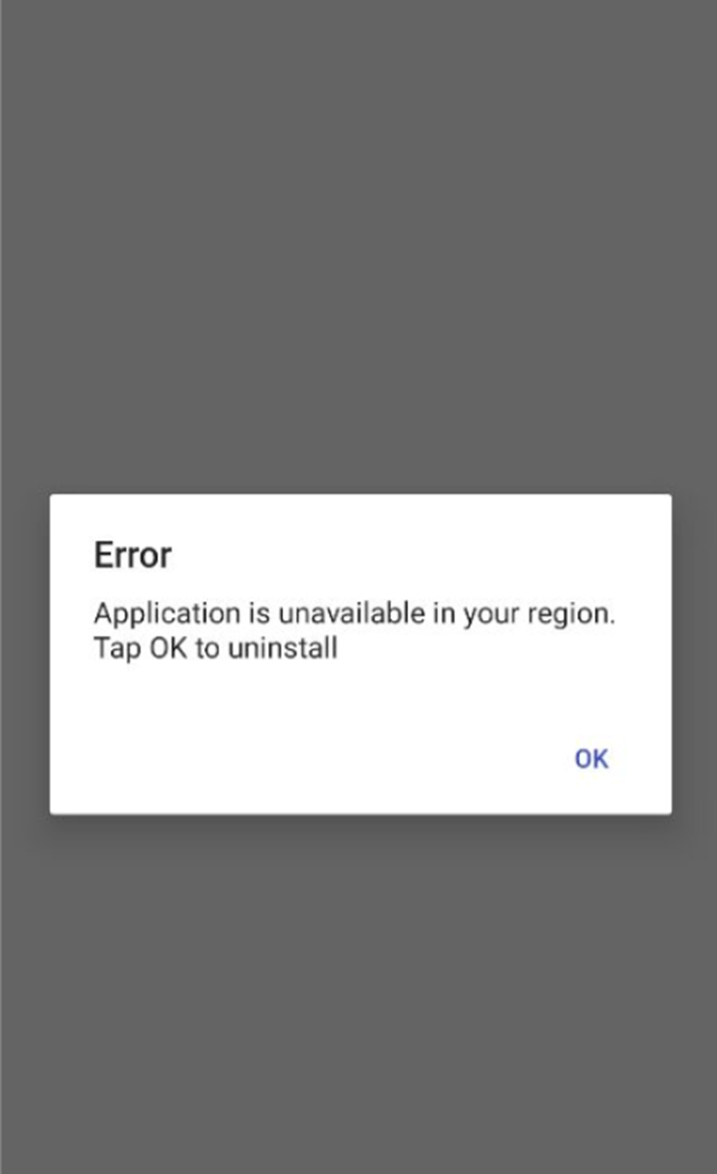
This is all the malware needs to ensure that it will not be removed. It starts by showing an "application is unavailable" message to trick the user into thinking it was never installed.
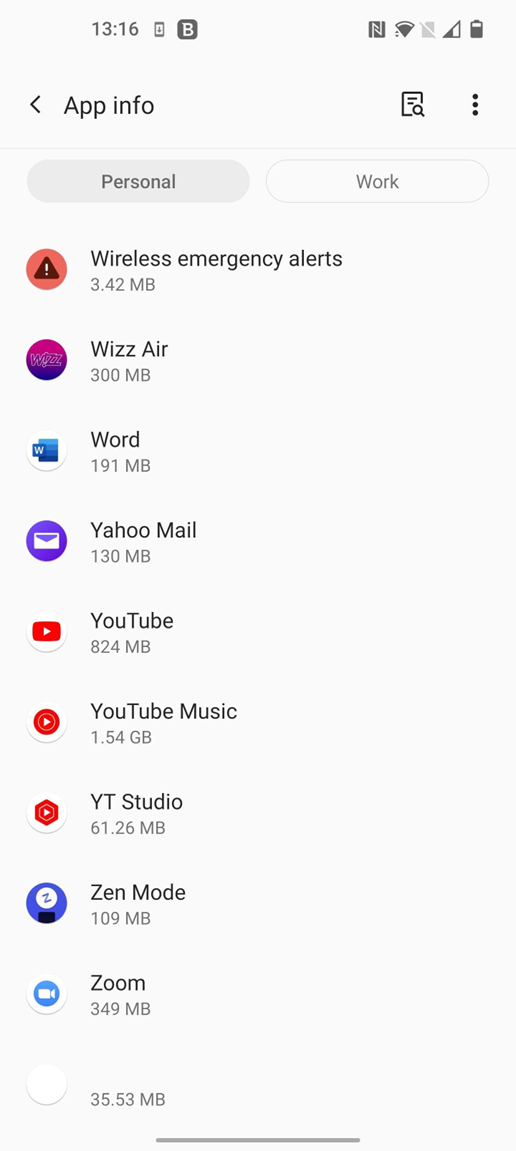
The fact that it has no icon in the launcher and a UTF-8 character in the label makes it harder to spot and uninstall. It will always be at the end of the list, which means the user is less likely to find it.
The result is similar to what is shown in the last entry in the Installed app list.
In fact, we can take a closer look at the code where the message: "Application is unavailable in your region from where the app serves. Tap OK to uninstall" is generated.
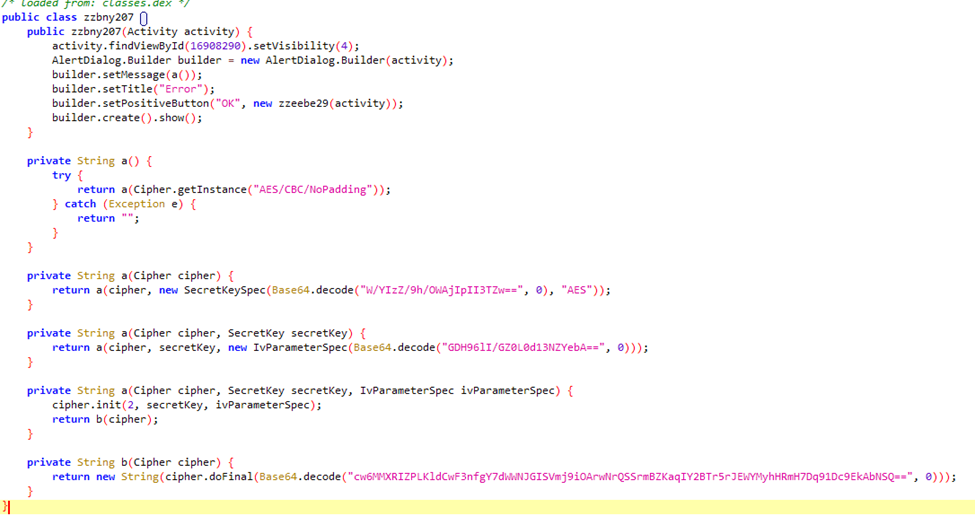
This is where the more interesting part comes into play. The application sleeps for two hours and registers two actions to be called on boot or when the user starts interacting with the device by unlocking the phone. The second action is disabled for the first few days.
Then, every two hours after that, the alarm is triggered, a request to the server is made, and another alarm is registered. The server can choose to initialize the adware phase at an unknown time interval.
The Packer is special too
This malware comes with an efficient packer that uses the SQLcipher package to unload its malicious content. By default, a standard SQLite database is not encrypted. Therefore, if someone opens the database with a text editor, its contents are directly visible to the reader.
The SQLCipher package encrypts all stored data. The malware stores its dex files as entries in an encrypted database; when needed, a simple query returns them. The key used to access the database seems to be the certificate's hashcode.
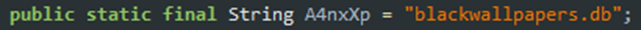
The following function loads the database file from assets. The highlighted variable contains the name of the database file.
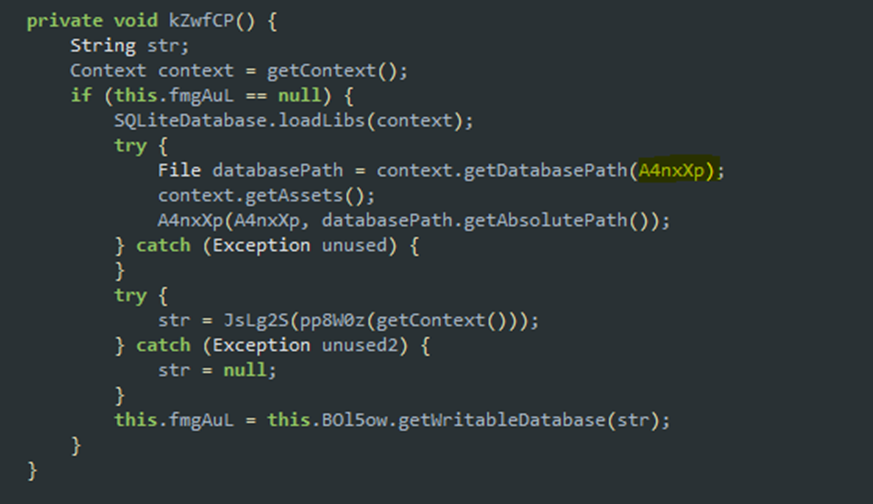
We can observe how this handle is used:
After this previous query, we get all the database entries containing malicious content. The following piece of code is straightforward. It iterates through the cursor, tries to create a file for each entry, writes some bytes to that file (bytes from the entry, meaning each entry has its own bytes), and loads the file as a class.
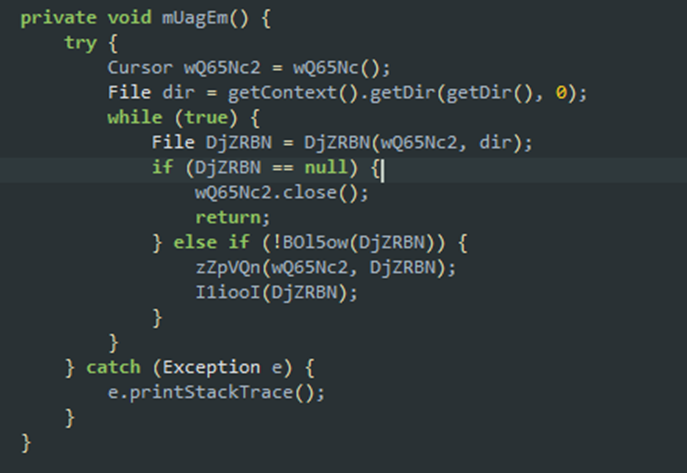
Loading the file as a dex:
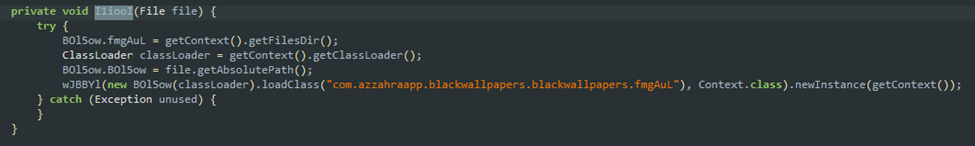
The following sequence is responsible for writing the bytes from an entry to disk:
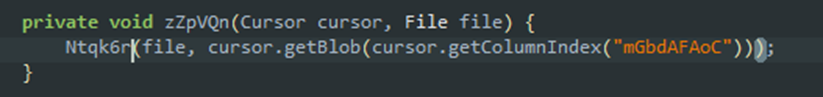
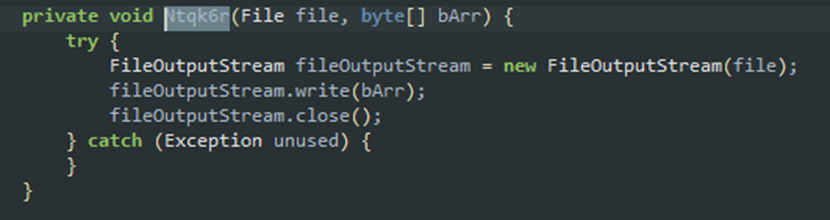
Adware behavior
When the user unlocks the phone, the application gets an adware URL from the server and uses the mobile browser to load the ad. Because the phone's browser is used, the Web Security feature in Bitdefender Mobile Security may catch the link before it is loaded.
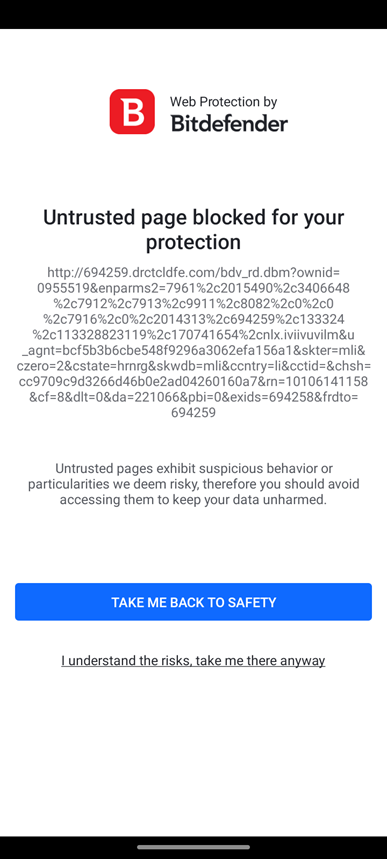

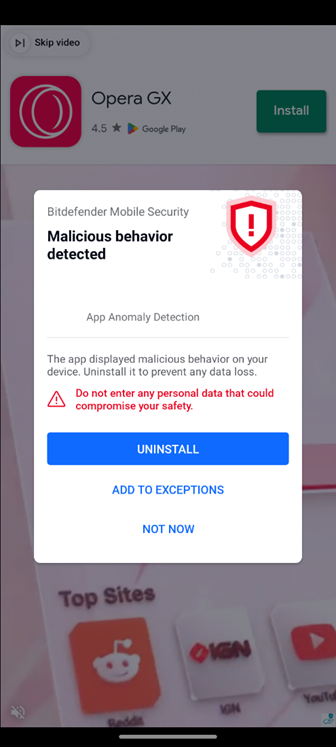
Displaying a full-screen ad is another crucial function of this adware. The application uses one of the adware libraries included to render a full-screen WebView of an ad. We implemented app anomaly detection technology in Bitdefender Mobile Security specifically to detect malicious actions like this.
The malware uses the same alert-based system we already described to receive one of the following commands:
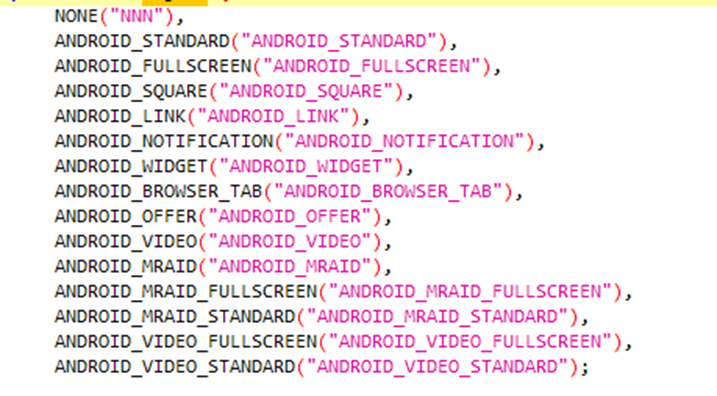
As you can see, it's ready to serve links, notifications, full-screen videos, open tabs in browsers and more. We also put together a short video to show this malware in action.
During our monitoring, we noticed the application loading ads from the following domains (the domains are not necessarily malware-related):
- Konkfan[.]com
- beahor[.]com
- gogomeza[.]com
- kenudo.net
- ehojam[.]com
- adc-ad-assets.adtilt[.]com
- adc3-launch.adcolony[.]com
- adservice.google[.]com
- auction-load.unityads.unity3d[.]com
- config.unityads.unity3d[.]com
- googleads.g.doubleclick.net
- httpkafka.unityads.unity3d[.]com
- pagead2.googlesyndication[.]com
- publisher-config.unityads.unity3d[.]com
- wd.adcolony[.]com
- Many more…
IOCs
All malware in this formerly hidden campaign is now automatically detected by Bitdefender Mobile Security at installation as Android.Riskware.HiddenAds.LL. Here are just a few of the hashed for the adware packages we found.
- 53f3fbd3a816f556330d7a17bf27cd0d com.contec.aflwallpapers4k
- a8b18a67256618cf9dcd433a04448a5b com.deadsimpleapps.all
- 53406cc4b3ced24152860a7984d96dbf com.devindie.appfacil
- c1d312818d07cddb76d2bece7ad43908 book.com.ram.app
- 4df8c05d0e323c5aeeb18c61e3c782c6 com.alamincarectg.app
- d6e33f7b6ff314e2b61f54434a77e8f0 stickers.russia2018
- 8ec0432424da16eb8053453f0ce0731a net.playtouch.connectanimalsok
- db9f921ccecdef6cd8fb7f5cb0a779d2 com.advfn. Android.ihubmobile
- 1313fa114436229856797384230a0a73 com.deadsimpleapps.all
- 3050f562374b275f843f6eb892d2f298 edu.cpcc.go
- 400568ea7406f4d3704fb4c02682313a com.ik.class3pdf
- 7a1efcc701f10d2eef08a4f4bcf16fc2 ir.amin.rostami
- 84aed79a10dd21e0996e08ba0c206965 com.alamincarectg.app
- 4376ecd8add3622c2793239f658aa5e6 com.fhuchudev.apyarcardownload
- 8fcc39166b1a8c29fba3f87307967718 book.com.ram.app
- b7fb1fa1738c5048cecbe73086823843 com.kacyano.megasena
- fd37ff8ded80e9fe07004e201422a129 com.ikeyboard.theme.tiedye.neon.weed
- ef83a9b6ffe20b3abdba08a6517b08f0 studio.harpreet.autorefreshanywebsite
- 319421d550ff761aa4ac2639b3985377 com.mdpabhel.autowebpagereloader2022
- 7e3fa8b054346c013a8148d76be81a48 uz.pdp.ussds11
- 60bae94bfa0c79c19fcc19bc5a9fb8e6 com.alamincarectg.app
Running a security solution that detects these threats is the best way to keep your device secure. Of course, downloading apps from third-party app stores and websites is definitely not recommended.
tags
Author

As part of Bitdefender’s Android team, Razvan’s focus is malware threat research, but he also likes to mingle with statistics and machine learning. In his free time he's either hiking or gaming
View all posts
Junior Security Researcher at Bitdefender, eager to learn anything about computer works. In his free time, he likes to take motorcycle rides and travel.
View all posts
I'm a Junior Security Researcher at Bitdefender, usually prefer to pass the time reading, volunteering, playing chess, and coding
View all postsSilviu is a seasoned writer who's been following the technology world for more than two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks

















