Vulnerability in JetAudio and JetVideo Media Players Allows for Arbitrary Code Execution

An arbitrary code execution in the JetAudio Basic (v8.1.3) and JetVideo media players for Windows could allow an attacker to craft a malicious “.asf” file and compromise the host, according to findings of the Bitdefender Research Team.
The JetAudio Basic and JetVideo applications enable playback of commonly used audio and video files, while also enabling other features ranging from sound effects and remote controll to CD burning and audio recording.
The problem
The problem lies in the JXVidInfo.dll when parsing the asf file’s codec entries. The code copies each codec name in a structure previously defined on the stack, but does not validate the number of codec entries. Consequently, for a large number of codecs the stack gets overwritten.
This particular .dll file is a video info plugin for jetAudio that’s proprietary to JetAudio Inc. As a significant component of the two applications, the same vulnerability can be reproduced on both JetAudio Baisc and JetVideo.
The Attack
We have managed to overwrite the SEH handler to gain execution and we’ve created a proof of concept exploit that works on Windows XP and Windows 7, both x86 and x64, with the default options of DEP (Data Execution Prevention). On Windows 8 and above, our PoC does not work because SEHOP (Structured Exception Handling Overwrite Protection) protection is enabled by default.
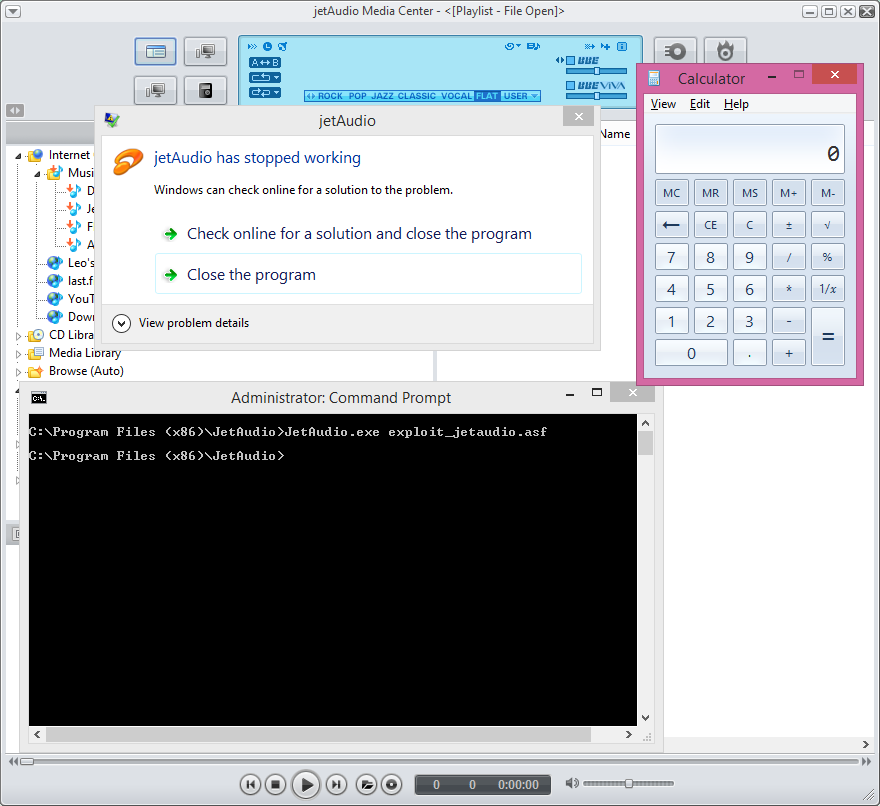
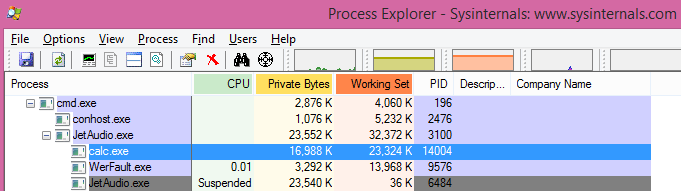
Our proof-of-concept works by passing the crafted “.asf” file as an argument to JetAudio.exe in the command line (Fig. 1) or open it with JetAudio from Explore. Following execution of the file, a new process will be spawned (Fig. 2) from “JetAudio.exe”, specifically, “calc.exe” – our payload.
Fig. 1
Fig. 2
Implications
Considering the trivial exploitation of the vulnerability, it would be fairly easy for an attacker to weaponize an “.asf” file as part of a spear-phishing attack and cause far more serious damage than opening the Calculator application. Knowing the victim has one of the two media players installed on his local machine could turn this vulnerability into a valuable weapon in siezing control of the host.
Whether the attack vector is a drive-by download or a malicious email attachment, it bears little consequence if the file is executed. The payload could be manipulated to execute any tool, process or service that an attacker would need to elevate his privileges on the targeted host.
Note: This article is based on technical information provided courtesy of Bogdan Timofte, Bitdefender Researcher.
tags
Author
Liviu Arsene is the proud owner of the secret to the fountain of never-ending energy. That's what's been helping him work his everything off as a passionate tech news editor for the past few years.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks