Unpatched Wordpress Instance on Yahoo Blog Leads to Cookie Theft

A spam wave that has been circulating for roughly a month is stealing Yahoo login credentials by exploiting an old – yet unpatched – vulnerability in a component of the Yahoo Developers blog.
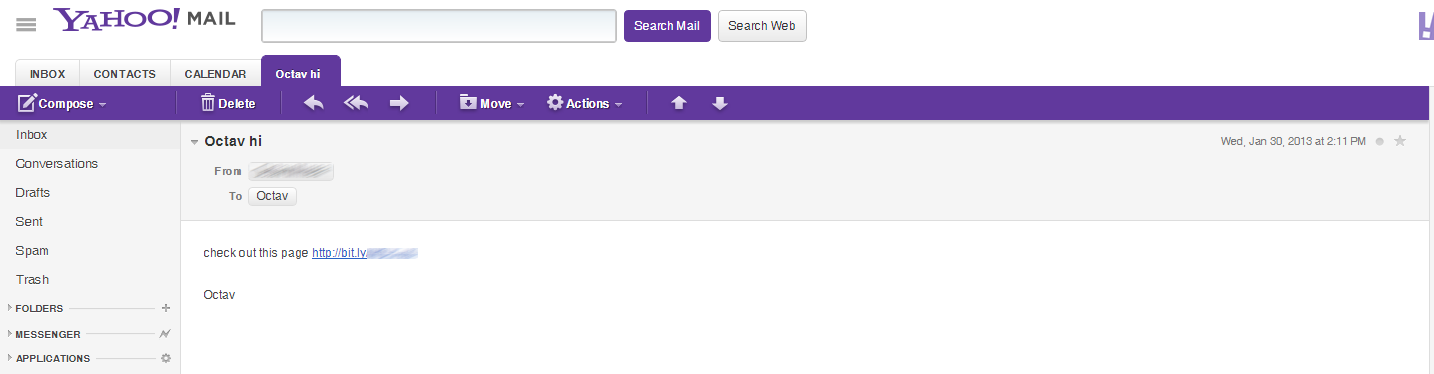
The spam message features a bit.ly shortened URL that takes the user to a web page impersonating the popular MSNBC page, but which turns out to be located on a series of subdomains on hxxp://com-im9.net.
Whois information for the domain reveals it was bought in Ukraine and hosted in a data center in Nicosia, Cyprus.
Once the user lands on the alleged MSNBC page, a piece of JavaScript code inside tries to exploit a known vulnerability (CVE-2012-3414) in the SWF Uploader component on the Yahoo Developers Blog, which is proudly powered by WordPress. We won’t get into the technical stuff, as the issue has not been fixed at the moment of writing.
Since the exploitable component is located on a sub-domain of the target website, the same-origin policy does not prevent the exploit code access to cookies, which are subsequently sent to the attacker. Once they have the log-in cookie, they can authenticate into the victim’s account and send spam or harvest contacts’ e-mail addresses for other spam campaigns. We believe this is the account recruitment stage of the operation and we expect the next wave of messages to feature links to malware.
Bitdefender is currently blocking access to the malicious pages used in the cookie-harvesting campaign. We have also notified Yahoo about the incident and provided the proof-of-concept documentation.
Attack description provided by malware researchers Răzvan Benchea and Octavian Minea.
UPDATED: We have confirmed that his attack does not work on Yahoo.co.jp. The .jp Developer blog seems to be powered by a different blogging platform, which is not vulnerable to the CVE we mentioned in the article, so the attackers won’t have what to bounce their code off of in order to execute code in the context of the Yahoo.co.jp site.
tags
Author
Right now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks